In July 2013, WildFire detected a new kind of Android Package File (APK) malware named Dplug. This malware poses as a system tool app for memory cleaning. Dplug uses SMS to hijack the device’s unique identifiers, subscribe to premium services and hide this behavior from the user by blocking the premium service notifications.
By reviewing its behaviors in our WildFire APK sandbox, we observed the following features of this malware. The package name of this detected malware sample is com.dlwx.clean_mc.mactivity, and its package signer is IadPush. After installation Dplug will send the device’s IMEI and IMSI number to a designated phone number through SMS. It then intercepts all incoming SMS and saves the intercepted SMS messages in a hidden folder on the device’s storage card. Further, it blocks incoming SMS messages from two specific premium service numbers belonging to ChinaMobile: 10086 and 1065889955. Another interesting feature is that it provides an auto-confirmation function to premium services that require subscription and SMS confirmation. Besides premium service subscription, the Dplug malware can also push ads to the screen and send customized notifications which are downloaded from remote attack website.
In a typical attack scenario, the attacker first lures the user to install the Dplug malware on the Android device. This is most likely accomplished through the in-app market of the TTpod Chinese music player app, found on Google Play. After installation, the malware will fetch a phone number from attacker website and send the device’s IMEI and IMSI number to this phone number via SMS messages. With the device information, the attacker can impersonate the victim device to subscribe premium services. For services requiring SMS confirmation, the attacker will deliver the confirmation SMS schema to the malware. When the SMS confirmation message is intercepted, the malware will auto-reply the confirmation code to complete the service subscription. All of the attack behaviors occur in the background. The user will sense nothing related to the service subscription until receiving the monthly bill.
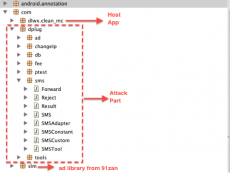
An overview of the reversed malware sample is shown in (Fig 1). The host app part performs the legitimate functions it claims. The attack code is in the dplug package. In this Dplug malware sample, a mobile ad library from “http://www.91zan.com” is downloaded from http://cdn.91zan.com/sdk/pi.jar. This ad library also aggressively collects the phone’s unique identifiers and uploads the collected information to http://service.91zan.com.
Fig 1. An overview of reversed Dplug malware sample.
Technical Details
Intercept and block incoming SMS messages
The malware claims the highest priority of receiving intent android.provider.Telephony.SMS_RECEIVED so that when an incoming SMS message arrives, the malware will intercept the message before other apps. (Fig 2)
Fig 2. Broadcast receiver com.dplug.ptest.DlwxReceiver claims the highest priority for receiving four types of intents in AndroidManifest.xml file
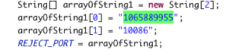
The intercepted SMS messages are then examined by the isPinBi() function in the file com.dplug.sms.SMSTool.java. “PinBi” means “shield” in Chinese. In this function, the malware intercepts SMS coming from two numbers, one is 10086 (a hotline number of China Mobile Communication) and the other is 1065889955 (a notorious malicious premium service subscription number widely used by mobile malware in China). These two numbers are hardcoded in the file com.dplug.tools.Constant.java (Fig 3).
Fig 3. The hardcoded numbers
If an incoming SMS message is from either number, the malware will block the message from being inserted into the inbox. The purpose is to block the premium service notices sent from carrier such as the premium service subscription notice, service subscription confirmation notice, and billing notices. The victim will not notice the premium services the attacker subscribed to using their phone’s identity.
The malware will save the intercepted messages in a “log.txt” file. For each message, the malware will log receive time, sender phone number and the message body (Fig 4).
Fig 4. Examples of intercepted SMS messages in the “log.txt” file
To hide the logs from being detected, the malware creates a hidden folder in the path “/mnt/sdcard/Android/.system/.dplug” and saves the logs there. The file path for “log.txt” is “/mnt/sdcard/Android/.system/.dplug/log.txt”.
Send IMEI and IMSI number of device to remote attacker via SMS
Dplug collects the IMEI and IMSI numbers from the device. The two numbers are sent via SMS to a designated phone number and then retrieved by contacting the URL http://www.android-3.com:8008/getPhoneNo.do?arg=0&m=get (Fig 5)
Fig 5. Retrieve the receiver phone number via www.android-3.com:8008
With the retrieved number the malware will construct a SMS message and sent out in the background (Fig 6).
Fig 6. The SMS message sent with IMEI and IMSI number
With the IMEI, IMSI and phone number, the attacker will impersonate the phone owner and subscribe to premium services. The attacker profits through those premium services.
Premium service subscription auto-confirmation
To avoid unnoticed premium service subscription, the carrier will send confirmation SMS messages to the subscriber’s phone. This message usually contains the subscription information and a random confirmation number. The user needs to replay this confirmation number in order to confirm the subscription.
To deal with the confirmation requirement, the Dplug malware first downloads an SMS configuration file from the url http://117.135.131.19:8008/sms.do. The configuration file is parsed by the ParseTool.parseSMSConfig() function and the parsed information is saved in a SMSCustom object. Related source code is shown in (Fig 7).
Fig. 7 A configuration file downloaded in the doSMS() function of com.dplug.sms.SMSAdapter.java file
The most important information in the configuration file is the Forward information that is described in the com.dplug.sms.Forward.java file. It includes the key string that is used to identify the confirmation code, and the format of confirmation SMS messages.
The auto confirmation procedure is done in the com.dplug.sms.SMSTool.java file. When an incoming SMS containing the key string is intercepted, the malware will use the Forward information to extract the confirmation code from the incoming message, and then automatically reply to the confirmation SMS sender with the confirmation code extracted (Fig. 8). The confirmation SMS message will also be blocked from being delivered to the inbox.
Fig 8. Auto confirmation with extracted confirmation code
The malware logs all communications between itself and the remote attack servers in the log.txt file which is saved in the hidden folder “/mnt/sdcard/Android/.system/.dplug/ASK/log.txt”.
Additional observations
The observed network communications include:
| URL | Returned results |
| http://www.android-3.com:8008/getPhoneNo.do?arg=0&m=url | “http://218.206.176.241:8084/0901?http://42.121.144.223:88/wyt.jsp” |
| http://www.android-3.com:8008/getPhoneNo.do?arg=0&m=get | “get:13241586871” |
| http://www.android-3.com:8008/3.php?arg=0?cancel=1 | “error” |
| http://www.android-3.com:8008/3.php?arg=0?cancel=0 | “error” |
| http://www.smqgame.com:888/new.jsp?arg=0?cancel=1 | “OK” |
| http://117.135.131.19:8008/sms.do | The confirmation message format. IP is still alive. The service is down. |
The Dplug malware requires many permission types including:
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.INTERNET
- android.permission.KILL_BACKGROUND_PROCESSES
- android.permission.FORCE_STOP_PACKAGES
- com.android.launcher.permission.INSTALL_SHORTCUT
- com.android.launcher.permission.UNINSTALL_SHORTCUT
- com.android.launcher.permission.READ_SETTINGS
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.INSTALL_PACKAGES
- android.permission.DELETE_PACKAGES
- android.permission.RECEIVE_BOOT_COMPLETED
- android.permission.RECEIVE_USER_PRESENT
- android.permission.RECEIVE_SMS
- android.permission.RECEIVE_USER_PRESENT
- android.permission.RECEIVE_SMS
- android.permission.SEND_SMS
- android.permission.INTERNET
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.GET_TASKS
- android.permission.ACCESS_WIFI_STATE
- android.permission.CHANGE_WIFI_STATE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.WRITE_APN_SETTINGS
- android.permission.READ_PHONE_STATE
- android.permission.CHANGE_NETWORK_STATE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.INTERNET
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.INTERNET
- android.permission.WRITE_EXTERNAL_STORAGE
- android.permission.READ_PHONE_STATE
- android.permission.ACCESS_NETWORK_STATE
- android.permission.SYSTEM_ALERT_WINDOW
- android.permission.GET_TASKS
Dplug listens to the broadcast of following intents:
- android.intent.action.MAIN
- android.intent.action.PACKAGE_ADDED
- android.intent.action.PACKAGE_CHANGED
- android.intent.action.PACKAGE_REMOVED
- android.intent.action.PACKAGE_REPLACED
- android.intent.action.PACKAGE_RESTARTED
- android.intent.action.PACKAGE_INSTALL
- android.intent.action.BOOT_COMPLETED
- android.intent.action.USER_PRESENT
- android.provider.Telephony.SMS_RECEIVED
- android.intent.action.PHONE_STATE
- com.dplug.ptest.DlwxService2
- android.intent.action.PACKAGE_ADDED
- android.intent.action.PACKAGE_REMOVED
- android.net.conn.CONNECTIVITY_CHANGE
- com.zan.action.ALARM_ACTION
- android.intent.action.USER_PRESENT
Malware sample availability
SHA256 value of the detected malicious APK file is:
c87fe742831f52834fe5dcdae6aa96006b129f93cb71b406a68973675d74f62c.
The APK file URL (valid at time of publication) is:
http://d1.ttpod.com/market-file/2013/07/05/and_cs_nck/new_80030004.apk
Ttpod.com is a Chinese music player app. The player app is available at Google Play store with name TTPod ( https://play.google.com/store/apps/details?id=com.sds.android.ttpod). It is highly likely that this malware sample was downloaded through the in-app market of TTPod app.