Key to the Palo Alto Networks story is that our products safely enable network traffic based on applications, users and content. In many of my meetings with customers, I'm asked to explain the difference between safe application enablement and more antiquated security solutions that either let too much in or keep too much out. So, let's review that difference.
Many legacy security products continue to rely on the same network techniques first introduced nearly two decades ago. In many cases, they are only capable of allowing or blocking entire ports as opposed to individual applications. That means that IT administrators are left with two less-than-desirable choices: they can either say "yes" and allow undesirable applications to operate alongside essential ones, or they can say "no" and block entire classes of applications, many of which might be beneficial to business.
Even products that bolt-on the ability to distinguish individual applications still rely on those old techniques to initially classify traffic -- a needlessly complex process with a high potential for configuration errors and performance degradation.
Palo Alto Networks' approach is a security platform that classifies all applications regardless of the network channel they use, or any bypass techniques they might employ. That information becomes the basis for all policies and inspections that are performed, and because we can identify users, content and data associated with each session, we can also identify "gray-area" applications that might be good or bad depending on circumstance.
Here's an example: you can write network security policies to allow a group of software engineers in R&D to use specialized development tools to share and collaborate on product specifications and source code amongst themselves. In addition, you can have granular control over which functions of that application your business partners might have access to such types of files that can be exchanges, read-only vs. read write access and more. You can also completely block users from other departments. The beauty of our approach is that you can adjust these policies to be as granular as you want, down to the level of individual functions of an application, a user or a group of users if needed.
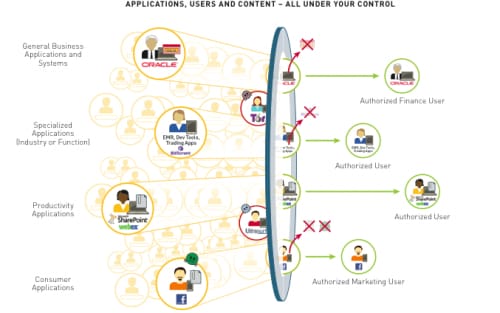
What results is the ability to confidently say "yes" to those applications needed to support business processes, without the concern of undue risk, policy management complexity or performance problems.