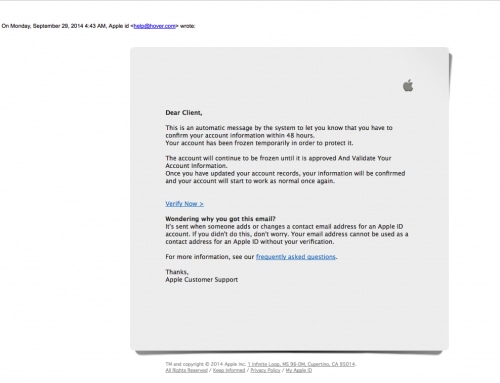
If you purchased an iPhone 6 recently, you probably received this email:
Some of you may have even clicked the “Verify Now” link and entered your Apple ID account information. I hope not, though, because this email is not from Apple. It’s a phishing email meant to trick recipients into giving sensitive information to the attacker who sent it.
This email illustrates two things:
- Attacks are more sophisticated as cybercriminals get smarter and craftier.
- An increased level of understanding regarding cyber attacks is needed, not just within the corporate community, but within the general public as well.
The market for enterprise network and cybersecurity grows each year highlighting the emphasis companies are putting on preventing modern threats from infiltrating their internal networks. However, the impetus is focused on technological preventative measures. Could an education in cybersecurity — who the attackers are, what they’re after, and the appropriate level of scrutiny that should be practiced — significantly bolster an enterprise’s cyber defense?
Yes. In 2011, RSA was the target of a spear phishing attack made successful by at least one employee opening the malicious attachment even after their spam filter had correctly placed the email in the “junk” folder. RSA suffered a data breach as a result.
“At least RSA’s SPAM filters were working, even if their social engineering training for employees was not,” -Avivah Litan, Gartner Analyst
More recently, a spear phishing attack targeting physicians at a Tacoma-based medical group led to the breach of 12,000 patient records. Emails were crafted to appear as though they were sent from the group’s parent company, and prompted targets to click on a link and enter their email account username and password. The group has since rolled out a company-wide phishing prevention system, including retraining the employees who fell for the initial phishing email.
Spear phishing attacks are:
Lucrative. The black market for data is huge, estimated at multiple billions of dollars, meaning that the person or organization behind the attack may not actually use what they steal to make money. Unfortunately, this also means they’re more difficult for authorities to track down.
Successful. Because hackers take pains to get their targets to fall for their schemes, they know what company and department you work for, what applications you use, who you report to, and what kinds of projects you’re likely working on. They know which job titles are likely uninformed or unwary of potential threats. This makes spear phishing campaigns one of the most highly-favored APT attack methods.
Simply a means of getting in. Once a target is duped into clicking a link, opening a file, etc., the attacker can carry out his mission, whether it’s stealing personal information, using a target’s personal account to transfer money, extract intellectual property or insider information.
A real threat to both corporate and consumer spheres. Both have data that attackers want to use to make money, and most people who work for targeted companies have a home computer or mobile device for personal use that is not protected by enterprise network or endpoint security policies.
Recognizable… sometimes, if you know what you’re looking for.
- Check the sender’s email address to make sure it’s someone from whom you should be receiving emails. If you’re still not sure, email clients like Outlook and web mail applications like Gmail usually have options to view email messages with the headers included, so you can make sure the “From” field matches the “Reply-to” field.
- Look for patterns of misspellings and incorrect grammar.
- Ask yourself if links and attachments within the message are expected information from the sender and work-related. Do the domain name or file name make sense? View the email with formatting turned off to view a link’s actual URL.
- Check the attachment’s file extension. Odds are that unless you’re in the IT or engineering department, you shouldn’t be receiving or opening file types with extensions .exe, .dll, .scr, or .class. According to Symantec, these file types were used in more than 50% of last year’s spear phishing attacks.
- If you’re still unsure that an email is legitimate, ask your company’s IT security folks.
Cyber best practices like these aren’t just for those who deal with security as part of their daily job duties. They need to be taught company-wide.
What kind of corporate policies and programs promote a healthy balance between paranoia and productivity?
I’ve heard of one corporate program where basic cybersecurity best practices are taught as part of the new hire training class for every employee. Another IT-run program periodically assesses its employees by sending fake phishing emails to different groups within the organization; those who fall for the faux scam by either opening an attachment or clicking a link are then required to take a cybersecurity seminar. The goal of these programs is to arm the company’s workforce with knowledge and deploy them as another layer of cyber defense.
Using the right tools to prevent attacks is key, and one of those tools is familiarity with the kinds of tactics cyber criminals are using, and how to recognize and avoid them. What processes or programs have you seen put in place that educates employees and encourages cyber scrutiny?