As 2014 comes to a close, our subject matter experts check in on what they see as major topics and trends for the new year. (You can read all of our 2015 predictions content here.)

I know this is a cliché statement, but this year has flown by at the speed of light. I love looking to the future and I can’t wait to see how next year will shape up. Looking back on a few key trends in threat prevention for 2014, I can provide some insight into what awaits us in 2015. Here are three trends that stuck out as important indicators of what’s to come in the next year.
1. Attackers will use more legitimate and convoluted means to launch widespread attacks.
You’ve likely seen the word “malvertising” tossed around. This attack method has been around for a few years, and Yahoo! and AOL were both targets in September and October of this year, earning attackers thousands of dollars per day.
But the use of malvertising as an attack method is a shift from the kind of dark-corner trickery seen in spear phishing and packet sniffing to a technique that leverages a legitimate business process to do all the hard work normally involved in delivering malware. The process gives the attacker access to potentially millions of users with minimal effort. All the attacker has to do is design the malvertisement code.
We’ll be seeing a lot more of these types of malware delivery methods. Not just malvertising campaigns, but also the use of bona fide business procedures to deliver malware and amplify results. Widely-used business channels with little to no security are tempting targets for attackers; they provide a constant stream of unsuspecting targets and feature lots of moving parts that make it impossible to track down the attackers. It will require careful coordination to make these channels more secure.
2. Application security is getting better all the time. However, we will continue to see a steady stream of zero-days, mostly related to legacy code.
Secure coding practices have become a part of the software developer’s everyday life. In the past few years, we’ve seen more application security and development teams turn to static and dynamic analysis to catch code and business logic vulnerabilities and fix them before the application is released or updates are pushed.
Customers are starting to build time-to-fix clauses with monetary penalties into their contracts with vendors. If anything is clear in the B2B universe, it’s that vulnerabilities affect application integrity, which affects customer trust, which affects revenue. It’s easier and much cheaper to fix vulnerabilities during the early development cycle than once an application has reached production or even QA.
However, this also means that legacy code is much more expensive to fix, even if a vulnerability has not yet been exploited in the wild. Along with the fact that black hat hackers are continuing to get more creative, this is the reason why the number of CVEs in 2015 will remain at least equal to if not greater than the number reported in 2014.
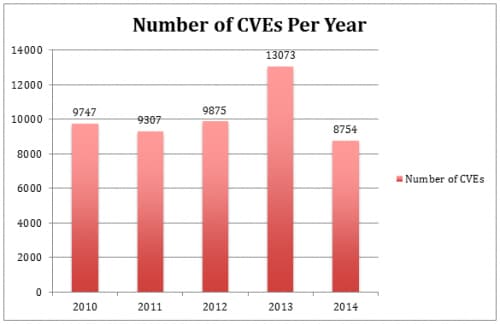
*CVE information for years 2010 through 2013 taken from Secunia <http://secunia.com/vulnerability-review/vulnerability_update_all.html>
*CVE information for 2014 taken from <https://cve.mitre.org/>
3. IPS functionality and firewall functionality will meld more than it already has.
As the enterprise market sees the benefits of a true platform-based approach to security, I suspect we’ll see more vendors phasing out stand-alone and UTM security solutions. What better way to truly bolster the way IPS handles security than by including other defensive techniques like decryption, decompression, application-ID, user-ID, data-loss prevention, and sandboxing?
The market’s move from traditional IPS to Next-Generation IPS to NGFW + NGIPS already started, but there’s more innovating to be done to supply security that keeps up with what the bad guys are doing. There’ll be more appeal than ever for a single, integrated platform that “does it all,” doesn’t require users to take a performance hit, and can be used anywhere from data centers to the cloud.
So, who else is excited for 2015?
Threat prevention is among many focus topics at Ignite 2015, where you will tackle your toughest security challenges, get your hands dirty in one of our workshops, and expand your threat IQ. Register now to join us March 30-April 1, 2015 in Las Vegas -- the best security conference you'll attend all year.
