There are many ways to look at cloud computing and what it means for your business. I personally like the definitions from cloud tutorial, which offers two classifications:
- Based on where the cloud infrastructure is located: Private, public or hybrid
- Based on the services that the cloud delivers, whether Infrastructure as a service (IaaS), Platform as a service (PaaS) and/or Software as a service (SaaS). Examples include Amazon web services, or Rackspace (for IaaS), Google Application Engine, Force.com, or Microsoft Azure (for PaaS), Salesforce.com, Google Docs, (for SaaS). Online services like Facebook, Dropbox, Box.net and others that are used both by consumers for personal purposes but also by many B2C and even B2B companies to interact with their customers fall under this classification as well.
Technologists and network security administrators tend to focus on the first cloud classification because it’s based on how the cloud is being deployed, managed and what needs to be done to make it work and secure it. Business-oriented folks focus on the second classification because it provides a more explicit description of the service provided and its related benefits. End users and employees often refer to cloud computing as services or applications because of how they experience the cloud: as a service or an application on their computer or mobile device.
The mushrooming popularity of cloud services makes it impossible to continue to rely on a security approach focused primarily on the perimeter of your enterprise. Employees can too easily move data and content from protected areas on your own network to cloud services that you have no direct control over. And it’s too easy for the leakage of information to get out of control: your team starts using an online file repository tool to share large video or creative files with partners ahead of a major event. Maybe that sharing next turns into more strategic files – plans, roadmaps and other sensitive documents - posted on these external collaboration services because the service is so convenient to use.
Cyber criminals can also attack these 3rd party services to steal credentials from your employees and in turn use these credentials to infiltrate your network. Targeting enterprise business partners has been a more common first step of many of the breaches that have made the headlines in the past 12 months.
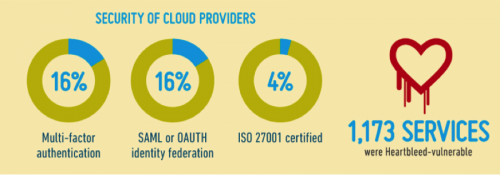
For a full view of the infographic, visit: http://www.skyhighnetworks.com/resources/cloud-adoption-risk-q2-2014/.
Doing your security due diligence on cloud services requires you to understand these cloud services better and why your company and your employees turn to them. As a starting point, read the top 50 list published by one of our technology partners, Skyhigh Networks. Then, consider the following steps to get a handle on the use of cloud services in your organization:
- Identify cloud services in use in your organization, and the employees or departments that use them: Get our Palo Alto Networks enterprise security platform deployed in tap mode on your internet gateway and you’ll start to get visibility into many of these cloud services (note that this is a non-disruptive process and you can start to get valuable information in as little as 24 hours). Our App-ID technology can help you discover traffic for hundreds of file sharing and file storage cloud-based applications. This includes Dropbox, Box.net, and Evernote amongst others. You can visit our Applipedia database to see the full list of applications covered. In addition, turn on the url filtering function in our platform to enable the discovery of services that are 100% web based.
- Understand the business need behind the use of the newly discovered cloud services: Whether these services are vetted on not by your IT department, you should proactively approach users and work with departments’ heads and IT to understand what’s the business need behind the use of any cloud service. Then you can decide whether the use of any specific service is legitimate and needs to be secured, whether the use needs to be restricted to specific departments, or finally whether the service represents too much risk to the business and you need to implement security policies to explicitly block it.
- Diligently manage the lifecycle of these cloud services: One of the most overlooked aspects of cloud services is what happens (or rather what does not happen) when an employee leaves the company. You need to apply to cloud services all the off-boarding procedures that are standard to other enterprise applications to ensure that access is turned off once the employee has left. This is actually a great driver to pursue the discovery of who uses which cloud services. In addition, cloud services used for business purposes should never be attached to an employee personal email, but unfortunately that is often the case.
- Revisit and update your security policies for the use of cloud services: Because there will be new, enticing cloud services launched every month, you need to continuously monitor activity on your network for the emergence of new cloud services adopted by your workforce. Keep repeating the above process on a quarterly basis at a minimum and proactively maintain a regular dialog with employees and users of these services. You might actually discover a few great applications in the process that should be used by everybody!