Organizations are facing persistent, elusive and sophisticated cyber-attacks more than ever. Sometimes these attacks might seem unavoidable, leading you to believe that your network and data cannot be protected. But if you think about how cybercriminals need to successfully infiltrate your network, remember the various steps in the cyber kill chain required to do so, including “breach premier,” “deliver malware,” “endpoint operation” and “exfiltrate data.”
The good news is that blocking just one step in this cyber-attack chain, you can protect your network and data from attack.
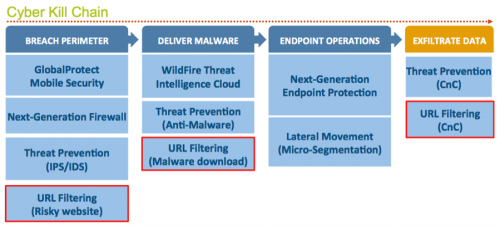
The above model shows how we think about the cyber kill chain at Palo Alto Networks. PAN-DB plays a critical role in three of the four stages, highlighted in red. As we discussed in the recent blog post, “Web security tips: How PAN-DB works,” PAN-DB has a rich database of malicious URLs that can be used to block malware downloads, and to disable Command and Control (C&C) communications. This database will help you to block attacks throughout the cyber kill chain.
Here are a few examples
Breach perimeter
Advanced attacks commonly try to breach the perimeter. PAN-DB gives you protection against breach perimeter by blocking risky websites such as hacking, phishing, malware, drive-by-download and exploit sites.
Deliver malware
Once the perimeter is breached, attackers try to make you download malware on to your network. PAN-DB helps you to block downloads from malware sites. In addition, by blocking file downloads from unknown URL category (as we discussed in another recent blog, “Web security tips: Using URL categories in your security policy”), you can reduce the risk of downloading malware significantly.
Exfiltrate data
Malware can enter your network by evading your gateway security, such as through an employee’s own laptop or USB drive. Malware in your network communicates with the attackers and exfiltrates data. But PAN-DB helps you to disable such C&C communications by utilizing C&C URL and IP database as provided in WildFire.
URL filtering should do more than prevent unwanted web browsing
Traditional URL filtering was born to block non-business web access for productivity and compliance purposes. Although those purposes still hold true for URL filtering, the solution is incomplete unless it can also filter harmful websites to protect your network and data from cyber-attacks.
PAN-DB will add more protection to your Palo Alto Networks Enterprise Security Platform. We hope you utilize the power of PAN-DB to protect your network from advanced attacks.
To learn more about web security, please visit our resource page, “Control Web Activity with URL Filtering.”