A big change is happening in the world of data centers. The software-defined data center (SDDC) is coming, and the biggest data center operators are leading the way – cloud providers, telecoms and social media companies. The change is all about service agility and driving down cost. In short, it is about maximizing data center ROI.
Security is an essential enabler of this change. It has to be embedded in the fabric of the SDDC. What are the key factors for achieving this, and how is Palo Alto Networks able to deliver on those requirements better than any other partner?
1. Zero Trust Security
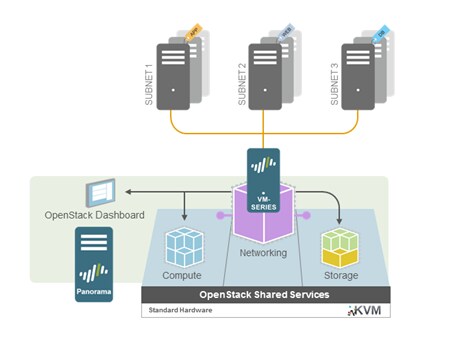
The amount of machine-to-machine, east-west traffic far eclipses the volume of traffic flowing into and out of the data center. Once malware gains a foothold in an infrastructure, it will move laterally in order to compromise more hosts, gain access to data, and steal or damage assets. With customers and business processes sharing the same physical infrastructure, there is a need for strict security isolation of inter-VM traffic, based on those business processes, rather than on ports, protocols and IP addresses. The Palo Alto Networks® VM-Series security platform provides these fine-grained traffic controls needed to achieve strong risk mitigation in shared environments. By enforcing a Zero Trust model of communication within each business process, the integrity of each process is well secured.
Figure 1. Zero Trust security with Palo Alto Networks VM-Series for KVM/OpenStack®
2. Positive Security Controls
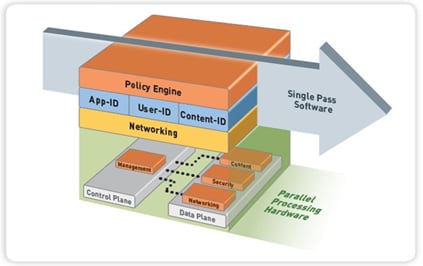
A positive security control model allows only what is explicitly identified as good (“whitelisting”). A negative control model (“blacklisting”) only blocks what is known to be bad. By definition, a negative security model cannot stop unknown threats. Traditional, port-based firewalls implement positive controls, but these controls do not extend to the application layer. To address this gap, legacy firewall vendors have added intrusion prevention system (IPS) functionality to port-based firewalling. However, IPS is still a blacklist approach — anything not known to be bad is assumed to be good. This is how hackers exploit traditional defenses. Our solution implements a positive control model through Layer 7, giving security architects the power to create policies that limit application and data traffic flows to the specific requirements of a business process. No other security solution does this.
Figure 2. Application/User/Content-based policy engine enables positive security control model
3. Security Orchestration
A positive, Zero Trust-based security architecture is of no value if it cannot be implemented and maintained in the software-defined environment. Traditional firewalls are designed to work in relatively static environments, where security policies are tightly coupled with network layer parameters (e.g., IP addresses, ports, protocols). This approach is not adapted to environments where the network topology dynamically adjusts in response to changing demand for services.
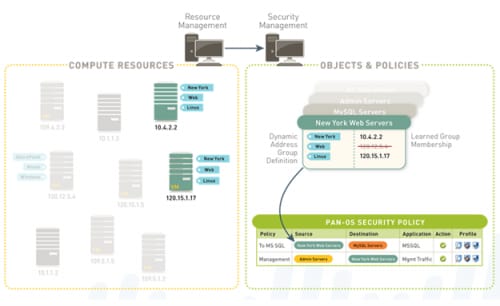
The Palo Alto Networks solution architecture is fundamentally different. Policy definition is based on business process-based parameters: the application, the user and the content. Security policy is associated with the logically defined resources (e.g., SQL servers supporting credit card transactions) that implement the business process — regardless of where those resources reside at the network layer. This architectural difference enables security controls to be instantiated dynamically and in concert with the compute, storage and network resources that are instantiated in response to changing demand. Equally important, when resources are removed, the security instances and policies associated with those resources are also removed. Figure 2 illustrates this capability (Dynamic Address Groups).
Figure 3. Security Orchestration with Dynamic Address Groups
4. People and Partnerships
As security and networking become software-defined, service providers are facing a growing skills shortage. Their staffs need to acquire new skills in scripting languages, writing to APIs and combining software packages into full solutions. In short, networking and security engineering is also becoming software-defined. The skills issue is possibly the biggest barrier to meeting the aggressive targets large DC operators have set for themselves.
At Palo Alto Networks, we have invested heavily in developing our people and the industry partnerships needed to help service providers take SDDC from the drawing board to implementation. Our platforms are tested to work with the virtualized platforms and orchestration stacks favored by service providers and enterprises. Our engineers and consultants have the real-world experience working with service providers to implement orchestrated, software-defined security solutions. This strong set of skills, experience and proven solutions are critical success factors for bringing SDDC projects to life on time and on budget.
Conclusion
Security is not a just a perimeter issue for the SDDC. There is an essential need to monitor and control east-west traffic, even within a single, physical server. Positive security controls must provide full visibility, reduce the attack surface to a minimum, and stop unknown threats. The security architecture must be business process-oriented; otherwise, the rules for enforcing policy cannot be orchestrated in tandem with the system as a whole. Finally, it only makes sense to work with a vendor that, not only offers a sound technology foundation, but also has proven solutions, a partner ecosystem, and the people to help you be successful.
To learn more about Security Orchestration for the Software-defined Data Center, check out the resources available on our website.