Having joined Palo Alto Networks following a 35-year career in the U.S. military, the past decade of which I served in a variety of leadership positions in cyber operations, strategy and policy, I have found that many of the cybersecurity challenges we face from a national security perspective are the same in the broader international business world.
This blog post series describes what I consider to be four major imperatives for cybersecurity success in the digital age, regardless of whether your organization is a part of the public or private sector.
Imperative #1 – We must flip the scales (February 16, 2016)
Imperative #2 – We must broaden our focus to sharpen our actions (March 12, 2016)
Imperative #3 – We must change our approach (March 30, 2016)
Imperative #4 – We must work together
IMPERATIVE #4 – WE MUST WORK TOGETHER
Before I get to the details, allow me to review some background and context, and then provide an executive summary of Imperative #4 in case you are pressed for time.
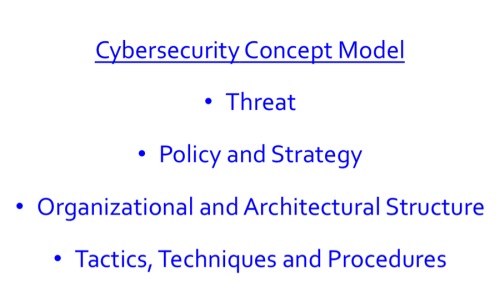
As a reminder from my previous three blogs, I use the factors in Figure 1 to explain the concept behind Imperative #4 in a comprehensive way.
- Threat: This factor describes how the cyberthreat is evolving and how we are responding to those changes.
- Policy and Strategy: Given our assessment of the overall environment, this factor describes what we should be doing and our strategy to align means (resources and capabilities – or the what) and ways (methods, priorities and concepts of operations – or the how) to achieve ends (goals and objectives – or the why).
- Structure: This factor includes both organizational (human dimension) and architectural (technical dimension) aspects.
- Tactics, Techniques and Procedures (TTP): This factor represents the tactical aspects of how we actually implement change where the rubber meets the road.
In this final blog of the series, I’d like to take you through Imperative #4 using the concept model outlined above, and step through the implications.
Figure 2
EXECUTIVE SUMMARY
For this last imperative in the series, I want to focus on something that I believe is absolutely vital to success. I’m leveraging my previous national security experience, as well as my current private industry role, in emphasizing the critical importance of this imperative.
In my view, no single organization, public or private, has all of the talent, skills, resources, capabilities, capacity, or authority to act effectively when doing so in isolation. It truly takes teamwork and effective partnerships to act effectively with cybersecurity in the modern digital age. Therefore, we must work together if we want to be successful as a community.
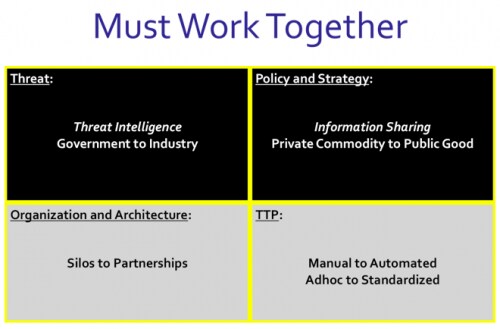
There is already a significant shift going on regarding cyberthreat information sharing. What was once the sole purview of governments is now increasingly being done by industry, and this is a much-needed shift.
It’s very important to distinguish cyberthreat information sharing from the more contentious terrorist threat information sharing and associated surveillance issues that flood today’s international headlines.
Cyberthreat information is focused on indicators of compromise and not commercial proprietary information, personally identifiable information, personal health information or the personal content of individual communications.
Indicators of cyberthreat compromise include:
- Malicious code
- Information infrastructure transmission
- Connection and collection points
- Compromised systems and networks
- Cyberthreat organizations and individuals
- The general categories of entities that these threat organizations and individuals target for their malicious activities
- The techniques that these cyberthreats employ to conduct their actions across the threat lifecycle
From a policy perspective, an increase in cyberthreat information sharing across private sector organizations has led to a change in the views of a growing number of industry leaders. Rather than hoarding cyberthreat information as a commercial commodity, many leaders are now seeing a growing need to share the information as a public good. The greater overall good achieved by sharing this specific type of intelligence vastly outweighs the parochial interests of individual commercial entities, and the focus shifts to what commercial competitors do with the information once it is shared.
Effective information sharing requires an accompanying organizational structure shift from working in isolated silos to building effective partnerships and an environment of strong teamwork. Some organizations find this shift difficult to achieve, which is why it must be driven by the organization’s leadership to be effective.
The final set of implications resulting from Imperative #4 deals with making it actually work at the tactical level with the required speed and scale. This requires a shift from manual to automated TTP regarding two distinct activities. The first activity is the automated sharing of cyberthreat indicators of compromise, themselves. Equally important is the need to shift from the manual, human-based efforts to prevent further threat success as a result of the shared intelligence to an automated defensive posture adjustment procedure in near-real time.
Scaling the distribution of threat intelligence to the scope that partnership growth demands also requires the use of standardized formats and procedures that enable automated sharing instead of legacy TTPs that use slow, adhoc and often manual approaches that usually result in confusion and complexity.
DETAILED DESCRIPTION OF IMPERATIVE #4
THREAT
I have 35 years of experience in the U.S. government and, more specifically, the U.S. military. During the vast portion of that experience, I had a close association with the national intelligence community, as well as the intelligence communities of many partner nations.
Now that I’ve been in the private sector for some time, I can tell you with confidence that what used to be the sole purview of governmental intelligence communities in terms of access and visibility into the cyberthreat landscape is now changing very, very dramatically. I believe this change is appropriate, as well as inevitable.
The private sector is awakening – in no small measure due to the alarm bell that the national and international security communities have been ringing for the past several years – to the growing size, sophistication and increasingly sinister intent of cyberthreats across the world.
In my view, there is a significant shift from governments being the sole dispensers of cyberthreat intelligence towards industry being more and more powerful as a producer of not just vulnerabilities and cyberthreat information but also real cyberthreat intelligence.
It’s very important to distinguish what I’m calling cyberthreat intelligence from other types of intelligence, especially terrorist threat intelligence and the contentious surveillance issues associated with it. I’m NOT talking about proprietary commercial information (intellectual property or financial data), personally identifiable information, personal health information or the personal content of individual communications.
If you recall the key points I made in each of my last three blogs in this series about how we must change our view of the cyberthreat, I’m talking about indicators of compromise (IOCs) based on the cyberthreat lifecycle.
Indicators of cyberthreat compromise include: malicious code; information infrastructure transmission connection and collection points; compromised systems and networks; cyberthreat organizations and individuals; the general categories of entities that these threat organizations and individuals target for their malicious activities; and the techniques that these cyberthreats employ to conduct their actions across the cyberthreat lifecycle. This kind of intelligence CAN be shared.
This is a good thing. Because if those in industry are expecting the government (whichever country you are from) to show up with all the intelligence needed to defend against the threat, that is not a realistic expectation.
Having come from government, one of my biggest frustrations as a network defender was the inevitable intelligence / gain-loss equity assessment that played out when there was valuable cyberthreat intelligence that the defense community needed. Sharing it usually represented too much of an intelligence risk to sources and methods, so there was always tension.
Sometimes, the tension surrounding sharing also came as a result of our own ability to take advantage of the same thing against one of our adversaries. Nobody on that side of the argument wanted to give away such an advantage by sharing the information with the cybersecurity community; and therefore, our adversaries then would have known as well.
In my opinion, this situation is improving slowly because the intelligence gain/loss balance is now tempered by a real sense of an equally strong and competing operational gain/loss equity at play. In my opinion, the more that the Internet of Things phenomenon plays out, the greater the overall risk will be to our ability to provide more and more vital security, as well as business operations, if we do NOT share cyberthreat intelligence widely and rapidly between public and private organizations.
However, these gain/loss dynamics still represent a challenge and government is biased not to share, or at least not to share rapidly. So, it’s a GOOD THING that industry is increasingly doing this on its own.
Believe me when I say that there will always be plenty of challenges left for governments to tackle, so this shift only helps the overall team effort, and that’s why it’s an imperative for future cybersecurity success.
POLICY AND STRATEGY
Given that we have a greater and greater industry role in cyberthreat intelligence, what should we be doing about this?
At Palo Alto Networks, as in a growing number of other like-minded (yet competitor) companies, we believe we must share this intelligence as a public good, rather than hoard it as a commercial commodity. THIS IS A HUGE SHIFT!
I remember when I was in the special operations and information warfare communities during military operations in both Afghanistan and Iraq. In the early days, you may recall that we had a similar dynamic going on across the multi-agency and coalition efforts. We all knew bits and pieces, but we all had trouble “connecting the dots,” which was one of the key reasons that the 9/11 attacks happened in the United States.
Over time, we made a deliberate decision that we needed to move from a “need to know” basis for terrorist threat information-sharing toward a “need to share” basis so that, collectively, we could work in a more effective, integrated fashion.
It was very painful making this adjustment, and many organizations resisted due to both real and perceived risks (some still do today). However, this shift in mindset and policy began to show promise, and the gains turned out to be worth the risks in terms of success against terrorists on the battlefields of Iraq, Afghanistan and other key locations around the globe.
This is the same strategic dynamic for cyberthreat intelligence, though I must make the key distinction that we are NOT talking about surveillance-related intelligence about terrorists, but rather cyberthreat IOCs. There’s a huge distinction between the two that many tend to conflate in today’s “security versus privacy” debates.
Now, let me tell you the story of the Cyber Threat Alliance.
ORGANIZATION AND ARCHITECTURE
The Cyber Threat Alliance (CTA) is an example of shifting organizational structure from silos to partnerships. This is a story about eight companies – several of which compete with one or more of the others, including my own – that have put their money where their mouths are and actually organized to share cyberthreat intelligence.
To illustrate the example, I’ll use a recent Cyber Threat Alliance pilot project to show how the notion of organizing to share cyber threat intelligence can work.
First, some background: CryptoWall Version 3 is a form of ransomware, and has been recently used by a cyberthreat criminal entity to steal and encrypt an organization’s or individual’s sensitive information to hold it for ransom (usually through Bitcoin or other digital currency). If the ransom is not paid in accordance with the criminal entity’s demands, the information stolen and held for ransom is then destroyed.
The Cyber Threat Alliance utilized the collective intelligence and analytic resources from the four founding members (Palo Alto Networks, Intel® Security, Symantec™, and Fortinet®) and four other contributing members (Barracuda Networks, ReversingLabs, Telefonica, and zScaler) to publicly publish a report on October 29, 2015, titled “Lucrative Ransomware Attacks: Analysis of the CryptoWall Version 3 Threat.”
This was the first published report using combined threat research and intelligence from the founding and contributing members of the Cyber Threat Alliance. The report provided organizations worldwide with valuable insight into the attack lifecycle of this lucrative ransomware family. The Cyber Threat Alliance further discovered:
- The $325 million in revenue that went to the attackers included ransoms paid by victims to decrypt and access their files.
- 406,887 attempted CryptoWall infections.
- 4,046 malware samples.
- 839 command-and-control URLs for servers used by cybercriminals to send commands and receive data.
- The hundreds of millions of dollars in damages span hundreds of thousands of victims across the globe. North America was a particular target for most campaigns.
Although this example of an effective partnership for cyberthreat intelligence-sharing was just a pilot project to prove that competitor cybersecurity organizations could actually work together to bring down a single threat, it was also a powerful endorsement of the concept and demonstrated the organizational structure required for success. In fact, the quote below, from Rick Howard, Palo Alto Networks CSO, sums it up nicely:
“This type of collaborative research by security vendors reflects the power of effective threat information-sharing and the positive effect it can have on helping maintain trust in our digital world. As a founding CTA member, we are committed to the idea that this new way of working together – of combining intelligence on a common adversary and sharing cyberthreat information as a public good – is to the benefit of all organizations in the battle against cybercrime.”
There will be more research published this year from the CTA. This represents an imperative to move from our traditional, legacy approach of working in isolation toward real teamwork and effective partnerships.
This surely won’t be easy, and if the CEOs from the partner companies in the CTA had not personally been involved, this partnership would not be effective today. With leadership commitment, this demonstrates an organizational approach to a more successful cybersecurity future – one where various entities determine that there is an overall common objective, the achievement of which provides more overall good on balance than individual efforts that work against one another for a single organizational advantage.
TTP
In the Cyber Threat Alliance example that I just used, there were two tactical, more procedural issues that we learned were key to success.
First, let me remind you of the problem I covered in my first blog of the series about the lopsided advantage that the attacker currently has over the defender. Taking a page from our cyber adversaries, in terms of one of the key reasons for this imbalance, we need to take slow, human decision-making out of the equation, and automate everything we can to determine known bad IOCs in near-real time from unknown activity/techniques/signatures.
Cloud capabilities are key to success in automating this process, and the only real way to wipe away an estimated 80–90 percent of more routine cyberthreat activity so that we can use the human processes for the really sophisticated stuff.
Using the Cyber Threat Alliance again as an example, in order to join the Alliance, each company must contribute a minimum of one thousand unique malware signatures every day and must agree to automatically consume rapidly discovered known bad signatures from any of the other Alliance partners. They must also ingest the resulting protections into their own company’s defensive capabilities, systems and platforms.
This TTP produces a rapid self-learning capability. It also produces a self-healing fabric that stretches across all of the partner organizations’ information technology enterprises, and limits the cyberthreat level of success dramatically.
One of the other important TTP lessons coming from the Cyber Threat Alliance experience is that in order to become self-learning and self-healing at scale, you have to get away from ad hoc information transmission methods and move to a standardized format. Doing so enables the automation of information-sharing and cybersecurity platform adjustment at the same time and on a much broader scope and scale.
The standardized methods for automated cyberthreat information-sharing being explored by the U.S. government and other international organizations called STIX/TAXII may prove successful, but both public and private organizations, including the Cyber Threat Alliance, are working through which techniques and procedures help to best scale for success.
CONCLUSION
Cybersecurity success in the digital age requires that we leverage teamwork and partnerships in powerful new ways that we are only beginning to understand and implement.
Private industry has a growing, increasingly important and entirely appropriate role in cyberthreat analysis and intelligence. Governments simply cannot, and should not, be the only ones to cover the entire cyberthreat landscape. However, we must be clear and precise about what cyberthreat intelligence means in order to avoid the confusion between security and privacy. When it comes to cyberthreats, security IS privacy.
The need to share cyberthreat information is rapidly becoming rightfully viewed as a greater societal good, where the risks associated with arguments not to share widely and rapidly are becoming eclipsed by an overall growing threat to the trust we place in our digital way of life.
On balance, this imperative to share information about both cyberthreats and the associated protection mechanisms against them requires that we think differently about the way we organize so that we are optimized for a “need to share” culture. This will require strong leadership by example.
The imperative that we work together also requires using standardized, automated TTP for both sharing the critical information and for loading it into the defensive posture of our information technology enterprise in near-real time.
Taken together, these shifts regarding the role of industry in cyberthreat intelligence, in the policies that guide a culture of sharing threat information as a public good, in the way we organize to facilitate a “need to share” culture, and in the TTP we employ to standardize and automate information-sharing and mitigations all reinforce the imperative that we must work together. More importantly, they also contribute to our collective cybersecurity success in the digital age.