Our commitment to making prevention a core component of architecture is real. As such, we created a standard assessment methodology to help set expectations about prevention and create a prevention-based architecture strategy that builds alliances between IT and security professionals. Let’s talk about how to assess prevention readiness using that methodology.
The basis of our prevention posture assessment comes from two things:
- The cybersecurity community continues to amass a significant amount of intelligence and information about attackers. We know the tools, techniques, indicators of compromise, and vectors attackers used to successfully attack organizations. However, IT and security professionals lack the ability to actively defeat many of those things we know about the attackers and techniques.
- IT and security leaders tell us they’re not confident they know everything that is happening in their network.
General Sun Tzu, in 500 B.C, said the following:
“Know the enemy and know yourself; in a hundred battles, you will never be defeated. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are sure to be defeated in every battle.”
The General’s words are as true today as they were in his time. In addition, they are extremely relevant in the cyber domain. You must know the enemy and yourself to prevent successful attacks. We want to work with you in a way that allows you to know yourself so you can use what we know about the enemy to prevent successful attacks.
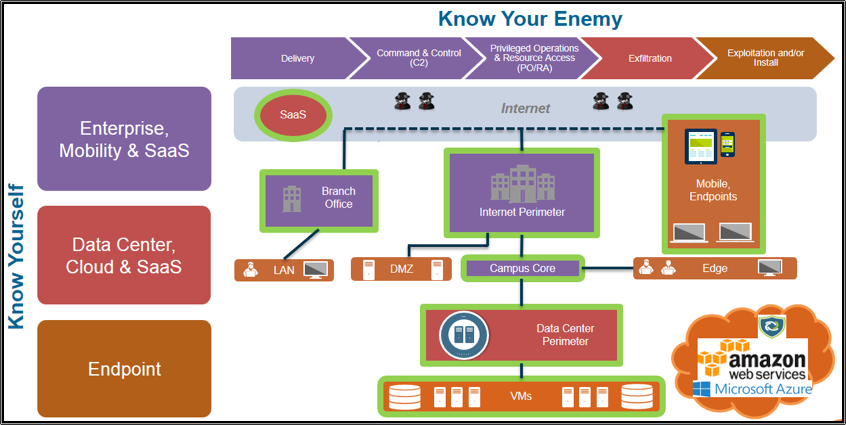
The figure below provides a visual about how we use the prevention-posture assessment to set expectations about prevention and create a prevention based architecture strategy with customers.
Figure 1: Prevention posture assessment
First, we separate architecture into three different areas, as shown on the left-hand side of Figure 1.
- Enterprise, mobility and SaaS
- Data center, cloud and SaaS
- Endpoint
In this way, we ensure the “know yourself” aspect or our methodology is consistent across all architecture. The separation of architecture is a deliberate action that ensures we distribute prevention capabilities across all architecture. In addition, the separation of architecture helps make the point that we need to work directly with both the IT architects and the security architects of an organization.
Second, we align the three different architecture areas with specific stages of the attack lifecycle. As Figure 1 shows, the colors in each area of the architecture align directly with specific stages of the attack:
Aligning the areas of architecture with stages of the attack lifecycle creates a compelling discussion about the difference a modern extensible approach to prevention makes for protecting organizations. In our approach, we drive home the need to position prevention capabilities across all three areas of architecture. In this way, we can actively defend ourselves by preventing what we know about attackers. At the same time, we maintain positive control that the enterprise is operating as intended, and we know everything happening in controlled environments.
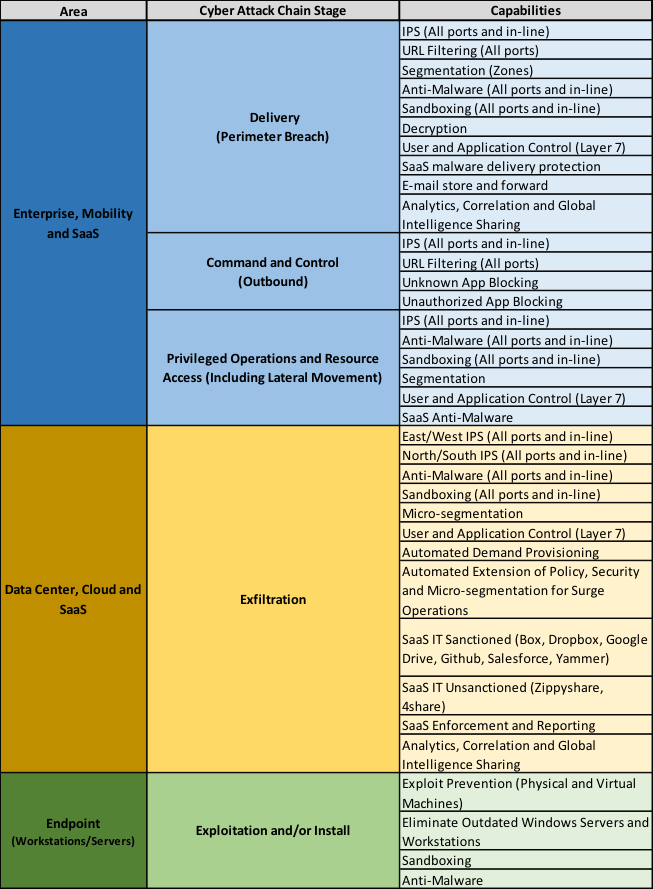
Figure 2: Prevention posture assessment capabilities
In Figure 2, we provide a list of the prevention capabilities assessed as part of the prevention posture assessment. As you read through the list, there are interesting items to note:
- The capabilities are redundant across areas of the architecture and stages of the attack. This is important because we must deliver prevention capabilities from the inside out rather than the way the status-quo hardens perimeters today.
- We don’t assess detect/respond capabilities, like IDS, because they are not prevention-focused. This is intentional. Frankly, we shouldn’t get “prevention readiness” credit for capabilities that don’t prevent.
- The prevention capabilities are all part of the “system-of-systems” Palo Alto Networks platform approach that is fully integrated. We set the expectation for all customers that they need to field all these capabilities to get the full value of their investment.
- The prevention capabilities are as relevant for IT infrastructure professionals as they are for security infrastructure professionals. For this reason, we always perform the assessment jointly with the IT and security architects.
In practice, we typically find that existing customers continue working to improve capabilities covering the Delivery and Command and Control stages of the attack. This makes sense given that the status-quo approaches emphasize hardening the perimeter. One exception for protecting against the Delivery and Command and Control stage, is that very few customers adequately protect SSL traffic. Today, it is common knowledge that threat actors take advantage of encrypted application traffic to deliver malware and control their attack. Since the amount of SSL traffic continues to grow in enterprises, customers must move deliberately to decrypt traffic and extend protection capabilities to eliminate blind areas.
In addition, we consistently see customers with immature and non-existent prevention capabilities covering the internal stages of the attack lifecycle. The limitations of extensible prevention capabilities across an architecture leaves us all at risk, and allows known attackers to move unmitigated throughout an enterprise.
Ultimately, it is your decision. A known attack methodology or technique is not advanced, and should be defeated using modern prevention capabilities. In this section, we discussed the capabilities we assess to prevent successful attacks. In the next section, we will discuss how we measure prevention capability readiness and our ability to build confidence that we know everything happening in a controlled enterprise.
Have you received your prevention posture assessment yet? If you're an existing customer, contact your our partner or local representative to request an assessment. If you're a potential customer, do the assessment with on of our representatives soon. The only cost is some time for your team, but it will be time well spent, as a leader.