Microsoft by the Numbers claims that Office has a staggering 1.2 billion users. Within this rather large number, users seem to be moving rapidly from traditional Office software to cloud-based Office 365. Microsoft’s latest earnings release revealed that the Office 365 consumer offering has 23.1 million subscribers. Subscriber numbers for the Office 365 commercial offering were not disclosed, but revenue for the commercial offering increased 54 percent.
We hear from many of our own enterprise customers that enabling and securing Office 365 is one of their strategic initiatives. The security implications of these initiatives are often not clearly understood, but the following are examples of what often gets discussed among IT teams as well as in the boardroom:
- We have an enterprise account with Office 365, but users also have their own personal accounts. How do we make sure that our sensitive data doesn’t end up in our users’ personal accounts?
- Our partners have enterprise accounts with Office 365. This is great for collaboration but how do we enable this collaboration securely, for example, by allowing access only to sanctioned Office 365 accounts?
If you are a customer of Palo Alto Networks and are dealing with such a project in your organization, rest easy. After reading this blog post, you will understand Office 365 access use cases, identify one that you want to start with, and know what resources to use to implement that use case.
What are consumer Office 365 accounts, and how do they differ from enterprise Office 365 accounts?
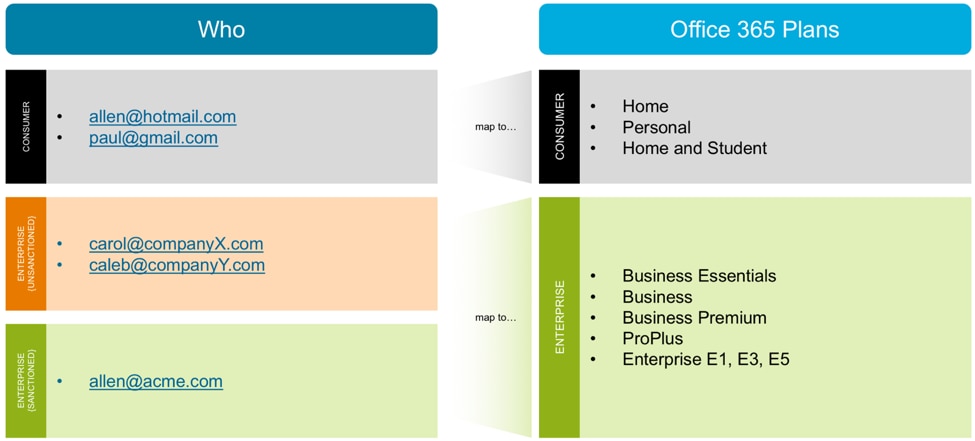
Microsoft offers many different types of Office 365 accounts, or what it calls “Plans.” These Plans are divided into two main categories, which we will call Consumer and Enterprise.
The Consumer category contains the following plans, described by Microsoft on its Office products page:
- Home
- Personal
- Home and Student
These are the accounts that you or I would buy for our personal use. We typically use our personal email addresses like @hotmail.com or @gmail.com to create these types of accounts.
The Enterprise category contains the following plans, described on this Office 365 business plans page and this Office 365 enterprise plans page:
- Business Essentials
- Business
- Business Premium
- ProPlus
- Enterprise E1, E3 and E5
These plans are bought by organizations typically with organizational email addresses, for example, @acme.com or @mycompany.org.
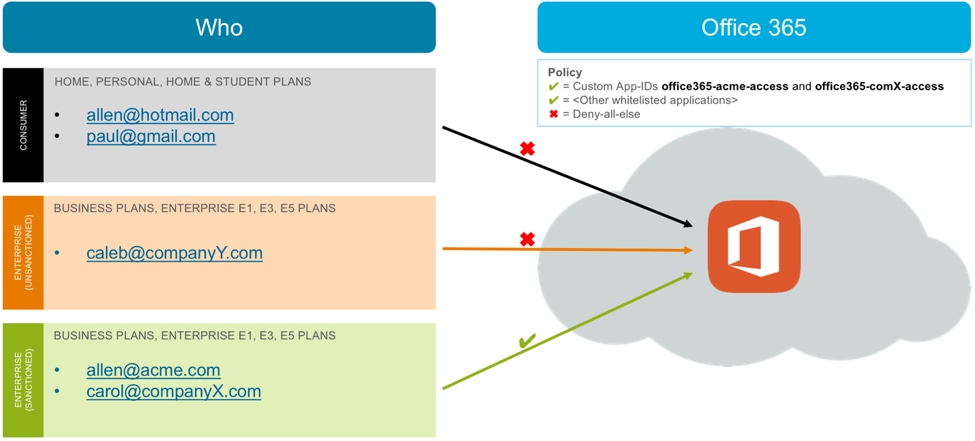
Chances are that your users access both Consumer and Enterprise types of accounts from your network. Some of the Enterprise accounts may be sanctioned, while others may be unsanctioned. Figure 1 shows an example scenario:
Figure 1: Consumer and Enterprise Office 365 account types (Microsoft calls them Office 365 Plans)
Here are the most common use cases that we hear from our customers for creating access policies for different types of Office 365 accounts.
Use Case 1: What is the usage of Office 365 in our organization? And what is the breakup of traffic destined to enterprise versus consumer accounts?
Many organizations don’t yet have a detailed and clear business policy for controlling Office 365 access. If your organization is in this camp, start by understanding the usage, and then share the information with other leaders in the organization. This visibility will help your organization’s leaders create a business policy for controlling Office 365 access.
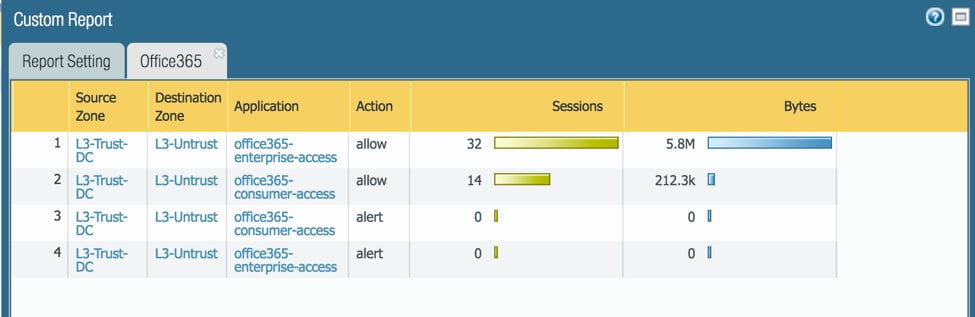
Figure 2 shows a sample report with Office 365 usage and its breakup into Consumer and Enterprise account types (see the column called “Application”).
Figure 2: Report showing Office 365 access and its breakdown into Consumer and Enterprise
Use Case 2: Let’s catch the low-hanging fruit first – block access to Consumer Office 365 accounts.
Users log in to their Consumer accounts from work for many reasons: to access their personal documents at work, to share documents with business partners, or they just find it easier to use the same account at home and at work. But allowing these Consumer accounts introduces risks, for example, the risk of data loss or the risk of downloading an infected document. That’s why many of our customers start by blocking access to these Consumer accounts.
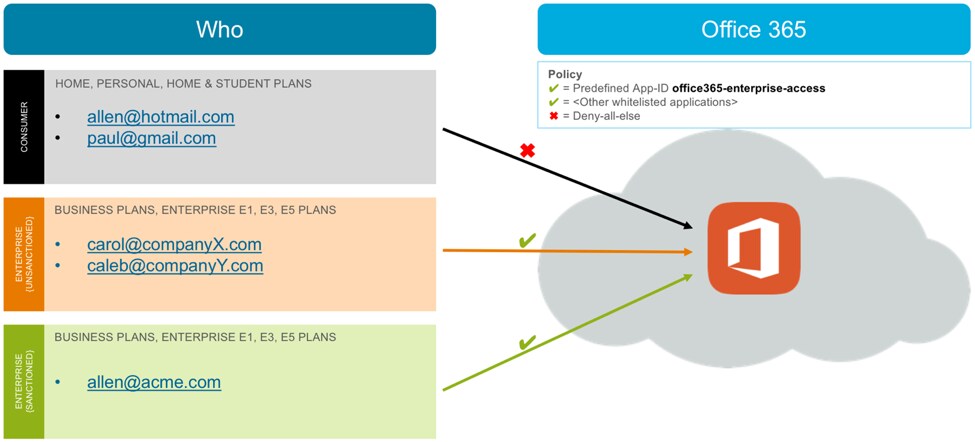
I recommend you first educate your users about what you plan to do, the rationale behind it, and your timelines. Then implement your security rule to allow access only to Enterprise accounts, as shown in Figure 3.
Figure 3: Block access to Consumer Office 365 accounts
Use Case 3: Let’s allow access to our own Enterprise account and block access to all other Enterprise and Consumer accounts.
This use case is relevant for an organization that doesn’t need to allow partner or subsidiary employees access to their respective Enterprise accounts and simply needs to enable its own employees.
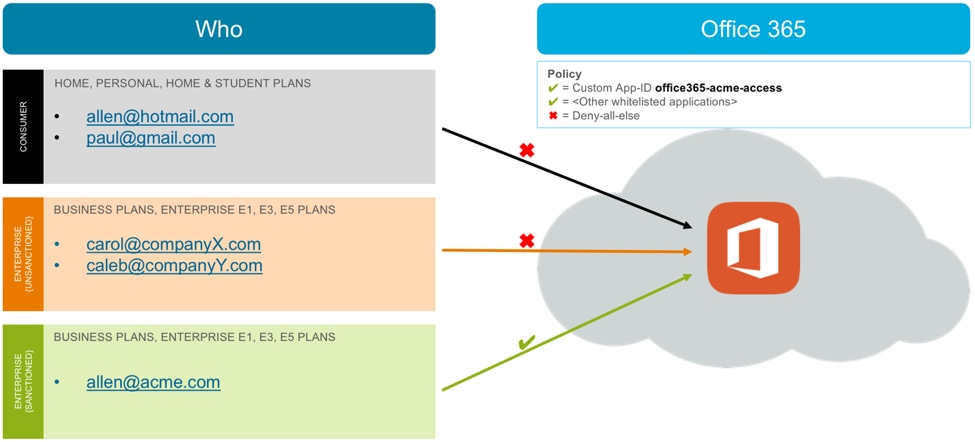
If your organization’s policy matches this use case, create a custom App-ID based on your organization’s domain. Allow access to this custom App-ID in your security rules, as shown in Figure 4.
Figure 4: Allow access to your own Enterprise account, and block access to all other Enterprise and Consumer accounts
In this example scenario, traffic destined to CompanyX and CompanyY Office 365 accounts will not match any allow rule and therefore will be denied by the default deny-all rule.
Use Case 4: We have a list of sanctioned Enterprise accounts, which includes our partners and subsidiary companies. Let’s allow access to these accounts and block all other unsanctioned Enterprise and Consumer accounts.
Often your partner employees, affiliate employees or subsidiary employees use your network and need access to their own respective Enterprise accounts. If you belong to such an organization, you will want to allow access to all sanctioned Enterprise accounts, including your own account. Before implementing this access policy, I recommend vetting this partner’s security practices and obtaining agreement from your security, HR and Legal teams.
To address this use case, add a custom App-ID for each sanctioned domain and use these App-IDs in your security rule as shown in Figure 5.
Figure 5: Allow all sanctioned Enterprise accounts
In this scenario, Acme’s own Enterprise account (for example, the account associated with the user allen@acme.com) and CompanyX’s Enterprise account (for example, the account associated with the user carol@companyX.com) are considered sanctioned Enterprise accounts. Access to these accounts is allowed via custom App-IDs.
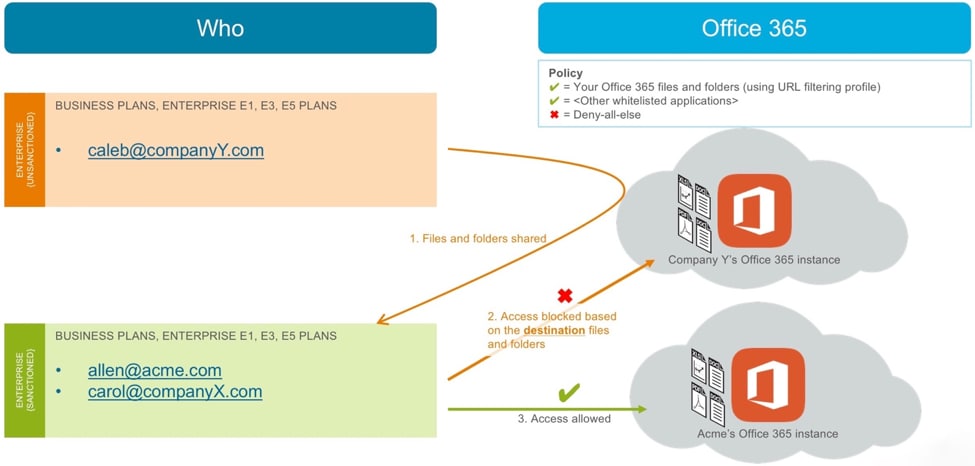
Use Case 5: We have allowed our employees, partners and subsidiaries access to their respective Enterprise accounts. But we still have a problem – our users are able to get to any shared files and folders – no matter in which account these files reside. We need to lock down access to shared files and folders.
App-ID rules identify the Office 365 accounts based on the source email address. For example, a user with @acme.com email address is tied to Acme.com’s Office 365 account. This is consistent with how Office 365 identifies users and ties them to their account.
Once sanctioned users are allowed to access Office 365 based on their email address, they can access Office 365 files and folders – those located in their own accounts, as well as those shared with them. This type of access can result in the downloading of infected files or uploading of sensitive data to shared folders.
To restrict access to shared files and folders, create a URL filtering profile and use it in an allow rule. Figure 6 shows how such a scenario works.
Figure 6: Specify File and Folder Access
In this scenario, someone from CompanyY shares files and folders with an employee (allen@acme.com) and a sanctioned partner (carol@companyX.com). Both of these users are allowed access to Office 365. When these users access CompanyY’s shared files and folders, the URL filtering profile blocks access because the destination files and folders are located in an unsanctioned Office 365 instance. They can continue to access files and folders in sanctioned accounts, like Acme’s own account.
Use Case 6: App-ID is fantastic! It secures all Office 365 traffic, right? Or do I need to think about any other use cases?
App-ID gives you a wide range of controls to secure Office 365, as we have discussed in the last several use cases. However, for complete visibility and control over Office 365 traffic, including visibility into past data that was uploaded even before the App-ID controls were put in place, Palo Alto Networks provides Aperture, which connects directly to Office 365 using the Office 365 API.
Here are some additional use cases that Aperture can help you with:
- Preventing accidental data exposure: Marty, a user in your organization, copies a sensitive file to a new folder in order to share it with a colleague. He does not realize though that the folder is accessible to the public, not just to people in your organization. But Aperture analyzes files in all publicly shared folders and enforces your organization’s policy by removing public sharing from that folder.
- Preventing malicious exfiltration: Neil is planning to resign because he did not get the promotion he was expecting. He adds his personal email address as an authorized user to the organization’s customer information folder in OneDrive. This will allow him to retain access to the folder even after he is removed from the corporate user directory. But Aperture analyzes all authorized users on your OneDrive and enforces your organization’s policy by removing personal email addresses.
Palo Alto Networks next-generation firewalls give you the ability to safely enable access to Office 365 with appropriate control. With the latest App-ID enhancements, you can:
- Enable access to Enterprise Office 365 account types while blocking access to Consumer account types.
- Enable access to sanctioned Office 365 accounts, for example, your own account and approved partner and subsidiary accounts.
- Allow users to share files and folders that are hosted on a verified and limited set of Enterprise accounts, for example, your own account and subsidiary accounts.
How do I get started with implementation?
- Step 1: Use this blog post to understand different Office 365 access use cases and to identify the use case that you want to implement first.
- Step 2: Use the following resources to implement the chosen use case:
- Step 3: Learn more about Aperture for complete Office 365 security.
Additional Resources
- App-ID Tech Brief (white paper)
- Safely Enable Office 365 (white paper)
- Securing Office 365 (lightboard video)
- Register for the “Let Application Controls Do Their Job and Prevent Breaches” webinar on June 6, 2017