Network security management tools should make your life easier. Panorama network security management is intelligent, fast, and plugs into your security ecosystem via application programming interfaces (APIs). It does the heavy lifting of correlating indicators of compromise across millions of log lines obtained from next-generation firewalls and endpoints; takes automated actions that you have pre-programmed; and ultimately gives you the information you need to act upon.
Introducing Panorama 8.0
As part of our recent PAN-OS 8.0 release, there are three new features introduced in our latest version of Panorama that will make your job easier.
- More data sources for greater visibility. Panorama now ingests logs from the next-generation firewalls, as well as Traps advanced endpoint protection. But what’s the point of more data if it can’t be converted into useful, actionable information? Panorama’s unique automated correlation engine processes all the data that it receives, scrutinizes security events that may appear isolated, and queries the data for specific patterns including ones defined by our Unit 42 threat intelligence team. The analysis provides you with the kind of information you are interested in. For example, by analyzing exploit prevention events on the endpoint with threat information received from WildFire, the correlation engine can tie together disparate indicators of compromise and point out which endpoints are infected, if any.
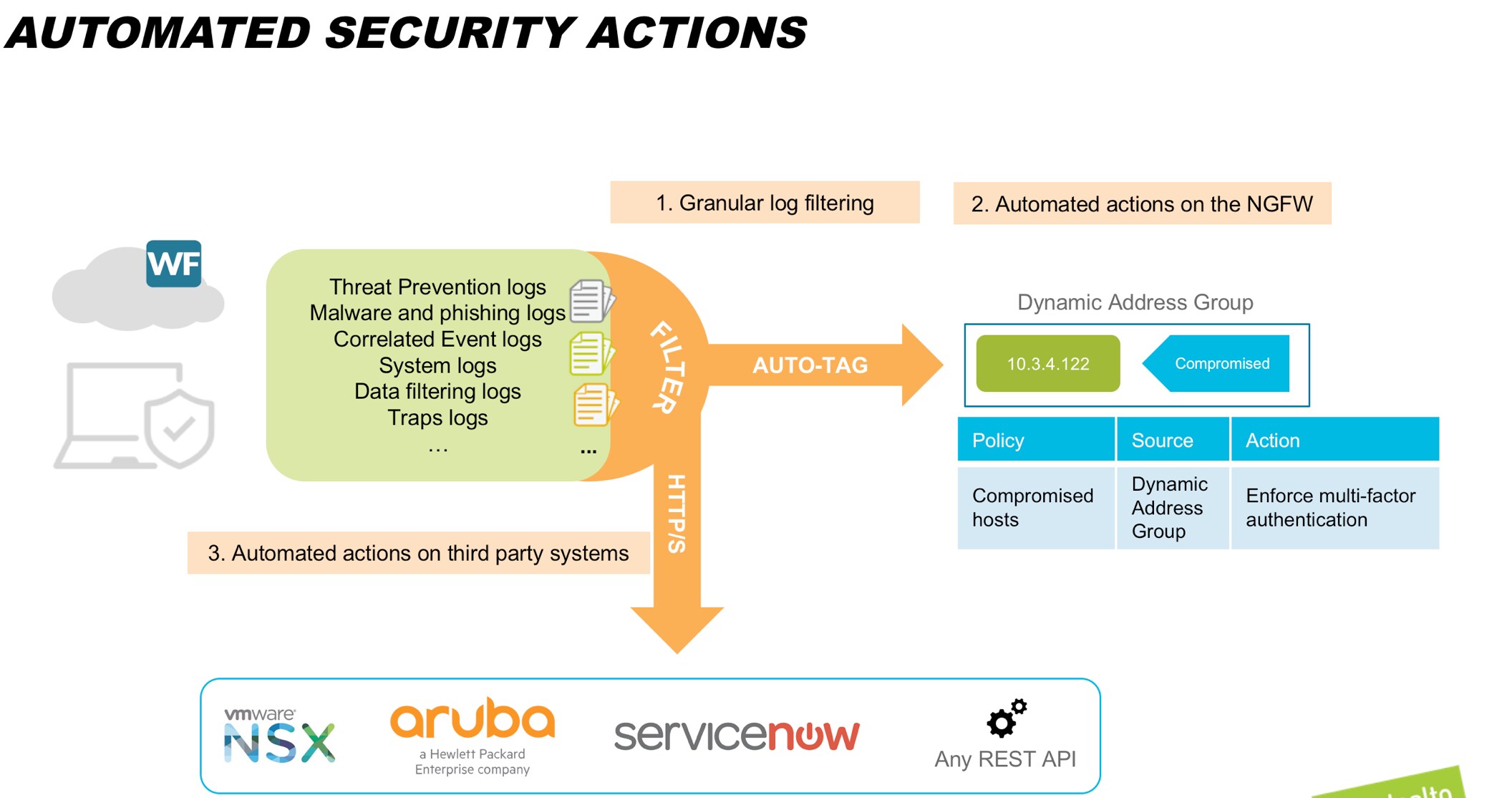
- Automated actions triggered on filtered events. As an administrator, you get inundated with events, events and more events. How do you know what to act on? This onslaught of events lets malicious events go unnoticed. Our approach is different. Panorama can define what kinds of events should be forwarded to specific teams. For example, the Security Operations Team may choose to receive only the high-priority malware and phishing-related events. This personalized event filter lets you analyze and act upon information relevant to your role. And that’s not all. Panorama also allows you to automate tasks. You can program appropriate events to trigger a workflow on any part of your security ecosystem that accepts an HTTP/S call, for example, a ticketing service.
- Granular change management for multi-admin teams. Often multiple administrators manage network security. And they need to make changes and commit them independent of other teams. Panorama enables administrators to do this. Let’s say that you are a security administrator and need to make an urgent, high-priority change to the security rules on the firewall. But you realize that the network team is making changes to the firewall’s VPN rules, which they need to test and verify before they roll them out. You can’t wait for them to complete their testing since your time window is much shorter. Panorama allows you to commit and revert your changes independent of other teams. You can commit your changes without affecting the network team’s changes. This frees you up from doing an offline coordination with other teams for commit and revert.
Making You More Secure: A Real-World Example
Let’s say that one of your endpoints, which does not have Traps installed, receives an exploit attempt through a new file that a user just downloaded. Imagine that this is a previously unknown threat, so the file gets sent to WildFire, our threat intelligence cloud. WildFire executes the file in the cloud, then concludes that it is malicious. It immediately creates signatures to catch this new malware and distributes it globally to all Palo Alto Networks Next-Generation Firewalls.
But what about the endpoint that received the exploit attempt? Since the endpoint does not have Traps installed, the file executes and the exploit attempt is successful. The endpoint attempts to make a command-and-control (C2) callback and is blocked by the firewall. When Panorama analyzes logs, the automated correlation engine inspects the data and finds a match between the attempted C2 activity on the endpoint and the malicious behavior that the file showed in WildFire. Based on this match, it now concludes that this is an infected host.
This information alone is extremely valuable to a security administrator. But Panorama goes beyond just highlighting the information. With the 8.0 release, Panorama can look at the source IP address in the log, and auto-tag it with a predefined tag, for example, “Compromised.” The next-generation firewall can be configured to place all IP addresses that are tagged “Compromised” in the appropriate dynamic address group, and apply your chosen policy on the group, for example, to block the traffic or enforce multi-factor authentication for these endpoints. All of this occurs without any manual intervention. As attacks become more and more automated, replacing manual intervention with automated actions is the only way to scale your team to effectively defend against them.
Now if the user at this endpoint is a malicious actor, the multi-factor authentication challenge blocks his attempt to move laterally within your network, which protects your sensitive data. On the other hand, if this is a legitimate user, he or she may get surprised with the multi-factor authentication challenge, and may deny the second factor authentication. If the adversary continues to attempt to move laterally or the user continues to deny the second factor, Panorama can automatically block the IP and log a service ticket. Remember the automatic triggering of actions from Panorama described in point #3 above? This capability comes in handy now. Panorama can use the HTTPS API exposed by your ServiceNow ticketing system to create a ticket so that the Operations team is aware of this action on the endpoint. They can then investigate the incident, remediate the endpoint if needed, and release it from the more stringent security policy.
See Figure 1 below for a depiction of this real-world scenario.
But Wait…Panorama 8.0 Offers Much, Much More
Available either as a dedicated management appliance or as a virtual machine, Panorama 8.0 enables organizations to manage their distributed network of Palo Alto Networks Next-Generation Firewalls from one central location – easily and intelligently. Here’s a complete list of features introduced in Panorama 8.0.
| More data sources for greater visibility, plus faster access | Improved Visibility |
| Vastly improved querying and reporting engine | ACC enhancements for SaaS visibility and interactivity |
| Up to 24TB of RAID storage per M-500 | ACC customization and collaboration improvements: default tab, share tabs |
| Up to 48TB storage for an HA-pair VM | Visibility for de-capsulated tunneled traffic |
| Log forwarding from PA-7000 Series to Panorama | Other features |
| Ingestion of Traps logs into Panorama | Admin-based commits |
| Automated actions triggered on filtered events | NetFlow support in PA-7000 Series |
| Filtered log forwarding | M-Series expanded multi-interface support |
| HTTP-based log forwarding to third-party systems | Plug-in architecture for external integrations |
| Auto-tagging of source/destination IPs | SNMP MIB for device log forwarding and support for HA2 interface |
To learn more, check out the following resources: