The shift to the public cloud has offered organizations increased agility, flexibility and scalability. However, as more and more organizations move critical workloads to the public cloud, the potential for attackers to steal data, intellectual property or computing resources also rises.
Below is a brief breakdown of three considerations for securing public cloud workloads. Download the white paper to view the detailed list of all 10 top considerations.
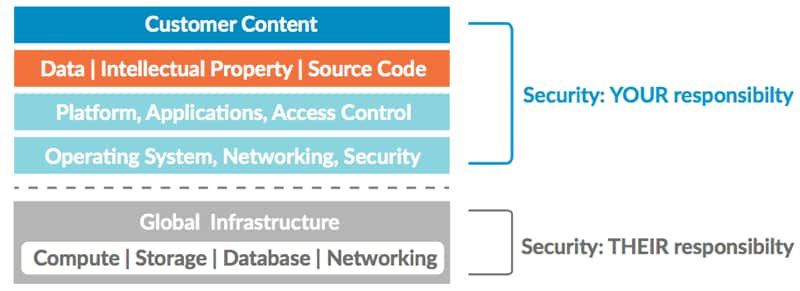
- Embrace the shared security model: The infrastructure is secured by the cloud service provider, but users are responsible for securing their own applications and
![Cloudworkflows]() data as it resides in the cloud. With this in mind, security practices must be implemented to secure workloads in the cloud as well as prevent loss of data and IP, just as if the workloads were on-premise.
data as it resides in the cloud. With this in mind, security practices must be implemented to secure workloads in the cloud as well as prevent loss of data and IP, just as if the workloads were on-premise. - Engage with business groups and DevOps early: Security teams and respective business groups, such as DevOps, should work collectively – particularly during initial stages of public cloud projects – to ensure all development needs are met while still maintaining a healthy security posture.
- Know your potential exposure: Monitor public cloud usage, ensure proper configuration of the environment, enforce two-factor authentication, and properly lock down Secure Shell (SSH) access to gain visibility and minimize potential exposure through “shadow IT.”
Read the full list of our Top 10 Considerations for Securing Public Cloud Workloads.
 data as it resides in the cloud. With this in mind, security practices must be implemented to secure workloads in the cloud as well as prevent loss of data and IP, just as if the workloads were on-premise.
data as it resides in the cloud. With this in mind, security practices must be implemented to secure workloads in the cloud as well as prevent loss of data and IP, just as if the workloads were on-premise.