Overview of the Black Hat NOC
In the beginning of December, Palo Alto Networks participated in the Black Hat Network Operations Center (NOC) in London as the official network security platform provider. The team included systems engineers and consulting engineers with the aim of not only protecting the network but actively monitoring and collaborating with other participating network and security vendors as well. These vendors included those that provide substantial contributions to the Cyber Threat Alliance of which Palo Alto Networks is a founding member.
In this blog post, we’ll provide an overview on how the Palo Alto Networks NGFW was utilized for the Black Hat Europe event and also discuss our findings of the types of malware that were trending this holiday season.

Coverage
While setting up for the week, the team looked to implement best practice configuration for all stages of the attack lifecycle to ensure complete understanding of threats and visibility of traffic. We needed to be able to quickly and easily determine what was just a classroom module malware drop versus a genuine attack on the network.
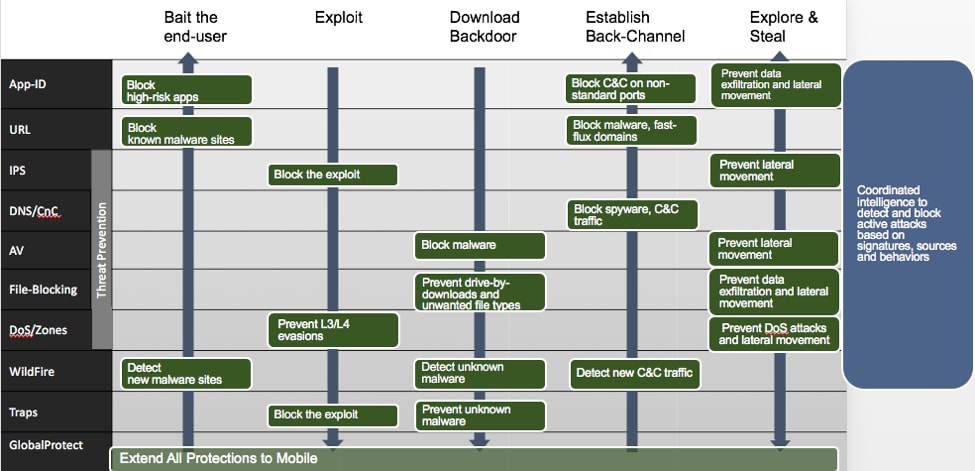
Each stage offering context in a single platform
Building further context into the traffic is always key, so the team cleverly utilized the XML API, whereby the hostname and/or MAC address related to a DHCP-allocated IP address were fed in to the User-ID database and kept automatically updated. This proved invaluable, allowing identification of the users at the root of the incidents, rather than simply their IP address, highlighting repeat offenders (some of which were actually unsuspecting victims) over the duration of the event.
As more teams are benefiting from the context provided by Palo Alto Networks correlation, a byproduct is more firewall user access being required. To mitigate this, we teamed up with RSA to utilize their Secure-ID MFA for RBAC. Role-based administration delegates feature-level access, including availability of data (enabled, read-only, or disabled and hidden from view), to distinct device users. Individuals can be given access to tasks that are pertinent to their job, but no more than that.
While we provide always-on, Layer 7 inspection with predictable, reliable performance, we are proud to report that not only did the Black Hat NOC team achieve 100 percent uptime but the team was able to showcase integrated technology, information sharing and adaptability executing a complex configuration.
Compromise
Early into the week, the Black Hat NOC team noticed distinct and peculiar network behavior from a single host. The host was phoning home in a series to a specific set of subdomains. The callouts on these subdomains were sandwiched between URLs that contained random characters.
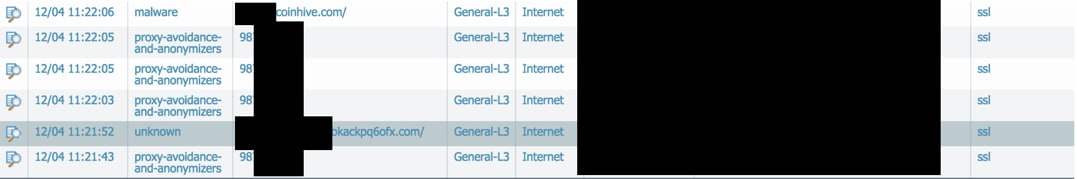
With these indicators of compromise, the team was able to collaborate and associate the data with RSA and Cisco. The final outcome of this investigation was that the host had been compromised via a browser hijack, and the host’s resources were being used for crypto mining, which you can learn more about from Unit 42.
The day after the crypto-mining incident, we noted several critical severity C2 detections in the threat log for Sofacy-related C2 traffic.
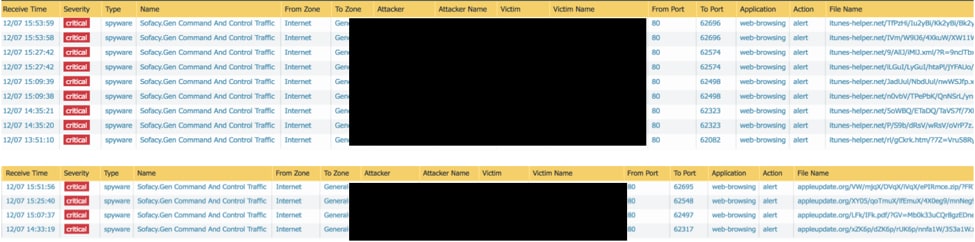
As shown above, destination URLs for the C2 communications were listed in the threat log as hxxp://itunes-helper[.]net and hxxp://appleupdate[.]org.
To validate and further analyze the context of the threat, we pivoted from the Next-Generation Firewall threat log to AutoFocus. This allowed us to search WildFire data for samples seen to be accessing these domains.
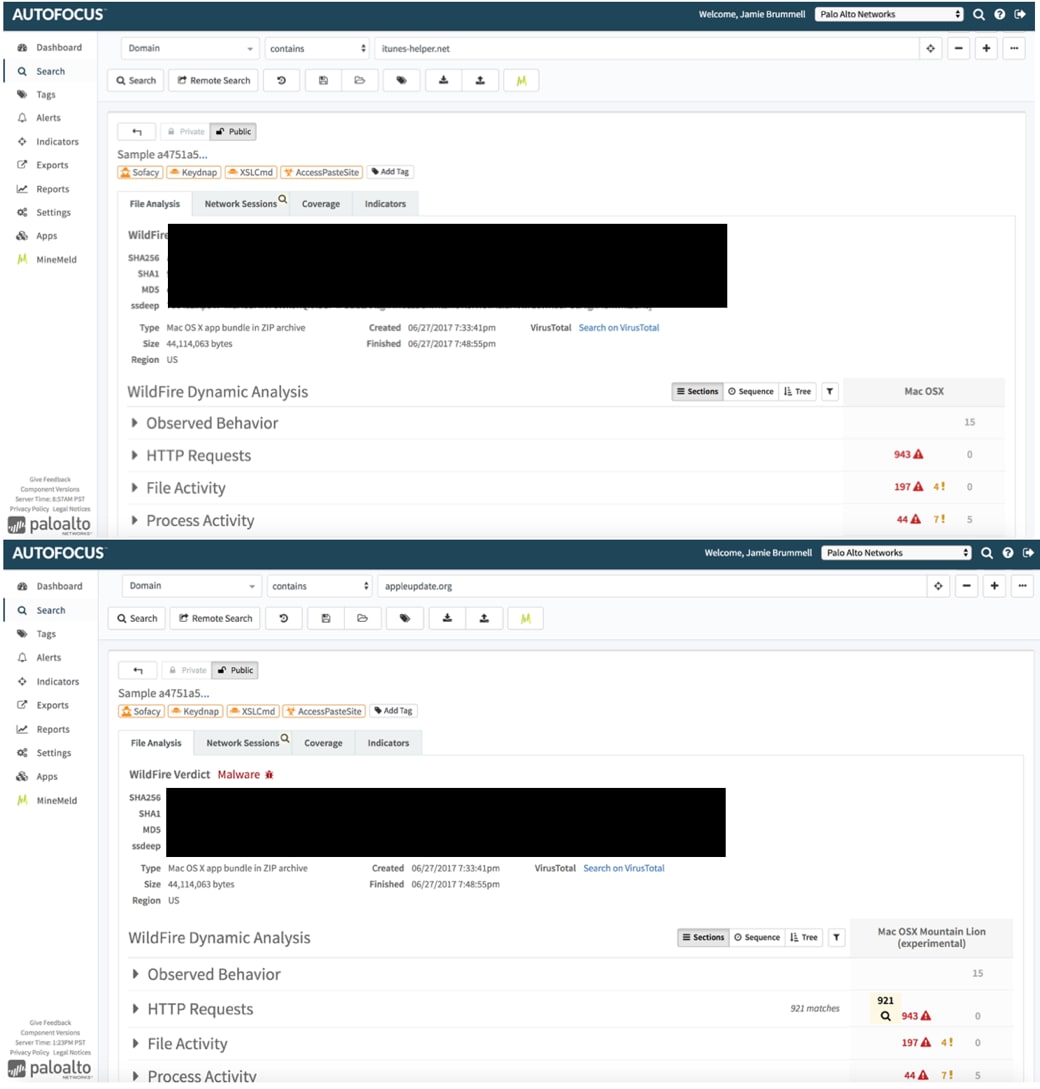
Samples were found in AutoFocus, validating that these domains are used in Sofacy (aka Fancy Bear/APT 28) campaigns. We were able to reference Unit 42’s blog post detailing the Sofacy group and related Komplex OS X malware, and the domains we saw in our C2 logs matched up with domains detailed in the blog.
We worked with the RSA team to further validate that it was indeed a Komplex Trojan infection based on their full packet captures.
Summary
Being placed in a purpose-built, hostile environment not only challenged the teams to think outside the box but also encouraged collaboration among the security vendors present at the event. The team not only worked in an operational capacity but was able to provide enriched context and value in incident response by incorporating the entire platform in the environment.
These types of experiences are an absolute privilege and a challenge that is most welcome. This is the Palo Alto Network’s Black Hat NOC team signing off and wishing you a Happy New Year!