One of three articles in a series about the VM-Series on: Google, AWS and Azure.
Organizations are adopting Google Cloud Platform to take advantage of the same technologies that drive the commonly used Google search engine and maps services. Business initiatives – such as big data, analytics and machine learning – deployed on GCP can leverage contextual data collected from billions of Google search engine data points. GCP offers a global footprint to allow you to quickly deploy enterprise-class applications and services.
Our VM-Series, deployed to protect workloads within a Google project, helps customers address their role in the shared responsibility model. GCP was designed with security as a core component and uses a variety of technologies and processes to secure information stored on Google servers. However, Google is very clear on where their security responsibilities end, and where the customer’s security responsibilities begin. As shown below, it is the customer’s responsibility to protect their operating systems packages and the applications they deploy.
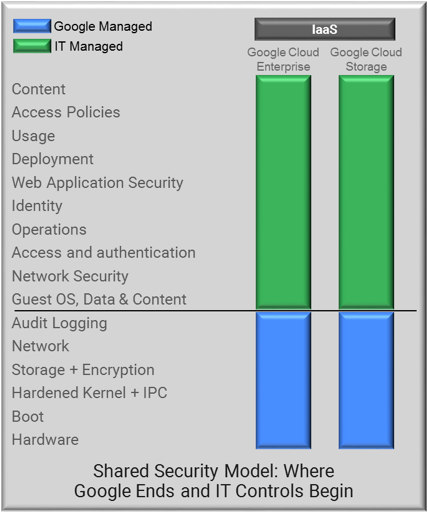
Figure 1: GCP Shared Responsibility Model
That’s where the VM-Series on GCP, which we officially announced this month, can help. It complements Google Firewall by protecting your applications and data using a prevention-based approach:
- Complete visibility and control: The VM-Series gives you complete visibility into the applications traversing your cloud deployment and the content within, malicious or otherwise. This knowledge allows you to deploy a more consistent, stronger security policy for inbound and outbound traffic to prevent known and unknown attacks.
- Reduce the attack surface; limit data exfiltration: Using the application identity as a means of enforcing a positive security model reduces the attack surface by enabling only allowed applications and denying all else. Application usage can be aligned with business needs, extending to application functions as needed (e.g., allow SharePoint documents for all but limit SharePoint administration access to the IT group). In addition to controlling applications, policies can be enabled to block or generate alerts on file and data transfers, thereby limiting data exfiltration.
- Prevent known and unknown threats: Applying application-specific threat prevention policies to allowed traffic can block known threats, including vulnerability exploits, malware, and malware-generated command-and-control traffic. Unknown and potentially malicious files are analyzed based on hundreds of behaviors. If a file is deemed malicious, a prevention mechanism is delivered in as few as five minutes. Following delivery, the information gained from file analysis is used to continually improve all other prevention capabilities.
To help eliminate security as a possible bottleneck, bootstrapping, the XML API and other VM-Series automation features, combined with GCP or Terraform templates, will allow you to embed next-generation security into your application development lifecycle. The VM-Series on GCP will be available in March 2018.
Learn More
Watch the VM-Series on Google Cloud Platform Lightboard
Read the VM-Series on Google Cloud Platform Deployment Guidelines
Visit the VM-Series on Google Cloud Platform resource page
