
On Dec. 13, the world learned of the now-infamous SolarWinds supply chain attack. The “SolarStorm” threat group infected countless SolarWinds Orion servers with a Trojanized DLL file and eluded detection for months.
While organizations chase down their SolarWinds servers and investigate the impact of the attack, it’s important to prepare more broadly for what inevitably comes next. An attack of this level of sophistication, conducted by suspected nation-state operators, highlights a set of tactics, techniques and procedures (TTPs). It’s only a matter of time before copycats reverse-engineer and reuse elements of the attack. In addition, the original threat actors behind the attack will undoubtedly update their methods, changing not only indicators of compromise (IOCs) like domain names, but also adversary tactics and tools to evade security controls. Protecting against these unavoidable threats requires a robust and layered defense.
Across our product portfolio, Palo Alto Networks deployed updates to help customers protect against the SolarStorm attack. In this post, we will specifically highlight the updates to our Cortex XDR product that helps SOC teams in the front lines defend against not just the SolarStorm attack but also SolarStorm variants and imitators. The key principle in defeating advanced adversaries is to continuously improve realtime prevention capabilities, and to give teams the right set of tools to detect and hunt threats down fast. By combining multiple layers of defense, from prevention to detection, investigation and response, Cortex XDR helps SOC teams fend off the risk of intrusion at every step.
Here’s what we’ve added to help protect security teams.
Block Threats in Realtime With Fortified Endpoint Protection
Realtime prevention is the first line of defense in any proactive security strategy. When Palo Alto Networks experienced an attempt to download Cobalt Strike on one of our IT SolarWinds servers, Cortex XDR successfully prevented the SolarStorm attack by blocking the attempt with our Behavioral Threat Protection capability.
Further analyzing the behaviors associated with the recent attacks, our XDR research team have developed additional protections in the Cortex XDR agent to help keep our customers safe from the SolarStorm group and its imitators. Specifically, we have:
- Introduced new Behavioral Threat Protection rules that identify the unique behaviors of the SUNBURST backdoor file and other malicious DLL files used in the attack.
- Updated our machine learning models for our local analysis engine by including the malicious files in our training database and allowing the models to extract attributes similar to the Trojanized DLL files.
- Added new child process protection rules to prevent legitimate applications from running malicious code identified in the SolarStorm attack.
In addition, the WildFire malware analysis engine has been updated to block the SUNBURST backdoor files and Cobalt Strike BEACON files associated with SolarStorm. The Cortex XDR agent integrates with WildFire for cloud-based analysis of files.
Detect and Hunt Down Intrusions in Near Realtime
In addition to the prevention controls outlined above, Cortex XDR now includes a comprehensive set of queries in the XQL query library to help hunt down intrusions that bypass prevention controls. Because the SolarStorm threat group targeted the Azure Active Directory (AD) service and attempted to read emails, the queries also identify Azure AD and email-based threats. These queries empower threat hunters to find:
- All endpoints with SolarWinds software installed.
- SolarWinds-infected processes that drop an executable, connect to a non-SolarWinds domain, create or modify a service, or conduct other malicious activity.
- Changes to Azure AD authentication settings, such as disabling single sign-on, adding unverified domains or modifying domain certificates.
- Azure tenants that were granted access to an Azure AD application.
- New or updated Azure AD service accounts.
- New mail read permissions added to a user account.
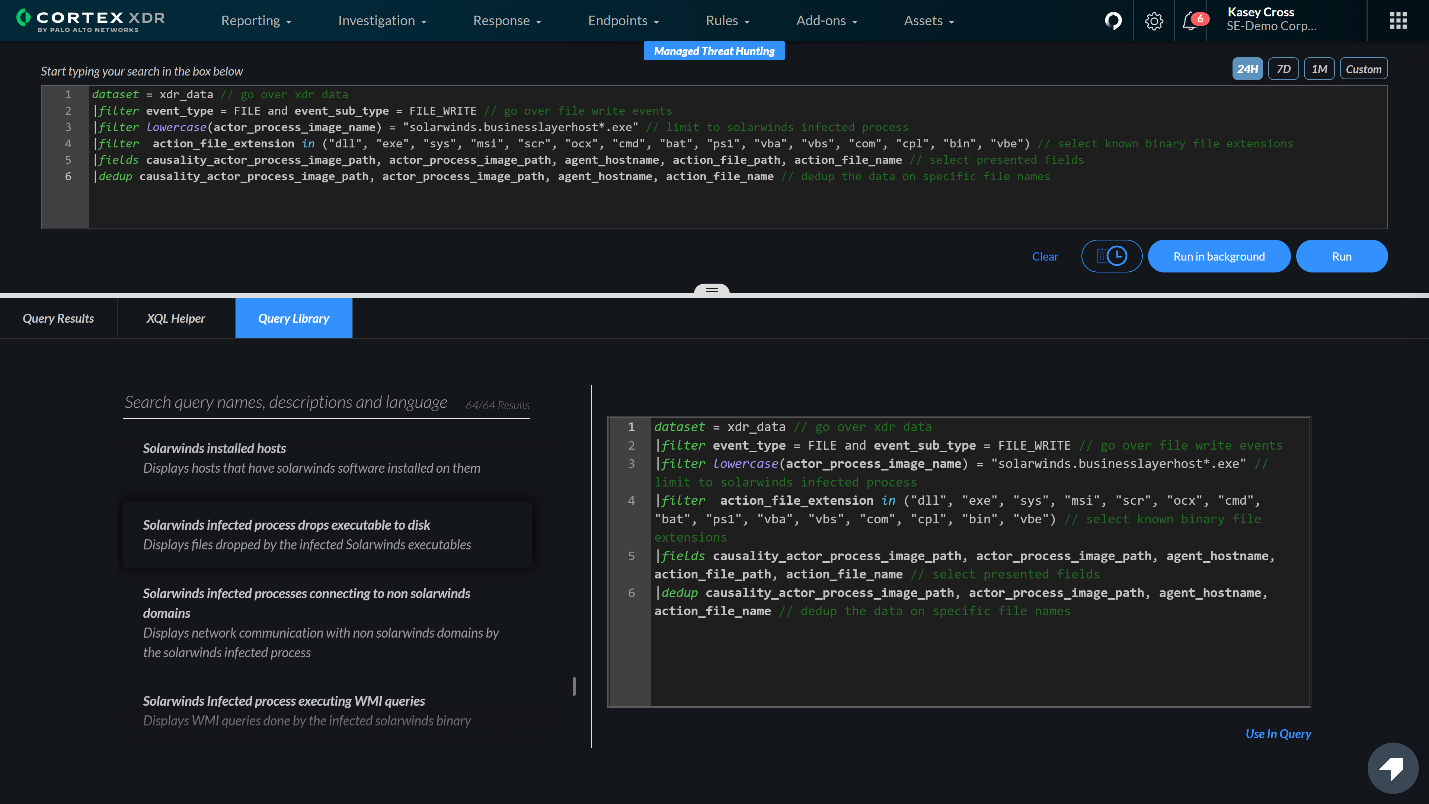
In addition to the queries that expedite threat hunting, a number of detectors were incorporated into Cortex XDR to automatically detect behaviors associated with SolarStorm TTPs that may be deployed by a broader group of adversaries. These automated alerts include:
- Domain federation settings that have been modified.
- Unverified domains added to Azure AD.
- IOCs associated with the SolarStorm attack.
The first two detection rules uncover attempts to compromise authentication controls by analyzing Azure AD audit logs. Since Active Directory is a top target for cunning adversaries the world over, these rules protect against any threat groups deploying such techniques. These rules, combined with Cortex XDR’s extensive behavioral analytics capabilities, will rapidly detect anomalies in post-intrusion stages of attacks, including credential abuse, lateral movement and exfiltration.
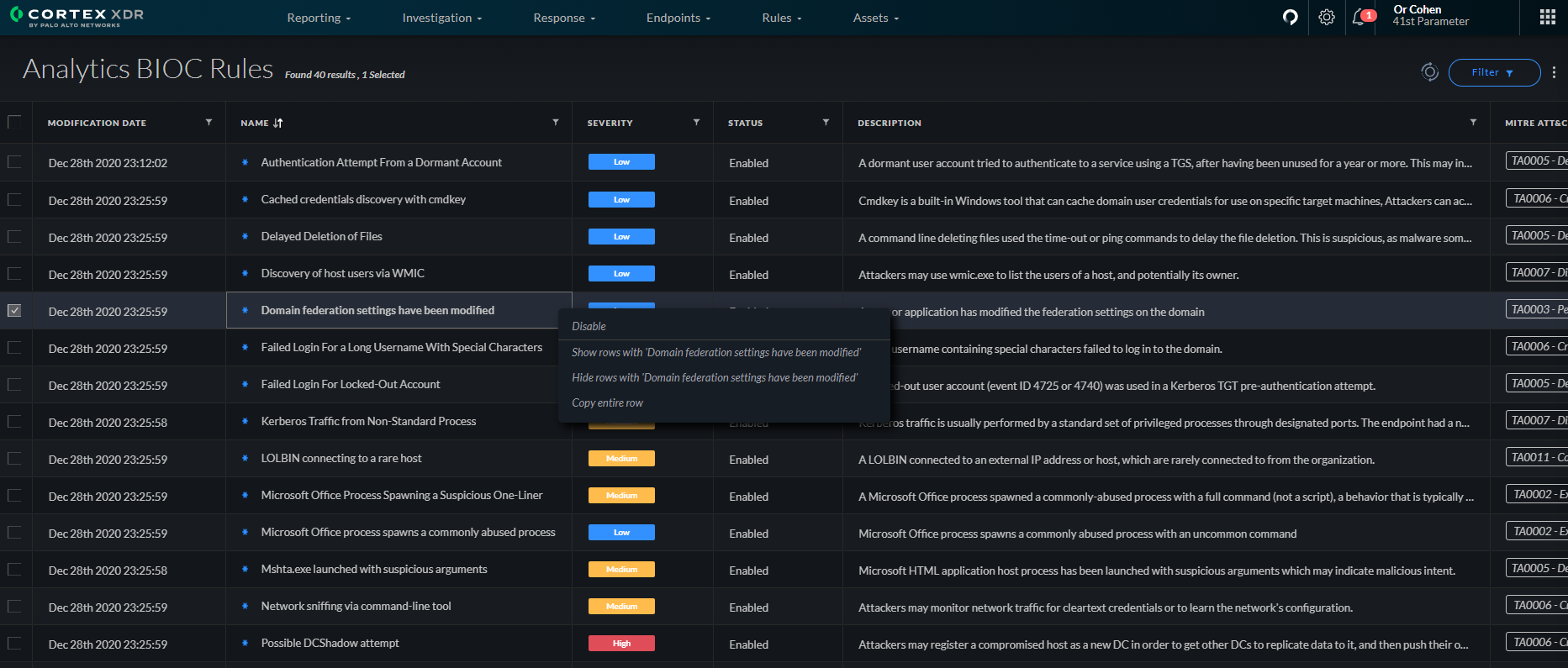
These alerts and out-of-the-box queries make it easy for security teams to detect and hunt for indications of a breach.
Palo Alto Networks: Your Port in the (Solar)Storm
In responding to SolarStorm, we need to protect against not only the original attack, but also the variants and copycats who try to use similar techniques and tactics. As new details of SolarStorm variants emerge, the Cortex XDR research team will continue to release updates to identify and stop associated threat vectors.
We’ve also established a rapid response program that helps you discover, investigate and recover from a breach if you’ve been compromised. Visit our SolarStorm resource center to learn more about our two rapid response offerings.