Digitization and edge connectivity are evolving at a more incredible pace than ever in the last decade. Agility, adaptability and innovation are the critical components of a successful modern business. Enterprises are rapidly migrating to cloud-native, connected platforms and embarking on an application modernization journey to streamline business operations, support virtual and hybrid work environments, and offer more value to their customers and end users in a digital economy driven by 5G, cloud and edge connectivity.
Mobile network operators (MNOs) are virtualizing their networks to enable scalability, resilience and flexibility by implementing cloud-native solutions that leverage network function virtualization (NFV). The success of 5G networks will rely heavily on cloud computing enablers, such as Multi-Access Edge Computing (MEC), private networks and network slicing. In the best-case scenario, network slicing and private network capabilities for enterprise customers may be installed in several hours, not weeks or months. However, adopting new technologies such as 5G and cloud computing increases the risk of cyber attacks as these technologies come with expanded attack surfaces, disappearing perimeters and increased vulnerabilities. Enterprises should not ignore the risks and must manage the security threats proactively.
As enterprises host applications and data in hybrid environments, a lack of visibility across hosts and services can make protecting a cloud-first strategy and edge connectivity even more challenging. The quick change to hybrid work modes in response to the global COVID-19 pandemic created millions of scattered remote offices. This brought bring your own device (BYOD), including laptops, cellphones and tablets, with limited visibility and control on user and device-level security. Security risks were further increased to the enterprise with a potential threat to data breaches, application susceptibility and malware. In such an environment, bad actors can uncover vulnerabilities in an enterprise infrastructure that its administrators may have overlooked, and cause severe damage.
Multi-tenancy is another critical vector in cloud-native architecture, allowing multiple customers (or tenants), solution providers and vendors to be served by a single instance of an application and shared physical infrastructure. It presents a significant security risk for 5G network infrastructure where MNOs and enterprises could deploy several elements from different vendors on top of common physical infrastructures. In the case of edge computing, the transfer of data from the edge to the multi-cloud providers, and the cloud back to the edge, makes it highly vulnerable to cyberattacks. Multi-tenancy and edge computing emphasize the necessity to harden and securely configure technologies that separate the workloads (e.g., virtualization/containerization) for each client and customer. A managed security service provider (MSSP) with the right security credentials can absorb the complexities of their well-designed services and help enterprises reap the benefits of secured critical infrastructure and services with enterprise-grade security.
It is also important to note that the cloud providers are responsible for the security of the cloud, MNOs and enterprises may share security duties in a way that compels them to secure their tenancy in the cloud. The diverse and complex deployment of a multi-cloud or hybrid-cloud deployment model in 5G, with evolving architectures and design methodologies, presents additional security challenges to the MNOs. If a malicious actor can move laterally or pivot from one compromised cloud workload to another, it can have widespread and cascading consequences on many other cloud tenants.
Some recent threats, such as the Log4j exploit, caused billions of Java devices to be vulnerable to complete control and exploitation, and over 11 million attack sessions were observed in less than one month. As expected, some of the most common cloud services essential for edge computing were vulnerable to the Log4j, including compute services, storage services, databases and more. A recently published research report from Unit 42 has shared an analysis of many such common vulnerabilities and exposures (CVE) and provided an evaluation of network threats and recommendations on how to assess your network security posture fully, how to deploy preventions for unknown command and control, and how to implement Zero Trust.
In summary, the proliferation of devices, the massive increase in intelligence at the network edge, and multi-tenancy and multi-cloud deployments are the significant difficulties that lead to a perfect storm of security risk in 5G enterprise deployments. To mitigate these, any enterprise going through the digital transformation journey should employ the following best-security practices to secure their cloud and edge infrastructure while enabling a seamless user experience and advancing business digitization:
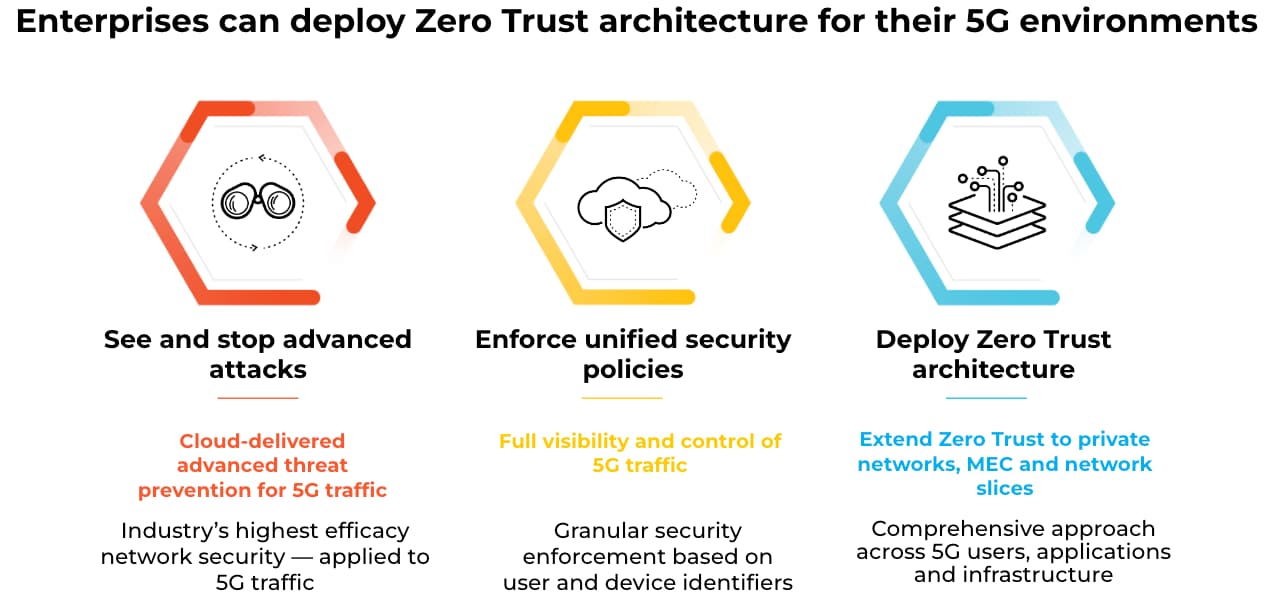
- Visibility: Implement visibility and control to scan the enterprise 5G network in a distinctive manner through customizable security permissions. Access privileges, which facilitate a secure, integrated supply chain for a multitude of suppliers and business partners.
- Control: Use cloud-based, advanced threat protection to detect and block malware, command and control traffic, as well as other vulnerabilities, by implementing ML-Based inline threat prevention to stop zero-day threats. Equipment ID-based security enforcement to correlate, isolate and quarantine infected devices.
- Deploying Zero Trust: Eliminate implicit trust throughout the enterprise by continuously implementing the “never trust, always verify and verify continuously” principle by adopting the Zero Trust security model for edge clouds and private networks. Achieve consistent security visibility, enforcement and analytics throughout your 5G network.
It is evident that the cloud, 5G and edge will accelerate digital growth and transformation across numerous industries, businesses and governments. Deploying 5G and cloud-based edge computing applications comes with its complexities and challenges. This is why it is critical for enterprises to design their infrastructure with enterprise-grade security through trusted industry leaders. Read more about our 5G security solutions here and learn our approach to 5G enterprise security.