Introduction: Remote Desktop Protocol (RDP)
Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft which provides a user with a graphical interface to connect to another computer over a network connection. The user employs RDP client software, while the other computer must run RDP server software. Furthermore, it provides remote display and input capabilities over network connections for Windows-based applications running on a server.
Why Should We Pay Close Attention to RDP Forensics?
Given the widespread use of RDP, especially in corporate environments, the ability to perform forensic analysis on the RDP bitmap cache can be invaluable in investigating various cyberattacks. These may range from insider threats (such as employee data theft) to external attacks (such as hackers using RDP sessions to gain unauthorized access to sensitive data).
How Adversaries Use RDP in Their Attacks
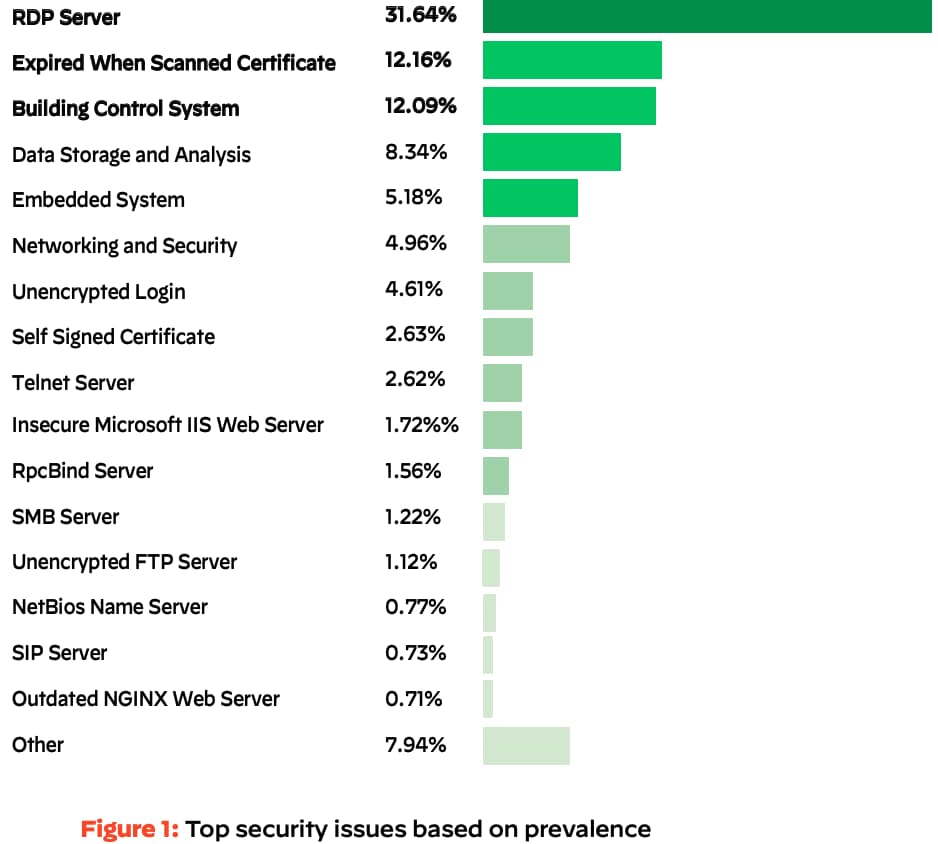
Cortex Xpanse’s 2022 Attack Surface Threat Report found RDP to be the most common security issue attackers can find on the global enterprise attack surface. Remote Desktop Protocol was the most common security issue among the global enterprises we studied, representing 32% of overall security issues (see Figure 1). RDP’s top spot is particularly worrisome because it’s a top gateway for ransomware.
Furthermore, when focusing on the Unit 42 Incident Response report, the report states that brute-force credential attacks are responsible for 20% of the initial attack vectors in cases Unit 42 investigated, primarily using RDP.
As mentioned, attackers often conduct brute force attacks to crack weak or reused credentials or exploit unpatched vulnerabilities to gain unauthorized RDP access. Once inside, they can move laterally across the network, escalate privileges, deploy ransomware, exfiltrate data, or establish persistent backdoors. RDP's legitimate use for remote access makes it an ideal camouflage, allowing attackers to blend their activities with normal network traffic, making detection considerably more challenging.
The Potential of RDP Bitmap Cache Forensics
When interacting with the remote server's desktop, all graphical changes must appear on the screen and therefore be transmitted by the server to the client, which, as you can imagine, can generate heavy network traffic.
RDP has a bitmap caching feature that, when enabled, allows the session to use data already in the local cache files to provide a smoother user experience and reduce network bandwidth.
This process involves storing frequently used images (bitmaps) from the remote host locally on the client machine. This way, the need to retransmit the same images over the network, which can be bandwidth-consuming and slow, is minimized.
The bitmap cache consists of several cache entries. Each entry stores bitmap data and metadata such as the key, dimensions, and color depth.
What's genuinely intriguing for digital forensics is that this cache persists on the client machine, even after the RDP session has been terminated.
The successful exploitation of the RDP cache files will make it possible to recover tiles (Figure 2) of what the user saw during the RDP session and, by putting the tiles back together, potentially discover new elements in an investigation.
This is similar to recovering puzzle pieces, which, when correctly assembled, can recreate the picture of a user's actions during an RDP session. (Figure 3)
The RDP Bitmap Cache Hunting Pack Walkthrough
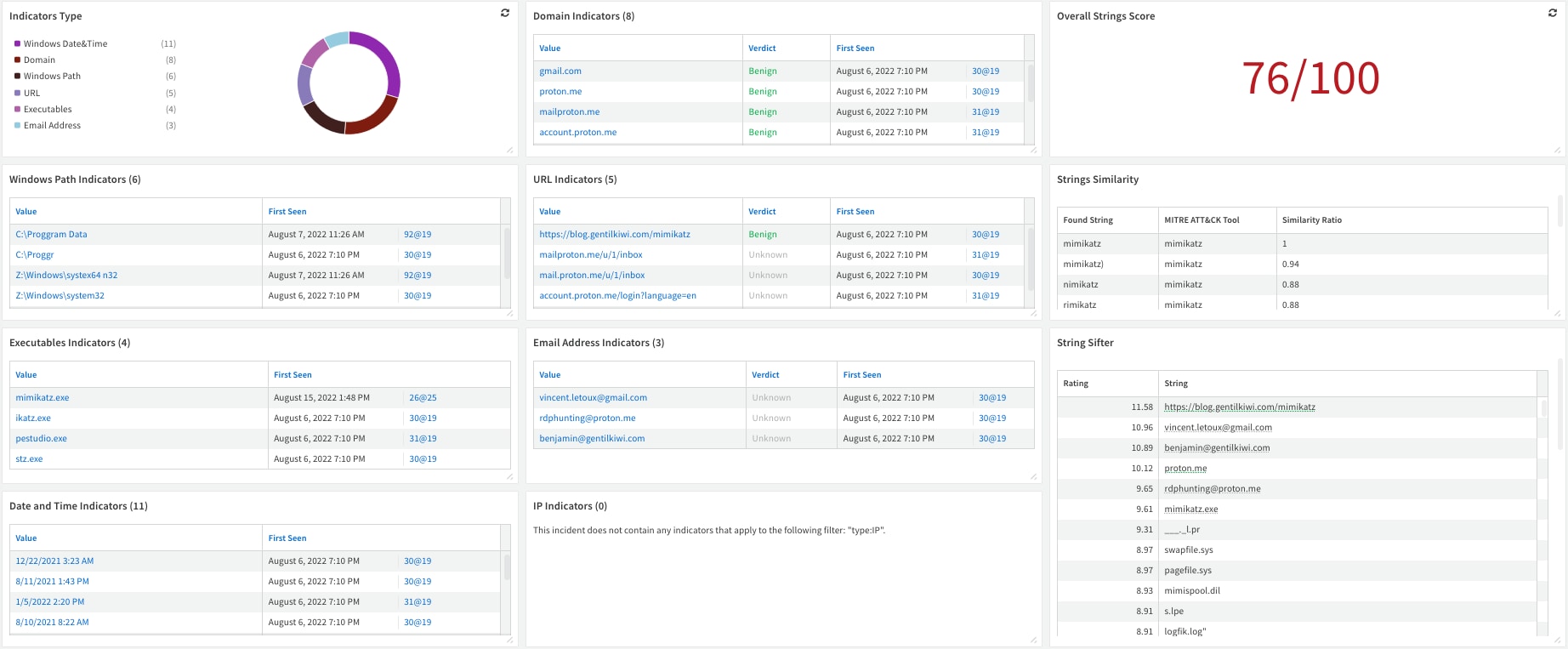
For organizations seeking to tighten their cybersecurity, the RDP Cache Hunting pack offers an advanced solution to detect and analyze potential threats in RDP connections. This pack can gather RDP bitmap cache files via different XDR solutions or Remote PowerShell. These files are then processed into a more comprehensible format — tiles are extracted and collaged, and text is extracted from the images.
An Automated Collection and Forensic Analysis playbook is also part of the RDP Cache Hunting pack to make this process even more efficient. This playbook simplifies the extraction and analysis process into four steps: Collection of cache files, conversion of these files into images, extraction of readable text from these images, creation of indicators of compromise (IOCs) from the text, and finally, enrichment of these IOCs with additional context for enhanced threat analysis.
The pack utilizes BMC-Tools by ANSI, a powerful utility designed specifically for extracting and processing RDP cache files. It parses Windows RDP cache files (.BIN) into tiles and generates a collage.
We thought about leveraging the collage and making the entire analysis process more efficient. We have decided to extract all the visible text from the collage created and try to detect suspicious activity based on the extracted text.
To do so, we used the tesseract-ocr OCR solution, which allowed us to go through all the available text combined from the tiles.
The information extracted is subsequently assessed for potential IOCs. Two mechanisms are used for this purpose: first, the MITRE ATT&CK Software list, a globally-accessible knowledge base of adversary tactics and techniques, is used in the String Similarity script, which measures how closely the extracted text matches the MITRE ATT&CK Software list, outputting a similarity ratio. In parallel, Mandiant Stringsifter, a machine learning tool, ranks these strings based on the likelihood of their maliciousness.
The RDP Cache Hunting pack, therefore, provides the following:
- A systematic and robust approach to detecting potential internal RDP sessions on predetermined hosts.
- Processing the collages for further analysis.
- Flagging any suspicious activity.
Users are encouraged to modify the pack and the playbook to meet their unique organizational needs and legal requirements.
Final Notes
As the use of RDP by attackers continues to rise, so does the importance of RDP bitmap cache forensics. The ability to extract and interpret data from these caches can offer significant insights into user activities during RDP sessions, aiding investigations of cybercrimes.
Organizations should adopt advanced forensics capabilities to get a brighter image of what was done by the attacker and how they can counter his activity.
For more information on the RDP Bitmap Cache Hunting pack and other XSOAR packs and playbooks, visit our Cortex XSOAR Developer Docs reference page.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.