Do you know if you have any exposure to the latest VMware ESXi vulnerability? Cortex Xpanse does.
From February 7th through the 14th alone, nearly 4,000 VMware ESXi servers have been the target of rapidly spreading ransomware targeting a nearly two-year old vulnerability. These attacks are widespread and are happening in every corner of the globe.
Internet-exposed ESXi servers have been a known point of vulnerability for years. These systems should not be facing the public internet ever, but in the recent weeks leading up to this article, we have seen that more are facing the internet than a security team would expect. While some organizations have policies that ESXi devices should only be accessible on the internal network, other companies continue to intentionally or accidentally expose them outside their firewall.
Cortex Xpanse Active Attack Surface Management helps prevent fires when known CVEs are being actively exploited by threat actors and even goes a step further by helping organizations prepare for new CVEs. This is done by allowing organizations to create non-CVE based policies to detect assets likely to experience CVEs in the future.
With the uptick in targeted ransomware in February 2023, Active ASM has undergone improvements to our VMWare ESX(i) policies to check for Service Location Protocol (SLP) over port 427.
Our attack surface management solution, Active ASM, indexes the global internet to find publicly exposed assets like IPs, domains, certificates, and more. Through this solution, we help customers identify exposures before they are a problem.
Active attack surface management (ASM) helps prevent fire drills when a new CVE is announced by quickly allowing organizations to create non-CVE based policies to detect assets likely to experience CVEs in the future. Our non-CVE based policies allow security teams to build a high-quality inventory of exposed systems, enabling them to get all of their instances behind a firewall before the next CVE exploitation wave hits.
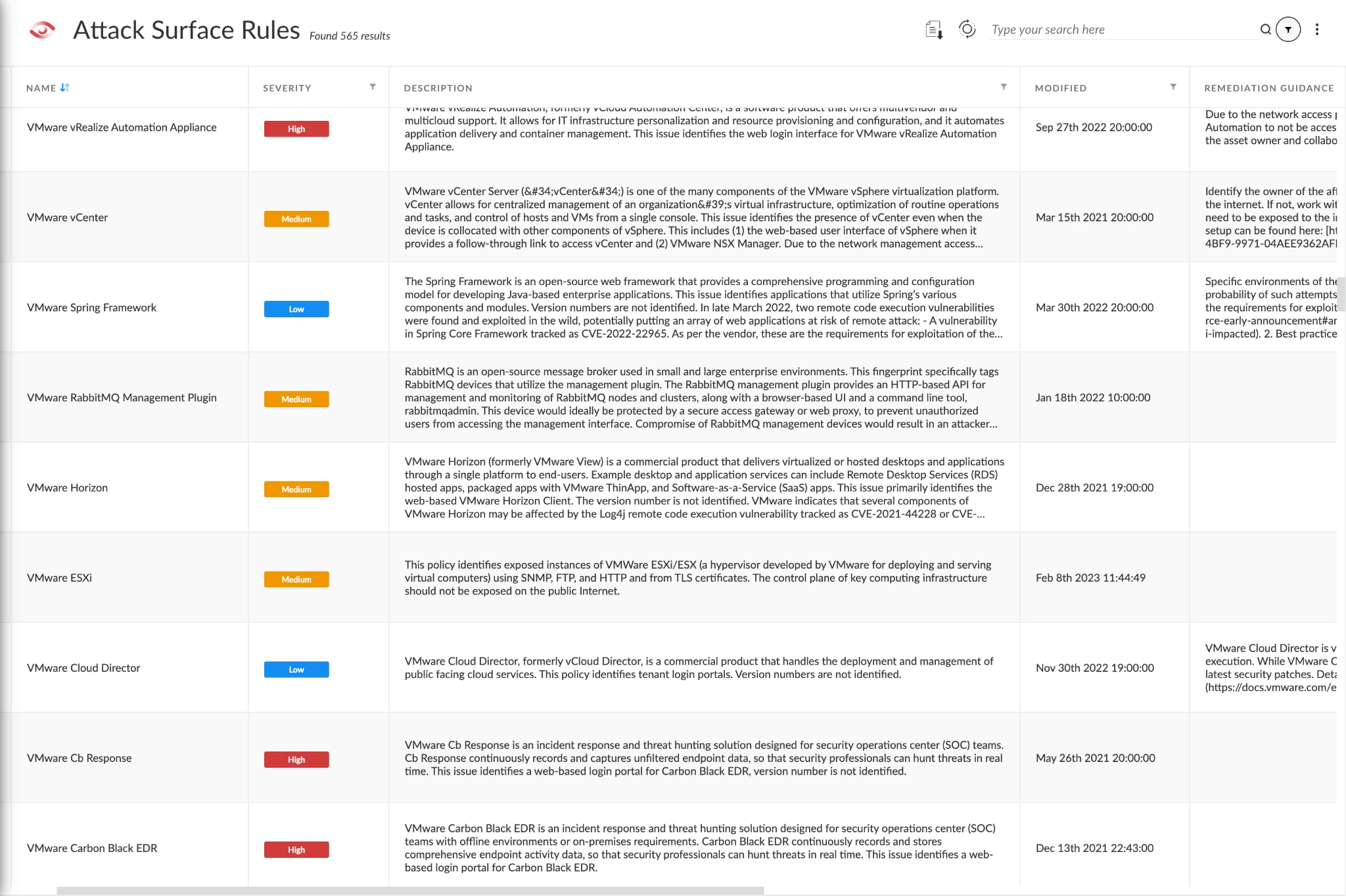
While SOC and vulnerability management teams may be aware of the VMware ESXi vulnerabilities, they can only patch instances they know about. Our research team has found that it can sometimes be challenging to account for every instance of an application running in an environment, and even more difficult to identify the ones that are internet-facing. Between years of renewals, switching between hypervisors, the influx of remote work, and the migration to the cloud, it’s been increasingly tedious and labor-intensive for organizations to track all assets exposed to the internet accurately.
Adversaries don’t have this limitation and seek to identify exposed assets, whether they’re on the known asset inventory list or not. On average, it takes 15 minutes from a new zero-day announcement for threat actors to begin exploiting it, according to the 2021 Attack Surface Threat Report. Cortex Xpanse helps organizations actively manage their attack surface and effectively respond to zero-days by discovering their exposed assets and services. This ensures that security teams are equipped with the most comprehensive and up-to-date information to remediate exposures and mitigate the risk of security incidents.
Xpanse indexes the global internet daily to find the assets our customers need to know about. When it comes to VMware and similar systems, we have developed a policy system to alert customers of exposures and keep our CVE database up to date to link customers' assets to known vulnerabilities, giving them a leg up in closing exposures and securing assets across a variety of services, ips, domains, certificates, and cloud instances.
Unfortunately, the security landscape is only getting more complicated. Between the latest ESXi exposure and the increasing prevalence of ransomware, organizations need to invest in tools that identify and help protect their blindspots.
Attackers are only becoming more crafty and automating their ability to quickly scan for and exploit new vulnerabilities on internet-facing assets. Some of the world’s largest and most demanding organizations use Xpanse to secure their attack surface and reduce risky exposures. Xpanse protects the U.S. Department of Defense, all six branches of the U.S. military, several federal agencies, and large enterprises like Accenture, AT&T, American Express, AIG, Pfizer, and over 200 others.
To learn more, watch the “Active Attack Surface Management with Cortex Xpanse” our on-demand webinar led by experts in attack surface management!
Reference:
https://www.cybersecuritydive.com/news/ransomware-spree-vmware-servers/642121/