Discover best practices to help secure your Docker environment with Prisma Cloud.
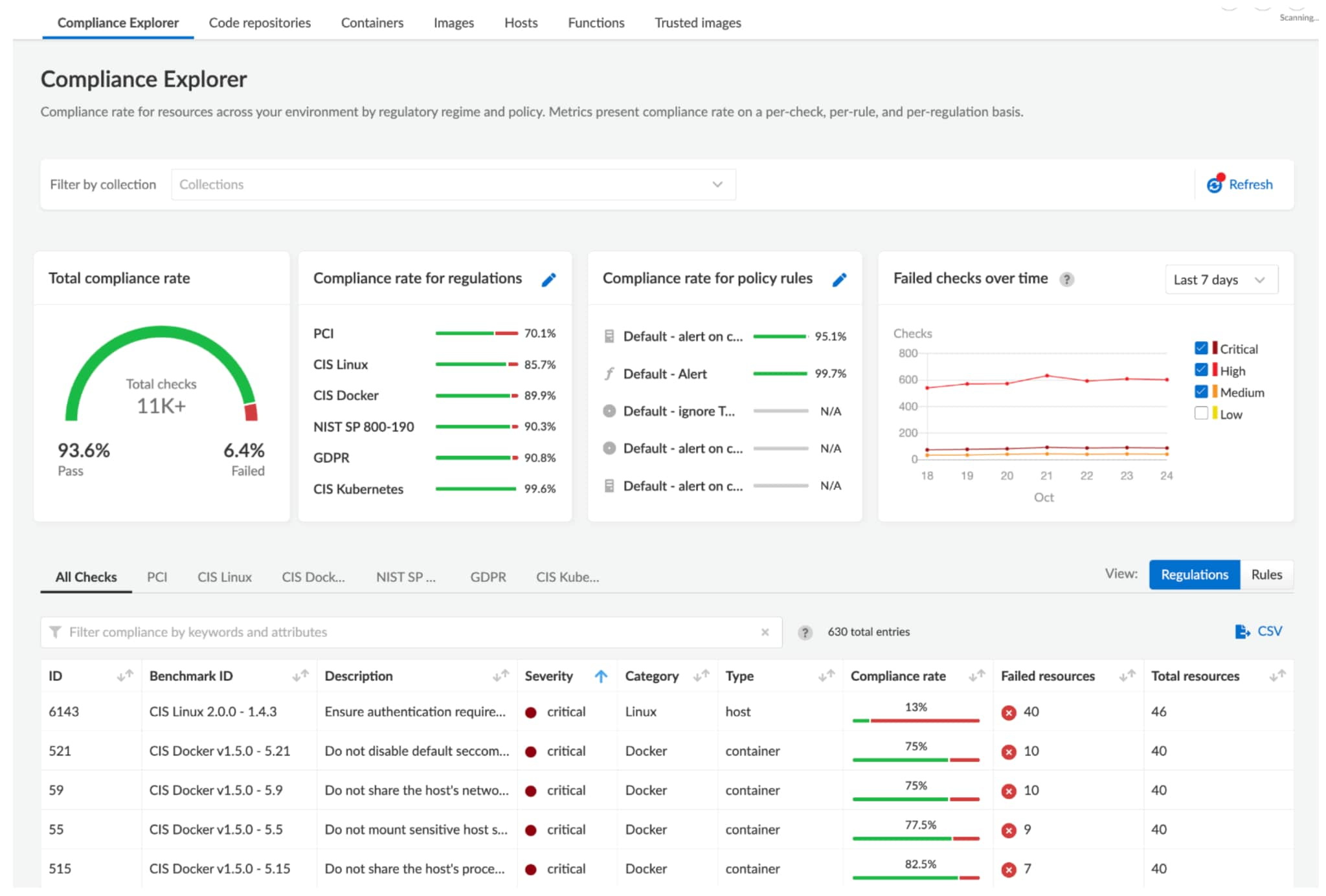
The Prisma Cloud Compliance Explorer showing Docker policy compliance and checks
Prisma Cloud can help improve the security of your Docker environment. Use Prisma Cloud to scan container images for vulnerabilities and misconfigurations in the DevOps IDE, PR workflows and CI/CD pipeline for complete protection from code to cloud.
Here are five best practices to help you secure Docker environments with Prisma Cloud.
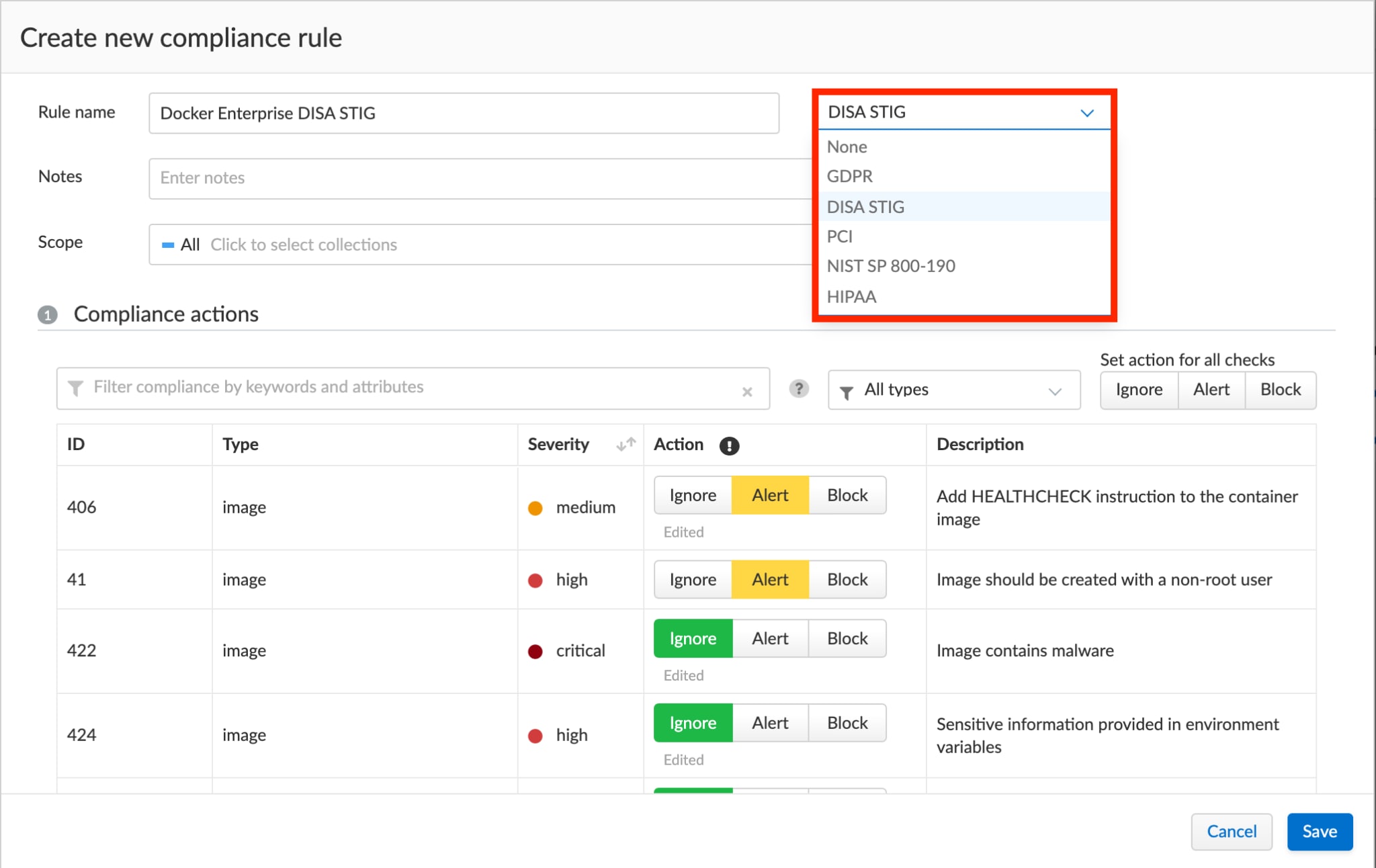
Best Practice #1: Use Prisma Cloud to Help Support Docker DISA STIG Compliance
Prisma Cloud helps enable public sector users to quickly assess and control their microservices environments with Docker DISA STIG compliance, specific security checks and guidance for Docker on Linux and UNIX-based operating systems. The Defense Information Systems Agency (DISA), a DoD agency, collaborates with private industry to create Security Technical Implementation Guides (STIGs).
With Prisma Cloud, you can help ensure public sector compliance for your Docker environment using the Docker Enterprise 2.x Linux/UNIX STIG, which includes configuration standards for Department of Defense IA and IA-enabled devices and systems.
Best Practice #2: Use Prisma Cloud to Protect Against Leaky Vessels Critical Vulnerabilities Affecting Docker
Four recent critical CVEs are affecting Docker. Since each Leaky Vessel vulnerability resides in a critical component of the container ecosystem — runc (container spawning), Docker (image building), Buildkit (image building), and Moby (container platform) — the potential impact ranges from unauthorized file deletion to a complete host compromise.
Prisma Cloud identifies workloads affected by Leaky Vessels and provides simple guidance on how to remediate with Docker.
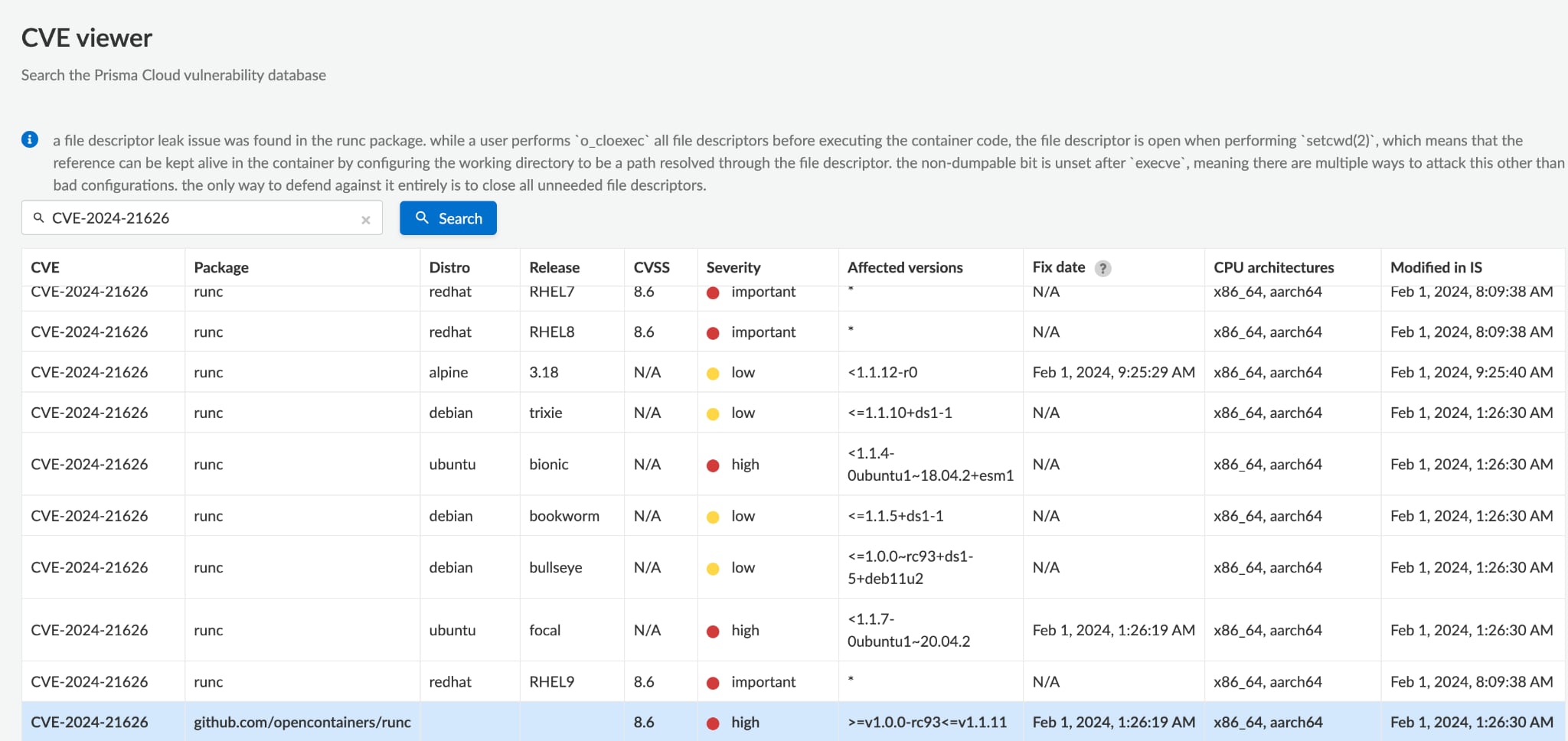
As a best practice, review existing Dockerfiles and stay cautious with Dockerfiles, especially those obtained from untrusted sources. Scrutinize them for suspicious commands like RUN, USER, or for misconfigured settings.
Best Practice #3: Use Prisma Cloud to Monitor Access Control of Existing Dockerfiles
Prisma Cloud lets you control access to Docker commands based on group membership or on a user-by-user basis. For example, after integrating Prisma Cloud with Active Directory, OpenLDAP or SAML, you just need to create a group called Dev Team. Then in the Prisma Cloud Console, you can help secure Docker by granting all users in Dev Team permission to remotely run Docker commands on hosts in the development environment but deny permission to create, start or stop containers on hosts in the production environment.
With Prisma Cloud, you gain better control over Docker activities and can manage rules governing Docker configurations, containers, images, nodes, plugins, services and more, to ensure your Docker environment runs the way you choose. To better understand the intended behavior of each access rule policy in Prisma Cloud Console UI, see our list of Prisma Cloud access rules for Docker.
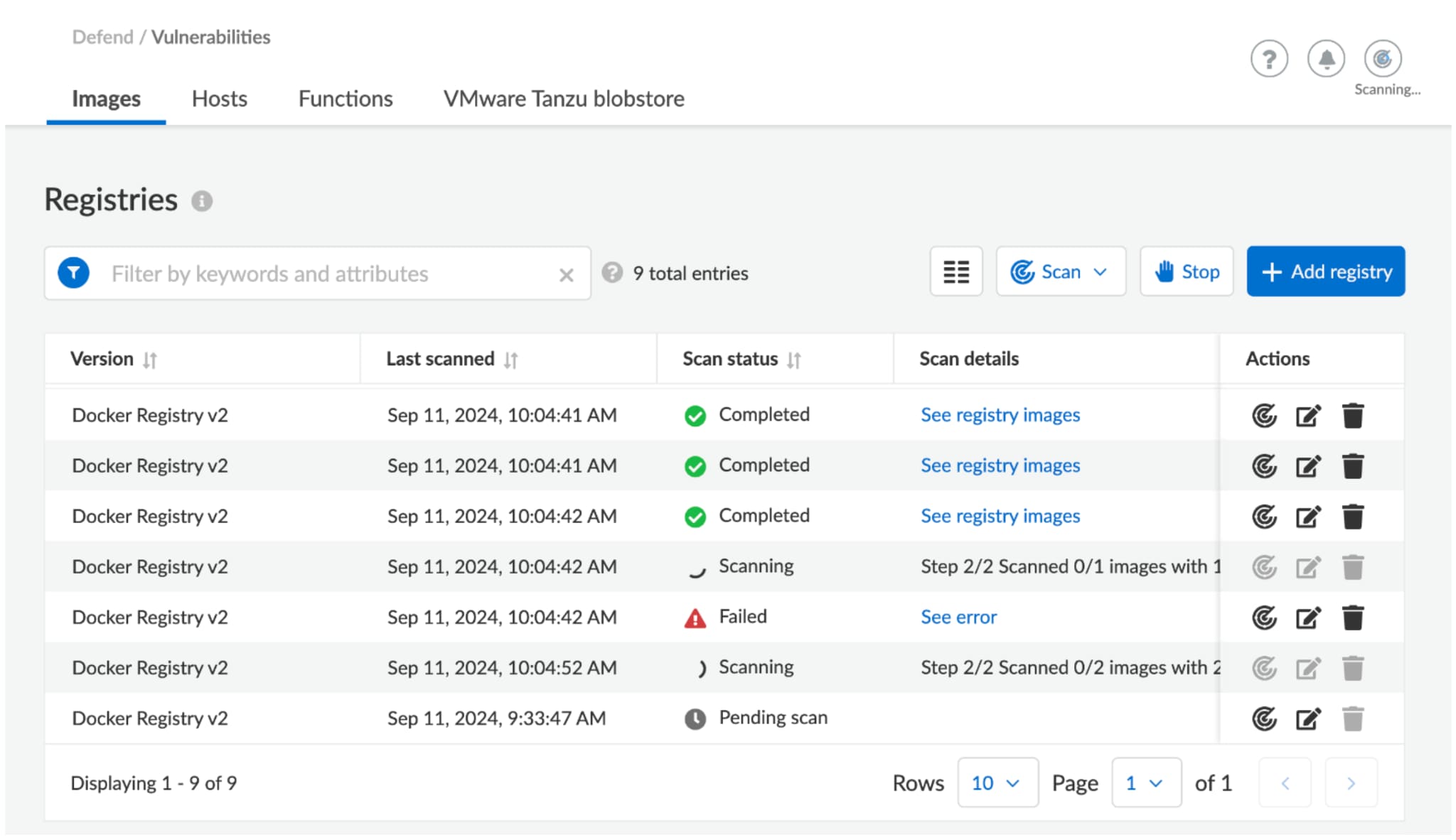
Best Practice #4: Use Prisma Cloud to Shift Security Left and Scan Images in the Docker Registry V2
The Docker Registry is a system for versioning, storing and distributing Docker images. You can use Prisma Cloud to identify code risks in the Docker Registry at the same time that developers are building and testing software.
With Prisma Cloud you can choose to be proactive and shift left by checking open-source packages and images for vulnerabilities and compliance issues across Docker Registry V2 (and GitHub, and many other repositories).
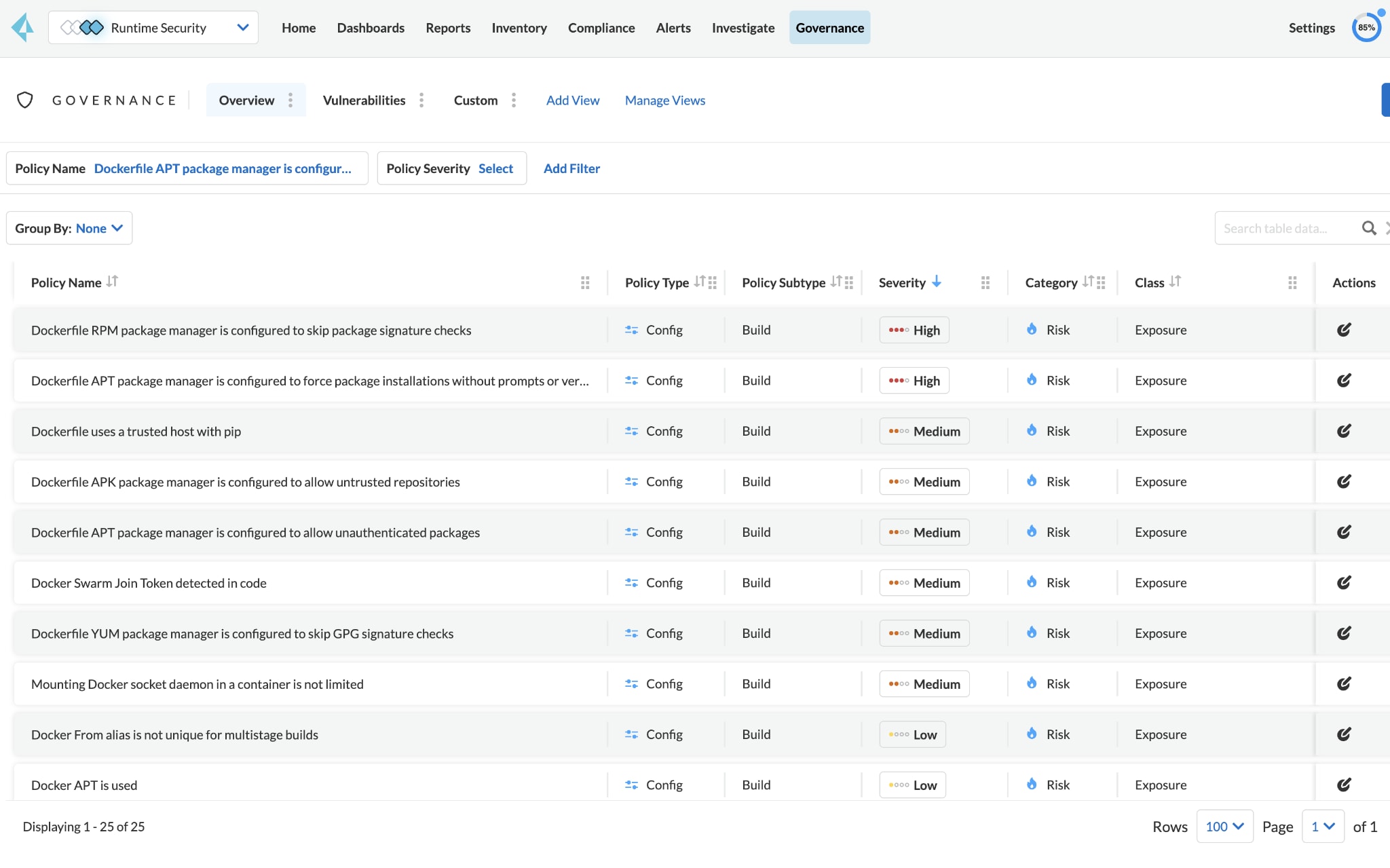
Best Practice #5: Use Prisma Cloud to Help You Securely Configure Your Docker Environment
Prisma Cloud alerts you when your Docker environment is configured insecurely. For instance, in addition to many other Docker security risks Prisma Cloud alerts for, the following are high-severity Docker misconfigurations that you can avoid:
- Prisma Cloud alerts you when using the --force-yes option with the APT package manager (apt-get) in Dockerfiles. This perilous configuration automatically answers "yes" to all prompts during package installation, which can lead to the embedding of malicious software or insecure versions into your Docker images.
- Prisma Cloud alerts you when the GIT_SSL_NO_VERIFY environment variable is set to true within Dockerfiles, a critically insecure state. When set to true, it instructs GIT to bypass SSL certificate verification when cloning repositories or interacting with remote servers, which can lead to man-in-the-middle (MitM) attacks, cloning of malicious repositories, code alterations, or the leaking of sensitive information.
- Prisma Cloud also alerts you when employing the --nosignature option with the Red Hat Package Manager (RPM) in Dockerfiles as a substantial security risk. Turning this option on directs the RPM to bypass package signature verification during installations and can lead to malicious software or vulnerable versions being incorporated into your Docker container image.
Docker Is Better Together with Security by Prisma Cloud

Palo Alto Networks is a Leader and Outperformer in the 2023 GigaOm Container Security Radar with Prisma Cloud offering the strongest threat intelligence and registry scanning capabilities available for container workloads.
Don’t neglect the security of your Docker environment. Use Prisma Cloud to scan container images for vulnerabilities and misconfigurations in the DevOps IDE, PR workflows and CI/CD pipeline for complete protection from code to cloud.
Learn more about securing Docker with Prisma Cloud on our Docker environment page.
Want to try out our industry-recognized cloud-native security solution? Get started now on a free trial of Prisma Cloud.