Cloud workload protection (CWP) changed the game when it arrived. For the first time, teams could extend security controls into new cloud native workloads where traditional security methods no longer sufficed. This meant scanning container images, virtual machines, and serverless functions for vulnerabilities and compliance issues — and without slowing development. It offered visibility without friction, and security teams embraced the momentum it brought.
But the cloud didn’t stand still.
As cloud-native environments grew more dynamic, and workloads more ephemeral, security teams found themselves confronting new challenges — attackers moving faster, vulnerabilities compounding at scale, and runtime risks escaping traditional controls. CWP, on its own, didn’t provide enough visibility into the attack kill chain.
Agentless scanning provided a deploy-friendly way to gain visibility into cloud workloads. Runtime protection introduced mechanisms to catch threats in action. In practice, though, these capabilities remained fragmented. They offered snapshots in time, often leaving CloudSec teams without the context needed to act confidently and quickly.
CloudSec needed more than alerts. It needed intelligence — smarter correlation — that spanned predeployment posture and live attack behavior. It needed security that could keep pace with how cloud applications are built and run today.
That’s the shift Cortex Cloud delivers.
Why CloudSec Teams Struggle to Investigate Incidents
When a cloud workload triggers a runtime alert, the investigation shouldn’t begin from scratch. Too often, though, that’s what ensues. Security teams have to trace what happened, understand why, measure the risk, and prevent it from recurring.
But acquiring the knowledge to do that requires more than data. Security teams need the ability to follow an attack as it moves across ephemeral infrastructure, identity sprawl, and shifting workload states.
To move at the speed of today’s cloud, teams need expedient answers to essential questions:
Where did it happen?
Security analysts need to pinpoint the provider, region, and workload. Was the container running in a managed service like AWS Fargate or a self-managed cluster? Was it exposed to the internet or isolated to a private VPC?
Why did it happen?
Security must uncover the root cause. Was the container built with a vulnerable dependency? Did a misconfigured IAM role expose more access than intended? Were secrets exposed in the environment variables?
What was at risk?
Teams need to assess the blast radius. Did the workload have access to sensitive databases or cloud storage? Were there lateral connections to other services or suspicious outbound activity?
How do we prevent it from happening again?
Most critically, teams must act. Are runtime policies too permissive? Are CSPM controls out of sync with real-world deployment patterns? Is vulnerability management tuned to what’s actually exploitable in production?
Each question draws from a different source of truth — and each delay in finding those answers extends the window of exposure.
That’s why traditional workload protection, even when comprehensive on paper, tends to break down in practice. Alerting isn’t the problem. The lack of clarity is.
How Cortex Cloud Fast-Tracks Threat Investigation
Most cloud security platforms collect data. Cortex Cloud connects it — turning fragmented signals into a single, coherent investigation workflow. When a threat emerges in a runtime environment, CloudSec teams can move from alert to action in minutes — not hours.
Here’s what that workflow looks like in Cortex Cloud:
Step 1: Surface Suspicious Behavior with Full Context
The investigation starts with more than an alert. Cortex Cloud immediately surfaces the full context — what triggered the detection, where it occurred, and which identities were involved — because the signals are already connected in a unified dataplane spanning runtime, telemetry, posture, and identity.
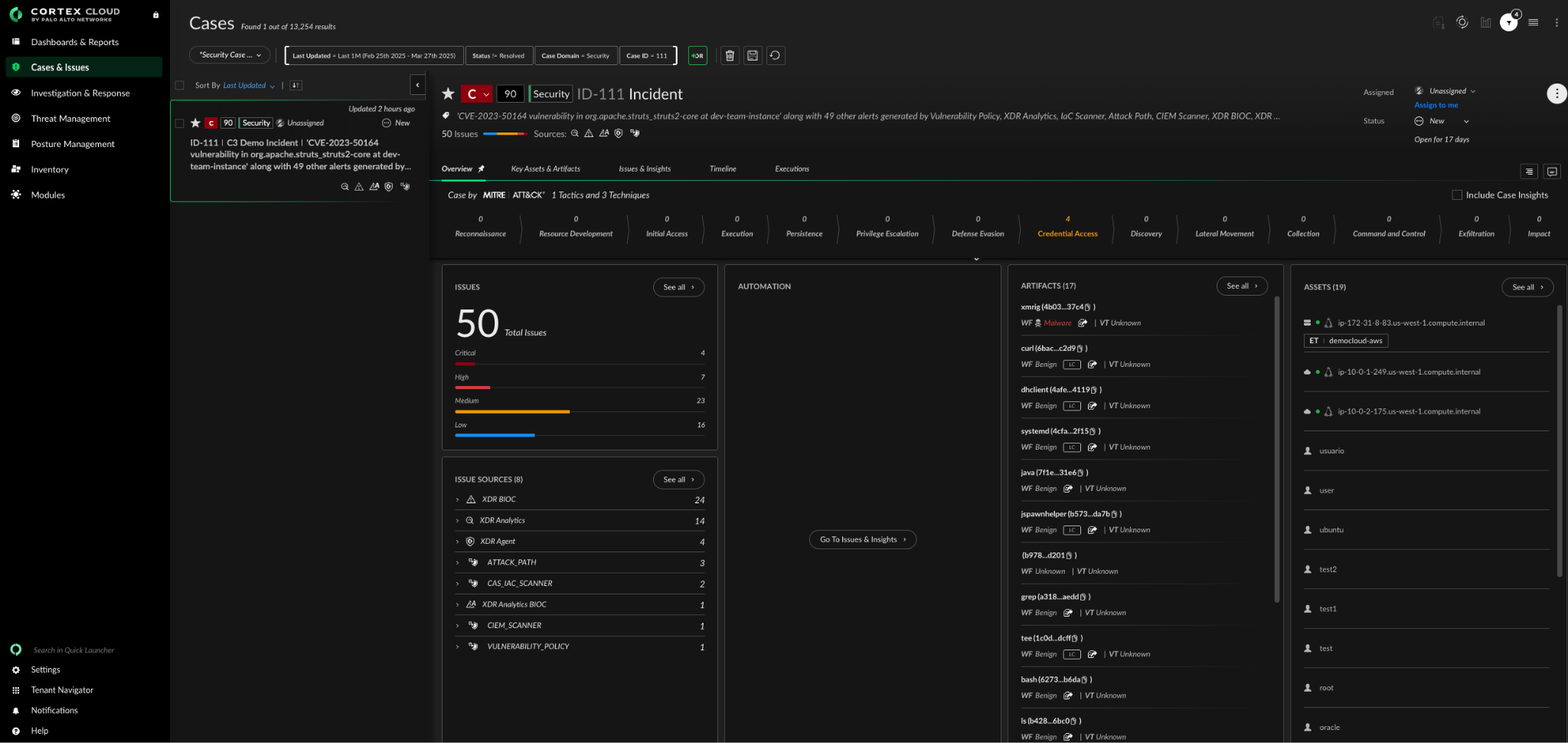
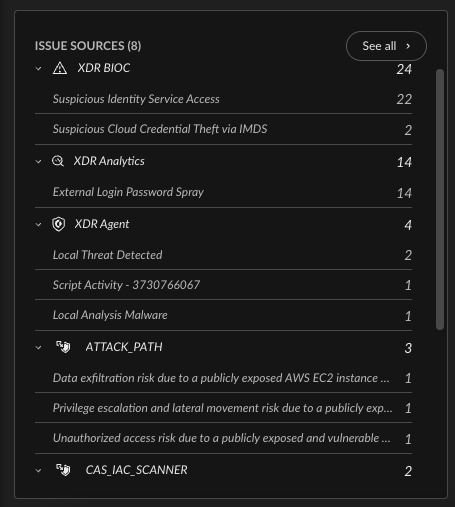
Step 2: Connect the Dots Across the Stack
Isolated alerts don’t tell the full story. Cortex Cloud correlates posture risks (misconfigurations and exposed secrets, for example) with real-time behavior such as lateral movement, anomalous activity, and abuse of overpermissioned roles. Integrated telemetry reveals how an incident unfolds across layers, as well as where to contain it. And because this context lives in one unified system, CloudSec teams can act immediately or escalate to the SOC. Every stakeholder sees the same incident, fully formed.
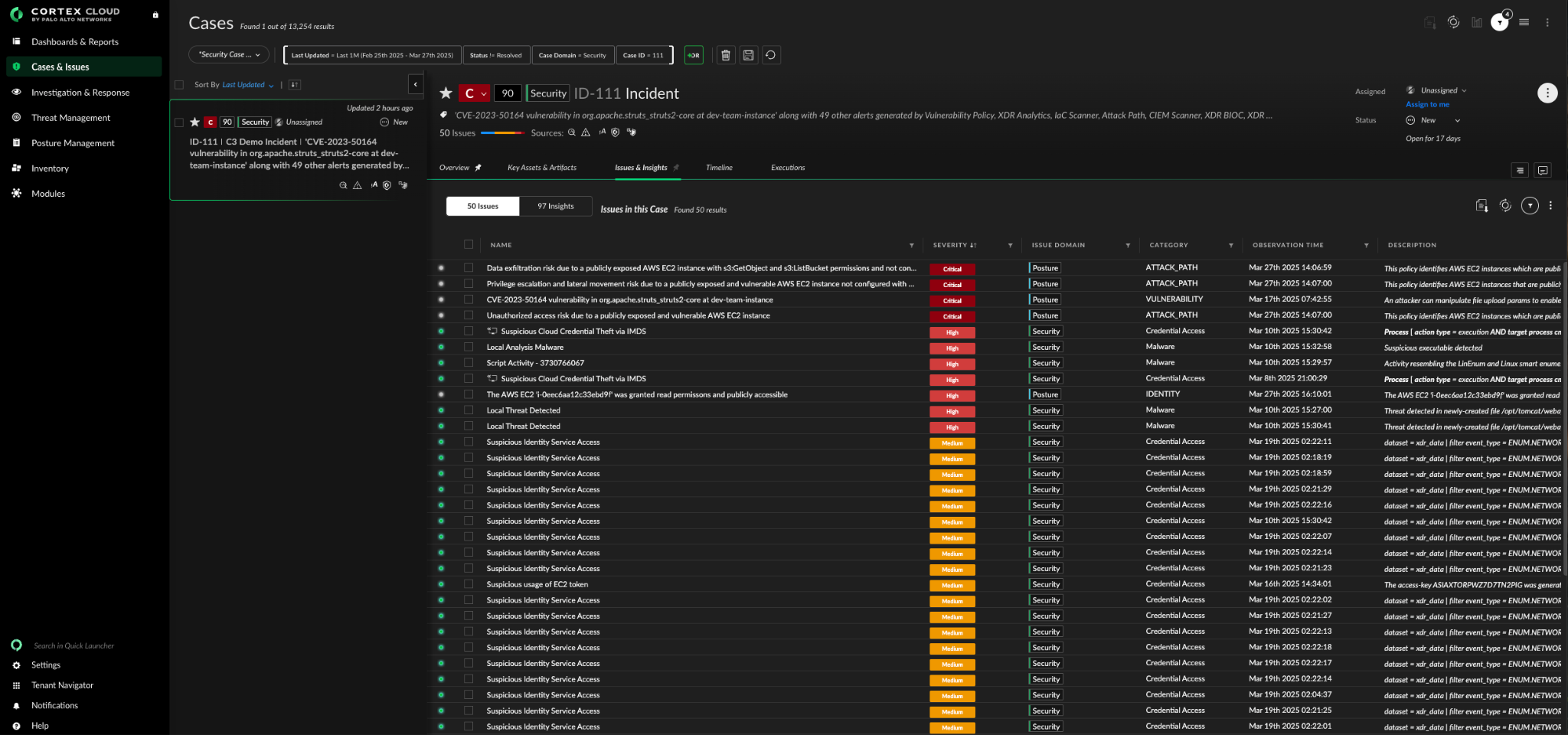
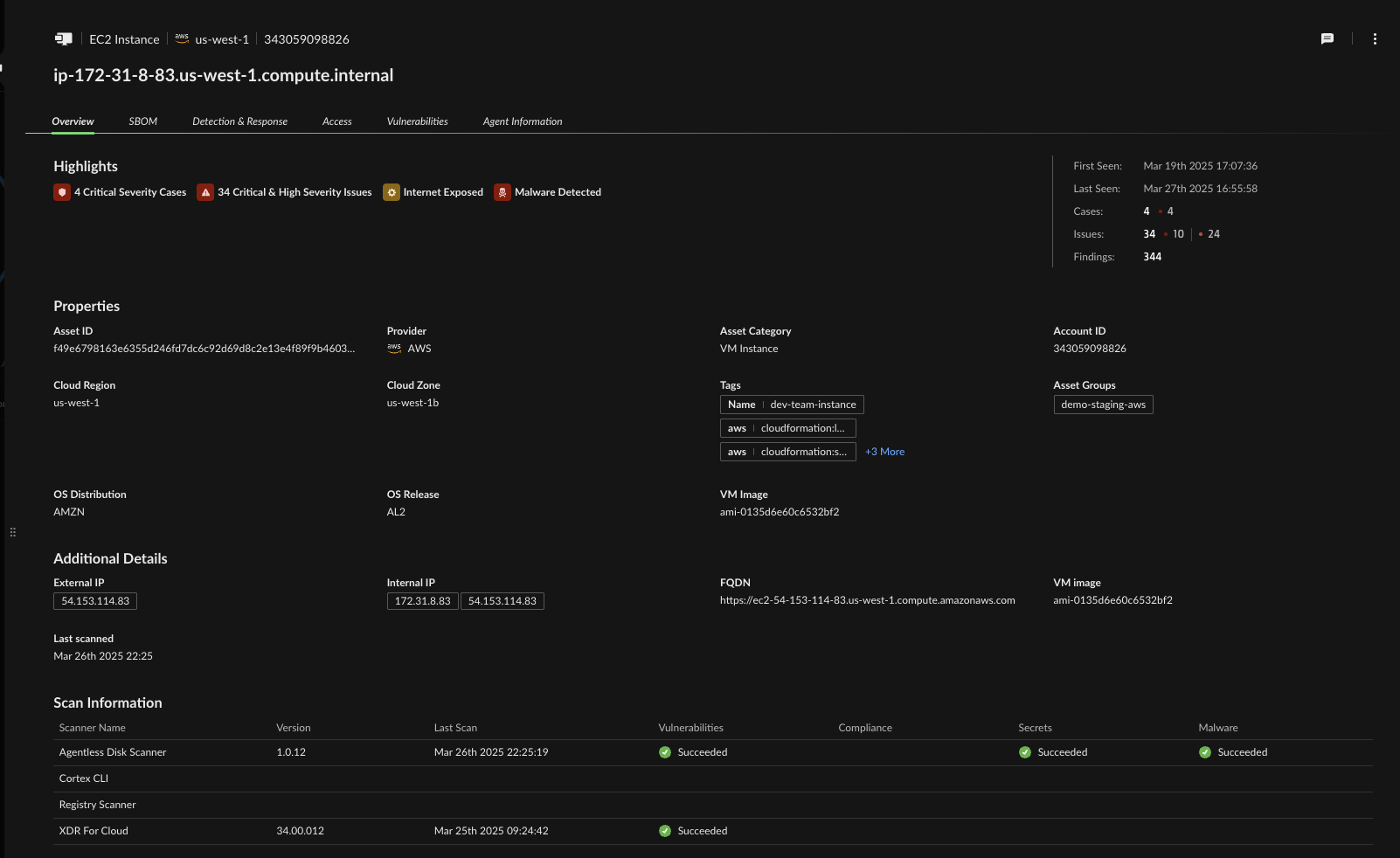
Step 3: Understand the Root Cause and Exposure
From within the case, analysts can drill into the affected asset. Cortex Cloud surfaces a software bill of materials (SBOM), internet exposure, IAM entitlements, and vulnerability data — all in one place. Security teams can immediately determine blast radius, exploitability, and next steps.
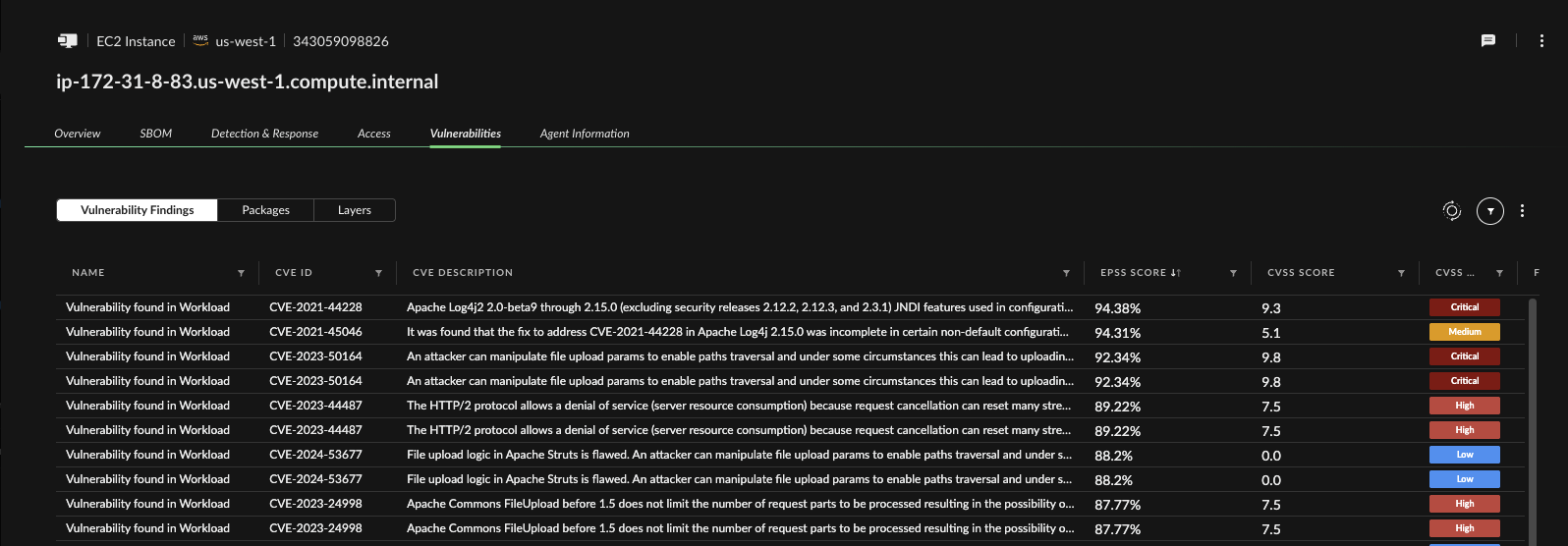
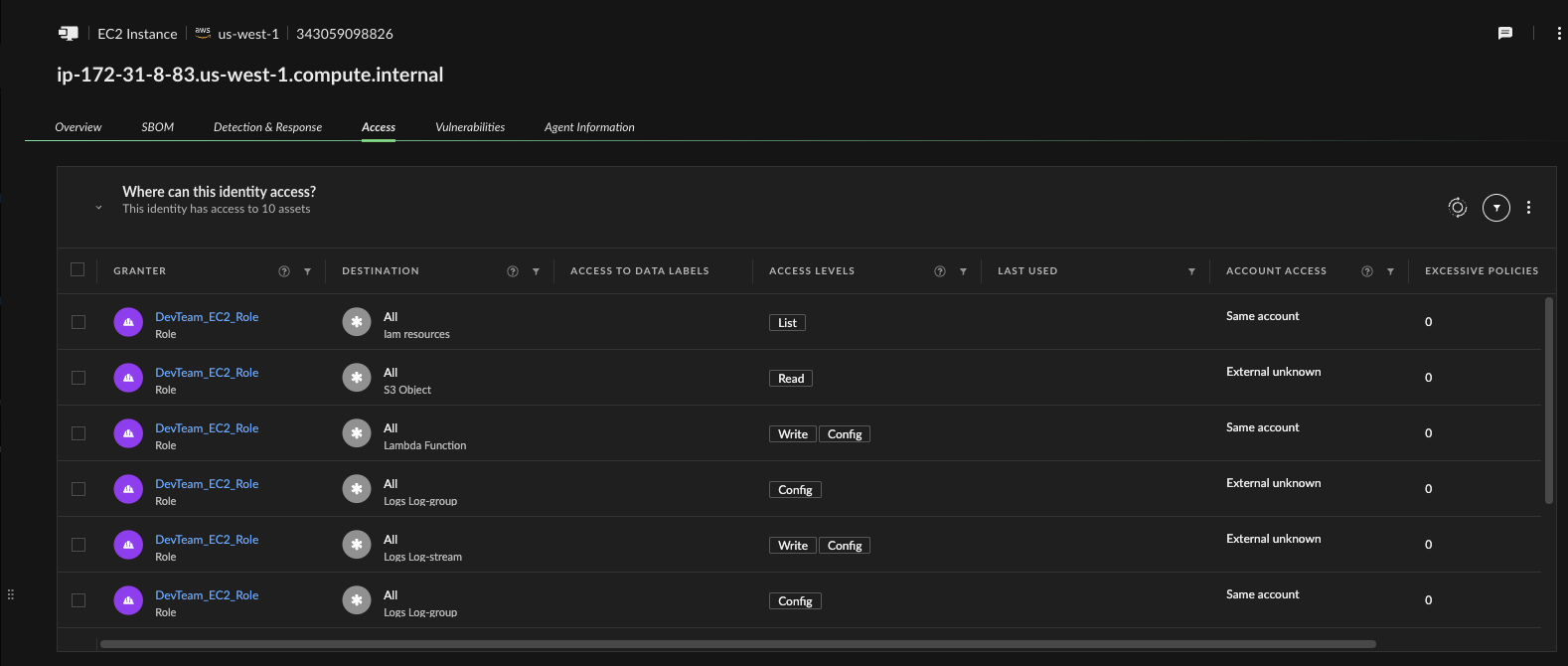
Why This Works: Turning Data into Intelligence
Cloud-native environments generate more data than most security teams can meaningfully use. Logs pile up, alerts multiply, signals arrive from every direction. But, without structure or context, all that data offers little in the way of clarity.
Cortex Cloud changes that. When a runtime event triggers, the platform doesn’t scramble to assemble context — it already holds the relationships between data points. This is only possible because all signals feed into a common dataplane that lives at the heart of the Cortex platform. It’s what allows Cortex Cloud to immediately surface correlated case views, connect the dots across the cloud ecosystem, and hand off investigation context between CloudSec and the SOC without delay.
See the Full Attack Chain in Real Time
Cortex Cloud doesn’t just ingest signals — it builds an impactful narrative. It correlates runtime activity with deployment context, posture data, and identity configurations to surface meaningful incidents as they unfold. CloudSec teams see not just where a threat landed, but how it moved, what it touched, and which risks made the attack possible.
Act with Confidence, Not Guesswork
An alert is only as useful as the action it inspires. Cortex Cloud enriches every alert with relevant context. CloudSec analysts don’t need to bounce between dashboards or request logs from other teams. They can make decisions on the spot because every signal comes tied to its root cause, blast radius, and associated risk.
Respond in Minutes
Decisions made in the first minutes of an incident shape its outcome. Cortex Cloud doesn’t just enable speed — it enables decisiveness. Teams can take action based on correlated evidence and prioritized impact. No more chasing low-fidelity alerts or waiting for human triage.
Automate What Matters Most
Context unlocks speed. Cortex Cloud enables automated playbooks that isolate workloads, revoke risky permissions, or block exploit paths as soon as a threat is confirmed. Because incidents arrive fully formed — with correlated evidence and recommended next steps — CloudSec teams can move directly to remediation.
That speed shrinks dwell time, closes exposure windows, and reduces the likelihood of missteps in a high-stakes moment.
Bringing CloudSec into the Future
The demands on CloudSec teams aren’t leveling off. In fact, they’re compounding, fueled by faster development cycles and expanding cloud architectures.
Staying ahead means more than spotting issues. It takes real-time insight, context that spans from code to cloud to SOC. It hinges on the ability to act before adversaries gain ground.
Cortex Cloud delivers clarity, driving the right response without delay.
Learn More
Have you seen Cortex Cloud in action? You’ll want to. Schedule your demo today.