Ransoms have come a long way since the days of a note constructed of cutout magazine letters being dropped in a target’s mailbox. As with many other threats, they have evolved, becoming more sophisticated and perilous. The same is true for today’s web threat landscape.
With organizations struggling to keep up with adversaries’ advanced methods, the web has been left wide open for malicious attacks like phishing, malware, ransomware, and data theft. But among these different threats, ransomware has proven to be one of the most costly attacks and continues to thrive.
Ransomware attacks are constantly evolving, affecting organizations regardless of size, industry or location. According to research done by Palo Alto Networks Unit 42 threat intelligence research team, in 2021, the names and proof of compromise for 2,566 victims were publicly posted, marking an 85% increase compared to 2020. One of the leading factors contributing to this growth is the use of Ransomware-as-a-Service (RaaS). RaaS is a business run by cybercriminals, for cybercriminals, making the tools to launch ransomware attacks widely accessible for adversaries of all skill levels in exchange for monthly fees or a percentage of ransoms paid. Because of RaaS, the barrier to entry has been lowered, increasing the volume and frequency of ransomware attacks. And while ransomware attacks become more common, it is expected that the cost of these attacks will continue to grow.
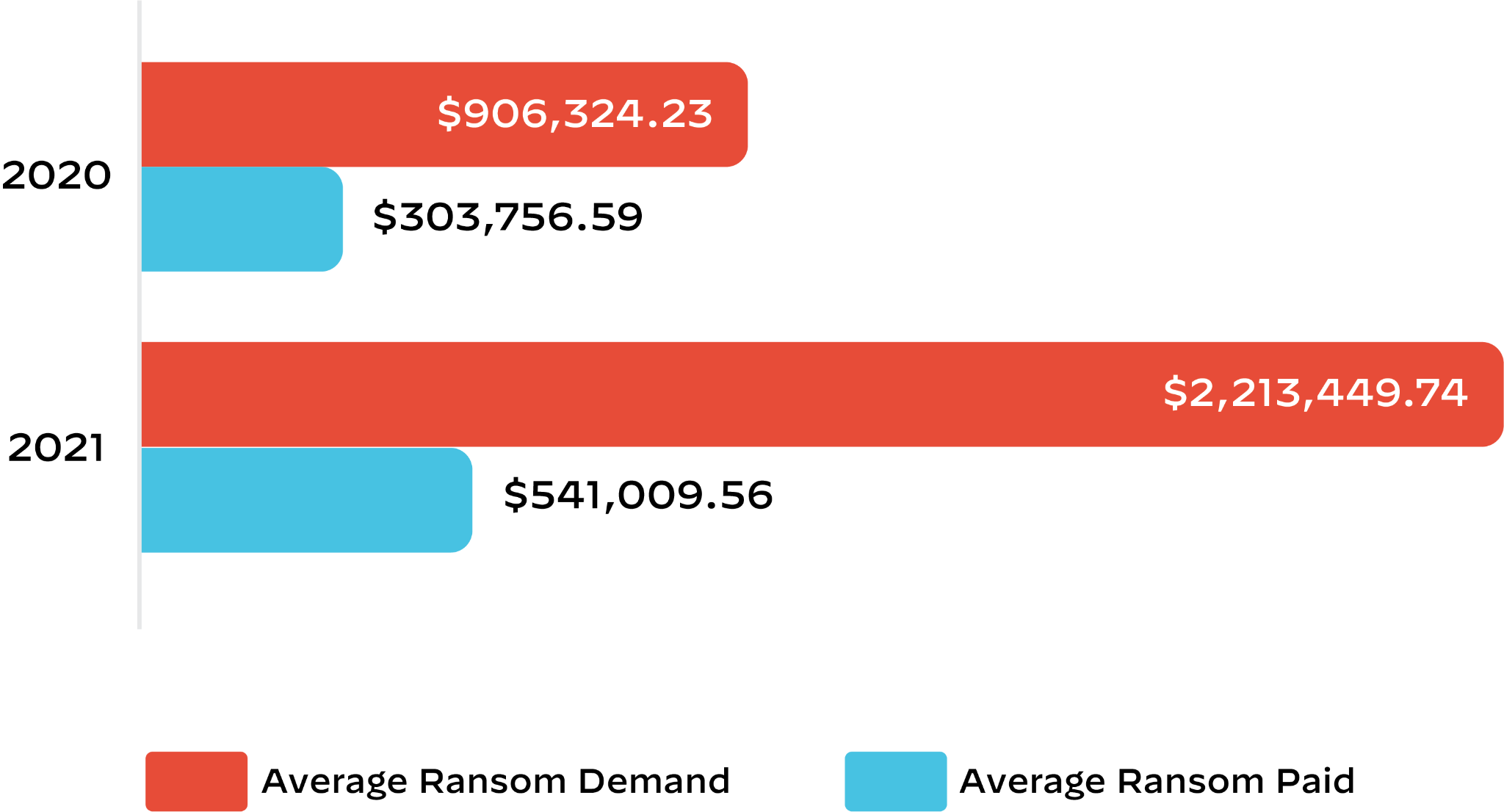
According to Palo Alto Networks Unit 42 threat intelligence research team, the average demand of a ransomware attack in 2021 was $2.2 million, a 144% increase from 2020, while the average payment was $541,000, a 78% increase from the previous year. As ransomware attacks become more frequent and payout demands soar, organizations are biding their time until they become the next target.
One of the most common ways adversaries deliver ransomware is through phishing emails, where their intent is to trick victims into clicking a malicious link or downloading an attachment that will then install ransomware on their device. Therefore, ransomware protection requires a two pronged approach, prevention of malware files and access to malicious domains (URLs). Studies have shown that 78% of organizations in 2021 received a phishing email loaded with ransomware or a link to download ransomware. Knowing that phishing is extremely common and its ties to ransomware attacks, it is more important than ever for security teams to prevent it. Studies have shown that 90% of today’s security incidents include phishing, yet organizations still struggle to prevent them to this day. This is largely due to the various evasion techniques threat actors use to bypass security defenses. Common techniques for a malicious website to avoid detection include:
- Use of new and never-before-seen URLs. Attackers can easily bypass defenses by generating never-before-seen URLs that traditional offline web-crawlers fail to detect.
- Hiding malicious content through cloaking. Since web-crawlers do not analyze live web traffic, attackers can cloak malicious intent by first sending security scanners to benign content or a blank page before eventually launching the phishing page.
- Multi-step attacks and CAPTCHA challenges. Adversaries hide phishing content behind a series of benign steps, such as CAPTCHA challenges, to prevent web-crawlers from detecting the actual malicious content behind them.
- Single-use and short-lived links. With the help of automation tools, it is now cheaper and easier than ever before to generate a vast amount of new, never-before seen URLs. This allows adversaries to use a phishing page for mere seconds or minutes before switching to a new URL, making it difficult for security databases to track.
- Attacks within compromised websites. Attackers compromise legitimate and benign websites to establish a phishing page within it, allowing them to easily clear security defenses.
Adversaries have combated traditional security with these evasive techniques, allowing them to bypass security with ease. In fact, 90% of today’s phishing kits include at least one of these evasive techniques. Unfortunately, this puts an immense amount of pressure on SOC teams to properly secure the web and prevent their organization from becoming the victim of a ransomware attack. No longer able to rely on legacy security using outdated methods, organizations need to adopt a solution with specific capabilities suited to detecting and preventing highly-evasive threats.
Palo Alto Networks has revolutionized web security with its Advanced URL Filtering solution, introducing the industry’s only inline web protection engine that can detect and prevent evasive threats like phishing and ransomware attacks, all in real time. Using next-level analysis and inline prevention capabilities through the use of our inline deep learning modules, customers can defend against highly-evasive phishing attacks and avoid becoming the victim of a ransomware attack. Advanced URL Filtering offers visibility into categorized threats like ransomware, giving SOC teams the knowledge and context they need to create and enforce policies.
Unfortunately, web-based threats like ransomware are constantly evolving and can threaten an organization in multiple ways, which is why SOC teams must have a holistic approach to security. Palo Alto Networks offers best-in-class cloud-delivered security services, such as Wildfire, Advanced Threat Prevention and DNS Security, that all work together to ensure your entire enterprise is protected. Whether it be blocking malicious URLs used for ransomware, preventing data exfiltration through command-and-control attacks, or inspecting a malicious file loaded with malware, these best-in-class services give customers comprehensive protection against ransomware attacks.
To learn how you can use Advanced URL Filtering to stop your organization from falling victim to ransomware attacks, visit Palo Alto Networks.
To better help you identify any vulnerabilities and risks in your business, request a complimentary Security Lifecycle Review assessment. This evaluation will give you actionable intelligence and recommendations on how to reduce your organization’s overall risk exposure. Request your free assessment today.