For more than seven years now, cloud security posture management (CSPM) tools have provided cloud asset visibility, detected risky misconfigurations and monitored compliance posture for organizations. The emergence of cloud-native application protection platform (CNAPP) solutions has transformed modern CSPM, shifting its focus from detecting misconfigurations to managing all cloud infrastructure risks — vulnerabilities, public exposures, excessive privileges and more.
Organizations have stayed ahead of adversaries through security modernization. Still, attackers will never stop innovating. According to The State of Cloud-Native Security Report 2024, 38% of cloud security professionals consider AI-powered attacks a top concern.
With adversaries using artificial intelligence to deliver higher volume and more sophisticated attacks, it’s become more important than ever to rapidly close out risk gaps. CSPM (and CNAPP) providers must equip organizations with AI-powered defenses. Here’s how adopters should use these tools to their advantage.
Where Is My Top Risk? Ask, Don’t Search
When newsworthy vulnerabilities emerge, security teams struggle to identify, prioritize and remediate the impacted machines. An alarming truth is that attackers can scan the internet for exposed vulnerabilities in minutes, but organizations take more than three weeks on average to remediate a critical exposure.
What’s also concerning is that between January 1, 2024, and today, more than 1,600 critical vulnerabilities have emerged, averaging over 9 per day.
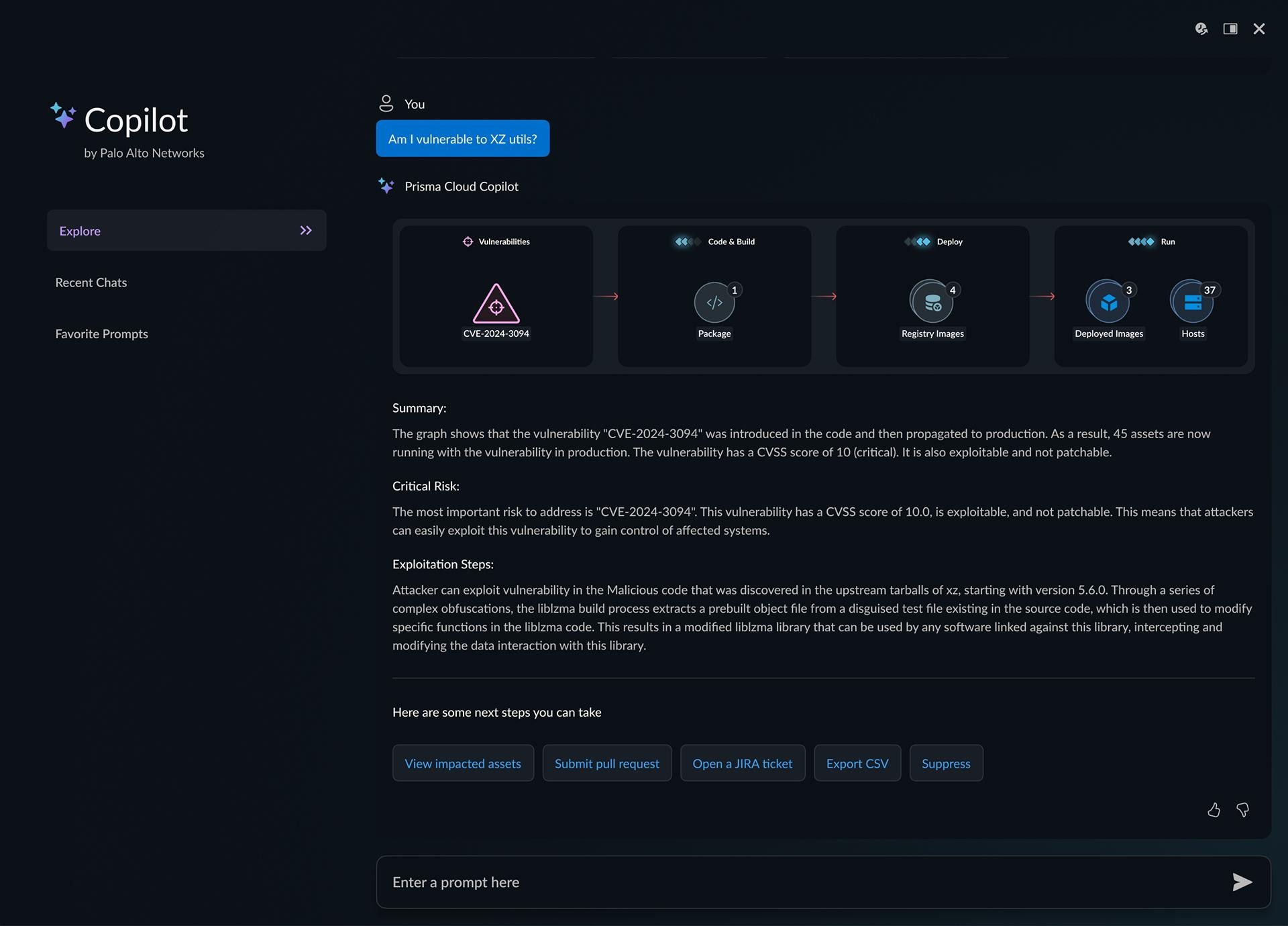
Using AI, security teams should be able to ask simple questions to overcome challenges. What are my top risks? Am I vulnerable to XZ Utils?
When pressing zero-day vulnerabilities arise, such as log4j or XZ Utils, having a copilot should go beyond identifying where CVEs exist. They need to answer real questions.
- Where do I have this vulnerability publicly exposed?
- Where did the vulnerability come from? (from cloud all the way down to the source code)
- How can I remediate the issue at the source?
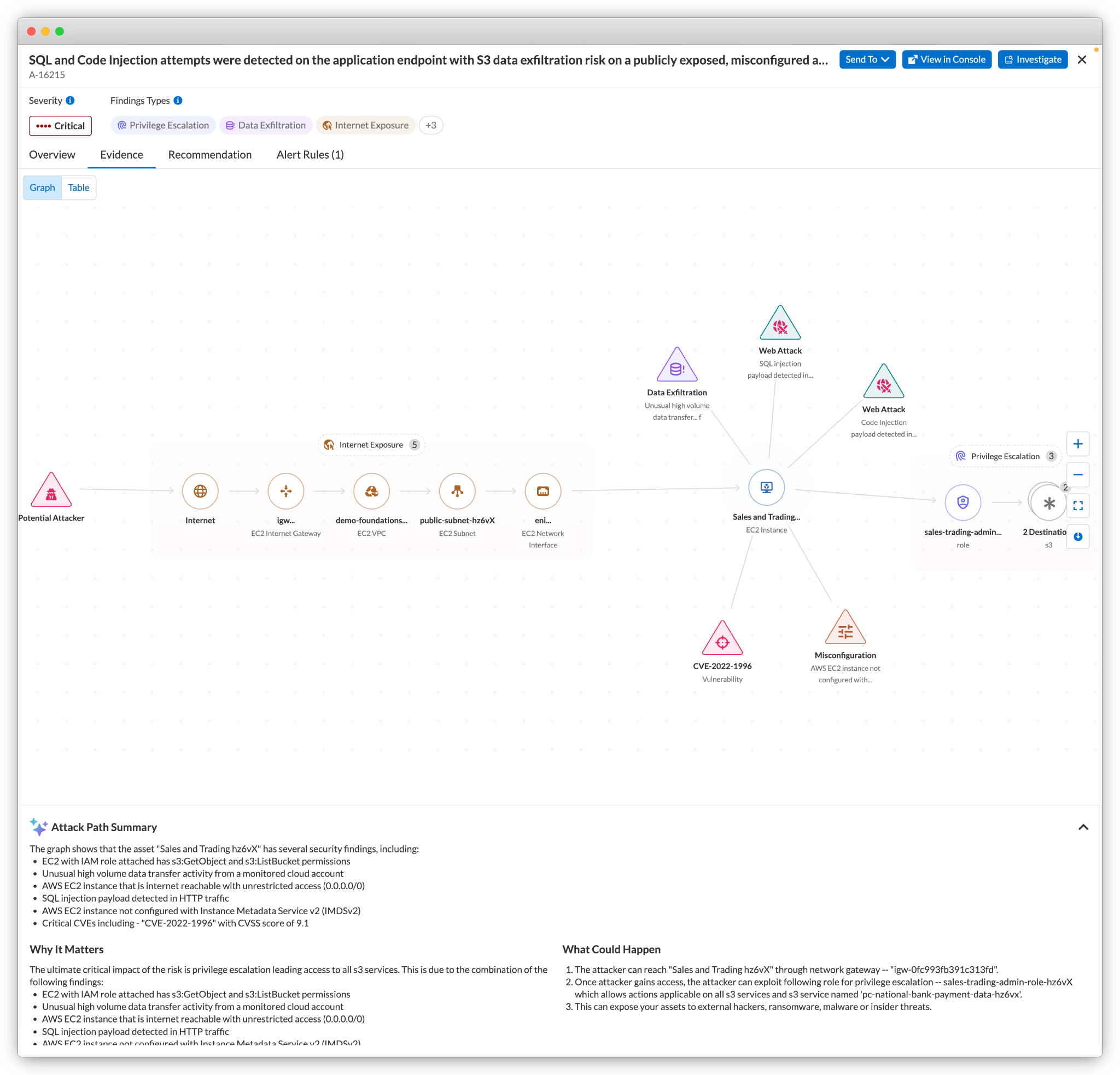
Uncover Highly Complex Attack Paths
CSPM not only identifies a broad set of risk signals but also correlates data points to pinpoint related misconfigurations and vulnerabilities that increase the chances of an attack. Modern CSPM approaches accomplish this through policies that flag various combinations of risk signals.
AI-powered security continuously analyzes your cloud stack, precisely connecting insights from across your environment. Additionally, use AI to gain context, such as why the risk is critical and how an attacker could exploit the pathway.
Spotting open entry points for attackers is just the beginning of triaging attack paths. Security teams should understand the impact of potential attacks and all possible lateral movement pathways to their crown jewels. With AI-assisted technology, organizations can model the possible pathways an adversary could take from the initial asset and understand how a potential attack could spread before a breach even occurs.
Increase Remediation Efficiency
Once security teams discover issues, the remediation steps can take weeks or months to complete. With AI, organizations should have autogenerated analysis, detailing remediation recommendations and the best action to take — whether it’s opening a ticket or applying automated remediation.
A Code to Cloud™ platform can perform a root causes analysis on cloud risks. It can, for example, trace a cloud misconfiguration back to the infrastructure-as-code template that caused it. With AI, security teams should get the optimal remediation workflow for addressing cloud misconfigurations and vulnerabilities, such as correcting an IaC template or opening a pull request with the responsible developers.
How Prisma Cloud Can Help
Prisma Cloud, the Code to Cloud platform secures applications across the full lifecycle. The platform offers the Prisma Cloud Copilot, designed with Precision AI, helping organizations know exactly what risks to focus on and which actions to take, simply by having a conversation.
Rapidly prioritize with AI: For every threat, quickly understanding what’s reachable and how best to fix it is paramount. Prisma Cloud employs AI-powered risk prioritization to analyze the blast radius from at-risk assets, enabling your teams to uncover complex risks with ease.
Don’t just ask. Act: Eliminate the need for specialized expertise. Simply have a conversation and get the answers you need, fast. Prisma Cloud Copilot analyzes vast amounts of data from code to cloud to help you fix faster and prevent breaches — all with a single click.
Learn More
Want to learn more about what Prisma Cloud can do? Book a personalized demo or donwload our latest e-book, Defending Your AI Future with Prisma Cloud.