Today’s enterprises use a combination of hosts, containers and serverless architectures to power their business applications. As these organizations begin to scale these diverse environments, most find that it is not sustainable to manually detect and confirm configurations for each resource.
In the January 2021 release for Prisma Cloud we added the ability to automatically scan Amazon Web Services (AWS) accounts and discover all cloud hosts to determine their protection coverage. Discovery is done via AWS APIs, without any agent installation, and only requires an authorized service account.
Now as part of the April 2021 release we are expanding this capability for even better visibility and control for cloud hosts, with:
- Auto-discovery of cloud hosts on Google Cloud and Microsoft Azure.
- Auto-protection for AWS hosts.
Why Automated Protection is Needed for Hosts
Unprotected virtual machines present compromise points for enterprise security. Without protection, organizations lack continuous vulnerability management, compliance monitoring and runtime protection, as well as capabilities like host audit log analysis, file integrity monitoring (FIM), malware detection and more.
With Prisma Cloud Defender installed on a cloud VM, security teams can quickly see vulnerability and compliance data, and implement protections for their applications at runtime. Additionally, teams can enable custom compliance rules, vulnerability policies, and other powerful runtime protection capabilities like the ones described above.
Unlike traditional datacenter hosts, cloud hosts are primarily deployed via templates or command line interface/quick-launch flows. This results in churning virtual machines on-demand, with greater frequency.
Prisma Cloud provides security and DevOps teams quick visibility into any unprotected VMs, with automatically-delivered protection for ones on public clouds, thus removing blind spots.
Auto-Discovery for Public Cloud VMs
To enable auto-discovery for VMs on Azure and Google Cloud, users just need to add the accounts to Prisma Cloud and kick off a discovery scan, the same way they already do for AWS.
The scan identifies all instances across all regions within those accounts and populates them in Cloud Radar.
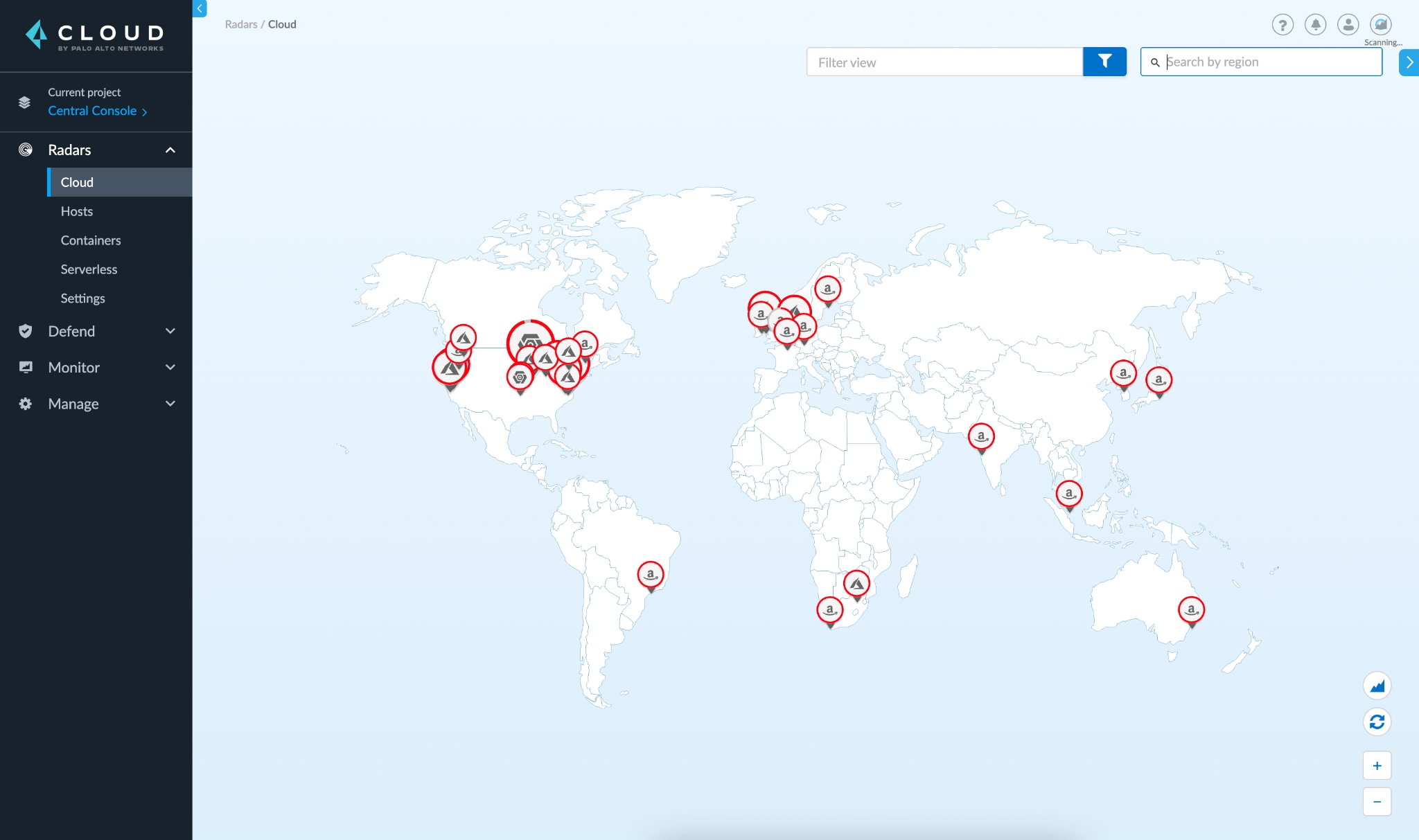
Users can then drill down into the specific cloud provider and region to view the details of the discovered assets, including security coverage status.
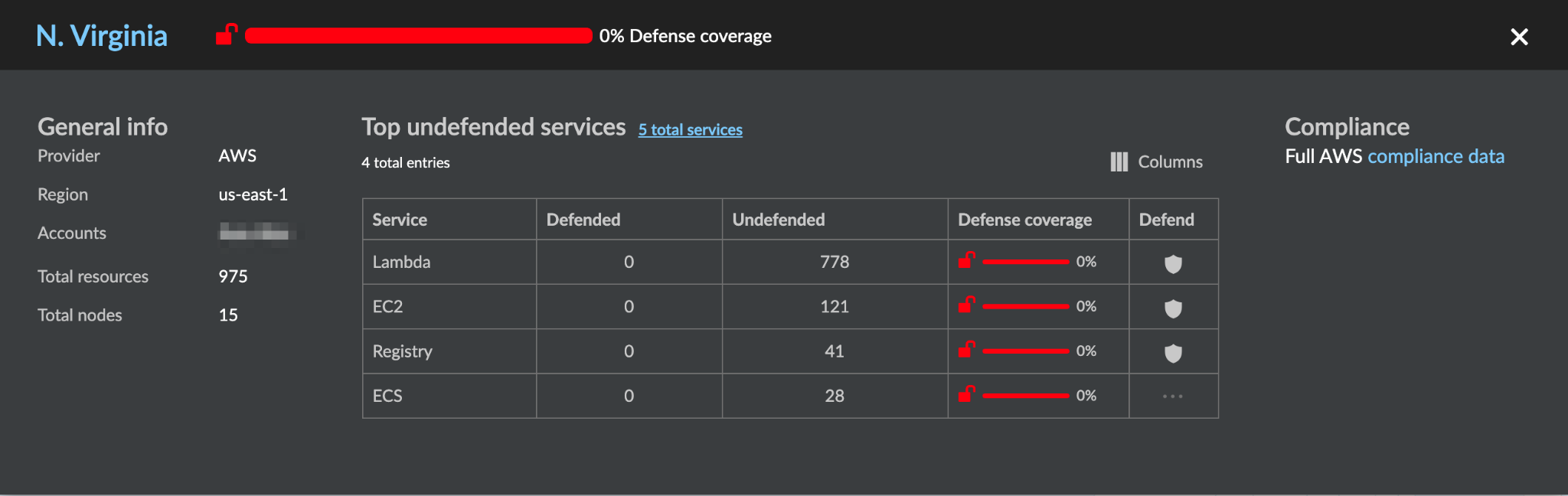
Auto-Protection for AWS Hosts
While gaining visibility of all cloud hosts is important, being able to automatically provide security coverage is even more important. Prisma Cloud now provides an auto-protect capability to automatically install Defenders on cloud hosts discovered in AWS accounts.
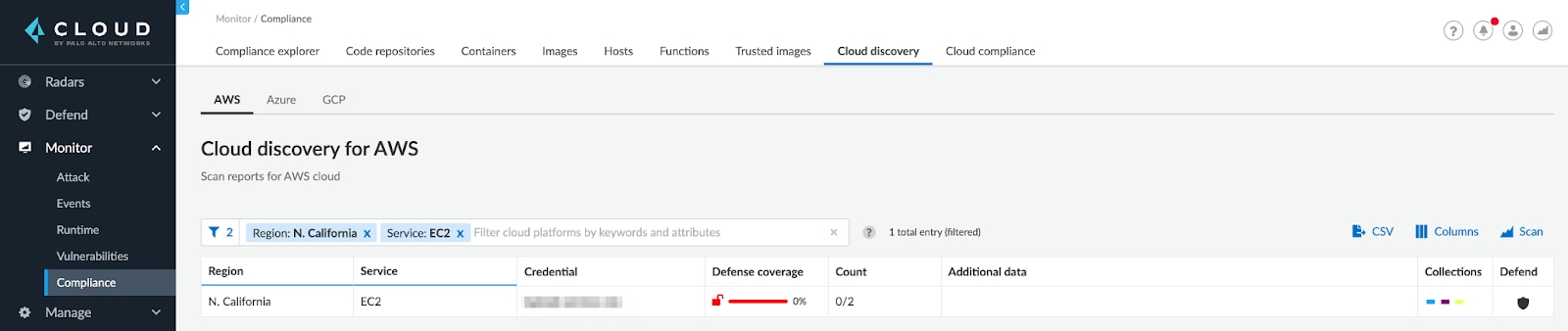
Users can create one or more rules, and use filters like account, region and tags to further target hosts in specific areas of their deployments.
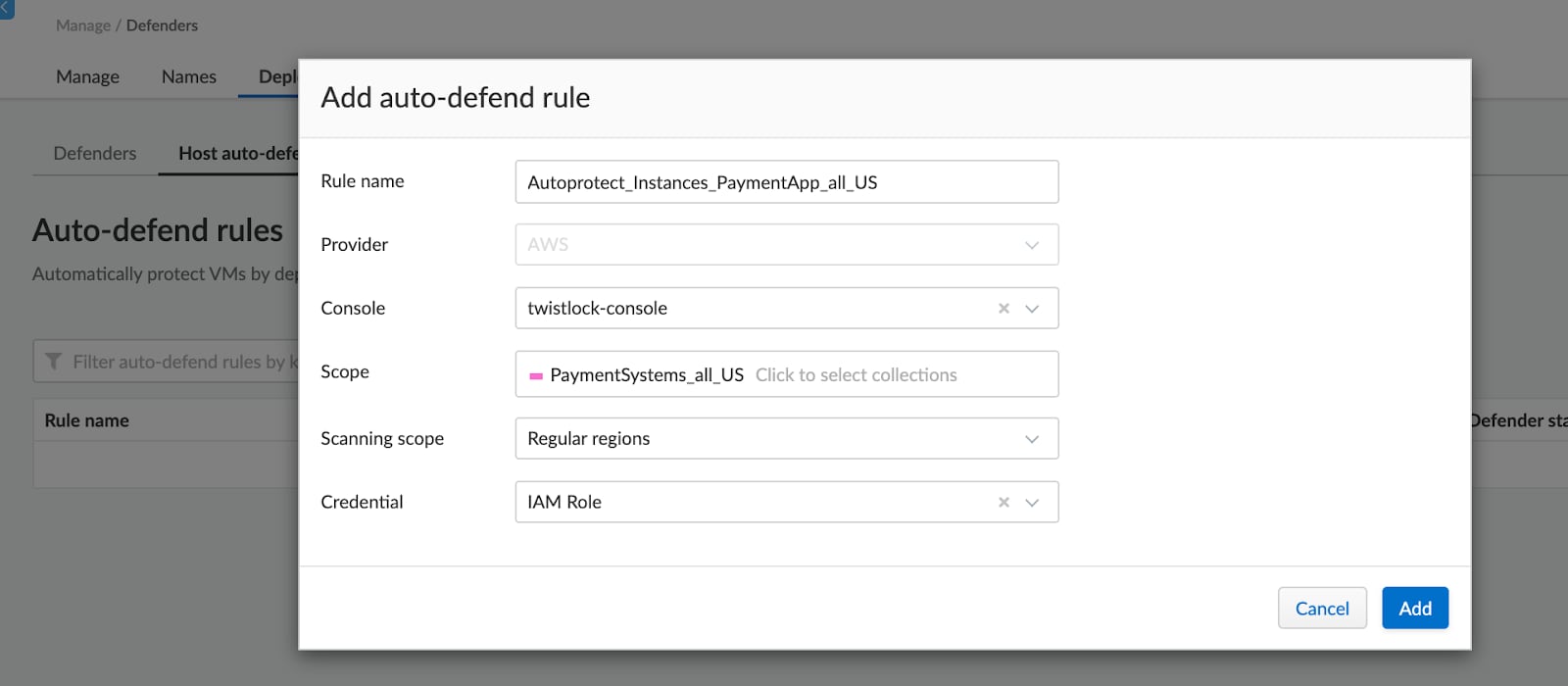
The rule deploys defenders immediately, and can be run periodically to cover any new hosts that have been spun up.
Auto-protection for AWS relies on a set of access permissions to the AWS API and utilizes AWS System Manager (SSM) to install the Defenders.
As a part of the 21.04 release, Prisma Cloud provides auto-protection for Linux hosts in AWS. Coverage for Google Cloud and Azure will be added in upcoming releases.
Conclusion
Auto-discovery gives you a full inventory of all of your protected and unprotected cloud hosts across AWS, Azure and Google Cloud. Auto-protect takes that a step further to automatically deploy Defenders to protect your Amazon Elastic Compute Cloud (EC2) instances without any manual installation. This lowers the friction involved in gaining visibility and security for your cloud assets.
You can learn more about securing diverse architectures into runtime with our latest ebook, Why and How to Add Runtime Defense to Your Cloud Security Strategy. And for technical reference, please refer to the auto defend hosts section in our documentation.