Prisma Cloud extends innovative Cloud Infrastructure Entitlement Management capabilities to Microsoft Azure to enable multi-cloud entitlement analysis and protection against excessive permissions.
As organizations increasingly adopt Infrastructure-as-a-Service (IaaS) models for cloud development, the number of entities that are granted access to critical infrastructure necessarily grows as well. However, organizations must ensure these entitlements are tightly controlled. Gartner recently reported that "the vast majority of granted entitlements in IaaS are unnecessary. More than 95% of accounts in IaaS use, on average, less than 3% of the entitlements they are granted, which greatly increases the attack surface for account compromises."
To help our customers better address these growing risks, we are releasing a comprehensive expansion of our Cloud Infrastructure Entitlement Management (CIEM) solution within Prisma Cloud:
- Cloud Infrastructure Entitlement Management (CIEM) for Azure: Net-effective permissions analysis and visibility for accounts, resources, and workloads managed by Azure.
- Azure AD integration: Ingest single sign-on (SSO) data from Azure AD to calculate net-effective user permissions, no matter which CSP or service the user is accessing.
CIEM and CSPM Work Together to Addresses Security Gaps
Security teams have become adept at monitoring resource configurations, ensuring compliance and detecting threats – collectively known as Cloud Security Posture Management (CSPM). However, controlling user access and permissions is equally important, and most CSPM solutions can’t monitor user privileges.
Even a single misconfiguration in these controls can be massively damaging. In 2020, Unit 42 researchers demonstrated how IAM misconfigurations could be used to obtain admin access to an entire Amazon Web Services (AWS) cloud environment – a potentially multi-million dollar data breach in the real world.
CIEM tools address this gap, going beyond what traditional identity governance and administration (IGA) and privileged access management (PAM) tools offer to address the unique challenges of cloud environments. For example, they can provide visibility into ever-changing IaaS architectures, or offer automated suggestions to remediate excessive privileges across multiple cloud providers.
The Difficulty of Securing Identities in the Cloud
There are several factors that make it difficult to calculate the minimum level of access a user or entity needs to perform a role – known as the principle of least privilege.
First, each cloud service provider (CSP) uses different definitions of controls for users that are authenticated (signed in) and authorized (have permission) to modify infrastructure. There are competing and overlapping controls that can be attached to any given user.
Then, there is the volume of possible entitlements. In the same report linked above, Gartner noted that the average number of distinct entitlements across cloud providers now exceeds 5,000. Manually calculating how any one of those entitlements affects net-effective permissions is effectively impossible.
Finally, there is simply an inherent level of risk in users having access to cloud infrastructure. These users have privileged access to resources, permissions, and data. Developers and DevOps teams need this kind of access to execute efficiently, but this must be balanced against broader risk management considerations.
These issues are why Prisma Cloud has pioneered the integration of Cloud Security Posture Management (CSPM) with Cloud Infrastructure Entitlement Management (CIEM) capabilities. The combined functionality helps users apply the same level of precision and certainty needed to confidently administer large-scale, multi-cloud environments to an increasing number of entitlements that come with them.
New Innovations for Securing Cloud Infrastructure Entitlements
The latest innovations to Prisma Cloud put a greater number of cloud entitlements under users' direct control, with features that significantly reduce the work needed to understand and remediate entitlement issues.
Cloud Infrastructure Entitlement Management (CIEM) for Azure RBAC
Available: Today
Prisma Cloud can now calculate and analyze net-effective permissions, monitor for risky and unused entitlements, and offer least privilege recommendations for Microsoft Azure cloud accounts managed with Azure RBAC, in addition to Amazon Web Services (AWS).
Visibility to Net-Effective Permissions
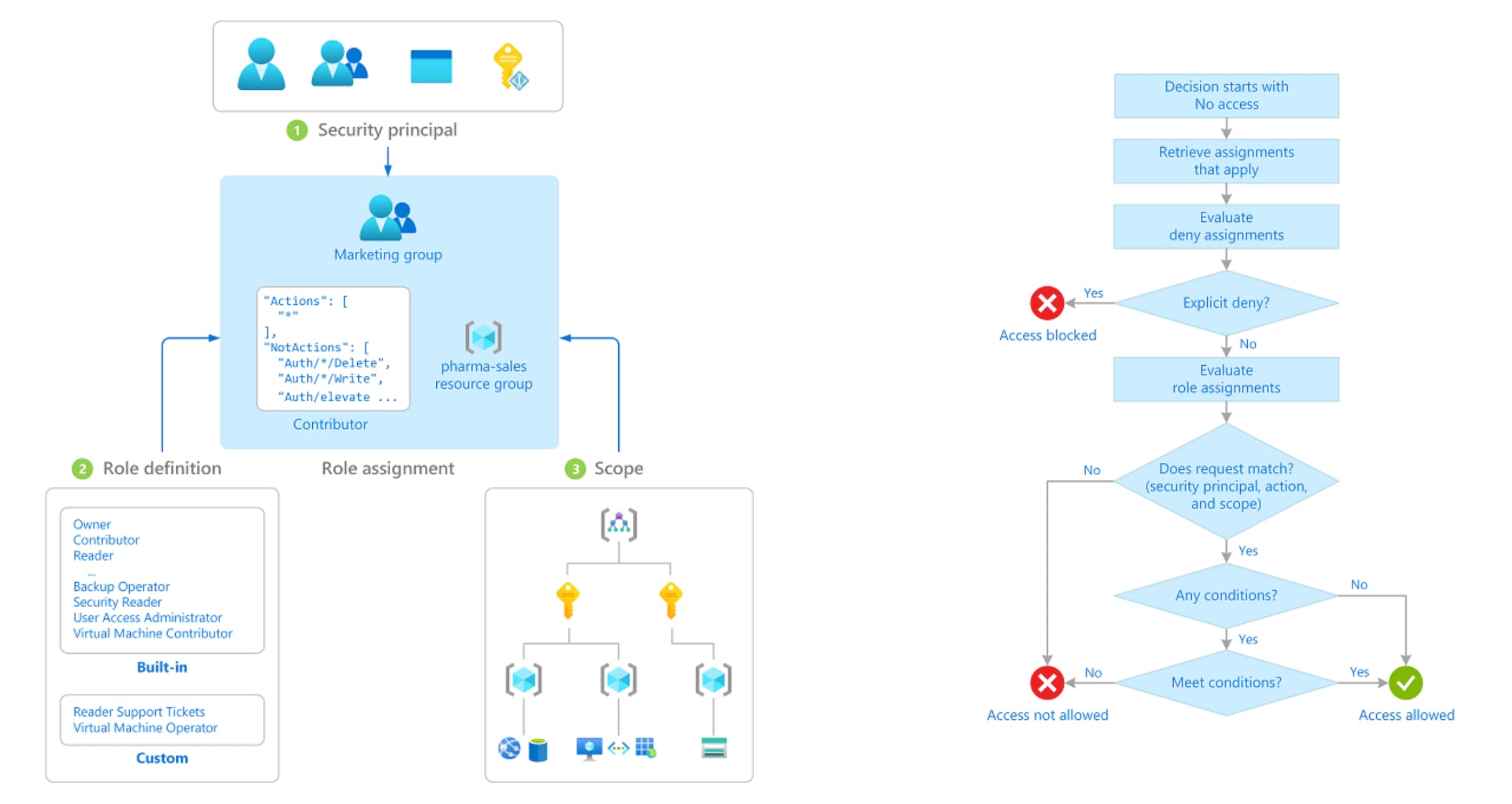
Get detailed visibility of which users have the ability to perform a given action, and on which resources. Prisma Cloud can precisely determine net-effective permissions by analyzing and correlating entitlements granted through role assignments including security principals, role definitions and scopes.
Rightsizing Permissions
Cloud Infrastructure Entitlement Management (CIEM) includes specialized, pre-built policies that help detect risky entitlements and remove excess privileges to cloud resources. Once your Azure account is onboarded, it can automatically begin detecting overly permissive user access, then provide suggestions to right size them to achieve least privilege
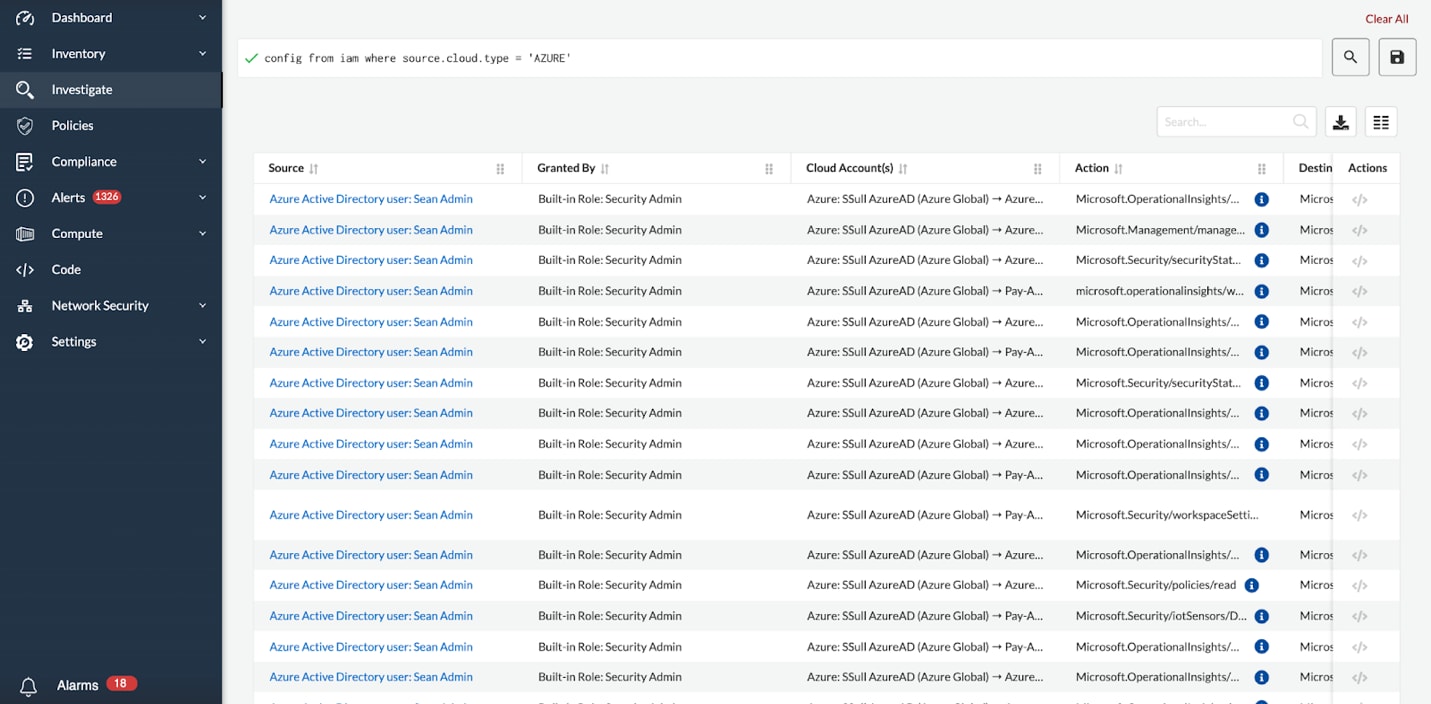
Investigate Cloud Infrastructure Entitlements
Customers can gain deep insights into specific entitlements using Prisma Cloud Resource Query Language (RQL). Examples of identity-related questions include:
- What users have access to resources A, B and C?
- What accounts, services, or resources can User_1 access?
- Is resource Y accessible to the entire company?
You can view the documentation on Prisma Cloud RQL to see the breadth of potential insights.
Permissions Audits for Internal Compliance
Prisma Cloud already includes a resource audit trail that captures changes made to a resource from the moment it's deployed. The permissions tab expands this information by showing the permissions “of” a resource and “to” the resource. It also lets users to look back to understand when an overly permissive entitlement was granted, and which user or entity granted it.
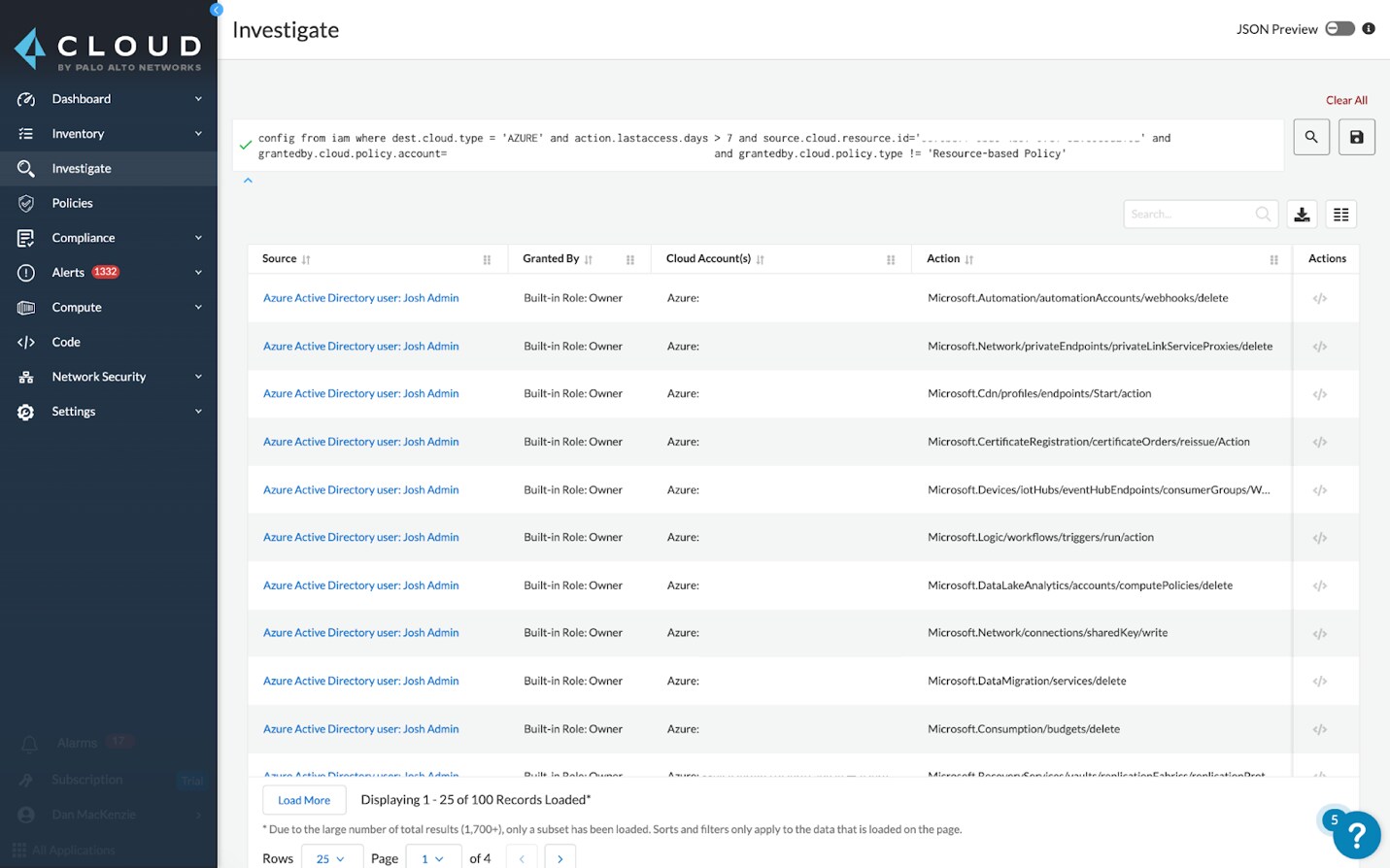
Auto Remediation
If excessive permissions are identified, Prisma Cloud will suggest the remediations needed to get the user or entity back into a state of least privilege. You can also set up automatic adjustments to help support continuous privilege enforcement.
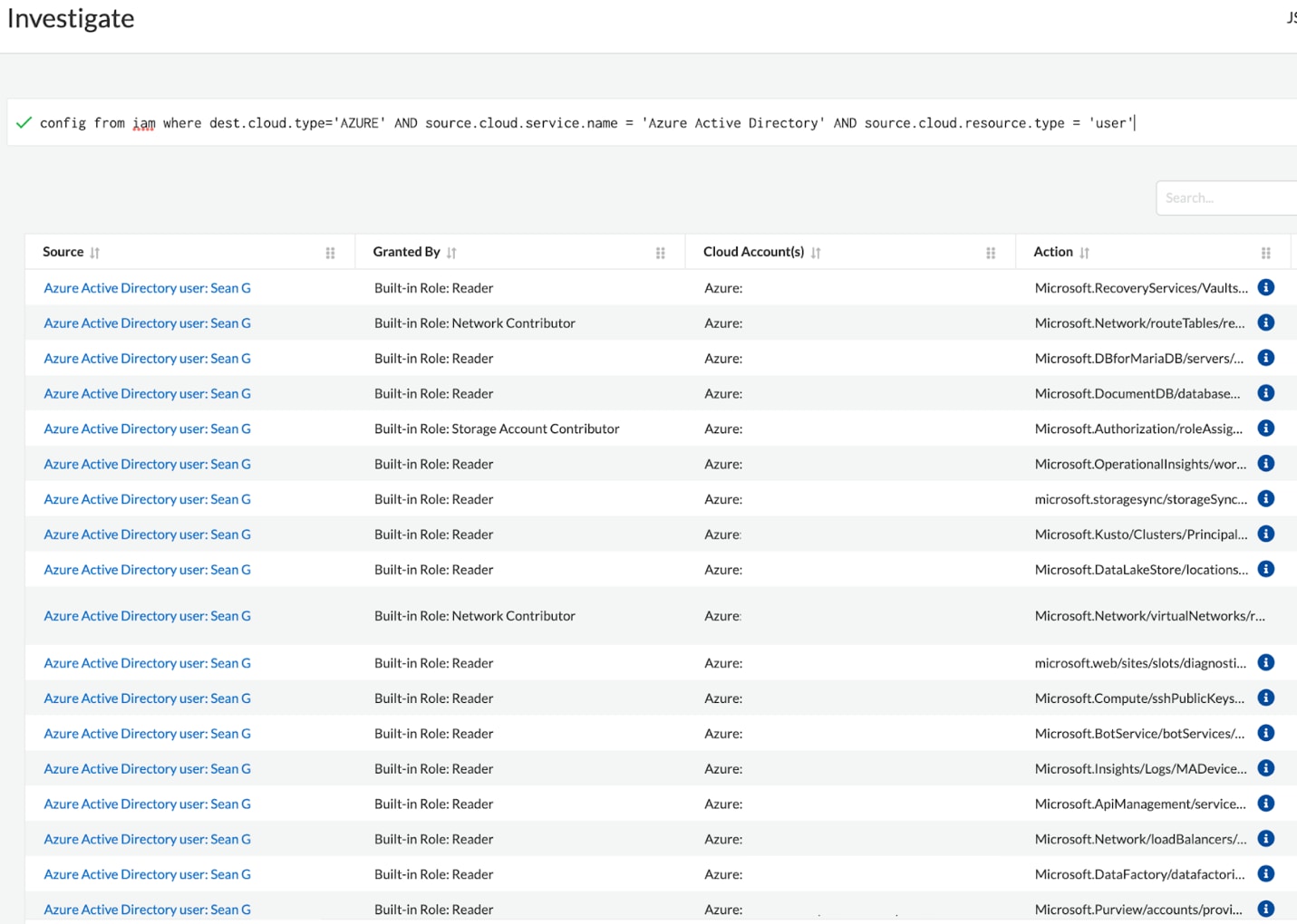
Azure AD Integration
Available: Today
Prisma Cloud now integrates with Azure Active Directory (Azure AD) to ingest single sign-on (SSO) data as part of net-effective permissions calculation. This lets users view the effective permissions of Azure AD users for any service they log in to, such as Azure and AWS. This enhances RQL functionality, helping answer identity management questions such as, Is [Azure AD User] able to create an AWS IAM user? The answer can highlight potential back doors into your cloud environment, which in turn helps you mitigate security breaches.
How to Start Using the New Enhancements
These new features are available immediately for existing Prisma Cloud customers. You can view our technical documentation to begin ingesting Azure account logs and Azure AD roles into Prisma Cloud.
You can also experience the new CIEM features along with our CSPM functionality by signing up for a hands-on trial of Prisma Cloud.