Prioritization might be the biggest challenge in modern cloud security. Cloud environments are complex, often comprising hundreds of services and thousands of cloud resources. This disparate and diffuse nature creates virtually unlimited misconfiguration and vulnerability possibilities. Chasing down and fixing every issue is impossible, even for the best-resourced organizations. Instead, security teams typically identify the most critical security and compliance risks, which developers then prioritize in remediation workflows.
Attack path analysis plays a vital role in prioritization. It enables organizations to focus on combinations of risk factors such as identities, permissions, network exposure, infrastructure misconfigurations and vulnerabilities that create dangerous openings for threat actors.
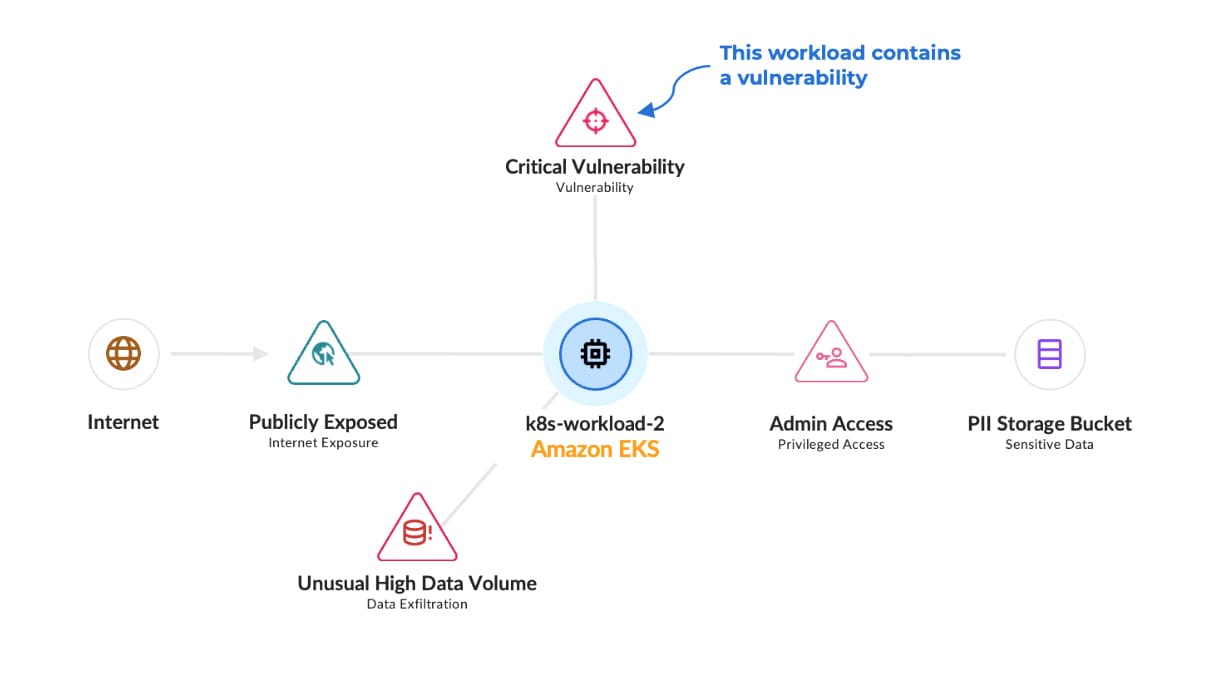
Prisma Cloud has long been a leader in attack path analysis thanks to its unified Code to Cloud™ approach. Today, we’re pleased to introduce yet another improvement. With Prisma Cloud’s latest integration of data security posture management (DSPM), organizations can now see whether specific attack paths put sensitive data at risk. Such insight can then feed into more granular prioritization or issues.
Importance of Data Context to Cloud Risk Prioritization
Data is the most frequent target for cyberattacks. Attackers are particularly interested in high-value information such as personally identifiable information (PII), financial records, and protected health information (PHI) of customers. A breach involving these types of sensitive data can lead to severe consequences — for example, regulatory fines and reputational damage — as well as harm to compromised individuals.
The nature of cloud environments and workloads exacerbates the challenge. Organizations go to great lengths to segregate sensitive records, minimize access permissions, and prevent unneeded duplication. But a foolproof way to ensure that sensitive data doesn’t flow into one of dozens or hundreds of datastores used for testing, development or analytics doesn’t exist.
A successful attack against cloud storage or databases containing sensitive data can be a much bigger problem than one against datastores containing anonymized system logs or publicly available records. Clearly, most organizations would prefer to address the former attack path first to avoid a costly data breach or severe compliance violation.
We have found that effective attack path analysis reduces 99% of alert noise, enabling developers to focus on the 1% that matters most. But 1% of thousands of potential incidents is still a lot to wade through. Adding relevant data context to the mix enables organizations to minimize the time during which their most critical assets are exposed.
Find and Block Most Critical Attack Paths with Prisma Cloud
Prisma Cloud is Palo Alto Networks Code to Cloud™ security platform — an agentless, cloud-native application security platform (CNAPP). Prisma Cloud provides complete protection for cloud infrastructure and cloud applications by combining best-of-breed capabilities, including cloud security posture management (CSPM), cloud infrastructure entitlement management (CIEM), code security, and data security posture management (DSPM).
Prisma Cloud DSPM detects and classifies sensitive data across your entire cloud or multicloud environment. It scans cloud storage, such as Amazon S3 or Azure Data Lake. It in fact scans CSP-managed infrastructure — Amazon Redshift, databases hosted on self-managed VMs or EC2 machines — in addition to database-as-a-service tools like Snowflake. In essence, Prisma Cloud DSPM scans anywhere your data lives or flows in the cloud.
Today’s feature release injects DSPM findings directly into your attack path analysis for more accurate and actionable prioritization. Now that Prisma Cloud can identify the relevant combination of risk factors, you can instantly see whether the attack’s destination node contains sensitive data, as well as recognize classifications and other relevant information.
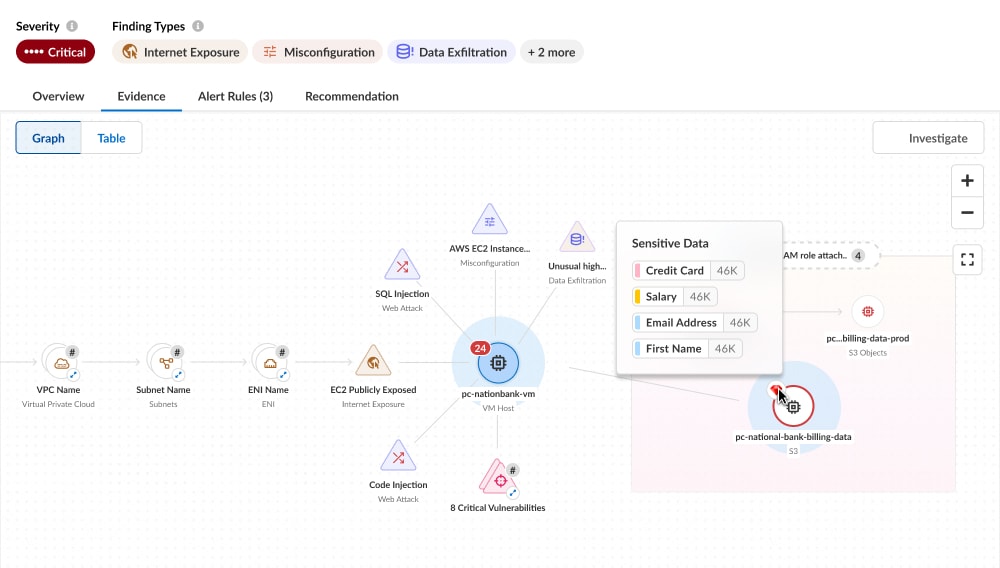
For example, a common attack path we’ve seen in data breaches includes a publicly exposed Amazon EC2 machine that hackers target to access an Amazon S3 storage bucket via privilege escalation. While this should be fixed under any circumstance, it becomes significantly more urgent when that storage bucket contains sensitive data, such as credit card numbers. Prisma Cloud’s latest addition makes it easier for organizations to find and act on these types of insights.
Even before today’s announcement, Prisma Cloud was an established leader in attack path analysis. Unlike point solutions, the Code to Cloud platform relies on a unified data model and correlates findings across the cloud ecosystem — including code, runtime and infrastructure — to suggest actions to address risks and block detected attack paths. With the addition of DSPM insights and data context, organizations can now see the final (and crucial) piece of this puzzle within a single, tightly integrated security platform.
Experience the Difference
New to Prisma Cloud? Request a free 30-day trial. And if you'd like to learn what to look for in a cloud data security provider, download a copy of The Buyer's Guide to DSPM and DDR today.