In partnership with Palo Alto Networks, Accenture has launched Secure Cloud Express, an evaluation of the client's cloud estate, both internally and externally. Palo Alto Networks Xpanse powers the external attack surface evaluation — with Prisma Cloud providing insight for the cloud infrastructure environment and Accenture delivering subject matter expertise. When combined with Accenture Cloud expertise, Secure Cloud Express 2.0 produces actionable insight for our clients. Through this partnership, in more than 50 evaluations of client cloud estates, we have seen many findings, with a few overriding themes.
Companies often don't have an accurate understanding or inventory of their cloud estate and lead clients to be unaware of many resources listed, perpetuating the assumption that resources were decommissioned. Several issues are driving this misconception, including:
Shadow IT. Departments go rogue and spin up cloud resources because IT is too slow or it's easier to bypass the IT administration. This puts the company at risk, as the compliance and security tools that protect and monitor aren't in place to guard these unmanaged assets.
Compliance and best practices are often disregarded. Many companies implement disparate protections across their cloud estate, and the controls implemented on Azure are vastly different from those on AWS. When we inquired about this, the clients mentioned that implementing similar rule sets and compliance policies across multicloud is difficult. Clients also mentioned that implementing and reporting on compliance policies is time-consuming.
What Can Be Done
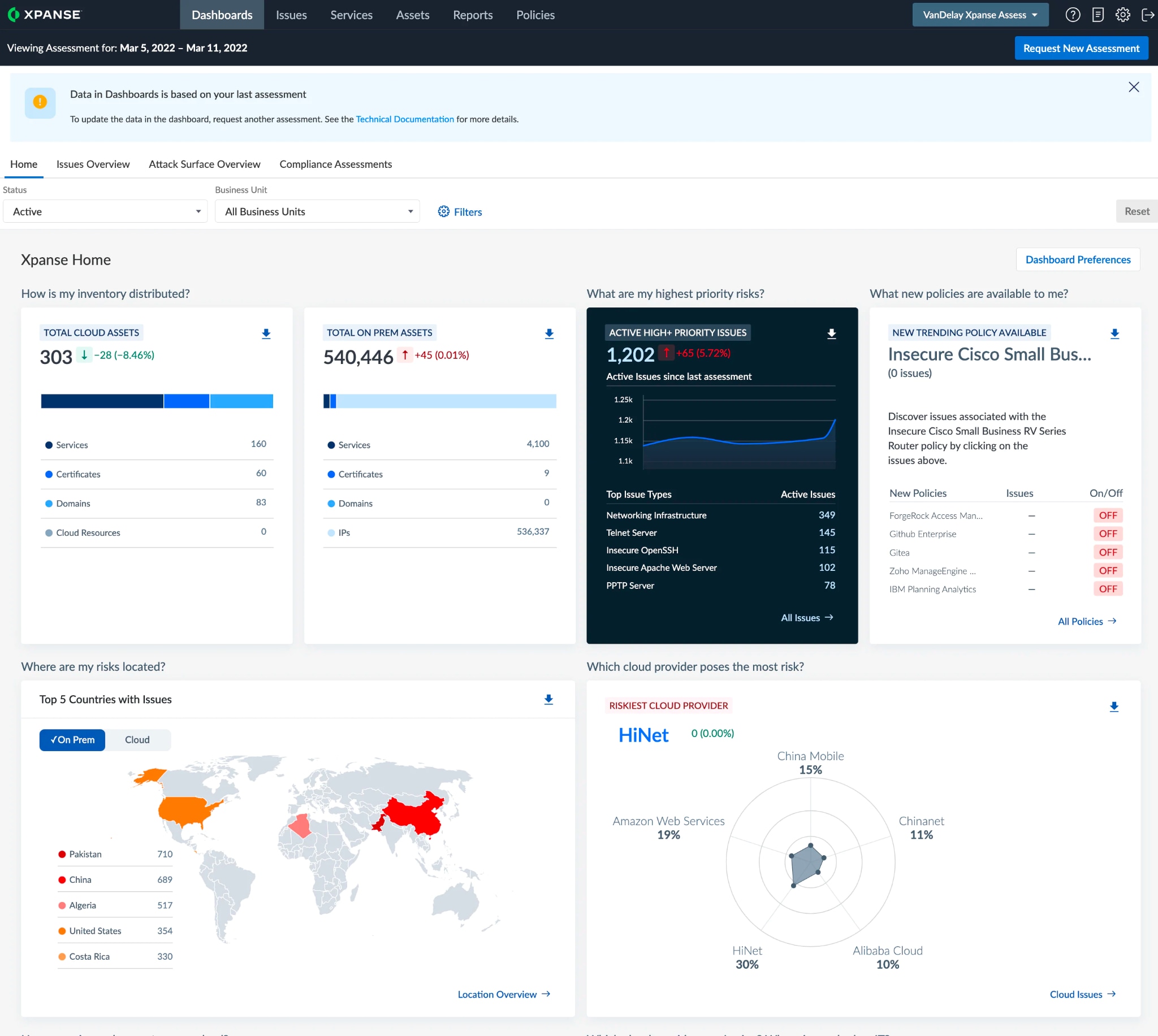
Clients need to accurately understand their complete cloud estate, both internally and externally. To address the external, attack surface management is key. Cortex Xpanse from Palo Alto Networks is an ASM tool that provides the outside-in view of the cloud estate, including shadow IT. Xpanse automatically identifies the public-facing assets, providing the client with a map of their attack surface from an attacker’s view. Xpanse commonly identifies 30% or more corporate assets to better inform vulnerability management and finds RDP and Netbios exposures for remote desktops.
Clients can't manage the unknown, which makes it essential that they accurately inventory their cloud assets. Prisma Cloud provides continuous visibility across all deployed assets from a single, unified console with over 1.5B assets monitored across customers. With automated workload and application classification across 100+ services and full lifecycle asset change attribution, cloud assets are managed and protected, reducing the risk for the company and potentially decreasing costs. 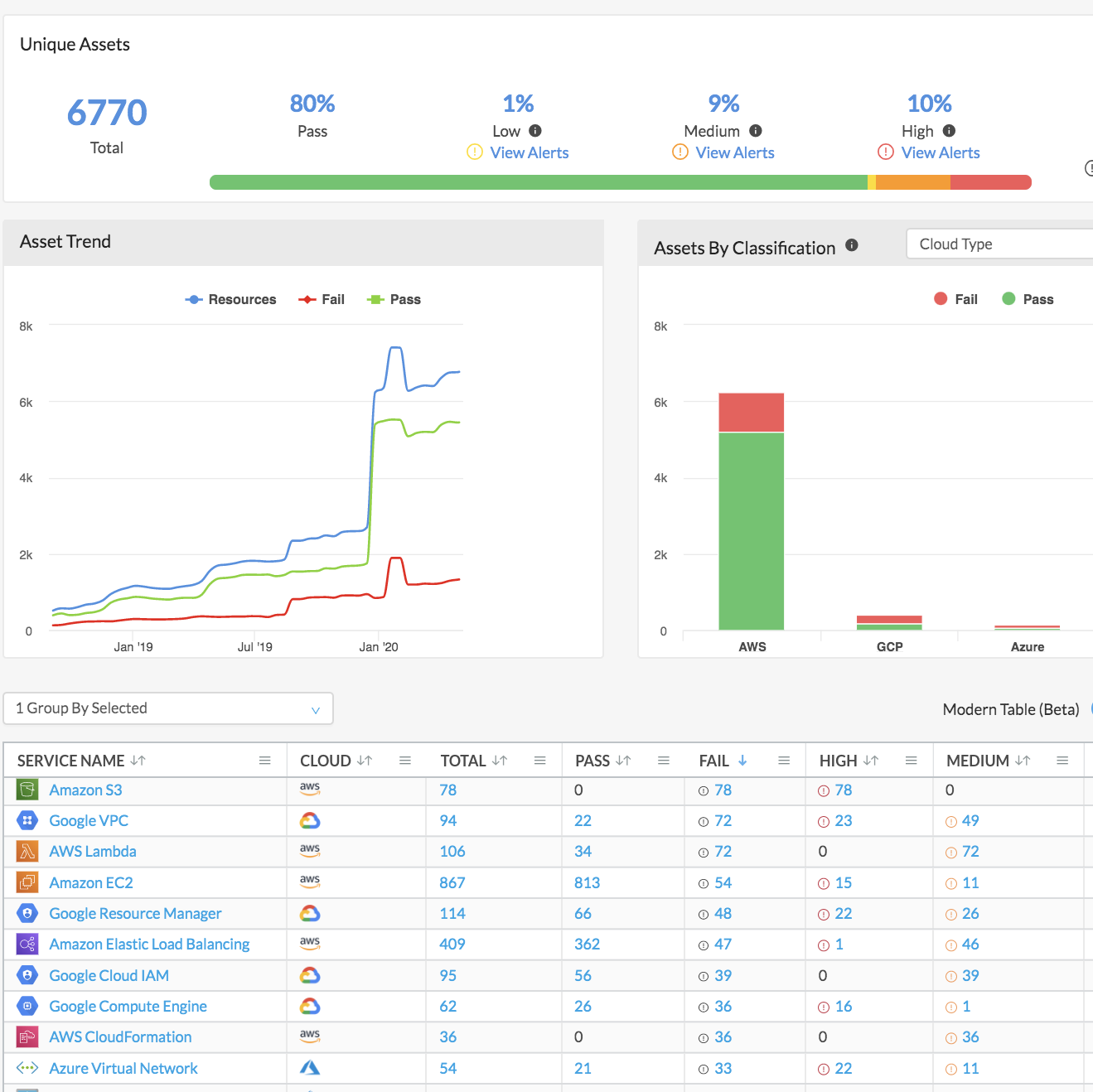
Compliance and best practices should be implemented holistically across the entire cloud estate, including multicloud environments. Prisma Cloud provides continuous compliance posture monitoring and 1-click reporting across multicloud environments, reducing human error. It supports over 26 compliance policies today and has comprehensive coverage (CIS, GDPR, HIPAA, ISO-27001, NIST-800, PCI-DSS, SOC 2, etc.) and support for custom reporting. Prisma Cloud makes it easy to investigate and auto-remediate compliance violations.
Enforcing best practices and remediating misconfigurations before an incident is key to an effective cloud security program. With Prisma Cloud, clients can enforce configuration guardrails for compliance and best practices with 600+ policies built-in across 120+ cloud services. Common misconfigurations can be auto-remediated before they lead to security incidents, and custom policies can be built once and span across multicloud environments. These are a few of the first steps needed to implement a comprehensive cloud security program.
What's Next for Secure Cloud Express?
With the launch of Secure Cloud Express 2.0, we have added two additional modules: Agentless Scanning and Security as Code. With Security as Code, we scan infrastructure as code repositories to identify configuration risks, common vulnerabilities, and exposures introduced every time a template is used. We ensure that the public access level is set to private for blob containers and that RDP access is restricted from the internet. Agentless scanning gives the team the ability to assess vulnerabilities in hosts, containers, and images on hosts. In scope are compliance assessments for K8S clusters across CSPs, including Openshift clusters. Oracle cloud is also supported for host scanning.
If you're curious about what shadow IT exists in your organization and how well compliance and controls are implemented across your cloud environments, the Accenture and Palo Alto Networks partnership can help.