Incorporate Prisma Cloud directly into your development workflows with intuitive IDE and VCS integrations.
DevSecOps, while heavily marketed, is consistently overlooked in practice. The concept of “shift left” is obvious, but due to conflicting priorities between Dev and Sec teams, it’s difficult to implement.
Imagine, if you will, the traditional approach to application security. It's a bit like building a glorious cathedral and inspecting the work only after it’s been completed. Cracks in the foundation? Leaky windows? These would have been mere inconveniences to fix early in construction. Now, though, at the end, rework and fixing problems is costly and time consuming.
The concept of shift left flips this approach on its head by embedding security checks and fixes from the beginning onward. While developers and their wonderful code-slinging hearts might at first scoff — Security? That'll slow us down! — employing shift left actually speeds things up!
Another metaphor? Glad you asked! Think of shifting left like weeding a garden. A little effort early on keeps pesky vulnerabilities from taking root. If you wait, you’ll find yourself hacking away at a jungle of security flaws, which, let's face it, is far more difficult to deal with. Worse, attackers can easily harvesting your fruits from the overgrowth.

Now, some will tell you that shift left is all sunshine and rainbows. It's most definitely not! It requires a cultural shift, dissolving silos between developers and security teams. But when it works, wow does it work! It results in faster development cycles and more securely designed software. Most importantly, perhaps, you avoid that public spit-take moment when you find that a security breach has exposed your user base — a feeling akin to discovering that your unrefrigerated marmalade has spontaneously developed sentience and plans for world domination.
Let us shift (left) to the good part! Let's face it, even the most vigilant developer can't stare down every line of code like a security-obsessed owl. That's where our trusty friend, the integrated development environment (IDE), comes in armed with plug-ins to battle vulnerabilities.

Imagine an IDE that's not just a glorified notepad but a security vigilante — a beautiful marriage of cutting-edge automation and good old fashioned human ingenuity. You've got a new invisible friend scouring your code, sniffing out suspicious patterns and potential weaknesses. Think of it as a tireless intern, highlighting suspect areas with a cheery, nonjudgmental and highly educational tone.
Let’s be clear, this isn't some overlord dictating your every semicolon. It works in tandem with the developer's expertise. The human can delve into the flagged areas, understand the reasoning behind the concern, and make informed decisions. Perhaps your technological assistant flagged a library known to have vulnerabilities and suggests a helpful version bump. You then use your knowledge to see if this secure alternative makes good programmatic sense.
The harmonious interplay between human and machine is what takes shift left to a new level. We're not just weeding the garden — we've got a team of cyber-horticulturalists with the ability to predict future weed growth!

Does such an IDE still remain on the horizon, a shimmering oasis in the desert of insecure software? Nay, my codephiles (n. a person who loves writing code), it’s already within our grasp! With a best-of-breed, automated bloodhound and developers as our cyber-horticulturalists, we can build a future where software is secure from the get-go, where vulnerabilities are mere afterthoughts and developers can code with the confidence of a … well, a developer who knows their code is squeaky clean. And that is a beautiful thing.
Plug the Power of Prisma Cloud Directly into Your IDE
Let’s Begin with What’s Free
This, security champions, is the gift that keeps on giving — the Prisma Cloud plugin available for VSCode and Jetbrains, the successor to the venerable Checkov plugin. Checkov is the valiant warrior who brought the power of CLI scanning for infrastructure as code (IaC) and secrets directly to your IDE, and the Prisma Cloud plugin takes that magic formula and injects it with a double shot of espresso.
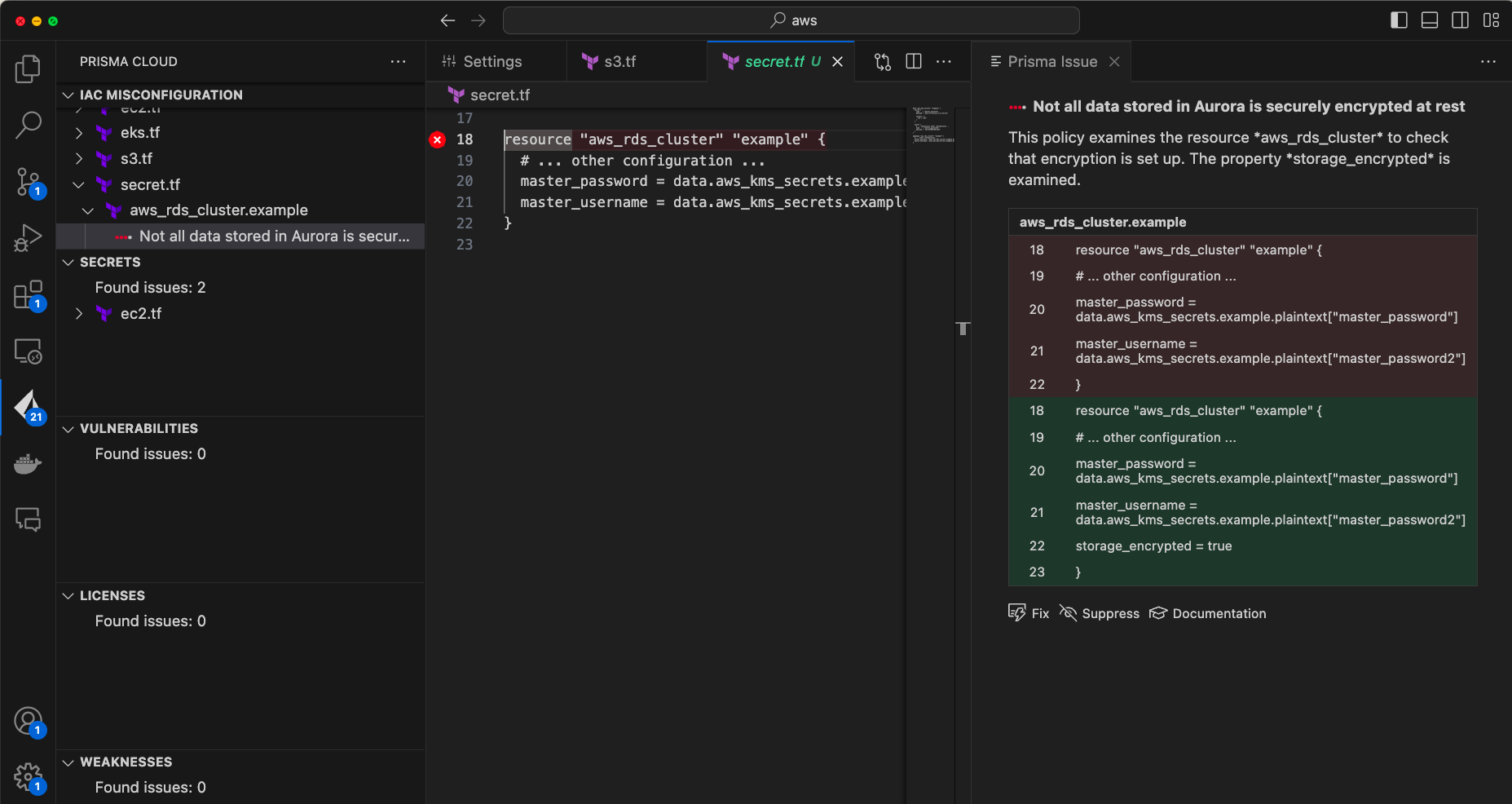
Prisma Cloud brings misconfiguration scanning for a veritable smorgasbord of frameworks — Terraform, Cloud Formation, Bicep/ARM, Kubernetes, you name it! It's like having a security butler who speaks every cloud dialect under the sun. And that's not all, folks! This beauty also scans for all the major types of secrets — finding and eliminating digital jewels to keep the bad actors at bay.
The Prisma Cloud plugin is your shield, your digital defender, a knight in a shining and very comfortable ergonomic coding chair.
Major types of digital jewels include:
| Policy | ID |
| Artifactory Credentials | CKV_SECRET_1 |
| AWS Access Keys | CKV_SECRET_2 |
| Azure Storage Account Access Keys | CKV_SECRET_3 |
| Basic Auth Credentials | CKV_SECRET_4 |
| Cloudant Credentials | CKV_SECRET_5 |
| Base64 High Entropy Strings | CKV_SECRET_6 |
| IBM Cloud IAM Key | CKV_SECRET_7 |
| IBM COS HMAC Credentials | CKV_SECRET_8 |
| JSON Web Token | CKV_SECRET_9 |
| Mailchimp Access Key | CKV_SECRET_11 |
| NPM Token | CKV_SECRET_12 |
| Private Key | CKV_SECRET_13 |
| Slack Token | CKV_SECRET_14 |
| SoftLayer Credentials | CKV_SECRET_15 |
| Square OAuth Secret | CKV_SECRET_16 |
| Stripe Access Key | CKV_SECRET_17 |
| Twilio Access Key | CKV_SECRET_18 |
But Wait, There’s More!
For those wading deep into the digital wilderness, a spade and bucket is merely a start. More is needed, but fear not! If your organization is already armed with Prisma Cloud you can get your hands on a Prisma Cloud API key and witness a glorious transformation well beyond what’s offered in the free version.
Yep, that's right — a significant "level up" to your personal security arsenal! This isn't some paltry trowel we're talking about. This is the digital equivalent of a monstrous, earth-moving machine ready to tackle any security challenges that may arise.
One Click Fixes
A well known frustration for developers is being presented with a list of errors in your code and having to — dread the thought — read some documentation. Worse, having to scour the internet for arcane stack overflows and Reddit conversations to gain further wisdom and understanding of the secure principles afoot.
Fear not. A Prisma Cloud API key unlocks the doorway to a library overflowing with out-of-the-box, tried-and-tested fixes for common IaC misconfigurations ready to banish those misconfigurations with a single click! Your infrastructure as code, once a potential storm of insecurity, quickly transforms into a haven of stability. You, the builder of infrastructure, are no longer a security apprentice. You are the wiser wizard, wielding the power of Prisma Cloud with the confidence of Gandalf himself.
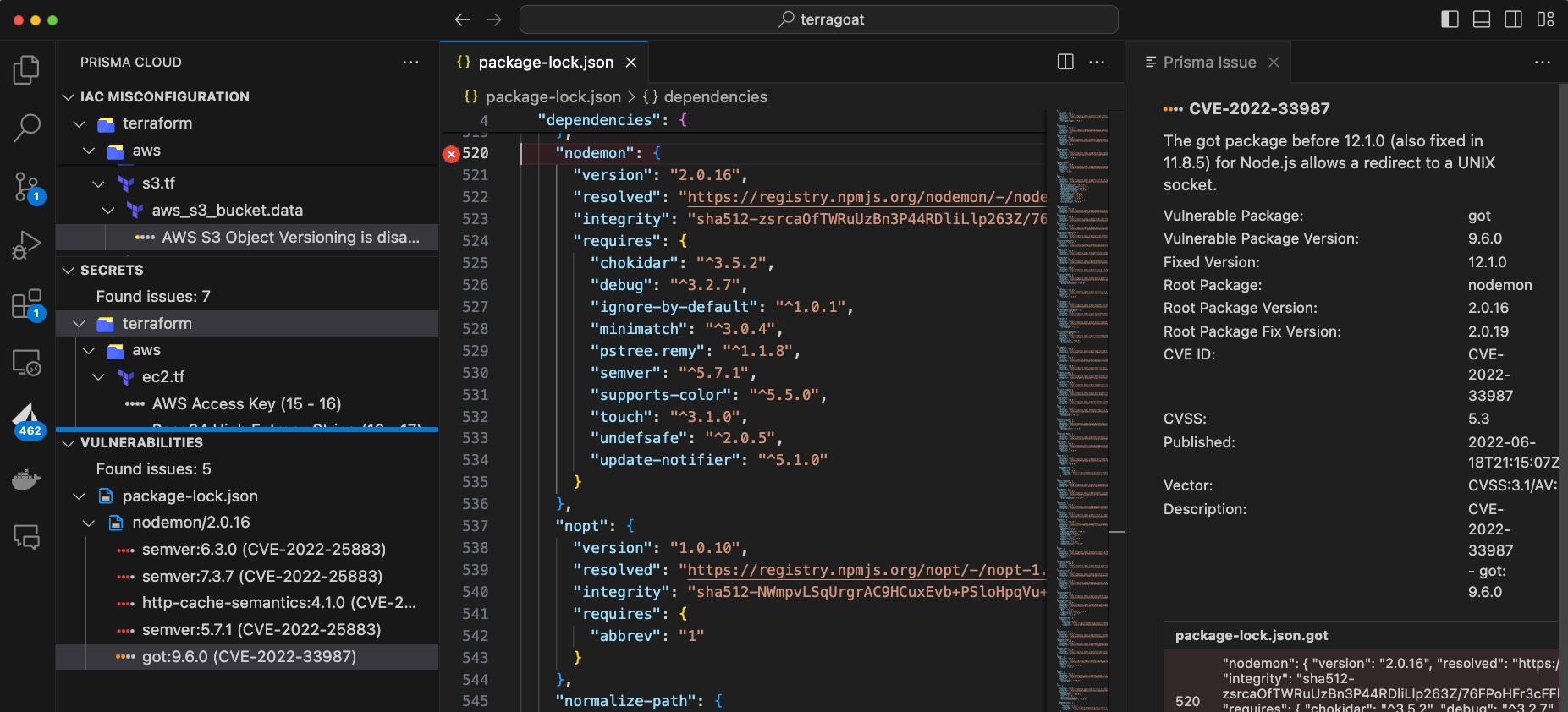
Software Composition Analysis (SCA) Delivered Straight to Your Developer Doorstep!
This marvel of modern technology scans not just your immediate dependencies but also those pesky transitive dependencies — the hidden pathways that lurk beneath the surface of your code.
And the best part? Software composition analysis isn't just some glorified sniffer dog. This brilliant buddy identifies those unlocked doors and windows in your code's architecture — and provides package bump suggestions for the identified root packages! With the click of a button you can eliminate CVEs from your code. It's like having a gardener with a green thumb and a keen eye for security vulnerabilities rolled into one. Weeding your technological garden has never been so effortless, so delightfully devoid of manual labor!
Extended Secrets Detection
Think of it as tuning up the keen nose of your technological bloodhound. This upgrade injects an additional 90+ Prisma Cloud server-side signatures into your security checklist. We're talking about the ability to sniff out everything from the familiar (think Jira tokens) to the downright obscure (Doppler API keys, anyone?). Securing your literal keys to the kingdom has never been easier!
Never a Better Conclusion
So, there you have it, the shift left philosophy — a small step for developers, a giant leap for cybersecurity. Just remember, folks, security baked in is far better (and less expensive) than a security patch slapped on later. After all, even the most aesthetically pleasing cathedral is useless if the roof caves in.
Learn More
Ready to get the power of Prisma Cloud in your IDE? Start by downloading for VS Code and JetBrains.