Executive Summary
Sophisticated phishing techniques are on the rise and are rapidly becoming a primary method for adversaries to deliver malware and establish a foothold within organizations. These attacks often combine social engineering, impersonation, and other evasive delivery methods, exploiting trust and context to bypass traditional email defenses. The result is the successful deployment of commodity malware, often as the first step in a broader attack chain, by advanced persistent threats (APTs) and cybercriminals.
To address this increasing risk, Palo Alto Networks has introduced the Cortex Email Security Module, an intelligent and integrated solution built to detect, correlate, and respond to the most evasive email-borne threats. This module works as part of the larger Cortex platform, connecting email threats to related activities on devices, in the cloud, across SaaS apps, and through user identities. This connected view helps security teams understand how an attack starts, spreads, and impacts the organization.
Modern email security must extend beyond the inbox, so the module enables deep email inspection, ties threats to broader attacker behavior, and automates response workflows.
Why Did We Develop the Cortex Email Security Module?
The days of spotting obvious red flags—like typos, awkward grammar, or vague greetings—are mostly behind us. Today’s attackers use generative AI (GenAI) to craft polished, professional emails that appear to be completely legitimate. These messages often include real names, roles, and references pulled from public sources, making them highly convincing. With the help of automation, threat actors can launch thousands of targeted attacks in minutes.
But the emails themselves are only part of the story. Legacy email security tools like secure email gateways (SEGs) analyze messages in isolation. This means that they miss critical context like signs of compromise on endpoints, suspicious identity activity, and anomalies across the network. This fragmented view leaves blind spots, and modern attackers are exploiting this lack of visibility.
Integrate, Correlate, and React
We built the Cortex Email Security Module not just to detect phishing, but also to understand how each email fits into a broader attack narrative.
- Deep Email Analysis - It starts with a deep email inspection. We look far beyond simple keyword scans. Cortex applies advanced analysis to detect business email compromise (BEC), impersonation attempts, and AI-generated phishing. It examines everything from metadata and message structure to subtle behavioral cues, catching signs of abuse that traditional tools often miss.
- Cross-Domain Threat Correlation - A single malicious message can be the first move in a larger campaign. That’s why Cortex connects the dots, linking email signals to activity across endpoints, identity providers, and other indicators within the network. We can trace an attack from the initial lure to further malicious activity, such as stolen credentials, account takeover, and lateral movement. This means we show you not just what happened in the inbox, but the entire story and context.
- Risk-Based Prioritization - Because not all threats are equal, Cortex prioritizes with precision. Every email is scored using behavioral baselines and real-time threat intelligence. This ensures that high-risk threats are escalated quickly, while benign noise is suppressed, reducing alert fatigue for security teams and enabling faster response where it matters most.
- Automated Incident Response - The Email Security Module automatically quarantines malicious emails, cuts off compromised senders, and disables affected accounts to stop the threat in its tracks before it can spread across the network.
Detecting Malicious Emails in the Wild
In real-world email threat scenarios, adversaries combine deceptive lures and dynamic themes to bypass defenses. Our new Cortex Email Security Module automatically detects and correlates these scenarios.
LLM-Powered Detection of Phishing Email Delivering AsyncRAT
AsyncRAT is a remote access Trojan that began as an open-source project on GitHub in January 2019, initially intended as a legitimate remote administration tool. While AsyncRAT was originally intended for system administration, threat actors quickly adopted it for nefarious purposes. It has since become a widespread commodity malware used in numerous campaigns by cybercrime and APTs.
Once running on a victim’s machine, AsyncRAT provides a rich set of features that grant the attacker almost complete control over the victim’s machine. Its capabilities include:
- Keylogging and credential theft
- File system manipulation
- Command execution
- Surveillance (webcam and microphone)
- View and record desktop screens
AsyncRAT is mainly delivered through phishing campaigns that leverage malicious attachments or links to trick users into executing the malware. One of the recent campaigns that our email module flagged purported to be a “Damaged parcels & invoice” notification, as shown in Figure 1. The email impersonated a well-known shipping provider and urged the recipient to review the attached invoice.
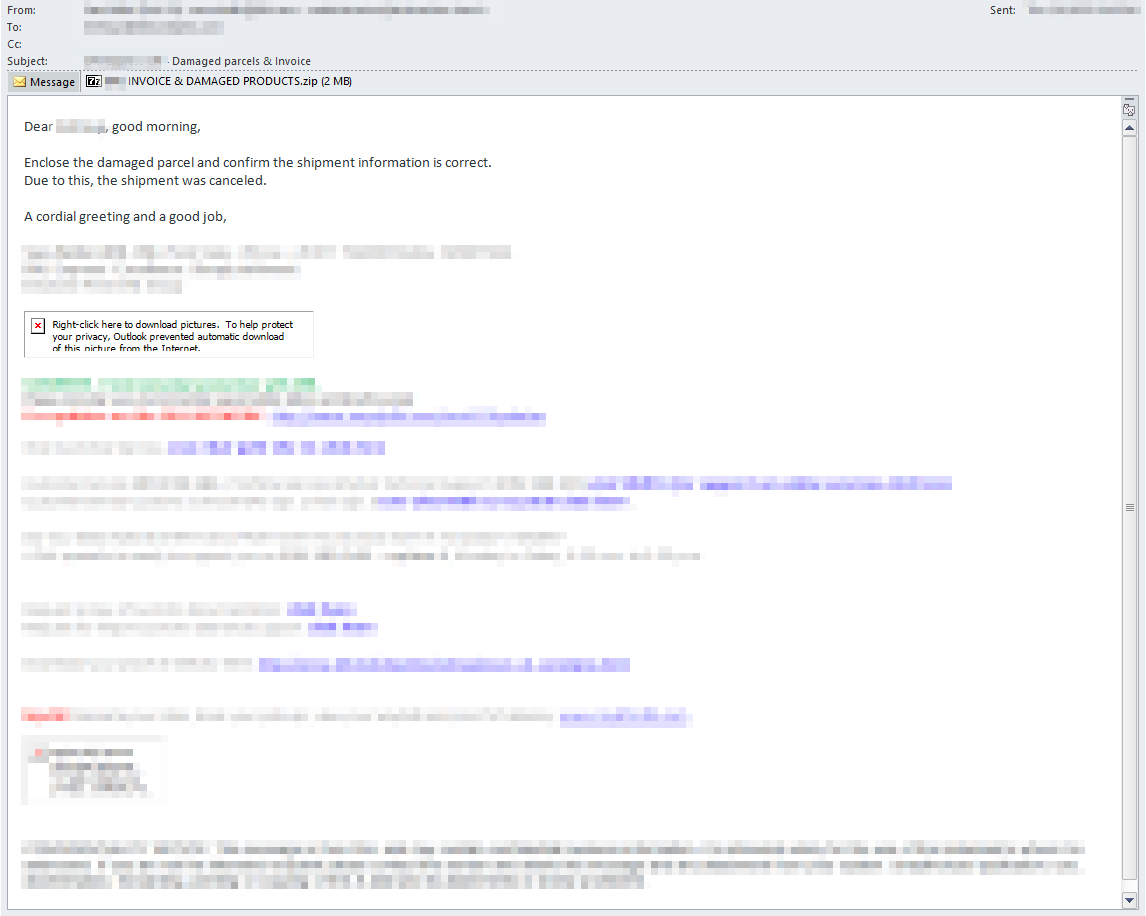
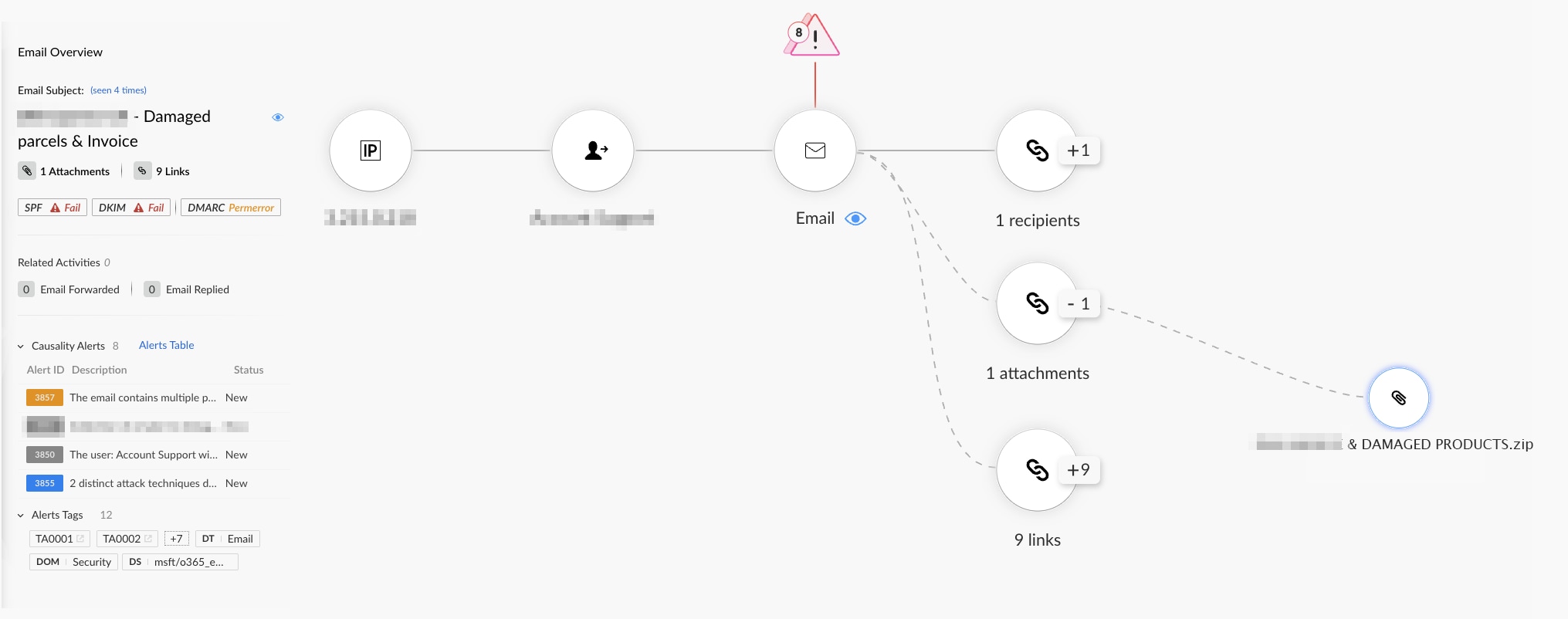
The Cortex Email Security Module flagged the suspicious email that initially appeared to be a routine logistics communication. The email content referenced a damaged shipment and included a ZIP file attachment labeled "INVOICE & DAMAGED PRODUCTS.zip". However, beneath this seemingly benign message, Cortex uncovered a multi-layered phishing attempt, triggering two high-fidelity alerts: “Multiple risk indicators detected in email” and “Elevated alert triggered by combined attack techniques.”
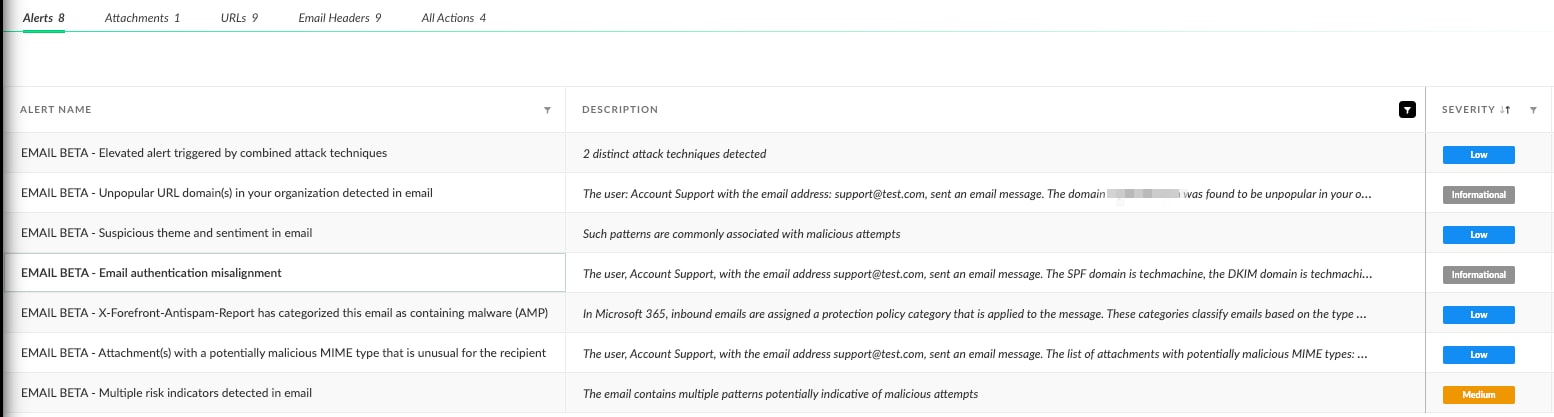
These alerts were not isolated; they represented the culmination of several overlapping threat signals, revealing a coordinated attack strategy designed to bypass traditional filters and manipulate human trust.
Unpacking the Indicators
Hidden Text Attributes - One of the first red flags was the use of hidden text attributes in the email's HTML body. This technique involves embedding invisible or obfuscated characters using CSS or HTML styling to disguise malicious phrases and bypass keyword-based detections. This subtle, stealthy form of evasion is often used to conceal phishing-related language from traditional scanners.
Rarely Used Domain - The module identified the inclusion of a legitimate-looking subdomain that had never been observed in the organization’s email traffic before. While the domain itself may not be malicious, its lack of historical usage raised suspicion - particularly when paired with logistics-themed content.
LLM-Powered Theme and Sentiment Analysis - We analyzed the email using an LLM-powered detection mechanism, which flagged the message due to suspicious themes and tone, recognizing linguistic patterns that are often associated with social engineering tactics:
“Dear [Name], good morning,”
“A cordial greeting and a good job,”
The message tone was neutral and polite, avoiding urgency or aggression - a deliberate strategy to lower defenses and gain trust. The theme of the communication related to a damaged parcel and shipment cancellation, in an attempt to exploit roles in logistics, procurement, or finance.
The Payload: A High-Risk ZIP Archive
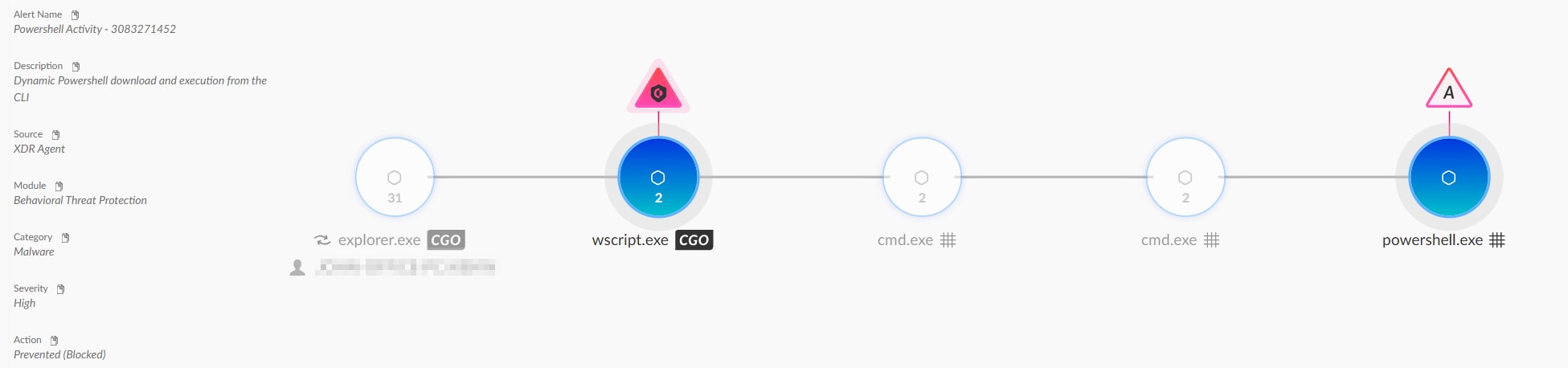
The ZIP archive attached to the mail held a Virtual Hard Disk (VHD) file that contained several VBS scripts masquerading as the invoice file. These VBS scripts were designed to drop and execute AsyncRAT. Figure 4 shows how Cortex XDR detects and prevents this infection chain.
What makes this email particularly dangerous is not a single tactic, but the combination of several:
- A socially engineered logistics theme, using polite, non-threatening language
- Obfuscated HTML content
- An unfamiliar but legitimate-looking domain
- A ZIP file attachment primed for user interaction
These techniques worked in tandem, triggering Cortex alerts for multiple risk indicators, and an elevated alert based on combined attack techniques. This layered approach is typical of the most evasive phishing attacks in the current threat landscape.
Detection of Dark Pink APT and FormBook Malware Attachments
Dark Pink APT
Dark Pink, also known as Saaiwc Group, is an APT that has been active since at least mid-2021. Its victimology reveals a heavy focus on the Asia-Pacific region, with occasional attacks in Europe. The targeted sectors are government and military agencies, non-profit and religious organizations, and educational institutions. One of Dark Pink’s defining characteristics is its almost entirely custom-built malware toolkit, which the group deploys at various stages of their attacks. Dark Pink’s arsenal includes several bespoke malware strains and utilities:
- TelePowerBot - A custom backdoor written in PowerShell and controlled via Telegram
- KamiKakaBot - The .NET version of TelePowerBot
- Cucky and Ctealer - Two custom information-stealer modules
Dark Pink employs a multi-stage attack strategy that demonstrates stealth and persistence at every phase. In documented cases, the initial breach is achieved via spear-phishing emails. These emails are meticulously tailored to each organization, often mimicking legitimate senders or incorporating accurate, relevant content to deceive recipients.
In a recent campaign, Palo Alto’s Cortex Email Security Module detected a phishing attempt disguised as a standard work email. It looked like someone was just sharing a document for review, in this case, a “System-Security-Plan,” and the message was written in formal language to give the impression of authenticity, as seen in Figure 5.
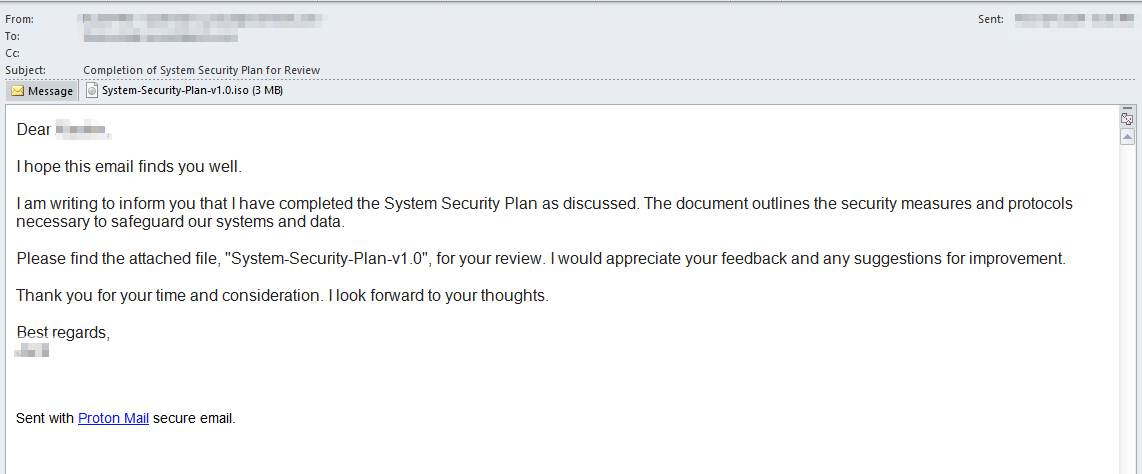
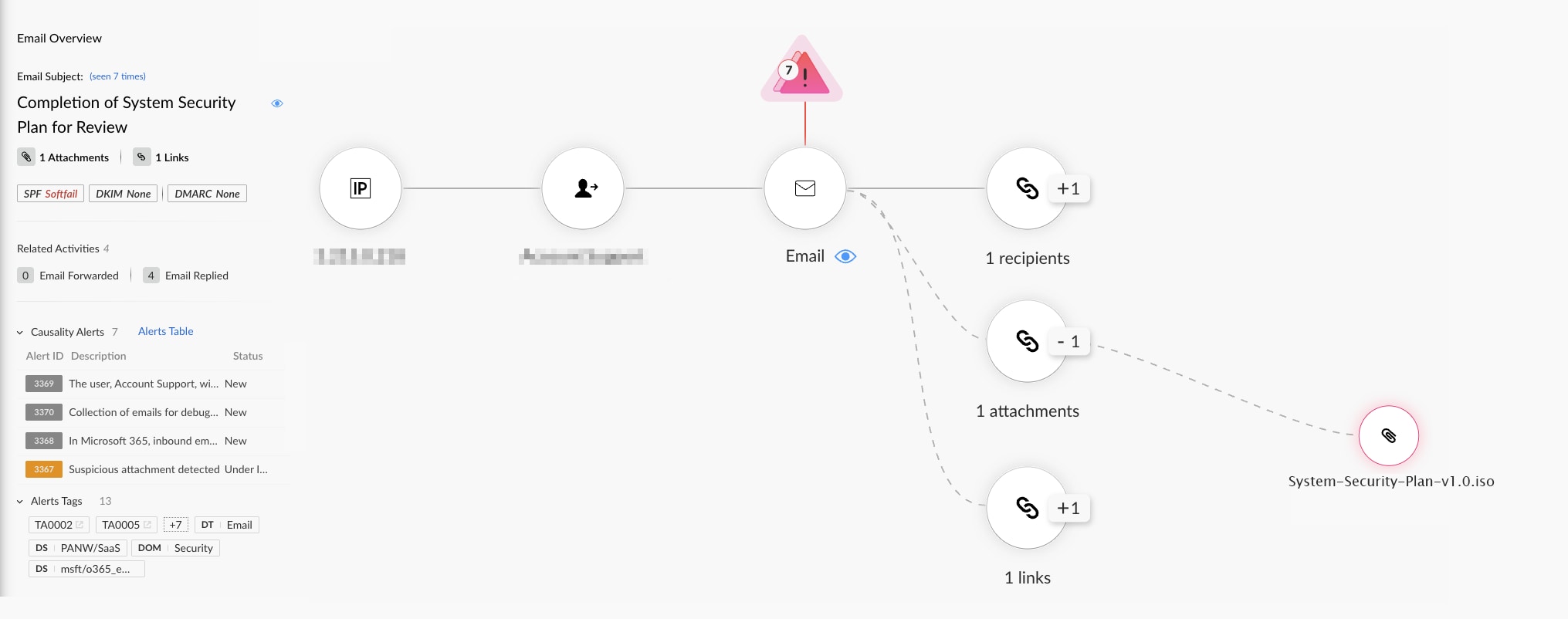
The ISO file attached to the email contained several files: a document, a PDF, a copy of winword.exe (disguised as a document named SYSTEM-SECURITY-PLAN-V1.0), and a DLL file named wwlib. When the copy of winword.exe is executed, the DLL is loaded, opens the decoy document and ultimately paves the way for KamiKakaBot to be dropped and executed. Figure 7 shows how Cortex XDR detects and prevents Dark Pink’s infection chain.
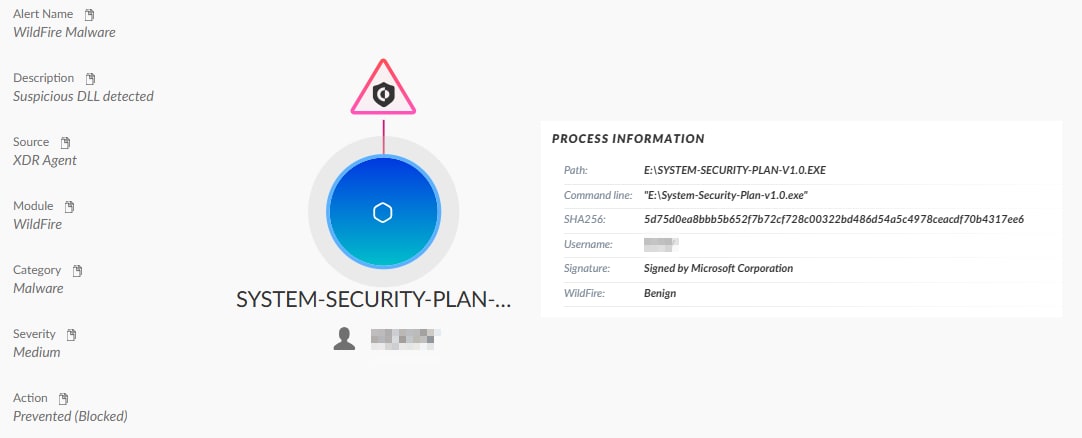
FormBook
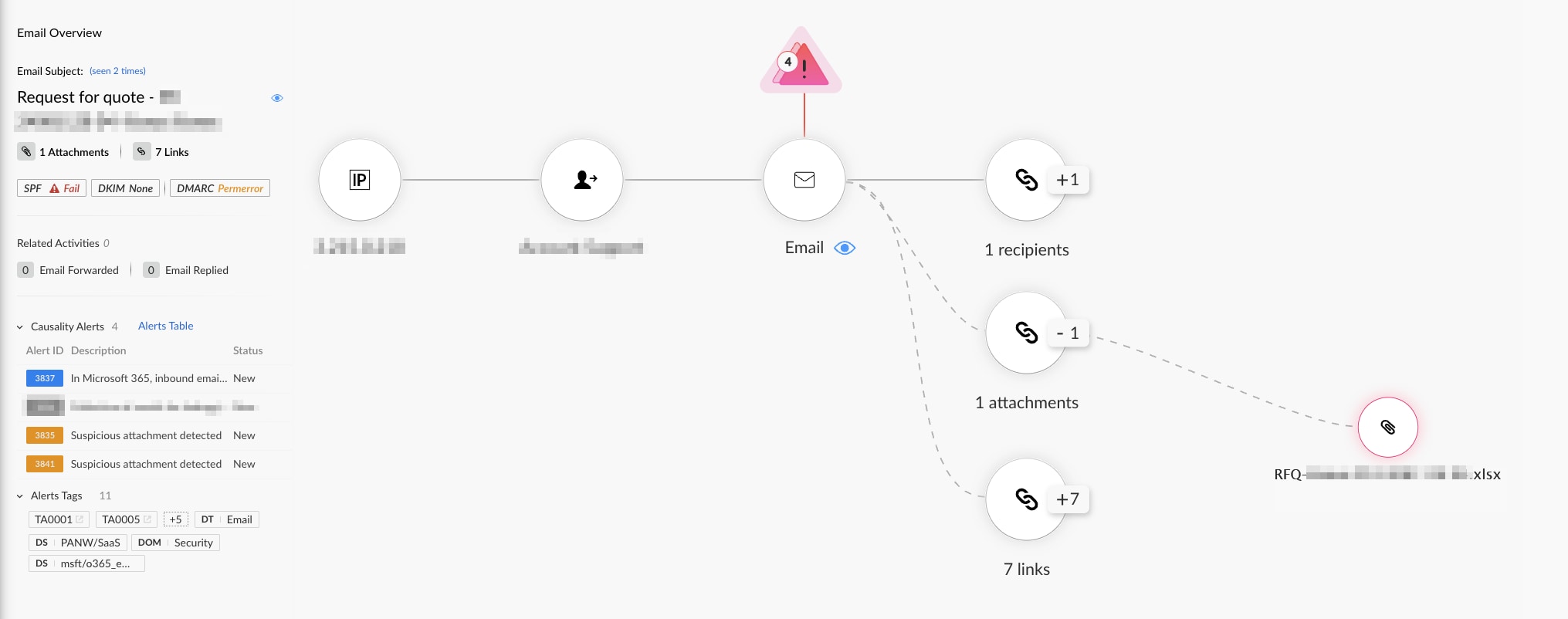
Another campaign was detected recently that targeted businesses with spear phishing emails themed as urgent requests for quotes. The emails contain an XLSX attachment, which ultimately leads to FormBook Stealer after the user opens it. The emails seemed to be sent from a compromised mailbox of a legitimate company. Figure 8 shows one of the emails that was sent as part of this campaign.
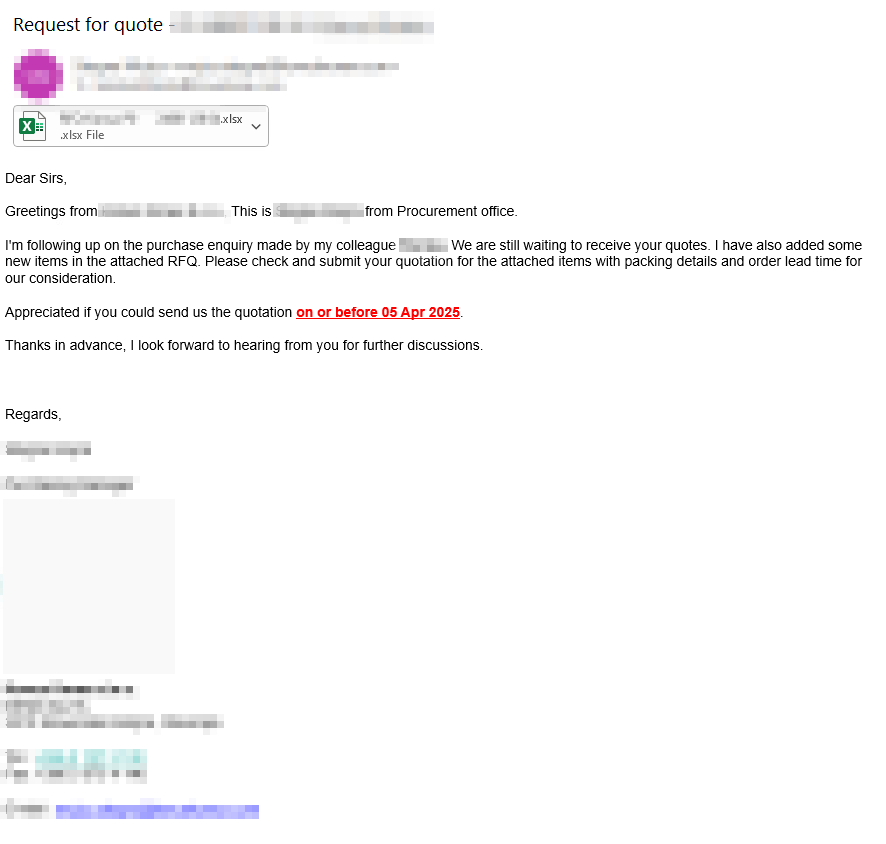
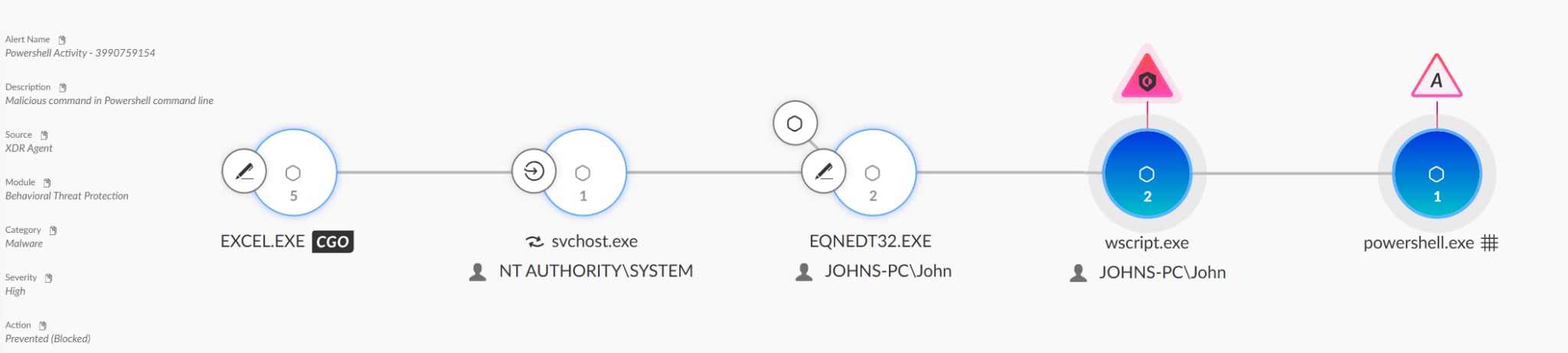
The XLSX file was crafted to exploit an old remote code execution (RCE) vulnerability in Microsoft Office (CVE-2017-11882), which is still being exploited in the wild. The exploitation allows the attackers to download a VBS script from a well-known cloud provider. The VBS script tries to download a JPG from legitimate services. The JPG file is padded with a base64-encoded payload decoded by the VBS script to download the FormBook payload from yet another cloud-hosted URL and execute it. The attack chain and techniques used in this campaign strongly align with recent research by Seqrite.
Figure 9 shows how our new Cortex Email Module detects this campaign, and Figure 10 shows how Cortex XDR detects and prevents the infection chain.
Conclusion
The Cortex Email Security Module marks a transformative leap in defending against modern email-based threats. By combining deep content inspection, behavioral analysis, and cross-domain correlation, this module offers increased precision and adaptive protection against advanced malicious phishing email campaigns, and malware attachments.
Through real-world detection of threats such as Dark Pink APT, AsyncRAT, and FormBook, the module has demonstrated its ability to detect multi-staged evasive payloads before user engagement or endpoint compromise. Its ability to deconstruct obfuscated infection chains and intercept malware embedded in seemingly benign attachments makes it a powerful proactive email defense tool.
This intelligence-driven approach represents a significant evolution in email security, shifting from static signature-based filtering to dynamic, context-aware prevention. As attackers craft more convincing lures and stealthy payloads, Cortex's unified, automated, and threat-informed defense module enhances organizations' ability to detect, investigate, and stop email-based attacks before they escalate.