This post is also available in: 简体中文 (Chinese (Simplified)) 日本語 (Japanese)
What Cortex Xpanse is doing to find vulnerable applications in your attack surface
Note:This situation is rapidly evolving and so we will regularly update Cortex® Xpanse™ with the most up-to-date information we have. Please reach out to your Customer Success Engagement Manager if you have questions. This post was originally posted 12/09/2021 at 7:55pm PT.
|
Summary
On December 9, 2021, a high-severity remote-code execution vulnerability in the Apache Log4j 2 logging library, colloquially known as Log4Shell, was identified as being exploited on the public internet (see the detailed analysis of the vulnerability and recommended mitigations on the Unit 42 blog).
The Log4j library is used by a great number of Java-based applications. Its widespread use in open-source libraries and products, combined with the low level of sophistication required to exploit it, makes this vulnerability particularly worrisome. The situation is evolving. Previous advice was to upgrade the Apache Log4j library to version 2.15.0. However, the patch in that version of the library was incomplete and has since been fixed in version 2.16.0 (see CVE-2021-45046).
Affected organizations are highly encouraged to upgrade to Apache Log4j version 2.16.0 or above as soon as possible.
How do you know if your organization is affected, particularly if those vulnerabilities are embedded in software that uses Log4j, rather than in-house developed applications? This post explains what we’re doing to help you identify applications in your organization that are vulnerable to this developing threat.
What Cortex Xpanse does today
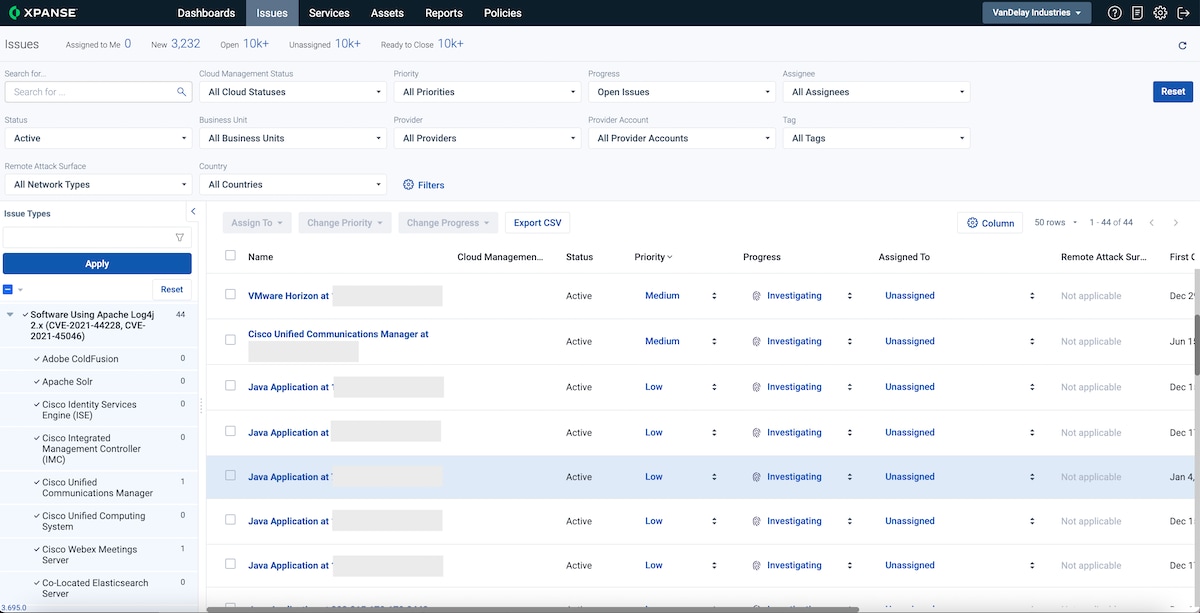
The Issues module in Cortex Xpanse detects security vulnerabilities in your digital attack surface by identifying makes, models, and versions of software with known problems. The Issues you see in Cortex Xpanse are produced through a series of Policies and contain information about the nature of the vulnerability, its severity, and relevant information about where it was found in your network, including affected IPs, certificates, domains, etc.
Finding potential Log4j vulnerabilities
Cortex Xpanse groups Issue types into categories or themes, to make them easier to browse and filter. We’ve created a new Issue category called Software Using Apache Log4j 2.x (CVE-2021-44228, CVE-2021-45046), containing all existing policies that cover software potentially affected by CVE-2021-44228 and CVE-2021-45056.
The new grouping is available right now, but it’s important to note that it may not cover all affected software makes, models, and versions—that list is growing and changing as you read this.
What’s next?
The section below lists all of the applications known to be vulnerable to CVE-2021-44228 and CVE-2021-45056 that Cortex Xpanse can detect. We will continually update this list as our research and development teams add detection capabilities to our product. Please refer back to this section for the latest.
Log4Shell Issues in Cortex Xpanse
A significant number of vendors have published advisory notices and patches in the last few days. This section will be kept up to date as we add new policies to our product.
Expander shows systems that are exposed to the public internet, without the need to install agents or sensors of any kind. Some of the systems below do not advertise version information, or are otherwise restricted from doing so depending on the configuration of our customers’ networks. Expander attempts to retrieve or derive version information, but this is not possible in all cases.
We are able to determine some devices/applications with a higher degree of confidence and thereby infer they are likely using an impacted version of Log4j. The following applications fall into that category, and have been automatically enabled as Issue Policies in Cortex Xpanse:
- Apache Solr
- Cisco Identity Services Engine (ISE)
- Cisco Webex Meetings Server
- Dell Wyse Management Suite
- IBM WebSphere Application Server
- Oracle E-Business Suite
- Oracle Fusion Middleware
- SonicWall Email Security
- VMware Carbon Black EDR
- VMware Workspace ONE Access
- VMware vRealize Lifecycle Manager
Other devices/applications do not provide this level of visibility. These applications have policies that can be enabled by your team in the Policies tab; we encourage our customers to toggle them to “On” as desired:
- Cisco Integrated Management Controller (IMC)
- Cisco Unified Computing System
- VMware vRealize Automation Appliance
- VMware vCenter
- Elasticsearch
- Palo Alto Networks Panorama. (Please note that at this time we are detecting all versions of Panorama exposed to the public internet. However, only versions 9.0.x, 9.1.x, and 10.0.x are affected. Series 8.1.x and 10.1.x are not affected.)
- Adobe ColdFusion
Open Source Scanning
The Cybersecurity and Infrastructure Agency (CISA) has open-sourced a log4j-scanner derived from scanners created by other members of the open-source community. This tool is intended to help organizations identify potentially vulnerable web services affected by the log4j vulnerabilities. Please find the tool available on GitHub.
Cortex Xpanse Log4Shell Active Scanning
Alternatively, Cortex Xpanse is offering our customers on-demand scans of their infrastructure. The Log4Shell scans are run from Cortex Xpanse-owned scanning infrastructure and will scan only approved perimeter targets. In practice, we commonly find that even though the exploit is triggerable from the perimeter, the exploited machine is not directly internet-facing (see diagram below).
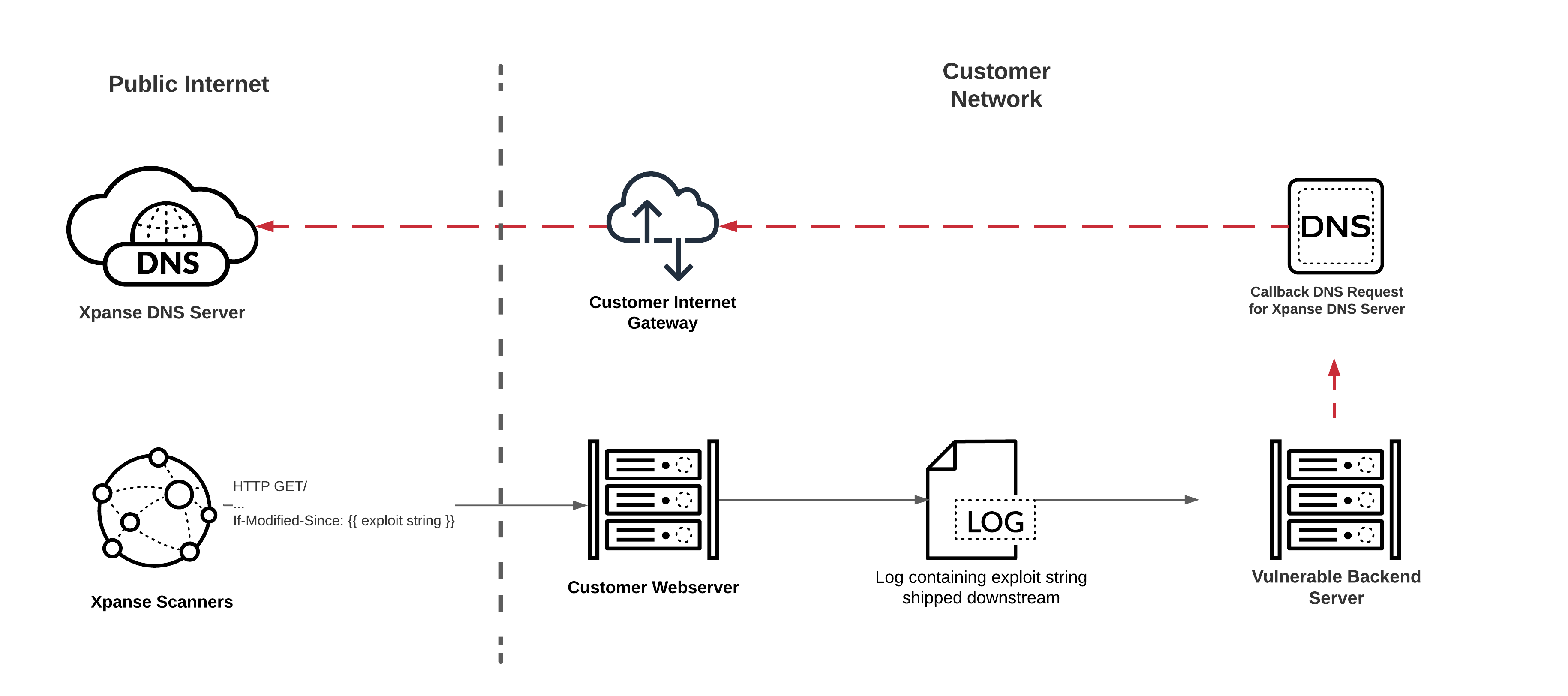
If we successfully exploit the vulnerability, we will make a DNS callout to a DNS server owned by Cortex Xpanse. We track all calls made to our DNS server and supply details of vulnerable systems to the customer.
If you would like to learn more, please contact your Customer Success Engagement Manager.
Questions? Contact us
As always, please reach out to your Customer Success Engagement Manager with any questions you have.