This post is also available in: 日本語 (Japanese)
Executive Summary
On May 27, 2021, Microsoft reported a wide scale spear phishing campaign attributed to APT29, the same threat actor responsible for the SolarWinds campaign named SolarStorm. This attack had a wide range of targets for an APT spear phishing campaign with 3,000 email accounts targeted within 150 organizations.
This blog will help you proactively search for related indicators of compromise (IOCs) and attack techniques using Cortex XDR.
Hunting for This Attack in Your Environment
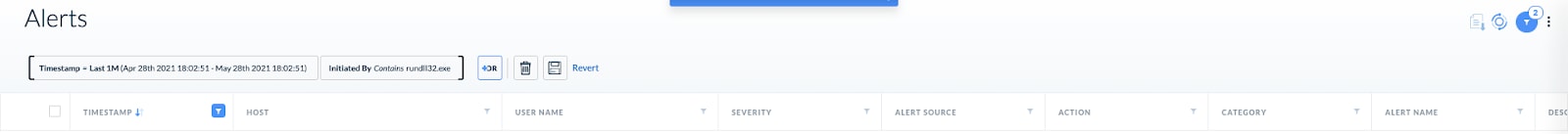
Hunt for the attack using Cortex XDR alerts
- Use the existing alert set and hunt for alerts with “rundll32.exe” as source of the alert:
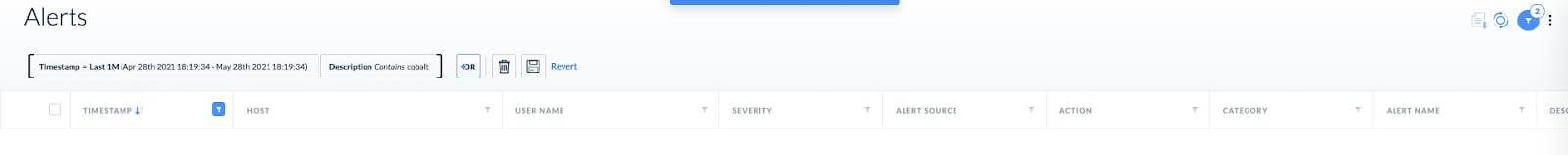
- Look for Cobalt Strike related alerts as Volexity mentioned that it might be used by the attackers:
Hunt for the attack using XQL Search in Cortex XDR
- Use this to hunt on known IOCs that have been attributes to this attack:
| dataset = xdr_data|filter action_file_sha256 IN ("2523f94bd4fba4af76f4411fe61084a7e7d80dec163c9ccba9226c80b8b31252", "d035d394a82ae1e44b25e273f99eae8e2369da828d6b6fdb95076fd3eb5de142", "94786066a64c0eb260a28a2959fcd31d63d175ade8b05ae682d3f6f9b2a5a916", "48b5fb3fa3ea67c2bc0086c41ec755c39d748a7100d71b81f618e82bf1c479f0", "ee44c0692fd2ab2f01d17ca4b58ca6c7f79388cbc681f885bb17ec946514088c", "ee42ddacbd202008bcc1312e548e1d9ac670dd3d86c999606a3a01d464a2a330") OR action_module_sha256 IN ("ee44c0692fd2ab2f01d17ca4b58ca6c7f79388cbc681f885bb17ec946514088c", "ee42ddacbd202008bcc1312e548e1d9ac670dd3d86c999606a3a01d464a2a330") OR dst_action_external_hostname ~=".*theyardservice.com|.*worldhomeoutlet.com|refreshauthtoken-default-rtdb.firebaseio.com" OR action_external_hostname ~=".*theyardservice.com|.*worldhomeoutlet.com|refreshauthtoken-default-rtdb.firebaseio.com" OR dns_query_name ~=".*theyardservice.com|.*worldhomeoutlet.com"
| fields agent_hostname, causality_actor_process_image_path, actor_process_image_path,action_external_hostname, action_file_path, action_module_path, dst_action_external_hostname, dns_query_name,event_id, action_file_sha256, action_module_sha256 |
- Hunt for ISO files dropped by browsers as the threat actor leverages ISO files as part of the exploitation attempts. Notice that there are legitimate cases of ISO drops:
| config case_sensitive = false
| dataset = xdr_data | filter actor_process_image_name in ("chrome.exe", "msedge.exe", "firefox.exe", "iexplore.exe", "google chrome", "firefox", "safari") and action_file_extension = "iso" | dedup agent_id, agent_hostname, action_file_name, action_file_path, action_file_sha256, action_file_size | fields agent_id, agent_hostname, action_file_name, action_file_path, action_file_sha256, action_file_size |
- Hunt for “rundll32.exe” loading “documents.dll” or “GraphicalComponent.dll” via command line:
| config case_sensitive = false
| dataset = xdr_data | filter action_process_image_name = "rundll32.exe" and action_process_image_command_line ~= ".*(Documents.dll|GraphicalComponent.dll).*" | dedup agent_id, agent_hostname, actor_process_image_name, actor_process_image_command_line , action_process_image_name, action_process_image_command_line | fields agent_id, agent_hostname, actor_process_image_name, actor_process_image_command_line , action_process_image_name, action_process_image_command_line |
- Hunt for the FRESHFIRE malware using “C:\dell.sdr” file access:
| config case_sensitive = false
| dataset = xdr_data | filter action_file_path = "c:\\dell.sdr" | dedup agent_id, agent_hostname, action_file_name, action_file_path, action_file_sha256, action_file_size | fields agent_id, agent_hostname, action_file_name, action_file_path, action_file_sha256, action_file_size |
Cortex XDR Product Response
Cortex XDR Managed Threat Hunting
The Cortex XDR Managed Threat Hunting team proactively hunted for threats and activities related to the event and notified customers with a detailed Impact Report.
Cortex XDR alerts that detect this attack
| Source | Description |
| Cortex XDR Analytics BIOC | LOLBIN connecting to a rare host |
| Cortex XDR Agent | Wildfire Malware |
Conclusion
Due to the high impact of a potential attack by APT29 and the technical prowess seen as part of SolarStorm, we highly advise Palo Alto Networks customers update to the latest XDR Agent and content version, and hunting for threats using the supplied XQL queries and the existing protection mechanisms within Cortex XDR.
Additional Resources
Cortex XSOAR for Nobelium Spear Phishing Attacks Rapid Response