To manage cloud security, you need agility and flexibility to deal with constantly changing infrastructures and expanded threat surfaces. You also have to coordinate with distributed teams across your organization. You need a platform that can provide rich, near real-time network incident visibility and harness that information to drive automated action across your cloud environment.
Cortex™ XSOAR primes your team for fast, standardized cloud security incident response through our integration with AWS Network Firewall, with playbooks that coordinate and automate incident response actions across your product stack. As a result, you can achieve better time to detect (TTD) and a faster, more scalable response.
With this integration you will be able to:
- Harness rich network visibility data from AWS Network Firewall for automated, playbook-driven response in Cortex XSOAR.
- Adjust firewall policies according to IOCs seen in AWS Network Firewall alerts and perform auto-remediation as appropriate.
- Use Cortex XSOAR’s orchestration to unify the network intelligence of AWS Network Firewall with data from other AWS security services like AWS Security Hub, Amazon GuardDuty or Amazon CloudWatch, etc., on a central console
- Improve analyst efficiency by centralizing collaboration, investigation, and documentation.
- Shorten decision-making cycle and time to respond (MTTR) by automating key tasks with analyst review.
With the flexibility of Cortex XSOAR’s playbook automation, you can automate any number of actions exposed with our API integration to reduce or fully eliminate the manual and repetitive incident management tasks that don’t require human review. Rather than being mired in the mundane, your security team can turn their attention to proactive threat hunting or tackling the more complex incidents.
Let’s take a deeper look at a couple of use cases you can leverage with this integration.
Automated Incident Enrichment and Response
As part of your daily firewall administration tasks, you frequently create, delete and update firewall instances, security groups and policy rules. With the Cortex XSOAR integration with AWS Network Firewall and other AWS security services (AWS Security Hub, Amazon GuardDuty, etc), incidents are ingested, classified and can trigger task-based workflows or playbooks to orchestrate specific actions.
For example, Amazon GuardDuty findings can be ingested into Cortex XSOAR as incidents to trigger the appropriate playbook for a specific threat. Currently, when malicious indicators are detected, the remediation approach is to revoke the security group rule that allows for the traffic. With XSOAR, you can take a more precise, surgical approach. Instead of revoking the security group rule, the playbook can be directed to create an AWS Network Firewall rule group which matches the traffic and either 1) forwards the traffic for stateful inspection (and alert/drop), or 2) simply drops the connection.
Interactive, real-time investigation for full lifecycle incident management
While standardized, repeatable playbooks can automate commonly performed tasks to ease analyst load, an attack investigation usually requires additional tasks such as pivoting from one suspicious indicator to another to gather critical evidence, drawing relations between incidents, and finalizing resolution. Running these commands traps analysts in a screen-switching cycle during investigations and a documentation-chasing cycle after investigations end.
With this new integration, analysts can now supplement their enrichment playbooks with even greater visibility and new actionable information about an attack by running AWS Network Firewall commands in the Cortex XSOAR War Room. For example, an analyst can run the aws-network-firewall-create-rule-group command to manually create a group. Analysts can also run commands from other security tools in real-time using the War Room, ensuring a single-console view for end-to-end investigation.
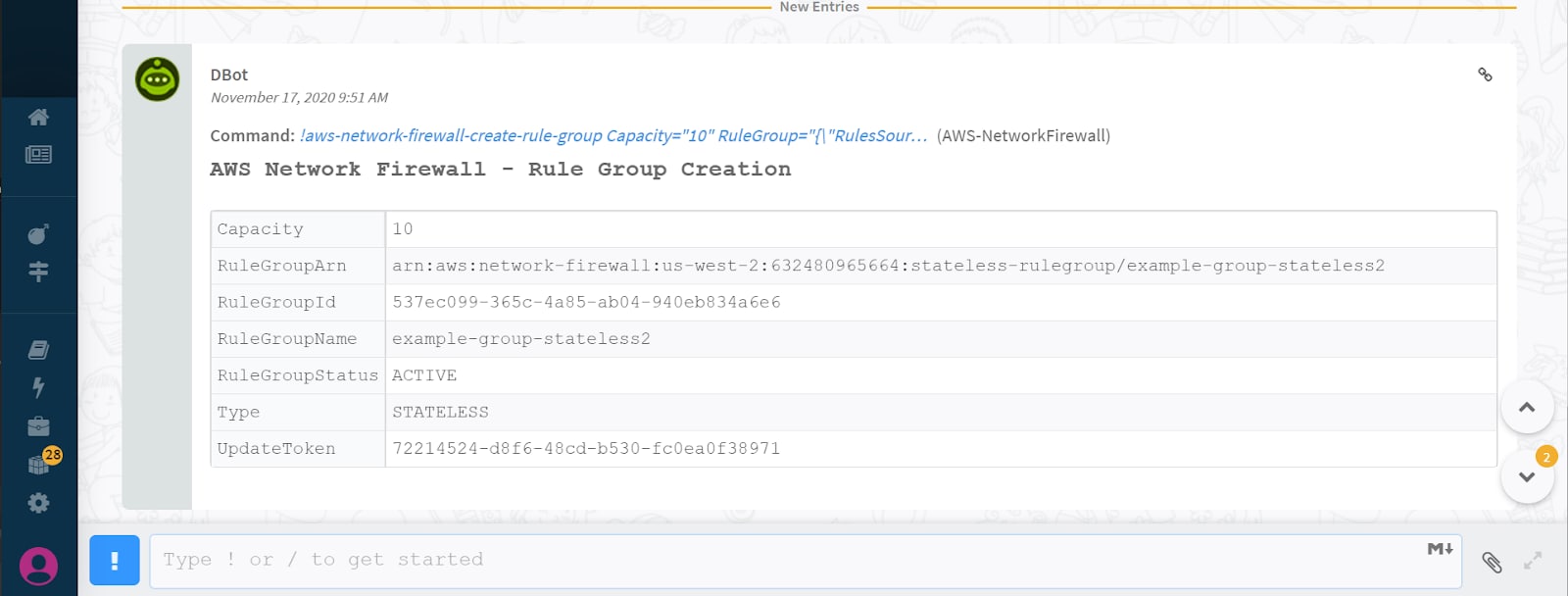
Cortex XSOAR playbooks can automate a host of steps, interacting with multiple intel sources, to accelerate the investigative process in threat hunting. Furthermore, the War Room also allows analysts to quickly pivot and run unique commands relevant to the threat case or incident in their network from a common window. All participating analysts get full task-level visibility of the process and can run and document commands from the same window. This also helps avoid the need for collating information from multiple sources for documentation.
If you are interested in checking out Cortex XSOAR, download our free Community Edition.