A threat actor's greatest asset is time. The countdown starts from the moment their phishing attack arrives in your organization's inbox. From then on, the likelihood of a careless employee – your weakest link – falling for the click-only malware bomb increases with each passing moment that threat goes undetected.
In the case of a sustained phishing campaign, your analysts are getting stuck in the high volume of persistent alerts that call for coordination between multiple security products and communication with end-users. As a result, the most destructive response to a phishing campaign involves the manual triage of incoming alerts.
After deciding whether the email is malicious, the analyst must perform manual response actions to raise its severity across multiple siloed tools. These actions are high-quantity, repetitive, and don't require critical thinking. Unfortunately, they also cost you time and money, but what if you could decrease investigation time by 75%?
Automate Your Phishing Response
To boost the speed of the game, your security team must use every tool that can automatically investigate and respond to an email-based phishing incident. In addition to classifying malicious emails, Cortex XSOAR’s Phishing Pack has fully automated playbooks that react rapidly to suspected phishing attacks and can seamlessly integrate across multiple endpoint systems.
It can be installed from the XSOAR Marketplace in an instant to serve your organization with the following features:
- Retrieve emails from user inboxes or ingest them using mail listeners.
- Create a phishing incident within Cortex XSOAR associated with the email.
- Extract and enrich all indicators from email attachments.
- Analyze files and provide reputation using your sandbox and threat intelligence integrations.
- Generate a screenshot of the email and embedded links and calculate reputation for all indicators involved.
- Run checks for SSL certificates of URLs, email address breach involvement, domain-squatting, and email authenticity using SPF, DKIM, and DMARC checks.
- Identify similar phishing incidents of the same campaign, providing visibility and manual or automatic actions to respond to such incidents.
- Calculate severity for the incident based on the provided initial severity, indicator reputations, email authenticity check, and critical assets, if any are involved.
- Remediate the incident by blocking malicious indicators and searching for and deleting malicious emails upon analyst approval.
- Engage with the end-user regarding the incident, such as notifying them of receipt of the email and providing further instructions if an email is suspected to be malicious.
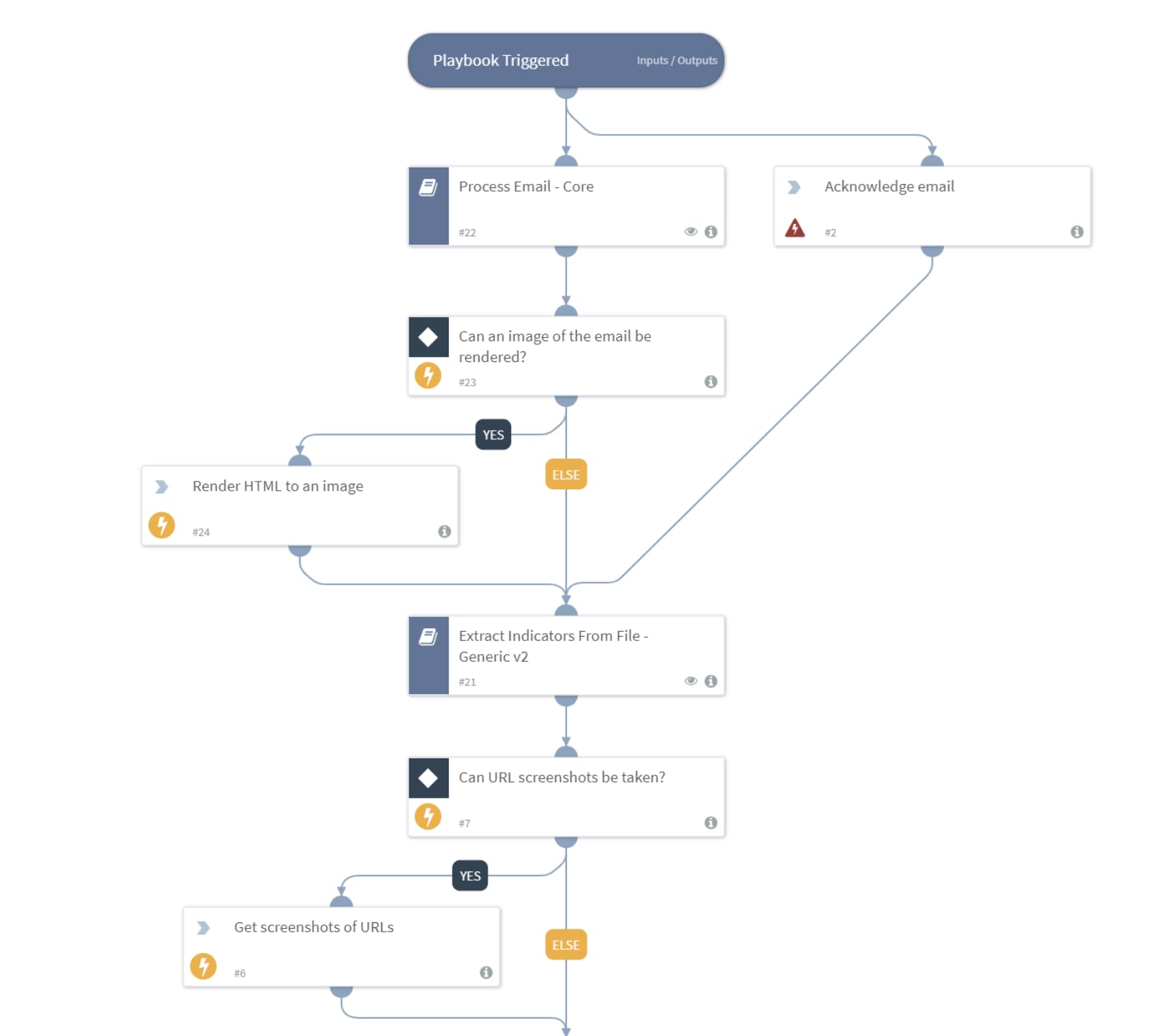
This image shows a phishing incident playbook work plan within the Cortex XSOAR’s Phishing Pack
Consider how long it takes to manually perform all of the above tasks while knowing a threat actor is attacking your organization. For example, the Palo Alto SOC calculated that an average manual investigation of phishing emails took 45 minutes, but XSOAR Phishing Automation cut that down to 8 minutes: a 75% decrease in SOC effort.
This pack facilitates analyst investigations by automating your organization's response to manual alerts. By downloading the XSOAR Phishing Content Pack, you're giving back ownership to your analysts of their time.
To learn more about how you can automate security operations with Cortex XSOAR, check out our virtual self-guided XSOAR Product Tour
We also host virtual and in-person events, so check here for upcoming ones.
Please Suggest Other Ideas or Vote!
If you like these ideas or would like to suggest other ideas, please collaborate with us through the Cortex XSOAR Aha page: https://xsoar.ideas.aha.io/ideas