The clock starts ticking as soon as a zero-day vulnerability is disclosed. Cybersecurity teams scramble to shore up their defenses and search for signs of compromise. Threat actors quickly develop exploits and launch countless attacks on hapless victims.
Whether the ultimate objective is data theft, ransomware deployment, cryptocurrency mining, or another nefarious scheme, successful zero-day attacks can cost organizations millions of dollars.
Fortunately, by adopting a Zero Trust architecture and implementing extended detection and response (XDR), organizations can reduce the impact of zero-day attacks and block many attacks outright. Let’s take a look at how.
Zero-Day Attacks on the Rise
Every year, thousands of vulnerabilities are discovered, and trends like remote work and cloud computing are increasing the risk of exploitation. In addition, threat actors have accelerated their vulnerability response times; they begin scanning for exposures within 15 minutes of a zero-day disclosure, forcing security teams to respond quickly to prevent successful attacks.
In 2021, the Apache Log4j vulnerability overshadowed all other vulnerabilities, with over 11 million attack sessions observed in less than one month after its disclosure. While attackers continue to target older vulnerabilities, zero-days pose an enormous risk due to both the volume of attacks and the challenge organizations face mitigating them before a patch is released.
Most Exploited Vulnerabilities of 2021
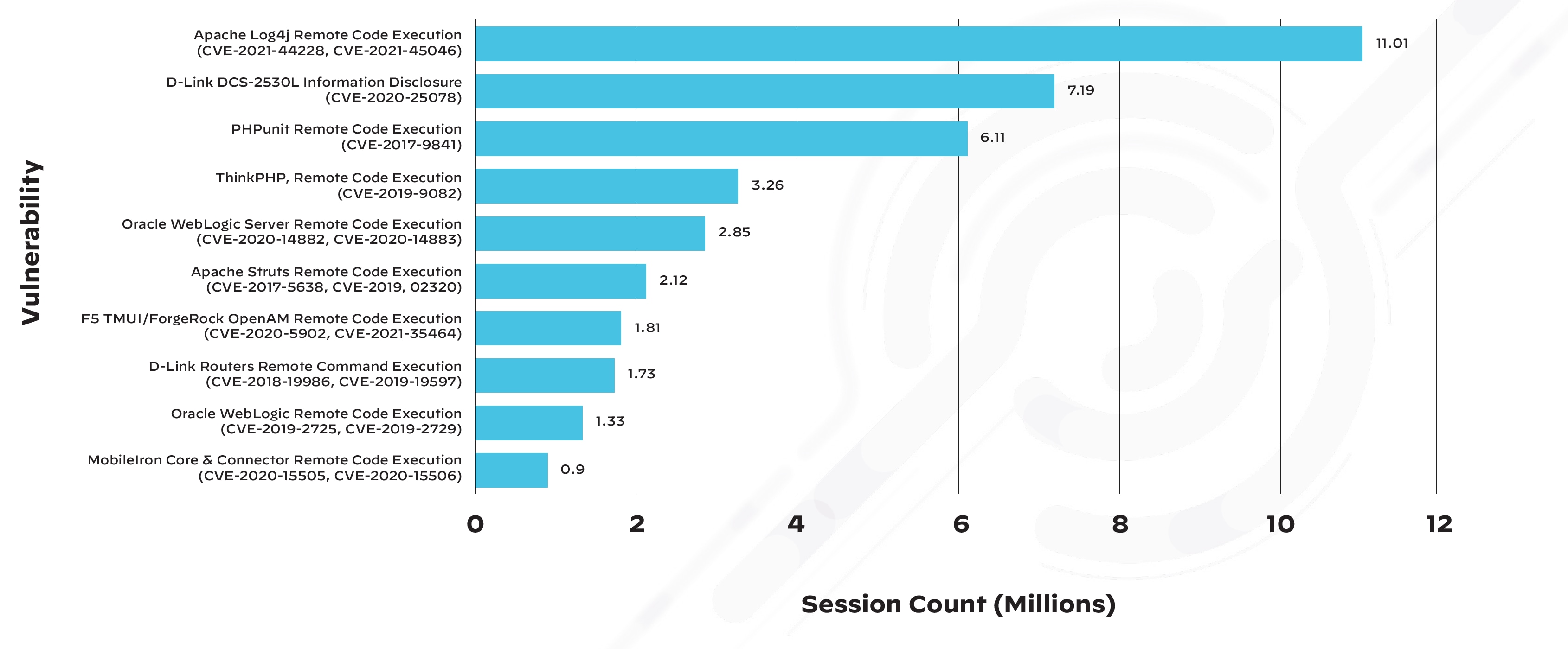
To underscore the threats posed by vulnerabilities, 31% of all security incidents investigated in 2021 originated from software vulnerabilities, according to the 2022 Unit 42 Incident Response Report.
Zero-Day Response Strategies
Responding to zero-day threats requires collaboration across multiple teams in an organization:
- Vulnerability management staff should locate all affected systems and, if possible, patch software.
- Threat hunters should search for signs of compromised assets, scouring through comprehensive data gathered from across the environment.
- Security engineers should attempt to monitor and block exploits and virtually patch exposed systems.
All these teams often need multiple tools to discover vulnerable software across their on-premises and cloud environments, prevent attacks, and detect and respond to malicious activity.
How a Zero Trust Approach Can Limit the Impact of Zero-Day Attacks
A Zero Trust strategy helps protect organizations from breaches, including ones originating from zero-day exploits. Zero Trust is an approach to cybersecurity that focuses on eliminating implicit trust and continuously validating user identity, devices, access, and transactions.
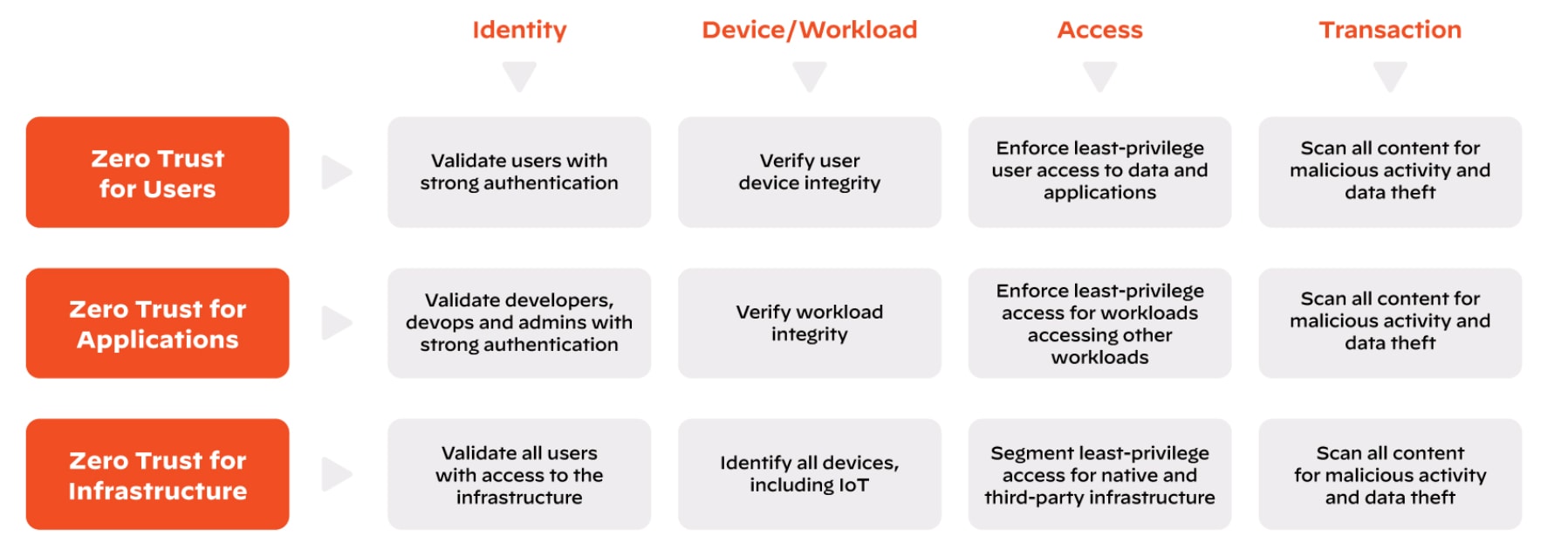
Rooted in the principle of “never trust, always verify,” Zero Trust relies on multiple layers of security, including network segmentation, strong authentication, threat prevention and more, to protect users and applications. All of these layers help limit the blast radius of a zero-day attack, but XDR technologies in particular, empower multiple teams to combat zero-day threats quickly.
Vulnerability Discovery, Hunting, and Threat Prevention with XDR
When faced with a critical zero day, XDR technologies can help speed response and reduce the risk of a successful attack. XDR is a fast-growing product category that delivers threat prevention, detection, investigation, and response in one integrated, cloud-native platform. XDR tools gather data from any source and detect stealthy threats with cross-data analytics.
In the event of a zero-day, SOC teams can quickly find, prioritize and patch vulnerable software by searching for endpoint or network artifacts or using integrated vulnerability assessment capabilities in XDR solutions. They can also detect post-exploit activity, such as web shell installation or lateral movement. They empower threat hunters to search for signs of compromise across all XDR data including network, cloud, endpoint, and identity data.
Oftentimes, XDR software installed on endpoints can prevent zero-day exploits. Whether blocking exploits based on pre-existing anti-exploit protections or through rapid updates provided by an XDR vendor, XDR endpoint software can often block exploits as well as post-exploit activity, such as malware installation.
Protecting Against Zero Days with Cortex XDR and Zero Trust as a Service (ZTaaS)
With zero-day attacks growing in volume and sophistication, organizations need both better tools and services to protect their digital assets. ON2IT and Palo Alto Networks have partnered to bring a scalable Zero Trust—Zero Trust as a Service (ZTaaS) solution to enterprises of all sizes. The joint offering helps organizations:
- Stop data breaches, including zero-day attacks, with a prevention-focused approach.
- Acquire modern SOC capabilities.
- Operationalize Zero Trust using an advanced platform purpose-built for managing Zero Trust environments.
The ZTaaS security services provided by ON2IT and Palo Alto Networks bring together leading cybersecurity technologies and expertise to create the market’s most advanced SOC technologies.
- Cortex XDR is the industry’s first extended detection and response platform that natively integrates from any source data to stop modern attacks. Cortex XDR has been designed to help organizations secure their digital assets and users while simplifying operations. Using behavioral analytics, it identifies unknown and highly evasive threats targeting your network. The Cortex XDR agent offers a complete prevention stack, starting with the broadest set of exploit protection modules available to block exploits such as Log4Shell, SpringShell and Follina.
- ON2IT AUXO delivers a highly automated, prevention-oriented managed cybersecurity platform that is tightly integrated with the Palo Alto Networks portfolio. Designed with the creator Zero Trust, AUXO combines world-class Zero Trust expertise, technologies, design, and implementation services into our managed security operations centers, enabling prevention unavailable in traditional security operations centers. For the first time, organizations will document and operationalize their Zero Trust strategy, within the Auxo platform, using the Zero Trust 5-Step Methodology.
Learn the Keys to Building a Zero Trust Enterprise
Zero Trust is an ongoing process that requires continual monitoring, updates and improvements. Technologies such as XDR help organizations implement Zero Trust not only by verifying devices and preventing attacks, but also by auditing and maintaining the overall Zero Trust architecture.
To learn how you can extend Zero Trust to the endpoint and beyond, check out ON24's Zero Trust Primer infographic or watch the on-demand webcast “Fever on the Endpoint: Zero Trust remote worker management in a hybrid world.” During the webcast, John Kindervag, Creator of Zero Trust, and Bruce Hembree, Cortex CTO at Palo Alto Networks, introduce the concept of Zero Trust as a Service (ZTaaS), a new approach to managed security services, enabling you to embrace Zero Trust with ease and 24/7 support from our comprehensive SOC team.