Kubernetes has revolutionized the way we deploy and manage applications, but its complexity and dynamic nature also introduce a new set of security challenges. Attackers are constantly looking for ways to exploit vulnerabilities in Kubernetes clusters, and it's crucial to have security measures in place to protect against these threats.
Traditional security tools often struggle to adapt to Kubernetes' dynamic environment, leading to gaps in visibility and control. Whether agent-based or agentless, they face limitations in their ability to fully understand and act upon the complexities of Kubernetes environments. Agent-based solutions often lack visibility and the ability to take actions at the cluster level, leading to challenges in detecting and mitigating threats effectively. For example, the persistence of the Kubernetes control plane in recreating pods for workloads can make agent-based solutions ineffective in deleting malicious containers. On the other hand, agentless solutions may struggle with visibility into the container runtime, limiting their effectiveness to detecting cluster-level attacks.
To address these limitations, Cortex XDR and XSIAM for Kubernetes combine the strengths of both approaches. It directly communicates with the cluster, enriches event data with relevant information, mitigates threats at the cluster level, utilizes advanced analytics for threat detection, and offers automated response capabilities through playbooks. This enables it to not only identify and kill malicious containers but also to prevent their recreation by the control plane.
Cortex XDR & XSIAM Agent for Kubernetes Architecture
The Cortex XDR and XSIAM Kubernetes agent is a specialized Linux agent designed specifically for Kubernetes Nodes, providing the same level of protection and functionality as any standard Cortex agent for Linux. Deploying the agent is straightforward, requiring only the deployment of a simple configuration file. Once deployed, the agent operates as a DaemonSet, deploying an agent Pod on each Node in the cluster, ensuring that all the cluster’s Nodes are protected by Cortex. These pods are equipped with admin capabilities and additional features that allow them to interact with the underlying host.
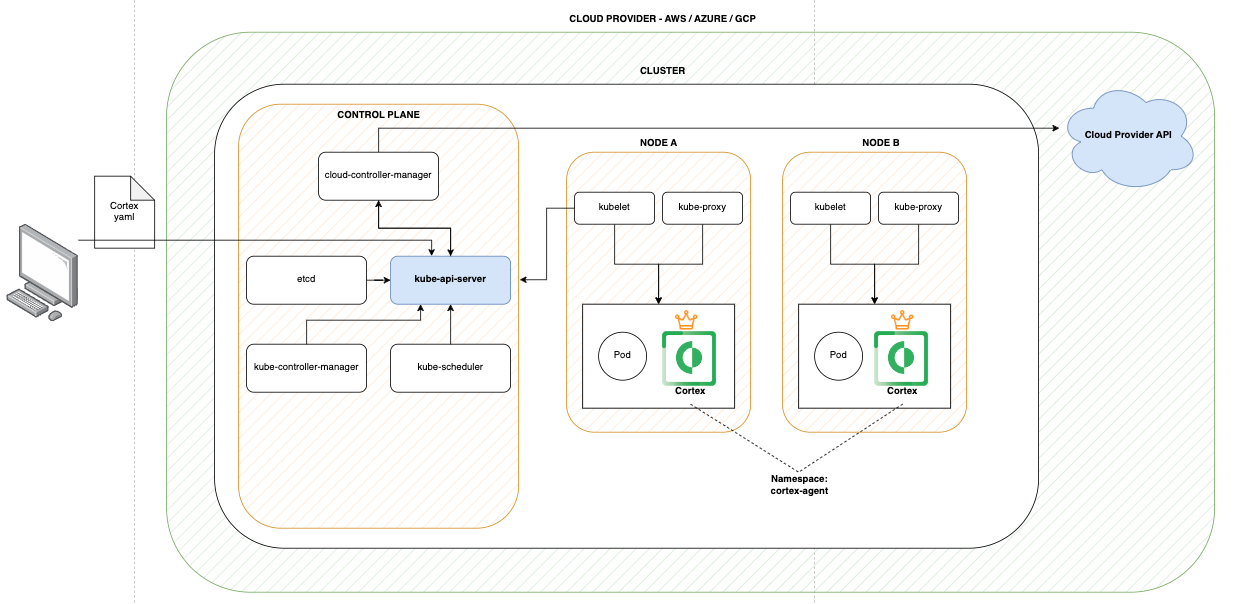
Cluster and Container Levels Visibility
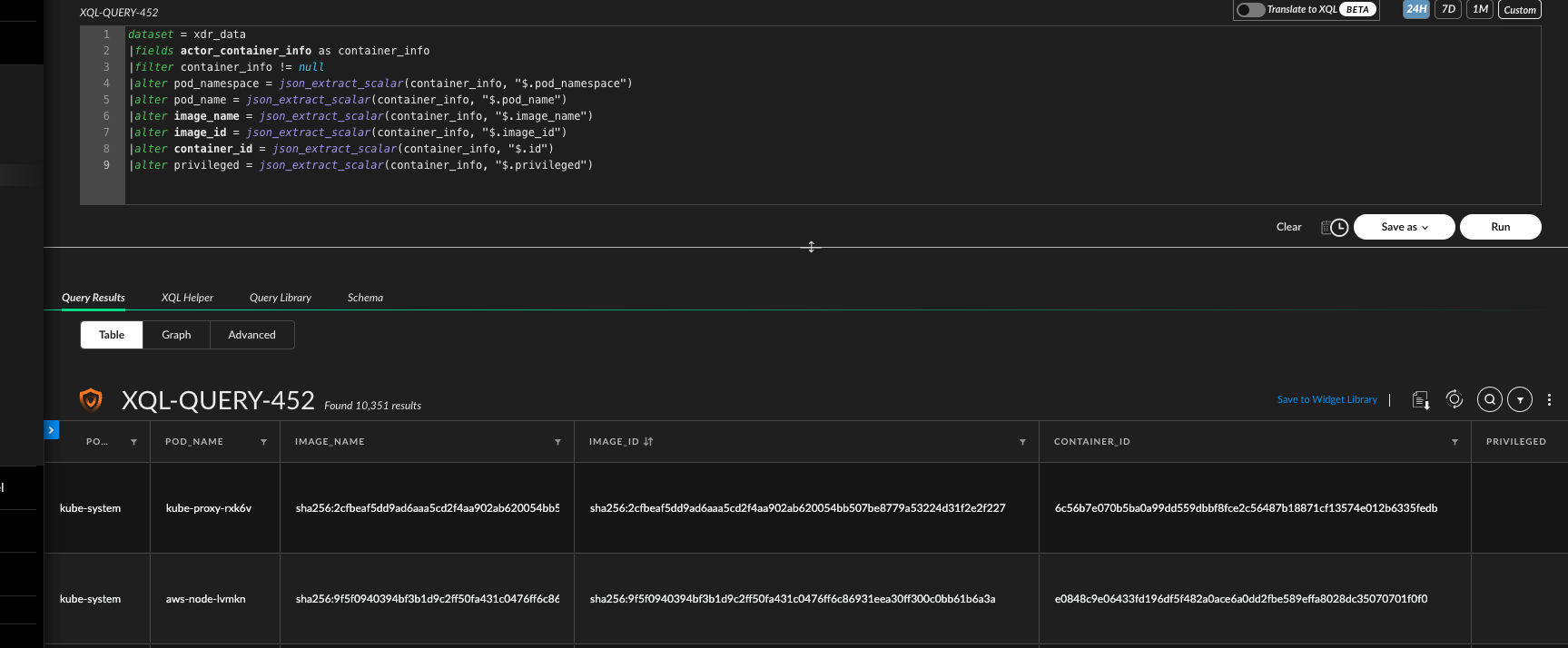
The Cortex XDR and XSIAM agent for Kubernetes enriches process, network, and file events by providing detailed information about the container and Kubernetes environments where they occur. Obtaining this information from the host is non-trivial, as the host is unaware of its role within the cluster and processes are unaware of being running inside a container. To achieve this, the agent uses unique container runtime queries for container-level information, including container name, container ID, image name, and image ID, and Kubernetes-specific queries for cluster-level information such as the cluster name, pod name, and pod namespace. This enables the differentiation between processes running at the host level (the Kubernetes Node) and those at the container level (the Kubernetes Pod).
dataset = xdr_data
|fields actor_container_info as container_info
|filter container_info != null
|alter pod_namespace = json_extract_scalar(container_info, "$.pod_namespace")
|alter pod_name = json_extract_scalar(container_info, "$.pod_name")
|alter image_name = json_extract_scalar(container_info, "$.image_name")
|alter image_id = json_extract_scalar(container_info, "$.image_id")
|alter container_id = json_extract_scalar(container_info, "$.id")
|alter privileged = json_extract_scalar(container_info, "$.privileged")
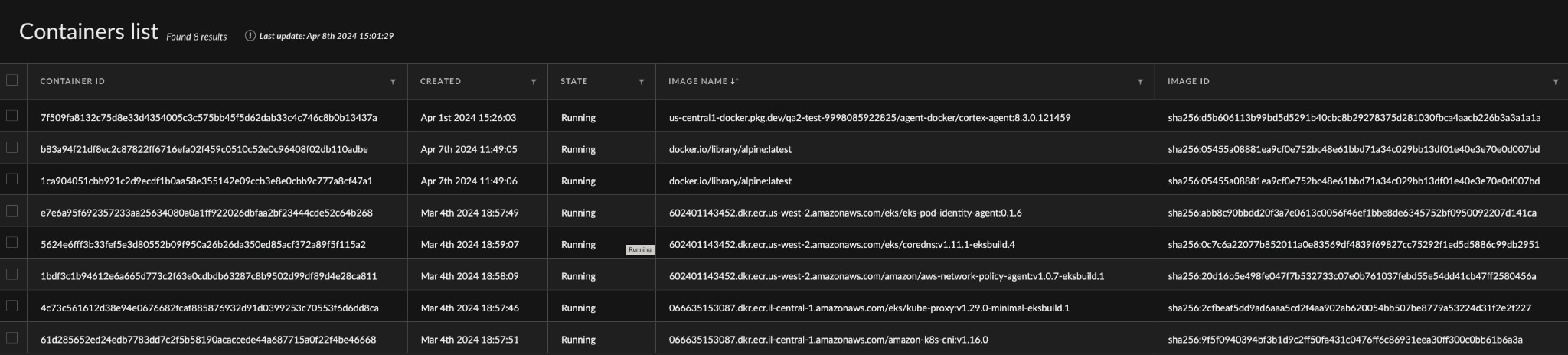
The Cortex XDR and XSIAM consoles also present a list of containers running on each Kubernetes Node within the cluster.
Kubernetes Agent Coverage
Cortex XDR and XSIAM leverage their advanced visibility features in Kubernetes to provide tailored endpoint protection capabilities and analytics-based detections, ensuring comprehensive coverage across various attacker tactics, techniques, and procedures (TTPs).
Cortex XDR and XSIAM detect threats in Kubernetes throughout the kill chain and the MITRE ATT&CK containers matrix. This includes exploits targeting containerized applications for initial access, execution attempts within pods for lateral movement, unauthorized access to credentials, exfiltration of persistent data, and deployment of privileged malicious pods and cryptominers for potential impact.
The Cortex XDR and XSIAM Agentless Approach to Protect Kubernetes Clusters
Security analysts can gather valuable insights and improve threat detection in their Kubernetes clusters with the help of Cortex XDR and XSIAM agentless solution for Kubernetes. By analyzing Kubernetes audit logs, analysts can uncover security risks and potential threats without the need to deploy additional agents directly onto their setup.
The agentless approach offers flexibility for organizations across managed and unmanaged environments, supporting setups in various cloud providers, allowing analysts to collect Kubernetes audit logs for analysis. These logs comprehensively record API calls within the cluster, ensuring a thorough overview of activities within the cluster. This high level of visibility enables analysts to quickly detect and respond to suspicious activity within the Kubernetes environment with the help of Cortex agentless solution for Kubernetes.
The Cortex agentless solution for Kubernetes provides tailored detections for managed Kubernetes environments. These detections are finely tuned to address common security risks and attack vectors unique to Kubernetes clusters. For instance, the Cortex agentless solution can detect unauthorized access to Kubernetes dashboard, suspicious anonymous user activity, and unusual access patterns to cluster resources.
By leveraging these capabilities, security analysts can enhance Kubernetes security effectively with Cortex XDR and XSIAM agentless approach.
The Synergy of Cortex XDR & XSIAM Agent for Kubernetes and Agentless Solution
The synergy between Cortex XDR and XSIAM Agent for Kubernetes and the agentless solution demonstrates a powerful integration, combining the strengths of each approach. While the agent excels in protecting and detecting attacks at the host and container levels, the agentless solution provides broader visibility into the entire cluster operation. This integration offers organizations a more comprehensive security posture, rather than considering them as competing alternatives.
Let’s illustrate this synergy with a recent real-world attack campaign based on the blog post ‘ScarletEEL 2.0: Fighting Kubernetes Threats at Scale’ from Sysdig. Breaking down the attack into phases, we can highlight how each solution could have been used to detect and respond.
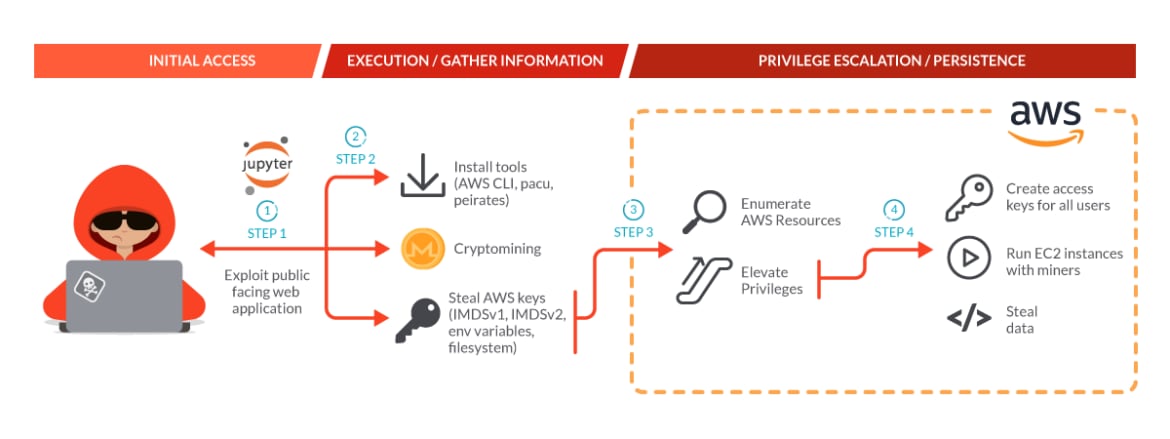
Phase 1: Initial Access via JupyterLab Exploitation:
The attack began with the exploitation of an Internet-facing JupyterLab Notebook within a Kubernetes cluster. The attack targets the container rather than the cluster, resulting in process, network, and file events being recorded by Cortex XDR and XSIAM agent for Kubernetes, triggering different agent-based detections. Given the alerts, security analysts can investigate the detected incident and respond accordingly.
Phase 2: Framework and Script Usage for Execution and Information Gathering:
In the second phase, the attackers used attack frameworks and scripts, targeting both the cluster and the compromised host. Security analysts can leverage both the agent and agentless solutions to detect such malicious activity.
The agentless solution, with its focus on the Kubernetes control plane, excels at detecting attacks at the cluster level. Consequently, it helps security analysts in efficiently detecting efforts to extract secrets from the cluster, enumerate the environment for information on cluster resources, execute within other pods for lateral movement, and deploy malicious pods for persistence and impact.
The agent, concentrating on the endpoint, is more effective for detecting attacks at the host and container levels. Thus, it assists security analysts in detecting attempts to extract credentials from the filesystem or the Instance Metadata Service (IMDS), deploy a cryptominer for impact, or exfiltrate data to an attacker controlled server.
Phase 3: Cloud Infrastructure Privilege Escalation and Persistence:
In the last phase, the attackers targeted the underlying cloud infrastructure of the Kubernetes environment using stolen credentials from phase 2, whether for reconnaissance, persistence, or impact. While not the primary focus, security analysts can leverage Cortex’s integrations with cloud providers to enhance the coverage of both the agent and agentless solutions, enabling them to detect attacks targeting the cloud environment.
Cortex XSIAM Auto-Remediation Solution for Kubernetes
Auto-remediating threats in Kubernetes managed environments is crucial for maintaining cluster security, but it presents unique challenges. Exposing the cluster to the Internet can expand the attack surface, while executing operations without exposure requires careful coordination. Additionally, Kubernetes' behavior of recreating pods presents a persistent challenge for removing malicious instances. This is compounded by the need for different permissions for the cluster and cloud provider.
Cortex XSIAM playbooks address these challenges by leveraging resources provided by the cloud providers. This allows the playbooks to temporarily create cloud resources and permissions, allowing them to execute operations within the cluster environment without exposing the cluster to the Internet. As a result, the playbooks can gather further insights about incidents from the cluster and remove malicious workloads from the Kubernetes environment, effectively halting the automatic creation of malicious pods by the control plane.
Closing Thoughts: Elevating Kubernetes Security with Cortex XDR & XSIAM
In conclusion, Cortex XDR and XSIAM offer a comprehensive security solution that effectively addresses the unique challenges of securing Kubernetes clusters. Providing both agent and agentless options, Cortex XDR and XSIAM allow organizations to tailor their security approach to their specific needs. The latest release of Cortex XDR and XSIAM introduce an agent-based and agentless detection analytics pack designed for managed and unmanaged Kubernetes environments, enhancing cloud workload protection by enabling proactive identification and mitigation of malicious content within containerized applications. This enhancement, combined with the ability to run playbooks to automate response actions, ensures the organization can confidently leverage the benefits of Kubernetes while protecting their clusters against a wide range of threat