Executive Summary
In today’s rapidly evolving digital landscape, cyber adversaries continually refine their techniques, presenting ever-increasing challenges for organizations striving to protect their assets. Among the many tools available to threat hunters, the Mark of the Web (MOTW) stands out as an important feature for enhancing security. Developed by Microsoft, MOTW tags files with a digital mark indicating their web origin and potential risk, offering essential metadata to assess the threat level of downloaded files.
Organizations often struggle with identifying and mitigating sophisticated threats that can compromise their systems. This is where Cortex XDR comes into play, leveraging MOTW-tagged data to enhance its security capabilities. In this blog post, we will explore how Cortex XDR helps organizations utilize MOTW to identify, analyze, and respond to potential threats embedded in marked files. By providing real-world examples and detailed analysis, we demonstrate how this integration aids security teams in preemptively isolating and neutralizing threats.
Cortex XDR's advanced telemetry and analysis capabilities allow threat hunters to prioritize their efforts by focusing on files flagged with MOTW. This ensures a more effective and targeted response, addressing the sophisticated threats that organizations face today. The ability to detect and mitigate malware before it compromises systems is crucial for maintaining robust security postures.
This post serves as a guide for security professionals looking to understand and implement MOTW as part of their threat hunting toolkit. By leveraging Cortex XDR, organizations can fortify their defenses and safeguard critical assets more efficiently and effectively.
|
Note: Mark of the Web (MOTW) data is available to customers deploying the Cortex XDR agent in versions 8.4 and above. |
|---|
Examples for how MOTW is used:
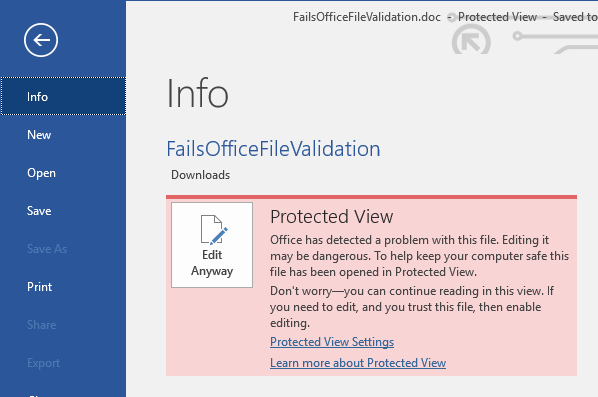
- Microsoft Office: When an Office document (e.g. Word, Excel) with a MOTW flag is opened, it opens in Protected View, restricting certain functionalities and requiring user action to enable editing.
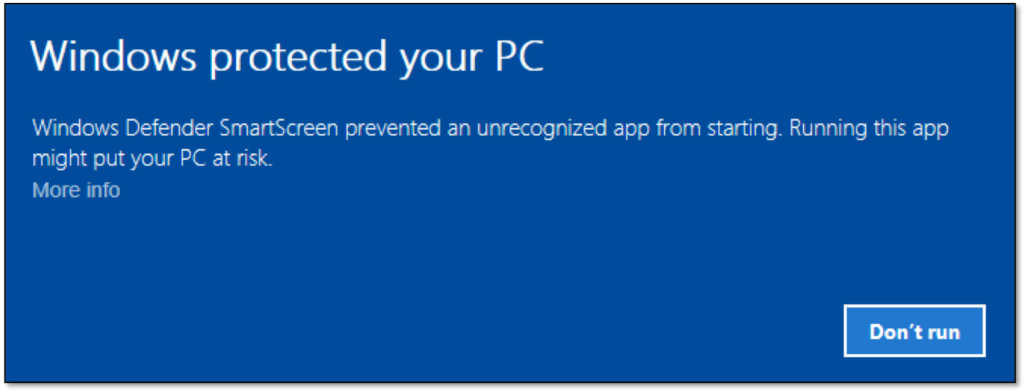
- Windows Explorer: When an executable file with a MOTW flag is run, a security warning prompt is displayed, alerting the user that the file might be unsafe.
Benefits for Threat Hunters
For threat hunters, MOTW provides a crucial layer of information that can be leveraged to identify and analyze potentially malicious files. Here’s how MOTW can aid in threat hunting:
- Identifying Malicious Files: Files with a MOTW tag can be prioritized for analysis since they originate from potentially untrusted sources.
- Behavior Analysis: Understanding how a file with MOTW behaves in a system environment can help in detecting unusual activities or the presence of malware.
- Incident Response: During an incident investigation, MOTW can help trace the origin of a malicious file, providing context on how it was introduced into the environment.
- Automated Detection: Security tools can be configured to automatically flag and quarantine files with MOTW for further inspection, reducing the risk of executing malicious content.
Hunting Queries
This section provides XQL queries designed to leverage Mark of the Web (MOTW) data within Cortex XDR. These queries enable threat hunters to identify potential threats associated with files flagged by MOTW. Utilize these queries to proactively hunt for and mitigate risks linked to web-downloaded content in your environment.
Hunting for Files Downloaded from URI's Containing IP Addresses
URIs containing IP addresses instead of domain names are considered suspicious in malware detection because they often bypass domain reputation checks and DNS monitoring, making them harder to trace. Malware frequently uses direct IP addresses for command and control (C2) communication to evade detection. This practice is unusual for legitimate services, which typically use domain names, indicating potential malicious intent. Additionally, many historical malware campaigns have used IP addresses to distribute payloads, adding to their suspicion rating in current threat analyses. These factors make such URIs a critical focus in threat hunting and malware detection.
|
// Description: Exploration of IPv4 URI’s for Files Downloaded dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter HostURL ~= "\bhttps?:\/\/(?:[0-9]{1,3}\.){3}[0-9]{1,3}(?::[0-9]{1,5})?(?:\/[^\s]*)?\.(exe|dll|bat|cmd|scr|ps1|vbs|js|jse|wsf|zip|rar|7z|tar\.gz)\b" OR ReferrerUrl ~= "\bhttps?:\/\/(?:[0-9]{1,3}\.){3}[0-9]{1,3}(?::[0-9]{1,5})?(?:\/[^\s]*)?\.(exe|dll|bat|cmd|scr|ps1|vbs|js|jse|wsf|zip|rar|7z|tar\.gz)\b" | alter URI_Host_IP = arrayindex(regextract(HostURL, "\b(?:\d{1,3}\.){3}\d{1,3}\b"),0) | alter rfc1918_172 = incidr(URI_Host_IP, "172.16.0.0/12") | alter rfc1918_10 = incidr(URI_Host_IP, "10.0.0.0/8") | alter rfc1918_192 = incidr(URI_Host_IP, "192.168.0.0/16") | filter rfc1918_172 = false and rfc1918_10 = false and rfc1918_192 = false and URI_Host_IP not in ("127.0.0.1", null, "") | fields agent_hostname, actor_effective_username, action_file_path, HostURL, ReferrerUrl, URI_Host_IP | dedup URI_Host_IP |
|---|
Hunting for Known Malicious File Extensions Downloaded from URI’s Containing Suspicious TLDs
URIs containing suspicious top-level domains (TLDs) like .xyz, .club, .zip, .info, .sbs, .ml, .gq, and .top are often flagged in malware detection due to their frequent association with malicious activities. These TLDs are popular among cybercriminals because they are cheap or even free to register, making them ideal for short-lived malicious campaigns. Additionally, the registration processes for these TLDs are typically less stringent, allowing attackers to obtain domains with minimal oversight. The prevalence of these TLDs in past malware campaigns and phishing schemes makes them a reliable indicator of potential threats.
|
// Description: Querying Suspicious TLD’s Downloaded Known Malware Files dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter HostURL ~= "https?://(?:[\w-]+\.)*[\w-]+\.(?:sexy|xyz|icu|tk|ga|cf|ml|pw|top|gq|ru|cn|work|info|club|loan|men|stream|cyou|monster|bar|host|io|date|surf|sbs|app|ly|dev|page|gd|gy|ms|zm|ug|sn|do|bd|np|sh|ng|id|sa|fail|exposed|viajes|zip)(?:[/?#]|$)" OR ReferrerUrl ~= "https?://(?:[\w-]+\.)*[\w-]+\.(?:sexy|xyz|icu|tk|ga|cf|ml|pw|top|gq|ru|cn|work|info|club|loan|men|stream|cyou|monster|bar|host|io|date|surf|sbs|app|ly|dev|page|gd|gy|ms|zm|ug|sn|do|bd|np|sh|ng|id|sa|fail|exposed|viajes|zip)(?:[/?#]|$)" | filter action_file_extension in ("exe", "dll", "scr", "bat", "iso", "js", "jse", "wsf", "vbs", "ps1") // Filtering for known file types used by malwares | fields agent_hostname, actor_effective_username, action_file_path, HostURL, ReferrerUrl | dedup ReferrerUrl |
|---|
Hunting for File Upload Sites Downloading Suspicious File Extensions
URIs containing domains such as dropbox.com, discord.com, telegram.org, github.com, and gitlab.com are increasingly flagged in malware detection due to their frequent use by threat actors to distribute malicious files. These platforms are popular among cybercriminals for hosting malware because they provide trusted and widely used file-sharing services, making it easier for attackers to disguise their malicious payloads as legitimate downloads. By exploiting these services, threat actors can bypass security measures like Mark of the Web (MOTW), as users are more likely to trust files from these sources.
|
// Description: File Upload Sites Downloading Known Malware File Types dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter HostURL in ("*dropbox.com", "*drive.google.com", "*onedrive.live.com", "*s3.amazonaws.com", "*pastebin.com", "*mega.nz", "*mediafire.com", "*github.com", "*bitbucket.org", "*docs.google.com", "*wetransfer.com", "*box.com", "*disk.yandex.com", "*pcloud.com", "*4shared.com", "*sendspace.com", "*zippyshare.com") OR ReferrerUrl in ("*dropbox.com", "*drive.google.com", "*onedrive.live.com", "*s3.amazonaws.com", "*pastebin.com", "*mega.nz", "*mediafire.com", "*github.com", "*bitbucket.org", "*docs.google.com", "*wetransfer.com", "*box.com", "*disk.yandex.com", "*pcloud.com", "*4shared.com", "*sendspace.com", "*zippyshare.com") | filter action_file_extension in ("exe", "dll", "scr", "iso", "js", "jse", "wsf", "vbs", "ps1", "msi") // Filtering for known file types used by malwares | fields agent_hostname, actor_effective_username, action_file_path, action_file_extension, HostURL, ReferrerUrl |
|---|
Hunting for Double Extension Files Downloaded from the Internet
This query looks for files that have been downloaded from the internet and are tagged with the Mark of the Web, specifically targeting those with double extensions like .pdf.exe or .docx.scr, which are commonly used by malware distributors. By correlating MOTW with the presence of double extensions, the query effectively identifies potentially suspicious files that may have bypassed initial security measures by disguising themselves as legitimate documents or images, thus aiding in the early detection and mitigation of malware threats.
|
// Description: Querying Double Extension File Types Downloaded From External URI’s dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter HostURL ~= "\bhttps?:\/\/[^\s/$.?#].[^\s]*\b" OR ReferrerUrl ~= "\bhttps?:\/\/[^\s/$.?#].[^\s]*\b" | filter action_file_name ~= "\b[a-zA-Z0-9_-]+\.(pdf|doc|docx|xls|xlsx|ppt|pptx|zip|rar|txt|jpg|jpeg|png|gif|bmp|rtf|html|htm|mp4|mp3|wav|avi|mov)\.(exe|scr|bat|cmd|com|pif|js|vbs|wsf|lnk|config|ps1|sh|jar)\b" | fields agent_hostname, actor_effective_username, action_file_name, action_file_path, HostURL, ReferrerUrl |
|---|
Detection of Suspicious UNC Paths in Mark of the Web (MOTW) Files
This query attempts to detect potentially malicious files by identifying UNC paths within the MOTW attribute. It specifically looks for files referenced by IP addresses in the UNC path, excluding internal IP ranges, to highlight suspicious downloads that might indicate an attempt to bypass security mechanisms.
|
// Description: Detection of Suspicious UNC Paths in Mark of the Web (MOTW) Files dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter ReferrerUrl ~= "\\\\(?:25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])\.(?:25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])\.(?:25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])\.(?:25[0-5]|2[0-4][0-9]|1[0-9]{2}|[1-9]?[0-9])(?::[0-9]{1,5})?\\" | alter URI_Host_IP = arrayindex(regextract(ReferrerUrl, "\b(?:\d{1,3}\.){3}\d{1,3}\b"),0) | alter rfc1918_172 = incidr(URI_Host_IP, "172.16.0.0/12") | alter rfc1918_10 = incidr(URI_Host_IP, "10.0.0.0/8") | alter rfc1918_192 = incidr(URI_Host_IP, "192.168.0.0/16") | filter rfc1918_172 = false and rfc1918_10 = false and rfc1918_192 = false and URI_Host_IP not in ("127.0.0.1", null, "") | fields agent_hostname, actor_effective_username, action_file_path, ReferrerUrl, URI_Host_IP, action_file_extension | dedup URI_Host_IP |
|---|
Adding Mark of The Web Context For Files Downloaded from the Internet
The following query takes the hostname as an input and uses the MOTW field data to gather information about downloaded files on a specific host. This is particularly useful for investigating suspicious files downloaded from the internet, allowing security analysts to identify and analyze potentially malicious downloads during an incident response.
|
// Description: Investigative Query for Downloaded Files on Host Using MOTW Data dataset = xdr_data | filter event_type = FILE and event_sub_type in (ENUM.FILE_CREATE_NEW, ENUM.FILE_WRITE, ENUM.FILE_RENAME) and lowercase(agent_hostname) contains lowercase("<agent_hostname>") and (lowercase(actor_process_image_name) in ("iexplore.exe", "chrome.exe", "msedge.exe", "firefox.exe", "opera.exe", "brave.exe", "webnavigatorbrowser.exe", "tor.exe", "browser.exe", "epic.exe", "safari")) and (action_file_path contains """\\Downloads\\""" or action_file_path contains "/Downloads/") | fields agent_hostname, agent_os_type, action_file_name, action_file_path, action_file_previous_file_path, action_file_extension, action_file_sha256, actor_process_image_name, actor_process_command_line, actor_effective_username, action_file_device_info, action_file_web_mark | filter action_file_path !~= "Zone[.]Identifier$" and action_file_extension != "crdownload" | join type=left conflict_strategy=left ( dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | filter lowercase(agent_hostname) contains lowercase("<agent_hostname>") | fields agent_hostname, actor_effective_username, action_file_path, action_file_web_mark as enriched_web_mark ) as web_mark (web_mark.action_file_path = action_file_path or web_mark.action_file_path = action_file_previous_file_path) and agent_hostname = web_mark.agent_hostname |
|---|
Case Study: Raspberry Robin Windows Script Files Campaign
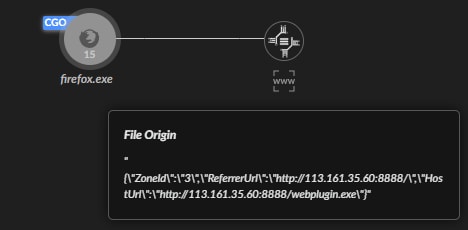
Using Mark of the Web (MOTW) data with the query for suspicious TLDs mentioned above, the Unit 42 Managed Threat Hunting team identified a campaign distributing Raspberry Robin malware via Windows Script Files (.JS and .WSF). These infections typically begin with a landing page that redirects users to a PHP download site, which then delivers an obfuscated script file to the user’s Downloads folder. When the user executes the script file with WScript.exe, the script performs multiple anti-analysis and VM detection checks. If the script determines it is running on a real end-user device, it downloads the final Raspberry Robin payload using a curl command and executes it. This payload can download and execute additional malicious files, establishing a foothold for further attacks.
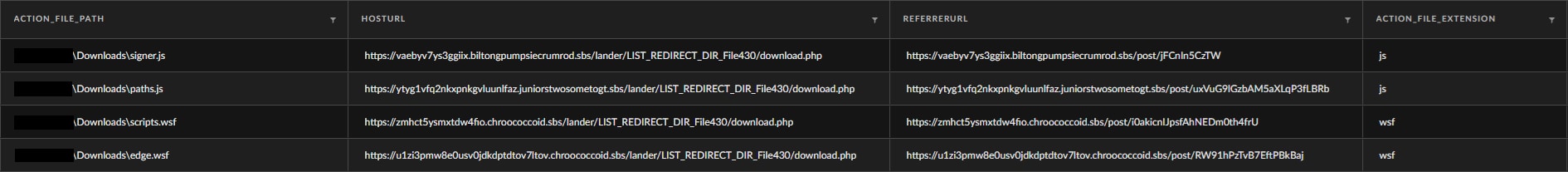
MOTW data was instrumental in discovering and tracking this campaign, highlighting the usage of specific URIs and files being dropped to disk. This data helped identify the campaign domains and file samples.
The following XQL query can assist with identifying additional variants of this campaign:
|
// Description: Querying Raspberry Robin URI's Downloading JS and WSF Files dataset = xdr_data | filter event_type = FILE and action_file_web_mark != null | alter HostURL = action_file_web_mark -> HostUrl | alter ReferrerUrl = action_file_web_mark -> ReferrerUrl | filter HostURL contains "lander/LIST_REDIRECT_DIR_File*/download.php" | filter action_file_extension in ("js", "wsf") | fields agent_hostname, actor_effective_username, action_file_path, HostURL, ReferrerUrl, action_file_extension |
|---|
Case Study: Download of Unauthorized Applications
Many organizations apply strict policies for downloading and using unauthorized applications in their environment, while hunting with the MOTW data using the XQL query mentioned above for IP addresses in URI’s, we have encountered several types of applications which are commonly unauthorized to use in these traditional organizations policies, applications varies from hacking tools, cracked applications, games and PUPs (Potentially Unwanted Applications)
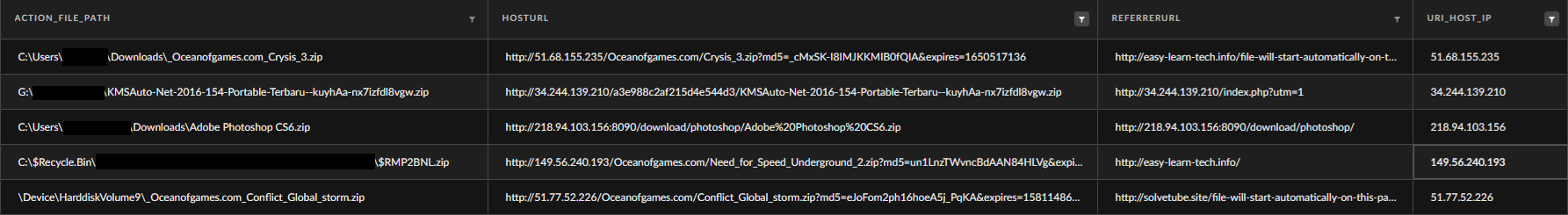
In the figure above we have noticed the download of:
- KMS Applications
- Cracked Applications
- Games
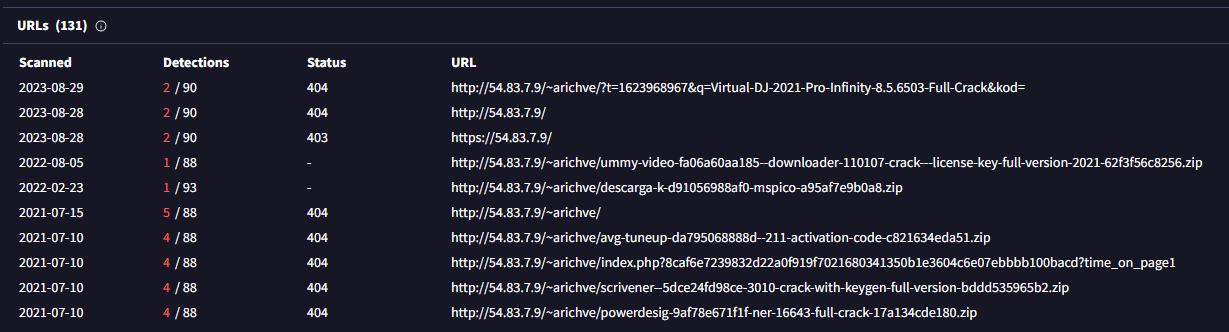
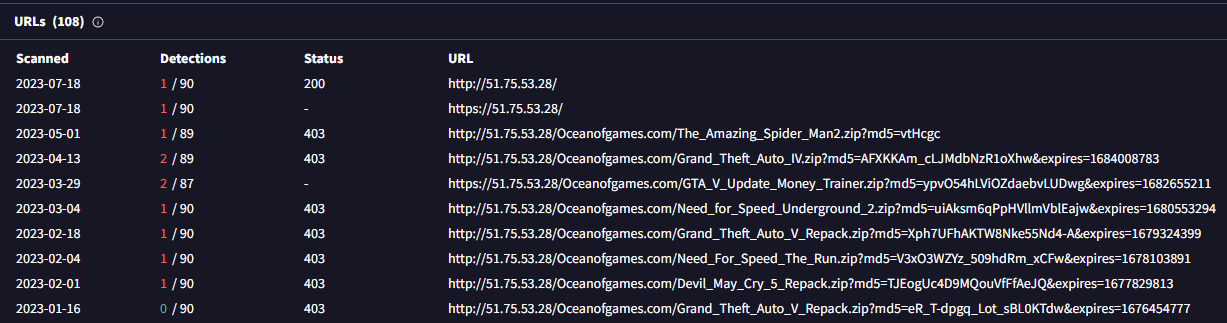
VirusTotal detections showcasing the usage of IP in the URI delivering software
Summary
Leveraging Mark of the Web (MOTW) with Cortex XDR enhances threat hunting by focusing on files tagged as originating from potentially risky sources. By employing techniques to detect suspicious elements such as unusual IP addresses, risky top-level domains, and uniquely structured URIs, threat hunters can effectively isolate and investigate threats. Utilizing MOTW allows organizations to proactively address security risks, ensuring a robust defensive stance against the evolving threats in the digital landscape.
About Unit 42 Managed Services
Unit 42 Managed Threat Hunting is a powerful service that empowers organizations to stay ahead of the ever-evolving threat landscape. Led by the renowned Unit 42 threat intelligence team, this service is designed to identify hidden attacks that would otherwise go undetected. Our team of expert threat hunters uses a combination of human expertise, big data analytics and comprehensive threat intelligence to surface malicious tactics, techniques, and procedures hiding in plain sight. This cutting-edge service is fueled by data collected and retained in the Cortex Data Lake, ensuring that organizations have access to the most comprehensive and accurate information available. With Unit 42 Managed Threat Hunting, organizations can take proactive steps to protect their assets and stay one step ahead of cybercriminals.