- What Is Container Security?
-
What Is Kubernetes?
- Kubernetes Explained
- Kubernetes Architecture
- Nodes: The Foundation
- Clusters
- Pods: The Basic Units of Deployment
- Kubelet
- Services: Networking in Kubernetes
- Volumes: Handling Persistent Storage
- Deployments in Kubernetes
- Kubernetes Automation and Capabilities
- Benefits of Kubernetes
- Kubernetes Vs. Docker
- Kubernetes FAQs
-
What Is Kubernetes Security Posture Management (KSPM)?
- Kubernetes Security Posture Management Explained
- What Is the Importance of KSPM?
- KSPM & the Four Cs
- Vulnerabilities Addressed with Kubernetes Security Posture Management
- How Does Kubernetes Security Posture Management Work?
- What Are the Key Components and Functions of an Effective KSPM Solution?
- KSPM Vs. CSPM
- Best Practices for KSPM
- KSPM Use Cases
- Kubernetes Security Posture Management (KSPM) FAQs
- What Is Orchestration Security?
- What Is Container Orchestration?
-
How to Secure Kubernetes Secrets and Sensitive Data
- Kubernetes Secrets Explained
- Importance of Securing Kubernetes Secrets
- How Kubernetes Secrets Work
- How Do You Store Sensitive Data in Kubernetes?
- How Do You Secure Secrets in Kubernetes?
- Challenges in Securing Kubernetes Secrets
- What Are the Best Practices to Make Kubernetes Secrets More Secure?
- What Tools Are Available to Secure Secrets in Kubernetes?
- Kubernetes Secrets FAQ
-
Managing Permissions with Kubernetes RBAC
- Kubernetes RBAC Defined
- Why Is RBAC Important for Kubernetes Security?
- RBAC Roles and Permissions in Kubernetes
- How Kubernetes RBAC Works
- The Role of RBAC in Kubernetes Authorization
- Common RBAC Permissions Risks and Vulnerabilities
- Kubernetes RBAC Best Practices and Recommendations
- Kubernetes and RBAC FAQ
-
Multicloud Management with Al and Kubernetes
- Multicloud Kubernetes Defined
- How Does Kubernetes Facilitate Multicloud Management?
- Multicloud Management Using AI and Kubernetes
- Key AI and Kubernetes Capabilities
- Strategic Planning for Multicloud Management
- Steps to Manage Multiple Cloud Environments with AI and Kubernetes
- Multicloud Management Challenges
- Kubernetes Multicloud Management with AI FAQs
-
Kubernetes and Infrastructure as Code
- Infrastructure as Code in the Kubernetes Environment
- Understanding IaC
- IaC Security Is Key
- Kubernetes Host Infrastructure Security
- IAM Security for Kubernetes Clusters
- Container Registry and IaC Security
- Avoid Pulling “Latest” Container Images
- Avoid Privileged Containers and Escalation
- Isolate Pods at the Network Level
- Encrypt Internal Traffic
- Specifying Resource Limits
- Avoiding the Default Namespace
- Enable Audit Logging
- Securing Open-Source Kubernetes Components
- Kubernetes Security Across the DevOps Lifecycle
- Kubernetes and Infrastructure as Code FAQs
- What Is the Difference Between Dockers and Kubernetes?
- Securing Your Kubernetes Cluster: Kubernetes Best Practices and Strategies
- Kubernetes: How to Implement AI-Powered Security
-
What Is a Host Operating System (OS)?
- The Host Operating System (OS) Explained
- Host OS Selection
- Host OS Security
- Implement Industry-Standard Security Benchmarks
- Container Escape
- System-Level Security Features
- Patch Management and Vulnerability Management
- File System and Storage Security
- Host-Level Firewall Configuration and Security
- Logging, Monitoring, and Auditing
- Host OS Security FAQs
- What Is Docker?
- What Is Container Registry Security?
- What Is Kubernetes Security?
- What Is a Container?
- What Is Containerization?
What Is Secrets Management?
Secrets management is the use of tools and techniques to securely store, access, and manage digital authentication credentials, also known as secrets. Organizations use secrets for digital authentication whenever privileged users — humans and machines — attempt to access protected data, applications, services, tools, containers, and cloud-native environments within their IT ecosystems.
An early step in secrets management involves identifying the secrets that need protection. Sensitive information includes:
- User or autogenerated passwords
- API keys
- Tokens for application use
- SSH keys
- Private certificates
- Private encryption keys for systems such as PGP, RSA, and other one-time password devices.
Organizations must choose secure storage and access control methods to maintain compliance with data protection regulations and ensure that only authorized users can access their resources.
Secrets Management Explained
Secrets management requires a comprehensive approach to protect sensitive information and maintain the integrity of systems and applications. In cloud environments, multiple nonhuman users (i.e., applications, services, automated processes) interact, increasing the attack surface and the potential for unauthorized access and data breaches.
Modern secrets management demands a holistic approach that accounts for the complexities of cloud environments, CI/CD pipelines, and nonhuman users. Centralized secret stores, least-privileged access control, dynamic secrets, auditing, and secure integration into CI/CD pipelines are key components of an effective secrets management strategy. These enable organizations to protect sensitive information and maintain the integrity of their systems and applications.
Why Is Secrets Management Important?
Applications, scripts, software, third-party tools, automation tools — and people — use privileged credentials to access resources, communicate with databases, and obtain encryption keys. But if these credentials aren’t secured, the gates of the enterprise are swung open, leaving assets across tool stacks, platforms, and cloud environments at risk.
Secrets in the digital era are ubiquitous, making secrets management integral to cloud security. As the use of cloud-based applications and datastores climbs, so does the need to protect sensitive information. Secrets management helps organizations to protect against data theft, unauthorized access, and other security threats.
Secrets Management Across the Enterprise
In enterprise-wide environments, the secrets management process must handle a diverse range of technology stacks, including legacy systems, commercial off-the-shelf applications, and custom applications. The diversity complicates the management process, as each system requires tailored solutions. Multiple departments and teams with varying access levels necessitate a granular and hierarchical approach to access controls.
Manual processes, such as IT teams handling access requests and granting privileges, can increase the risk of human error and unauthorized access. Additionally, compliance and governance are crucial in enterprise-wide environments, demanding comprehensive auditing, reporting, and monitoring capabilities in secrets management solutions.
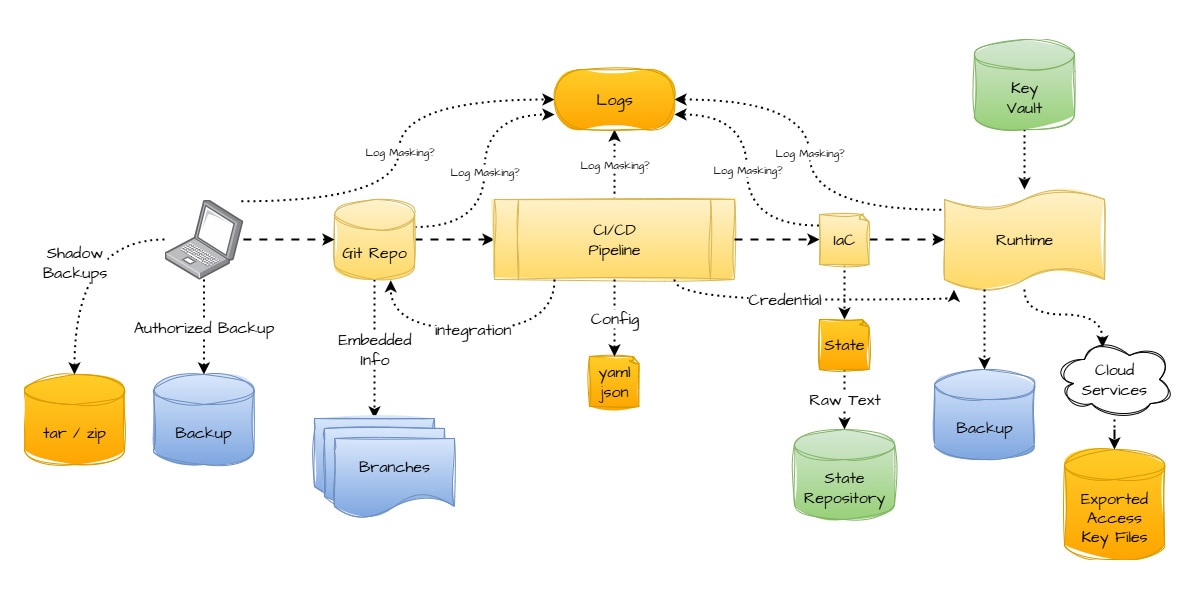
Figure 1: Secrets management within a CI/CD pipeline and cloud environment, highlighting potential locations of secrets (e.g., Git repos, configuration files, state files), their flow, and mechanisms like key vaults, backups, and log masking for handling them.
Secrets Management in DevOps Environments
For digital organizations, securing secrets in the DevOps pipeline is central to minimizing the attack surface. Automation and continuous delivery require secrets management solutions that securely inject secrets into applications and infrastructure as needed. These environments often rely on cloud-native technologies, like container orchestration platforms such as Kubernetes, necessitating tailored secrets management solutions.
The collaborative nature of DevOps teams demands a flexible approach, focusing on rapid access provisioning, revocation, and shared responsibility. What’s more, the frequent deployments and shorter development cycles in DevOps environments result in a higher volume of secrets and more frequent changes, requiring vigorous secrets rotation, automation, and dynamic secrets provisioning.
But security often — commonly — takes a backseat to agility. In the name of speed, developers have been known to hard-code credentials in source code, leaving secrets littered throughout configuration files and configuration management tools, or stored in plaintext in version control, wikis, and shared volumes.
Related Article: Exposed Credentials Across the DevSecOps Pipeline: 5 Places Secrets Hide in Plain Sight
When credentials in source code are publicly exposed, bad actors can gain unauthorized access and instigate attacks involving data leaks, code tampering, or service disruptions.
Challenges of Secrets Management
Despite the critical role secrets management plays in preserving the security of applications and infrastructure, organizations struggle with diverse challenges — including the consequences of mistakes. DevSecOps and IT are complicated fields. The many types of secrets an organization has to control makes transmitting and storing them difficult.
Incomplete Visibility
Managing privileged accounts, applications, tools, containers, and microservices — along with their associated passwords, keys, and secrets — presents a significant challenge in terms of scale. SSH keys can number in the millions at some organizations, for instance. Decentralized approaches, where admins, developers, and other team members manage their secrets separately or not at all, exacerbate this challenge. The result is fragmented control. security gaps, and challenges when it comes to auditing.
Remote Access
As employees access secrets from various locations and devices, the risk of exposure through unsecured networks, personal devices, and insecure communication channels increases. What’s more, the challenge intensifies as organizations need to enforce strict access controls and monitor usage without hindering the productivity of remote employees.
Default Security
Most new applications and IoT devices come preinstalled with default credentials, which are easy to crack. Even professional DevOps tools sometimes come with pre-made credentials that put the organization at risk if not changed.
Cloud-Based Services
Your company likely uses online services like Amazon Web Services and Microsoft Office 365. If so, you probably work with multiple virtual machines, which require secrets. How do you handle secrets with so many factors and data points to track? As the IT ecosystem increases in complexity and secrets proliferate, it becomes increasingly difficult to securely store, transmit, and audit secrets.
Hard-Coded Credentials
DevOps teams rely heavily on secrets for their tasks. As we know, secrets can hide anywhere — in infrastructure as code (IaC) and application code files, repo config files, and more. Subsequently, applications are often deployed with hard-coded credentials that hackers using scanning tools can crack.
Cleartext
When developers work together on an image in AWS, GCP, Azure, or some other cloud-native environment, it’s not uncommon for them to share .PEM files, SSH keys, and other configuration secrets in cleartext through various communication channels or store them in a directory or file assumed secure.
Secrets Sprawl
With the proliferation of multicloud and microservices, organizations have hundreds, or even thousands, of secrets their developers use for accessing machines. These secrets can be shared or left in code or just left unrevoked and leave organizations open to security incidents.
Related Article: The Top 5 Secrets Management Mistakes and How to Avoid Them
Privileged Credentials and the Cloud
Cloud and virtualization administrator consoles (as with AWS, Office 365, etc.) provide broad superuser privileges that enable users to rapidly spin up and spin down virtual machines and applications at a vast scale. Each virtual machine instance has privileges and secrets that need to be managed.
DevOps Tools
While secrets need to be managed across the IT ecosystem, DevOps environments amplify the challenges of managing secrets. Teams typically leverage dozens of tools that rely on automation and scripts requiring secrets to work. These tools, however, frequently have secrets hardcoded within the scripts or files.
Third-Party Vendor Accounts
Organizations rely on external services and APIs, which necessitate additional API keys and access tokens. The growing number of secrets associated with these integrations contributes to secrets sprawl.
Related Article: Ungoverned Usage of Third-Party Services
Manual Secrets Management
Manual secrets management processes are a recipe for error. Poor secrets hygiene, such as lack of password rotation, default passwords, embedded secrets, password sharing, and using easy-to-remember passwords, mean secrets aren’t apt to remain secret. Manual processes, in general, equate to a higher likelihood of security gaps and malpractice.
Related Article: Insufficient Credential Hygiene Explained
Secrets Management Best Practices
By following these best practices for secrets management, organizations can effectively protect their sensitive data, minimize the risk of security breaches, and maintain regulatory compliance.
Identify Sensitive Data
First, identify all types of password keys and other secrets across your entire IT environment. Secret types include passwords, access tokens, database credentials, encryption keys, and other sensitive information. Bring them under centralized management. Continuously discover and onboard new secrets as they’re created.
Limit Access to Secrets
Begin with access control. Least privilege and role-based access control are essential for managing secrets in complex environments. Ensuring that both human and nonhuman users have access only to the secrets necessary for their specific tasks reduces potential damage in the event of unauthorized access.
Rotate Secrets Regularly
Periodically change and rotate secrets to minimize the potential damage from compromised credentials. Establish a rotation policy that outlines the frequency and process for changing secrets. By implementing short-lived, temporary credentials — instead of long-lived, static credentials — organizations can ensure that even if a secret is compromised, its exposure is limited. Dynamically generated and automated rotation secrets minimize the window of exposure.
Eliminate Hard-Coded Secrets
No secrets in source control. Bring all hard-coded credentials in DevOps tool configurations, build scripts, code files, test builds, production builds, and applications under management. Regularly review your codebase for hard-coded secrets. Incorporate tools and practices, such as secret injection, container scanning, and automated security checks to maintain a high level of security and prevent the accidental exposure of sensitive information. Address any identified issues promptly to maintain a strong security posture.
Eliminate Default Passwords
Enforce password security best practices, Including password length, complexity, uniqueness expiration, rotation, and more across all types of passwords. Secrets should never be shared. If a secret is shared, it should be immediately changed. Secrets to more sensitive tools and systems should have more rigorous security parameters, such as one-time passwords and rotation after each use.
Elevate Accountability
Implement privileged session monitoring. Software that helps manage a secrets vault can also integrate with privileged access management (PAM) platforms, adding an extra layer of security and ensuring that access is restricted to users who need it. DevOps teams should be able to monitor privileged user activity and terminate sessions if necessary.
Encrypt Secrets
Always encrypt secrets, both at rest and in transit. Use strong encryption algorithms, such as AES-256, to protect sensitive data from unauthorized access and potential security breaches. Encryption keys used for encrypting and decrypting secrets should be appropriately managed and protected — meaning, they should be securely stored and rotated, in addition to implementing rigorous access control of the encryption keys.
Extend Secrets Management to Vendors
Ensuring that third-party services follow best practices for using and managing secrets requires oversight. Organizations should assign a dedicated team to manage vendor services. The oversight team should possess the skills and resources to effectively handle third-party integration, including understanding their functionalities, monitoring performance, and addressing security or compliance issues.
Log and Monitor Access
Continuously log and monitor access to secrets, including the identity of the requester, the time of access, and the requested secret. Regularly review logs to detect suspicious activity and potential security threats. The more integrated and centralized your secrets management, the better you can report on accounts, key applications, containers, and systems exposed to risk.
Audit and Compliance
Regularly audit your secrets management practices to ensure adherence to internal policies and external regulations. Address any identified gaps or weaknesses promptly to maintain a strong security posture.
Disaster Recovery and Backup
Implement a disaster recovery plan that includes backing up secrets in a secure, offsite location to ensure that sensitive data can be quickly restored in the event of a system failure or security breach.
DevSecOps
With the speed and scale of DevOps, it’s crucial to build security into the culture. Embracing DevSecOps means everyone shares responsibility for DevOps security, helping ensure accountability and alignment across teams. In practice, this should entail ensuring secrets management best practices are in place and that code doesn’t contain embedded passwords.
Related Article: Shift-Left Secrets Security: How to Prioritize Secrets Risks
A Comprehensive and Automated Solution
Secrets should not be stored in code repositories or configuration files. To ensure they’re not accidentally exposed, secrets should be stored in a secure location, such as a secrets management system or password vault.
But many secret management tools are incomplete, designed for one platform (i.e., Docker) or certain types of secrets. An incomplete tool won’t eliminate hard-coded and default passwords nor will it manage script secrets.
While application password management improves manual management processes and standalone tools with limited use cases, IT security would benefit from a holistic approach that manages passwords, keys, and other secrets throughout the enterprise.
Centralized secret stores, such as HashiCorp Vault or AWS Secrets Manager, enable organizations to maintain a single source of truth for all secrets, simplify access control, and track changes. These stores often provide features like encryption at rest, versioning, and automated rotation, enhancing security and minimizing the risk of compromise.
Secrets Management FAQs
A key vault is a secure, centralized storage system for managing cryptographic keys, secrets, and sensitive information such as API keys, passwords, and certificates. It provides access control, auditing, and encryption, ensuring that only authorized users and applications can access the stored keys and secrets.
Key vaults help organizations maintain compliance, reduce the risk of data breaches, and streamline the management of sensitive data across various services and applications.
Vault secrets management refers to the process of securely storing, organizing, and controlling access to sensitive information such as passwords, API keys, tokens, and certificates within a vault.
Vault secrets management solutions often provide features such as automatic secret rotation, versioning, and secure sharing, enabling organizations to enhance their security posture and simplify the handling of sensitive information.
Secrets scanning is the process of searching and identifying passwords, API keys, tokens, and other secrets within an organization's IT environment. It can involve scanning source code repositories, databases, cloud storage, configuration files, and other locations where secrets may be inadvertently stored or leaked.
Secrets scanning solutions typically use pattern matching, entropy analysis, or machine learning techniques to detect sensitive information and potential secrets leaking in any part of your SDLC and cloud infrastructure.
Privileged session management involves monitoring, recording, and controlling the activities of privileged users during their access to critical systems and data. The practice enables organizations to detect suspicious actions, enforce access policies, and maintain detailed audit logs for compliance and forensic purposes.
Privileged session management tools often provide features such as real-time alerts, session termination, and playback capabilities, facilitating enhanced oversight and control over privileged user activities.
Application access management is a security practice that focuses on managing and securing user access to applications and services within an organization. It involves implementing authentication, authorization, and auditing mechanisms to ensure that only authorized users can access specific applications and perform allowed actions.
Application access management solutions often include features such as single sign-on (SSO), multifactor authentication (MFA), and role-based access control (RBAC), helping organizations protect their applications from unauthorized access and potential security threats.
A certificate authority (CA) is a trusted entity that issues and manages digital certificates for secure communication and authentication over networks. CAs verify the identity of individuals, organizations, or devices before issuing certificates, ensuring that the certificate holder is legitimate. By validating the authenticity of digital certificates,
CAs play a crucial role in public key infrastructure (PKI), enabling secure communication, and trust in online transactions.
Public key infrastructure (PKI) is a system of policies, procedures, and technologies that enables secure communication, authentication, and data integrity over networks using public key cryptography. PKI components include certificate authorities (CAs), registration authorities (RAs), digital certificates, and public and private key pairs.
By managing the issuance, storage, and revocation of digital certificates, PKI establishes trust in online transactions, ensuring the confidentiality, integrity, and authenticity of the exchanged data.
An encryption key is a piece of data used with a cryptographic algorithm to transform plaintext into ciphertext (encryption) or ciphertext into plaintext (decryption). Encryption keys come in two types:
- Symmetric keys are used in symmetric encryption, where the same key is used for both encryption and decryption.
- Asymmetric keys, also known as public, and private key pairs, are used in asymmetric encryption, where the public key encrypts data and the private key decrypts it.
Just-in-time access is a security approach that grants users temporary, time-limited access to sensitive resources or systems only when it’s required for a specific task. JIT access reduces the risk of unauthorized access, data breaches, and insider threats by minimizing the exposure of privileged accounts and sensitive systems. The approach often involves implementing automated workflows to request, approve, and grant access, as well as monitoring and auditing user activities during the granted access period.
JIT access aligns with the principle of least privilege, enhancing an organization's security posture.
Multitenancy is an architecture principle in which a single instance of a software application or service serves multiple tenants, or customers, while keeping their data and configurations separate and secure. In a multitenant environment, strict access controls, data isolation mechanisms, and security measures are essential to prevent unauthorized access to or leakage of data between tenants.
Software as a service (SaaS), an example of multitenant architecture, requires vigilant attention to ensure tenant resources are properly isolated.