Secure Enterprise Browser | Prisma Access Browser
- 1. Securing third-party and contractor access
- 2. Monitoring and managing privileged user activity
- 3. Enabling secure BYOD policies
- 4. Preventing data exposure in GenAI apps
- 5. Mitigating web-based threats in the browser
- 6. Reducing VDI dependency
- 7. Securing undecryptable traffic
- 8. Protecting data at the last mile
- 9. Secure M&A onboarding
- 10. Preventing insider-driven data leakage
- Secure enterprise browser use cases FAQs
10 Secure Enterprise Browser Use Cases [+ Examples & Tips]
Secure enterprise browser use cases include:
- Securing third-party and contractor access
- Monitoring and managing privileged user activity
- Enabling secure BYOD policies
- Preventing data exposure in GenAI apps
- Mitigating web-based threats in the browser
- Reducing VDI dependency
- Securing undecryptable traffic
- Protecting data at the last mile
- Secure M&A onboarding
- Preventing insider-driven data leakage
- 1. Securing third-party and contractor access
- 2. Monitoring and managing privileged user activity
- 3. Enabling secure BYOD policies
- 4. Preventing data exposure in GenAI apps
- 5. Mitigating web-based threats in the browser
- 6. Reducing VDI dependency
- 7. Securing undecryptable traffic
- 8. Protecting data at the last mile
- 9. Secure M&A onboarding
- 10. Preventing insider-driven data leakage
- Secure enterprise browser use cases FAQs
- 1. 1. Securing third-party and contractor access
- 2. 2. Monitoring and managing privileged user activity
- 3. 3. Enabling secure BYOD policies
- 4. 4. Preventing data exposure in GenAI apps
- 5. 5. Mitigating web-based threats in the browser
- 6. 6. Reducing VDI dependency
- 7. 7. Securing undecryptable traffic
- 8. 8. Protecting data at the last mile
- 9. 9. Secure M&A onboarding
- 10. 10. Preventing insider-driven data leakage
- 11. Secure enterprise browser use cases FAQs
1. Securing third-party and contractor access
Independent workers—like freelancers, contractors, and consultants—often operate outside traditional IT boundaries. They use their own unmanaged devices, work across multiple organizations, and frequently require access to enterprise SaaS and private apps. Which means: they introduce risk that’s hard to control without also slowing them down.
Here's why this is a challenge.
Unmanaged devices increase the attack surface. Most ransomware and phishing attacks come through web browsers or compromised endpoints. And since independent workers often skip the same onboarding and oversight processes as full-time employees, sensitive data becomes harder to protect.
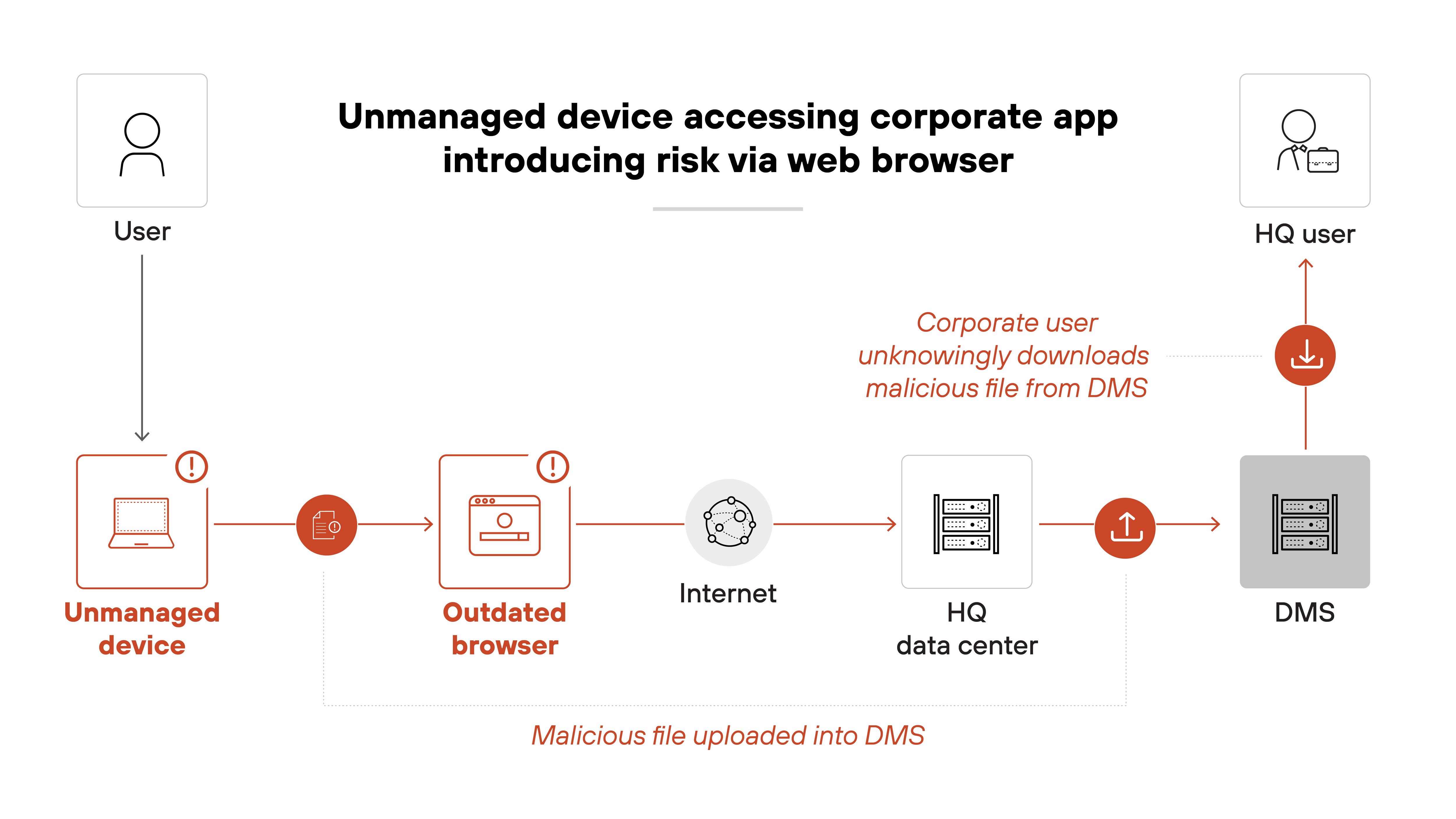
A secure enterprise browser helps contain this risk. It gives independent workers access to only what they need. With security policies enforced at the browser level—like masking sensitive data, blocking unauthorized uploads, and inspecting traffic in real time—it's possible to maintain compliance without deploying full desktop environments.
Like this:
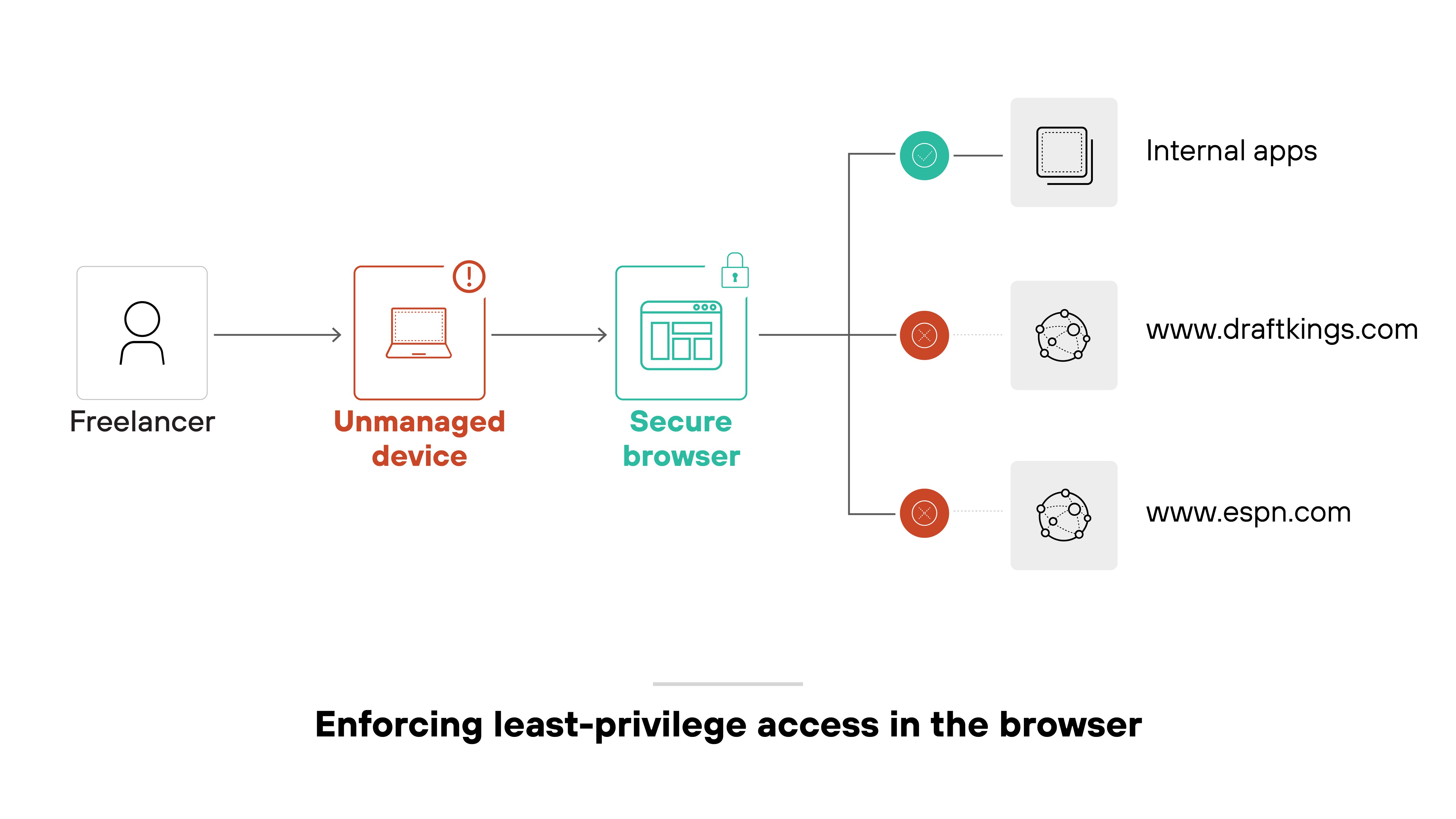
In other words: organizations can reduce complexity while extending protections across all users, regardless of device ownership or employment status. That’s key for maintaining productivity and security at the same time.
2. Monitoring and managing privileged user activity
Privileged users manage the systems that keep everything running. They hold elevated access to critical infrastructure, sensitive data, and administrative controls. Any compromise could lead to serious operational or security consequences.
The challenge is visibility and control. These users often work across environments and use secure protocols like SSH or RDP to access remote systems. Without fine-grained access policies and proper session oversight, privileged activity can bypass traditional defenses.
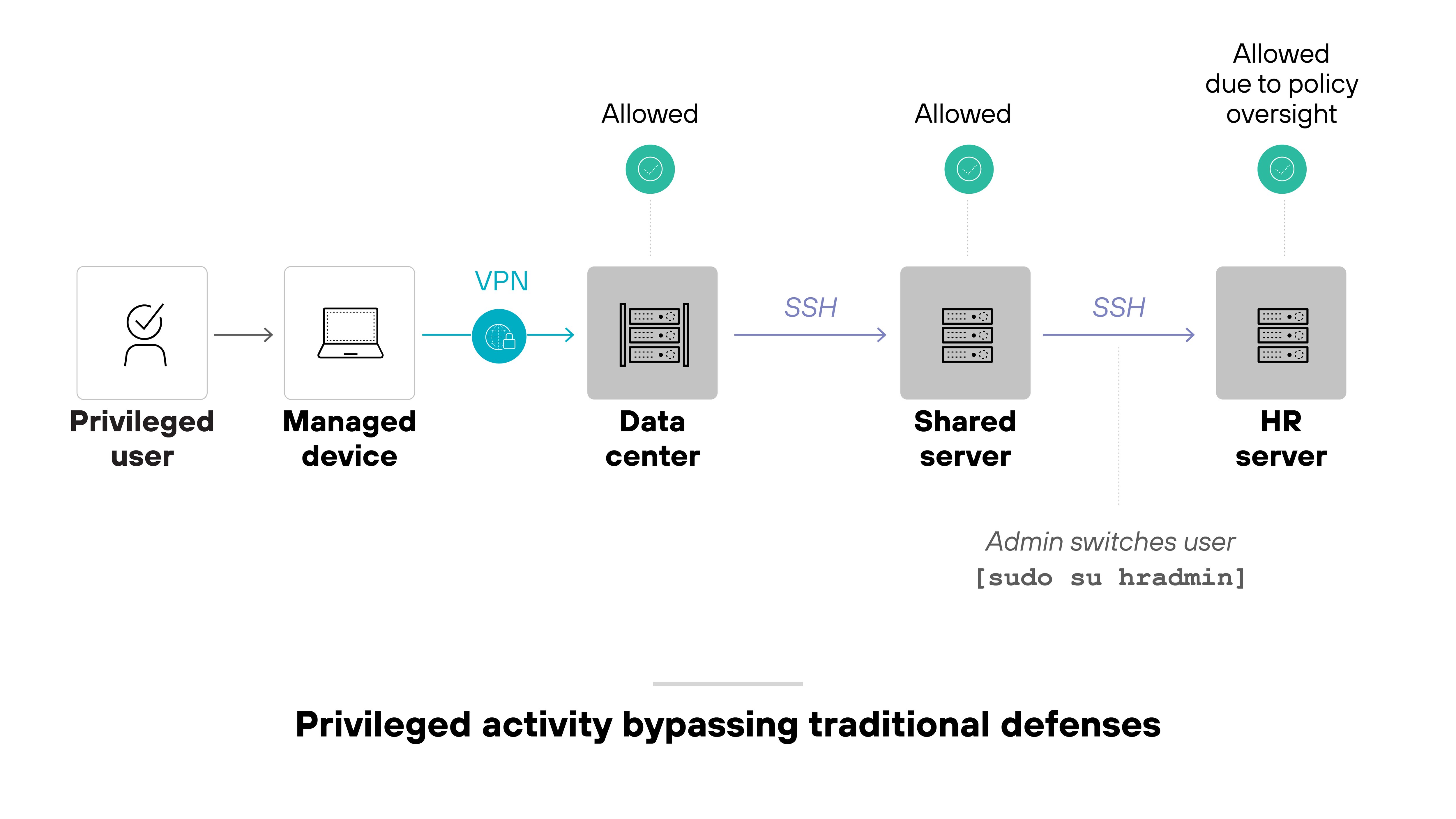
A secure enterprise browser helps reduce this risk.
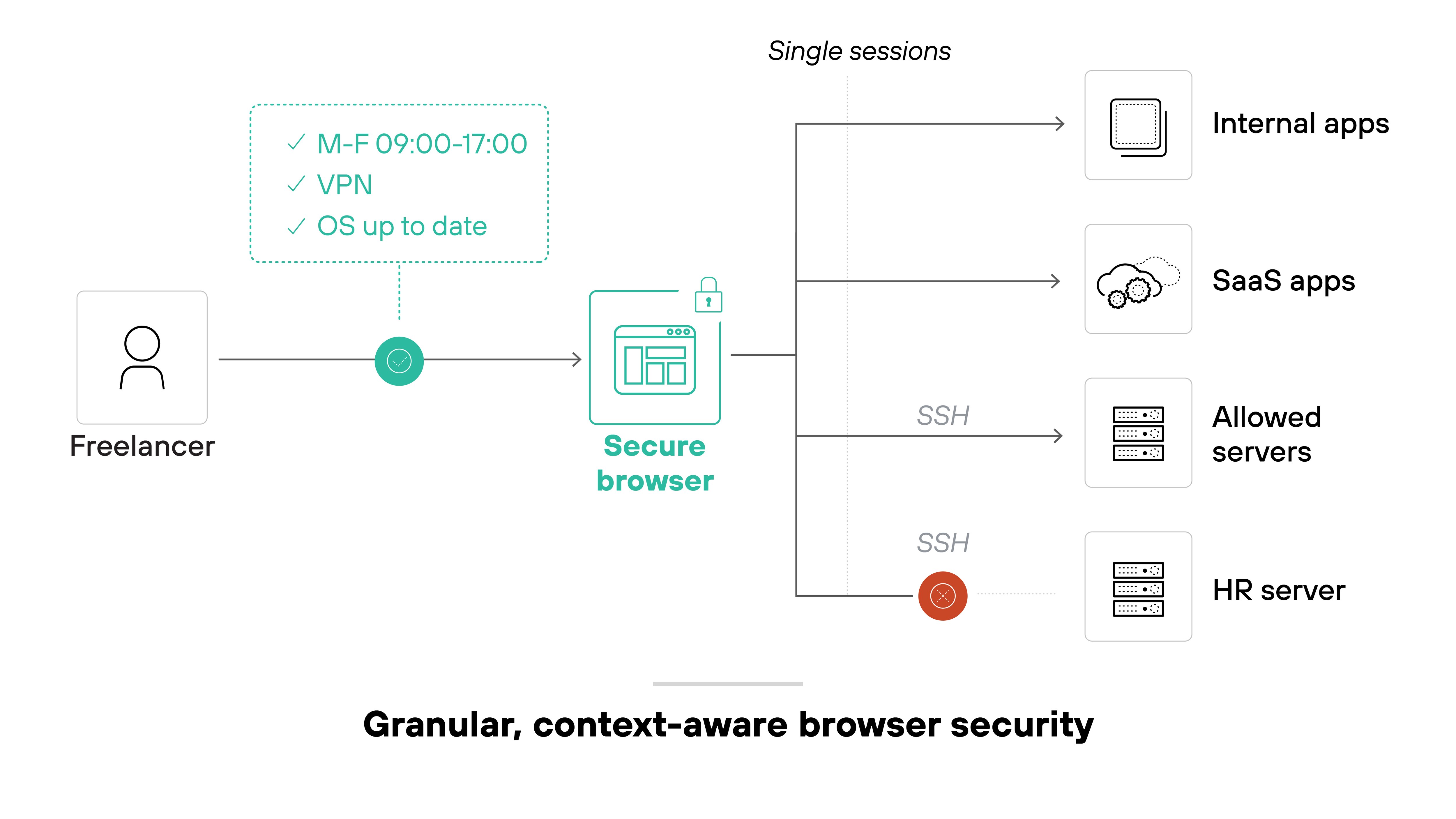
It enables contextual controls directly in the browser—like enforcing just-in-time access, device posture checks, and step-up authentication for sensitive tasks. It can also restrict session behavior, log actions, and apply least-privilege rules without needing full endpoint control.
Here’s how it works:
3. Enabling secure BYOD policies
Bring-your-own-device (BYOD) programs let employees use personal devices for work. This supports flexibility and can reduce hardware costs. But it also expands the attack surface—especially when unmanaged devices access sensitive applications.
Here's why that's a problem.
Most web-based threats originate from browsers. And without consistent controls across devices, organizations may lose visibility into risky behavior, data movement, or even credential misuse.
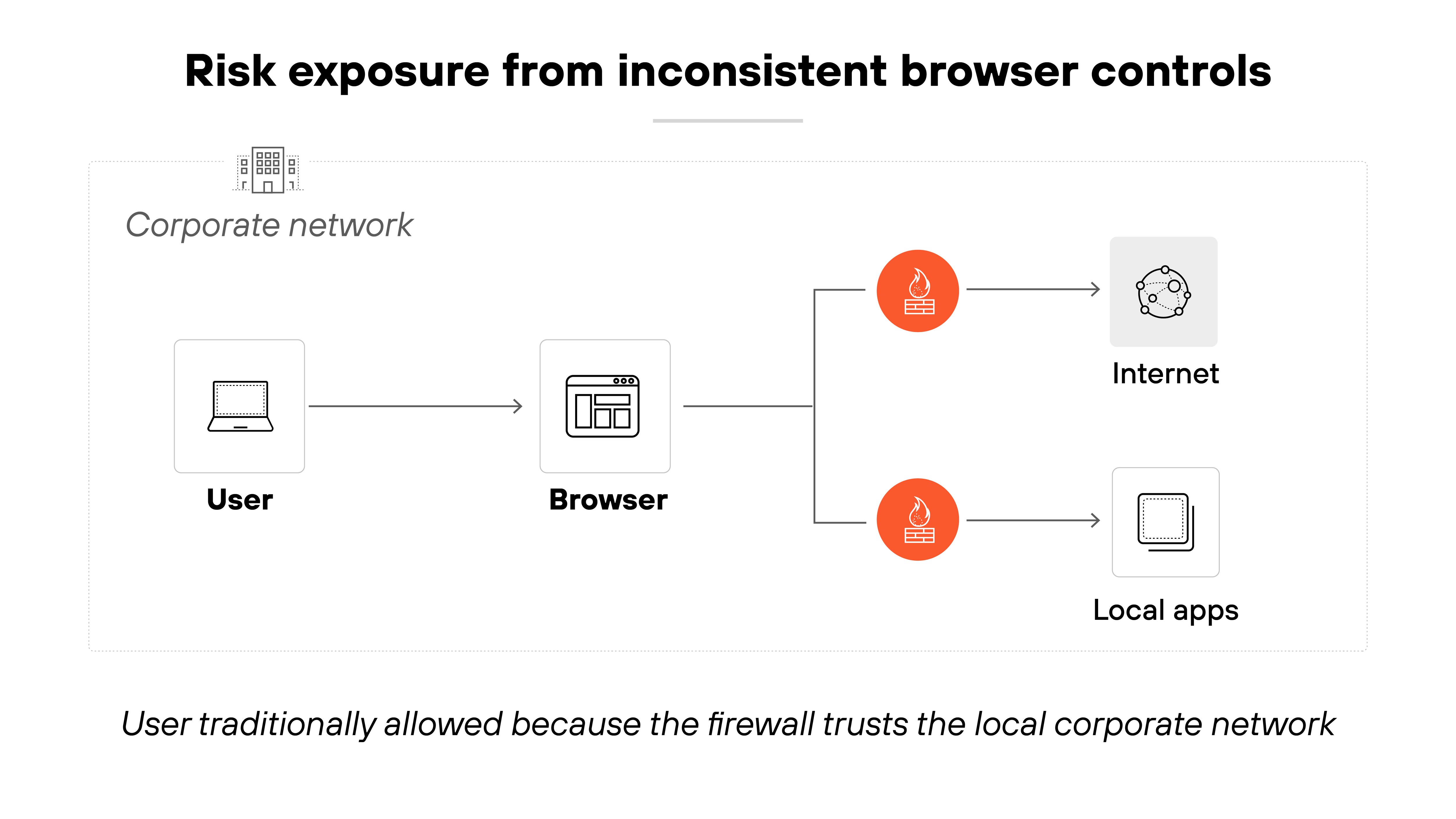
Traditional solutions like VDI and DaaS are often too expensive or frustrating to scale for every user.
A secure enterprise browser offers a more practical approach. It enables secure access to SaaS and private apps without requiring full device management. Security is applied directly in the browser—through posture checks, policy enforcement, and data protection controls—so personal devices stay isolated from enterprise assets.
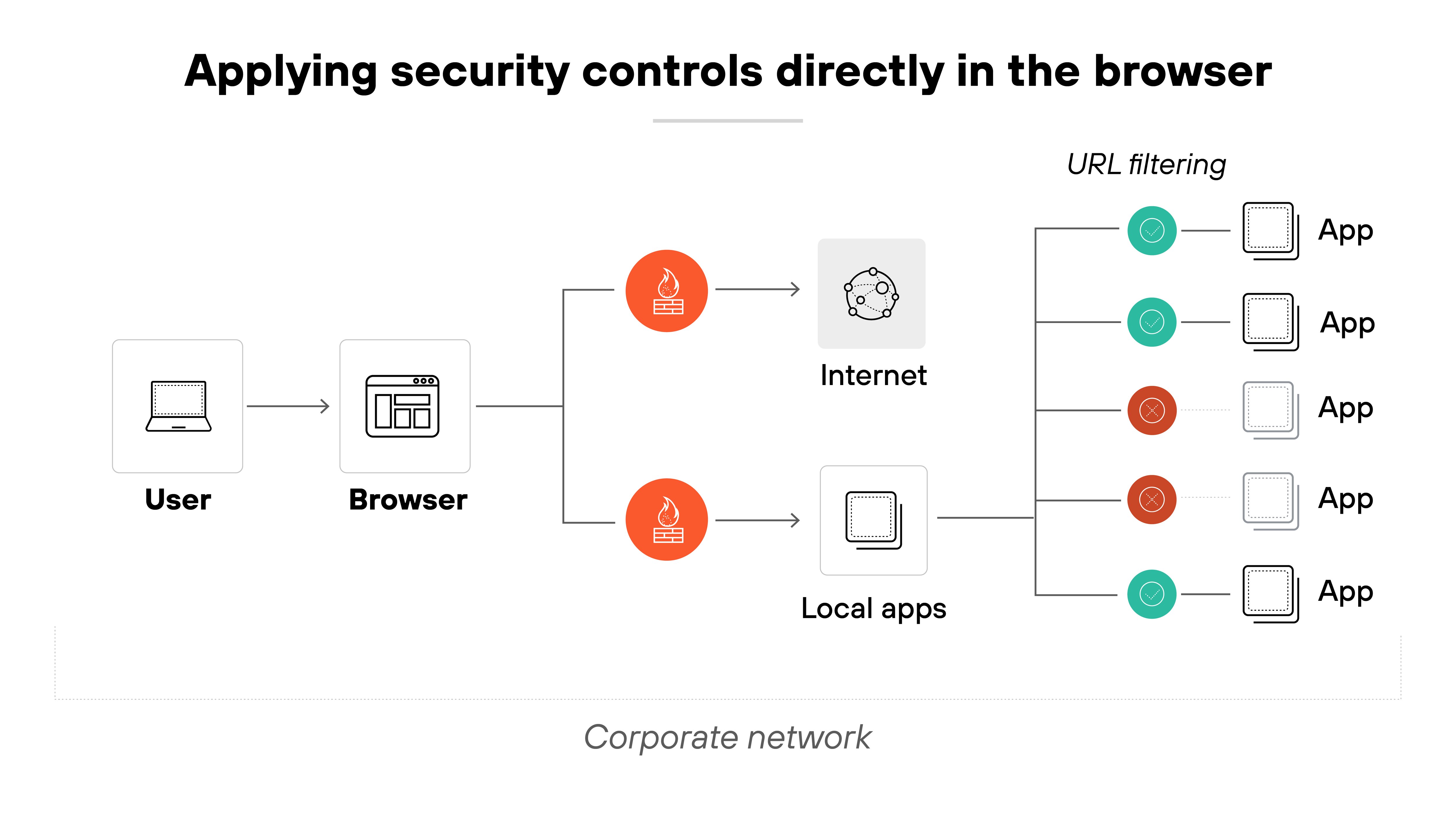
In other words: BYOD can stay flexible without compromising oversight. That balance makes it easier to support a modern workforce without creating new security gaps.
4. Preventing data exposure in GenAI apps
Today, most organizations have no visibility on user activity in GenAI apps.
And yet, generative AI tools are becoming a core part of many workflows. They support everything from content creation to software development and data analysis.
But they also create new security concerns—especially when users input sensitive data into public models.
Here’s why that matters.
Most GenAI platforms operate in the cloud. Which means: organizations don’t fully control where data goes once it’s submitted. Without guardrails, users can unknowingly share confidential information, intellectual property, or customer data with third-party services.
![Architecture diagram illustrating a scenario labeled 'Accidental data exposure in GenAI apps.' On the left, a user uploads a secure file that contains sensitive information such as social security numbers and account numbers. The user then issues a prompt that reads, 'Please summarize this file.' On the right, the GenAI system responds with a summary that includes partial sensitive data, displaying a response such as 'Account numbers starting with [000-00...].' Arrows connect the user and GenAI to show the flow of information between them.](/content/dam/pan/en_US/images/cyberpedia/secure-enterprise-browser-use-cases/Secure-Browser-2025_10.png)
A secure enterprise browser helps reduce that risk. It enables policy enforcement directly at the point of interaction—inside the browser. For example, security teams can block or redact sensitive inputs, apply content-based controls, and restrict usage based on identity, device posture, or app context.
In other words: organizations can safely enable GenAI without sacrificing data protection. That’s especially important as these tools become more integrated into daily operations.
5. Mitigating web-based threats in the browser
The browser is a primary target for external attacks. It connects users to SaaS apps, cloud platforms, and public websites—creating an open channel for phishing, malware, and exploit attempts. That's why browser activity needs to be monitored and controlled like any other threat surface.
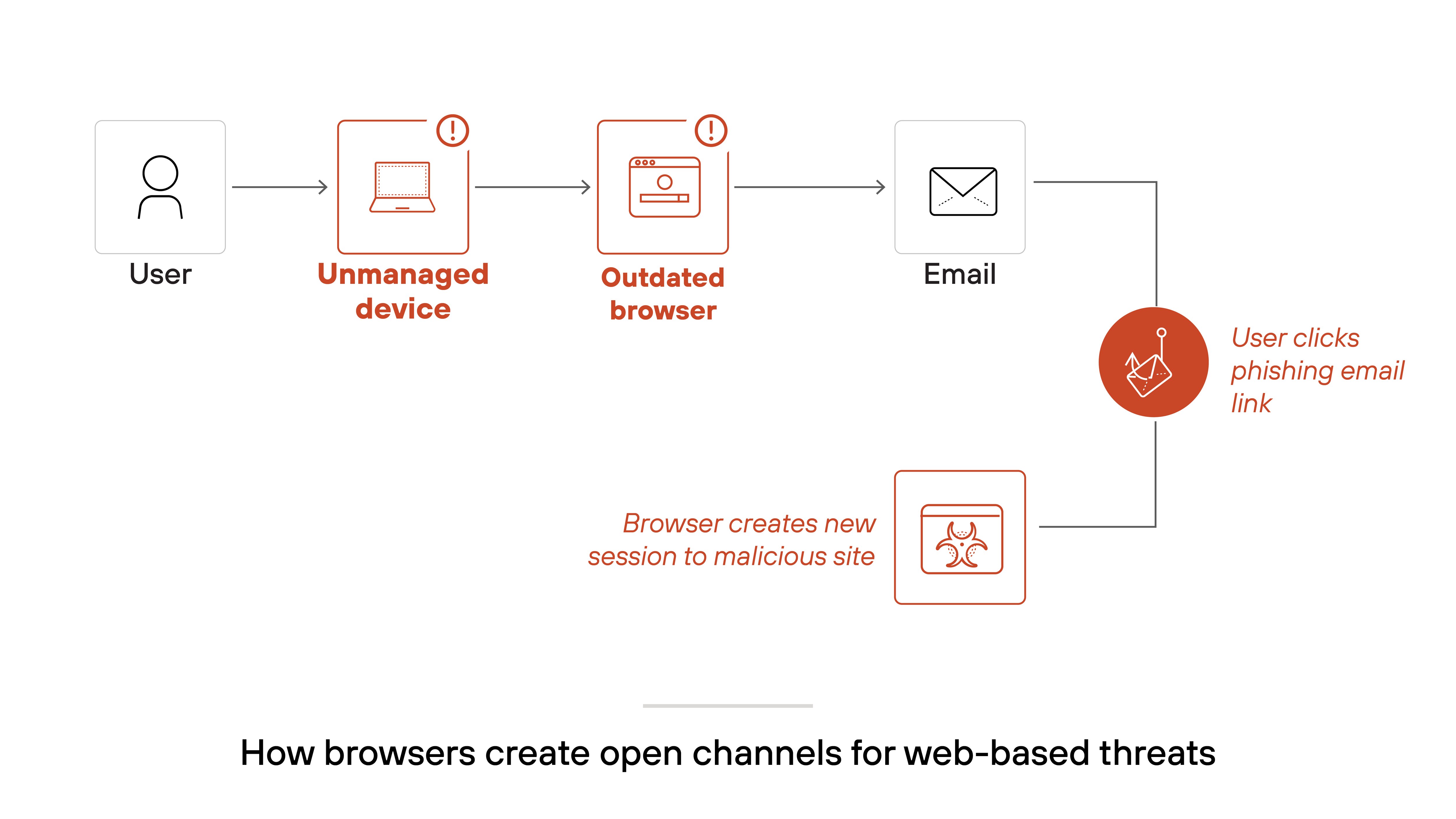
Here’s the challenge.
Most browsers aren’t built with enterprise risk in mind. They offer limited control over how users interact with data and applications. That makes it easy to trigger security incidents—even unintentionally—through downloads, third-party extensions, or unsafe websites.
A secure enterprise browser changes that.
It applies real-time controls at the point of use. Security teams can inspect behavior, enforce policies by app type or device posture, and block risky actions like downloading malware or logging into personal services.
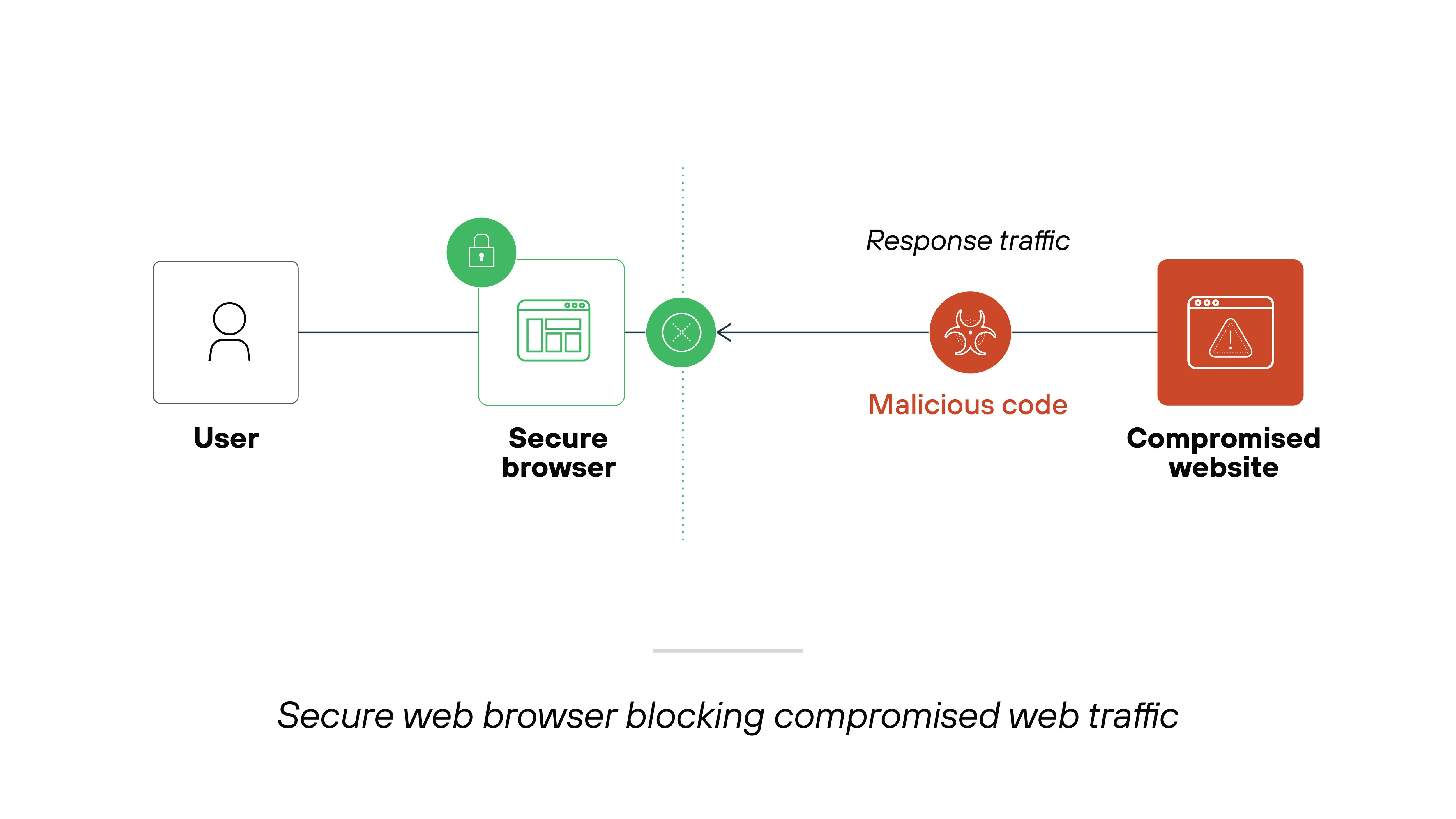
This reduces exposure without disrupting the user experience.
If you're deploying secure browser access, consider restricting domain-level logins to prevent users from signing in to personal accounts within the same session. This helps contain phishing attempts that rely on cross-account activity and keeps sensitive workflows separated from unmanaged destinations.
6. Reducing VDI dependency
Virtual desktop infrastructure (VDI) and desktop as a service (DaaS) are commonly used to support remote access. They offer centralized control and consistent user environments. But they also introduce high costs, complexity, and performance trade-offs.
Here's why that's becoming a problem.
VDI setups are difficult to scale and maintain. Many users only need access to web-based apps—not full virtual desktops. Running all activity through VDI creates overhead that may not be necessary.
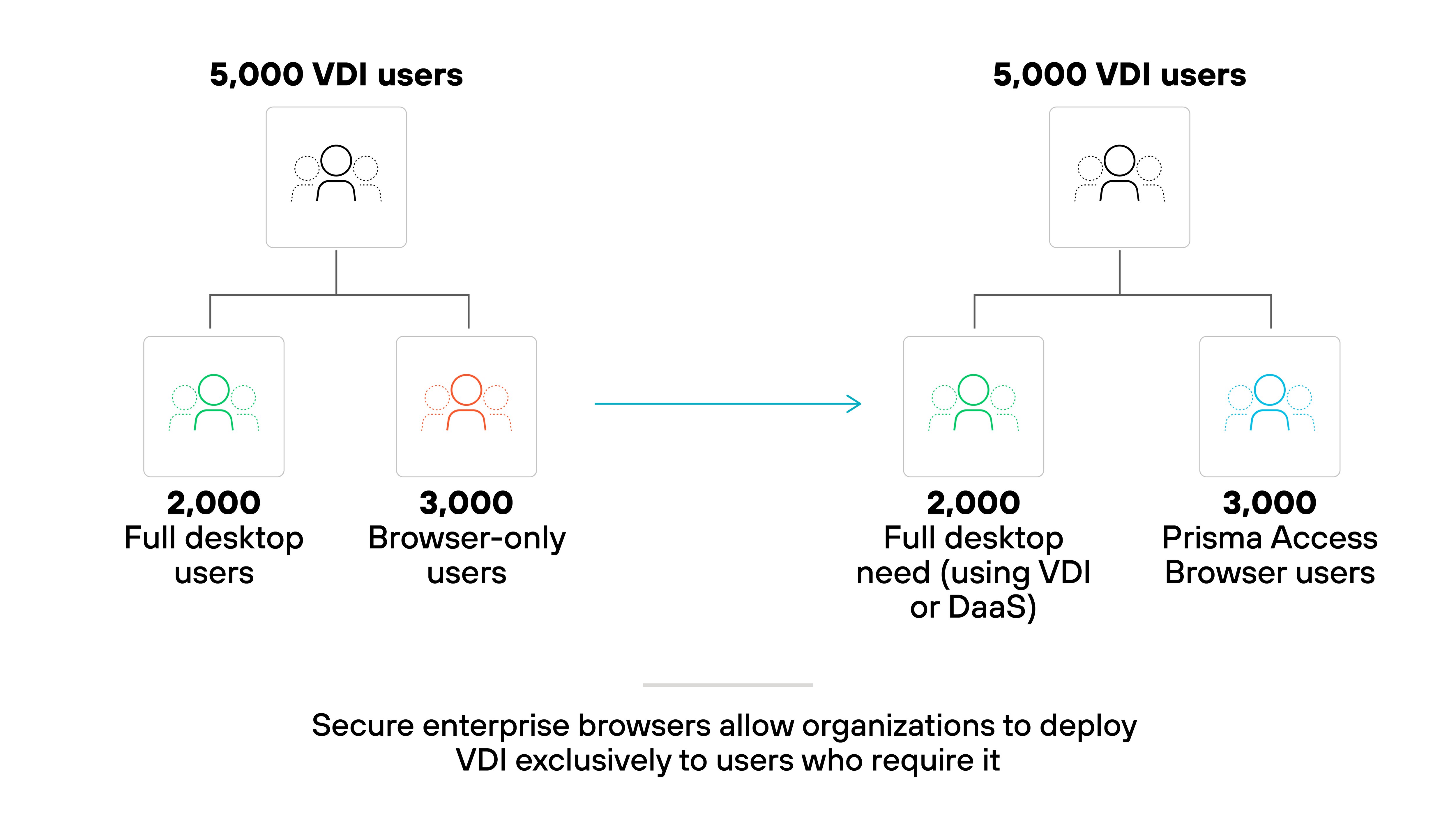
A secure enterprise browser offers a simpler option. It enables secure access to SaaS and internal web apps without relying on virtual desktops. That means fewer VDI licenses, reduced infrastructure needs, and a better user experience for browser-based tasks.
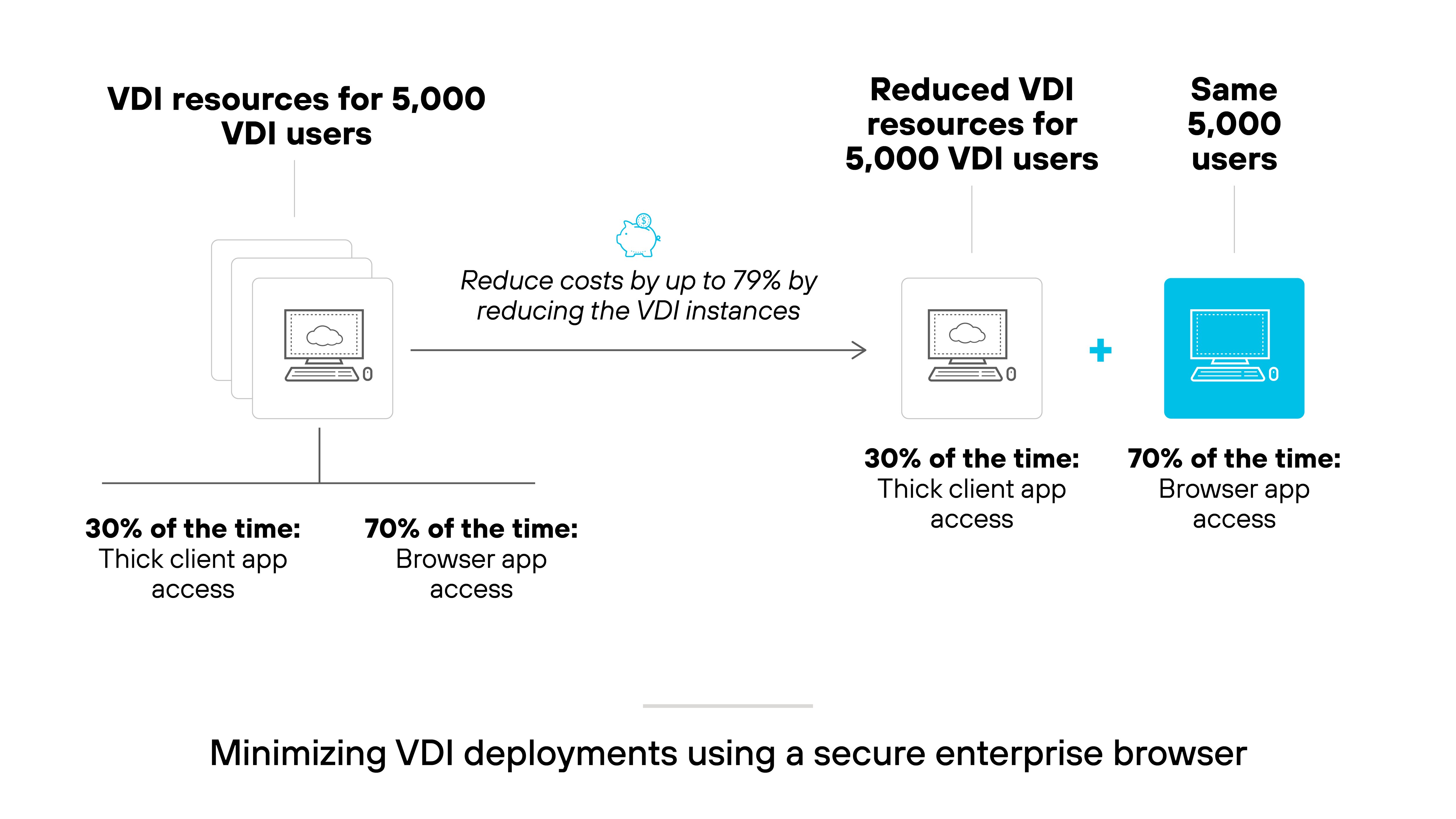
Essentially, organizations can reserve VDI for users who truly need it. Everyone else can operate securely through the browser, lowering cost and operational burden across the board.
7. Securing undecryptable traffic
Most internet traffic is now encrypted. That's a good thing for privacy. But it also makes it harder for traditional security tools to inspect and control what users are doing—especially inside the browser.
But here's the problem.
Some protocols, like QUIC, aren't easy to decrypt. Others, like Microsoft 365 traffic, come with service-level agreements that discourage deep inspection. So even if traffic is suspicious, security teams may not be able to analyze it without breaking compliance or disrupting performance.
A secure enterprise browser offers a different approach. Instead of decrypting traffic in transit, it applies controls directly at the point of use—within the browser itself.
This is how it works:
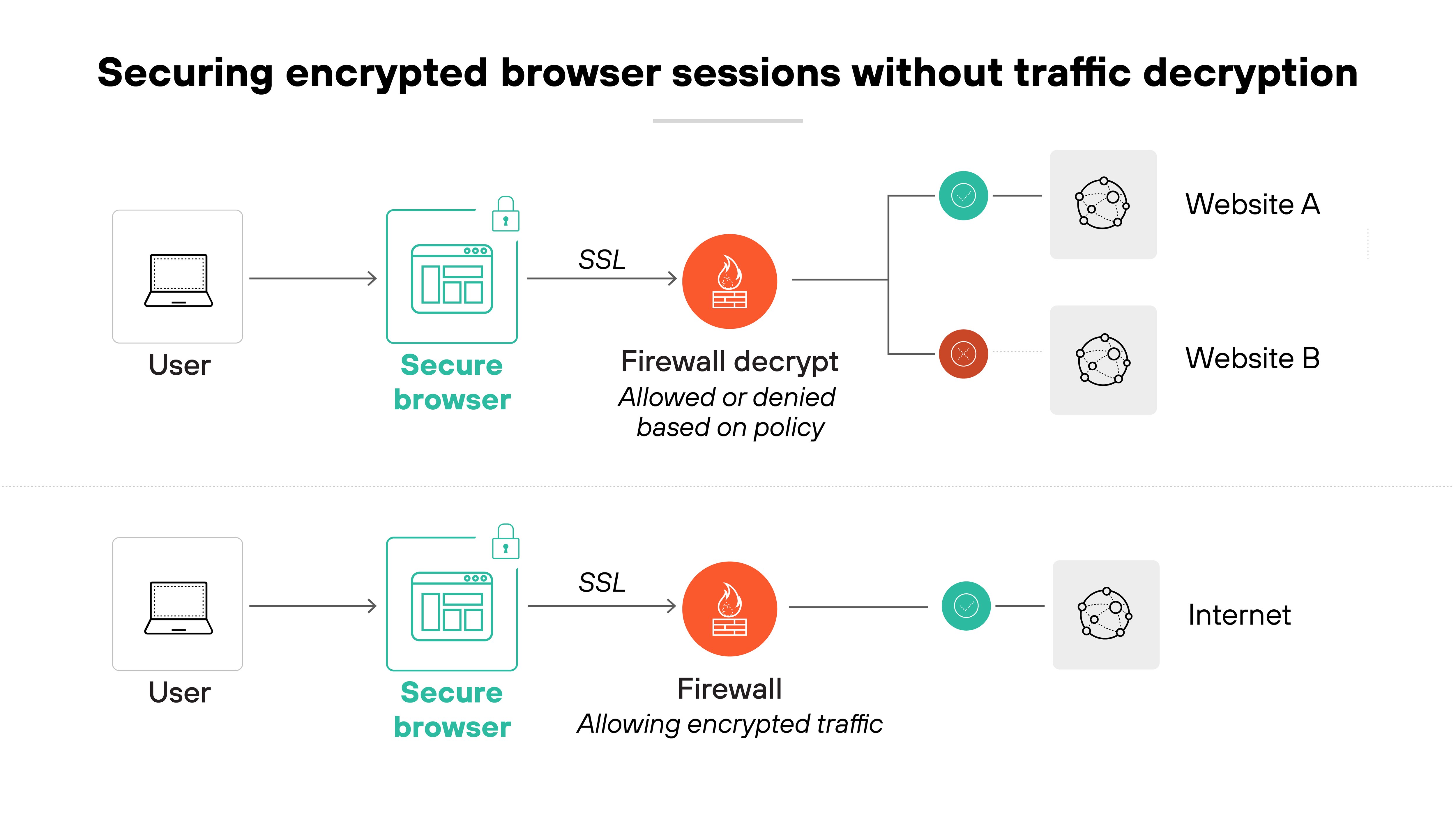
That means organizations can still monitor access, enforce policies, and detect risky activity even when the underlying traffic remains encrypted.
Basically, you don’t need to break encryption to secure the session. Browser-based visibility helps fill the gaps left by network-based tools, especially as more web and SaaS apps shift to modern encrypted protocols.
8. Protecting data at the last mile
The browser is where sensitive data is most exposed. Users read, edit, download, and share business-critical information in real time. Which means: the last mile—where users interact with data—is one of the most important places to apply security.
Here's why that matters.
Even with strong network and cloud protections, data is still at risk once it reaches the user. For example: someone might copy confidential content into a personal app, take a screenshot of sensitive material, or upload files to an unapproved drive. Traditional controls often miss this activity.
A secure enterprise browser addresses these gaps directly at the endpoint. It can mask sensitive data, block screenshots, restrict file uploads, and apply watermarks—without interrupting the user experience. These policies adapt based on content, user identity, and context.
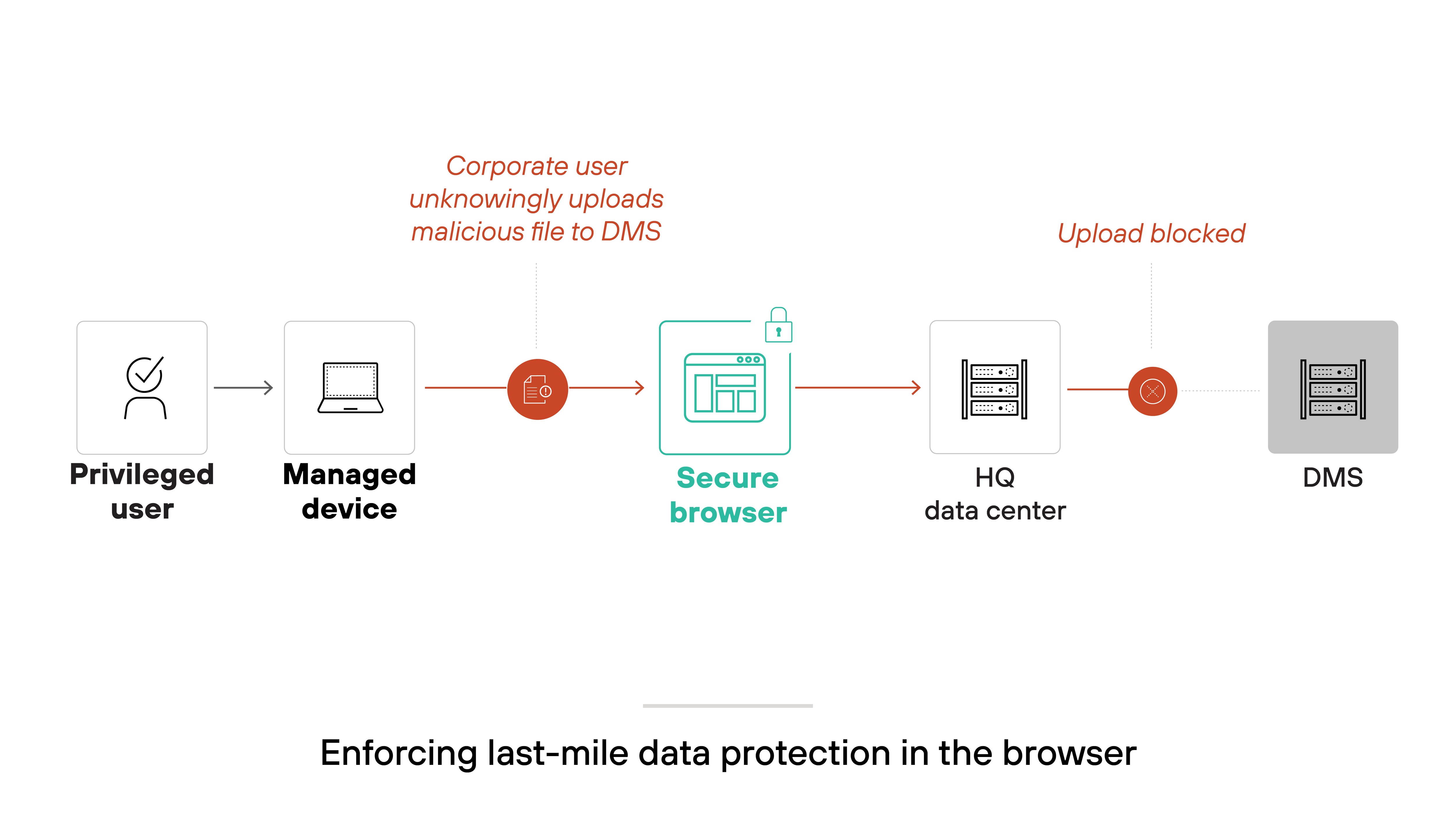
So: You get precise control over how data is accessed and used in the browser. That’s key to protecting information at its most vulnerable point—right before it leaves your environment.
9. Secure M&A onboarding
Mergers and acquisitions depend on speed. The faster newly acquired employees gain secure access to corporate applications and data, the faster the deal delivers value. Put another way, time-to-access directly impacts time-to-value.
There’s an issue, though.
Traditional onboarding approaches—like shipping laptops or provisioning VDI—take weeks. They also create logistical bottlenecks, raise costs, and delay productivity. Add compliance constraints or device assessments, and the timeline gets even longer.
A secure enterprise browser removes many of these delays. It enables secure access to SaaS, web, and private apps on both managed and unmanaged devices. Employees can start working in minutes, even before corporate hardware is delivered.

That means organizations can scale access quickly without sacrificing security. Browser-based controls enforce policy by user, device posture, or data type—helping IT stay compliant while enabling fast, secure integration.
Security teams can define access by user group, enforce device posture checks, and apply context-aware policies like watermarking, screenshot blocking, or file upload restrictions. These last-mile protections help prevent data leakage while employees work from personal or acquired devices. The browser also supports rapid offboarding, so access can be revoked instantly if needed.
10. Preventing insider-driven data leakage
Not all threats come from the outside. Insider risks—whether intentional or accidental—are a leading cause of data exposure. And browsers are one of the easiest ways for users to move sensitive information without detection.
That’s significant because:
The browser is where users access corporate tools, download files, and interact with data. Without guardrails, they can copy content into personal apps, upload files to unapproved destinations, or blur the line between work and personal use.
A secure enterprise browser gives security teams visibility and control over those actions. For example, they can block file uploads to personal drives, prevent copy-paste in high-risk workflows, or watermark sensitive sessions. They can also restrict login behavior or isolate sessions entirely to separate identities.
Put simply: You can reduce the risk of data loss without interrupting legitimate work. That makes browser-layer protection a practical defense against insider threats in modern work environments.
