- 1. What does a firewall do?
- 2. What are firewall rules?
- 3. What is firewall architecture?
- 4. What are the different types of firewalls?
- 5. What are the features of a firewall?
- 6. What are the benefits of a firewall?
- 7. What are the primary firewall challenges?
- 8. What are the main firewall threats and vulnerabilities?
- 9. How to configure a firewall in 6 steps
- 10. Top 10 firewall best practices
- 11. Comparing firewalls with other network security technologies
- 12. What is the history of firewalls?
- 13. Firewall FAQs
- What does a firewall do?
- What are firewall rules?
- What is firewall architecture?
- What are the different types of firewalls?
- What are the features of a firewall?
- What are the benefits of a firewall?
- What are the primary firewall challenges?
- What are the main firewall threats and vulnerabilities?
- How to configure a firewall in 6 steps
- Top 10 firewall best practices
- Comparing firewalls with other network security technologies
- What is the history of firewalls?
- Firewall FAQs
What Is a Firewall? [Firewall Definition & Explanation]
- What does a firewall do?
- What are firewall rules?
- What is firewall architecture?
- What are the different types of firewalls?
- What are the features of a firewall?
- What are the benefits of a firewall?
- What are the primary firewall challenges?
- What are the main firewall threats and vulnerabilities?
- How to configure a firewall in 6 steps
- Top 10 firewall best practices
- Comparing firewalls with other network security technologies
- What is the history of firewalls?
- Firewall FAQs
Firewalls act as barriers between private and external networks, checking and filtering data based on set security rules. Using these rules, firewalls decide if they should allow, block, or drop the data to protect the network.
Form factors include hardware, software, or a mix of both. This process ensures only safe, legitimate traffic gains entry.
What does a firewall do?
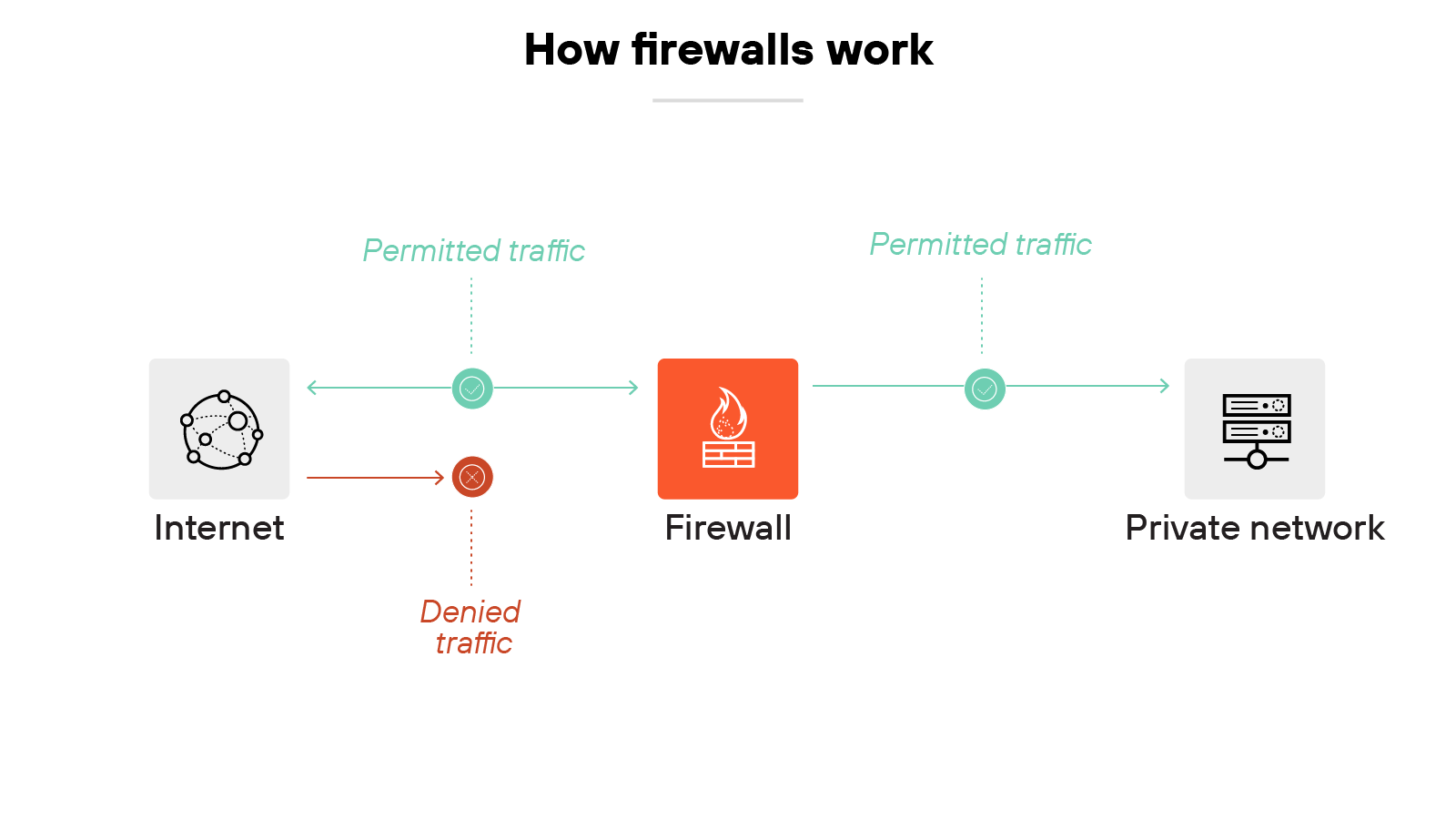
Firewalls monitor and manage network traffic.
Their job is to protect network devices (also referred to as hosts). That can mean computers, servers, or anything else with an IP address.
Basically, firewalls filter traffic to determine what should be allowed and what should be blocked.
To break it down further, a firewall uses rules to make those decisions. Rules can be based on IP addresses, protocols, ports, or other packet-level details. If a packet violates the rules, the firewall blocks it.
More advanced firewalls don’t just look at packets one by one. Instead, they use stateful inspection, which means they track the entire session that a packet belongs to. That way, they can understand if packet behavior is expected or unusual.
Like this:
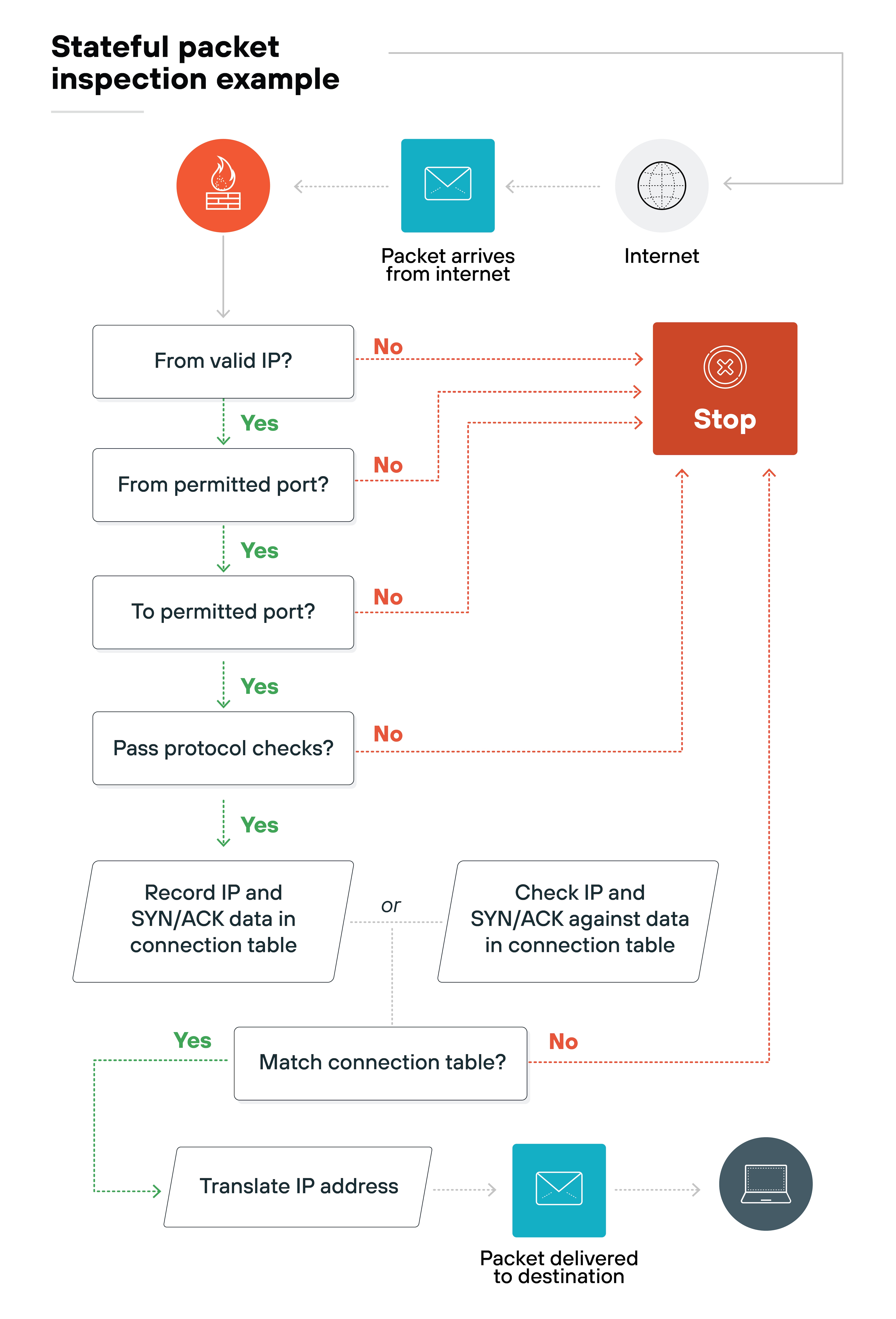
This matters because looking at the full context helps detect more complex or stealthy threats.
Firewalls also rely on threat intelligence. They compare traffic against databases of known malicious signatures. If a match is found, the firewall blocks the traffic.
Firewalls also treat different types of traffic differently.
Inbound traffic—called north-south—comes from outside the network. That includes internet traffic. It’s more likely to carry threats, so firewalls inspect it carefully.
Internal traffic—called east-west—moves between devices inside the network. It’s often overlooked, but it can be risky. Attackers that get past the perimeter can use east-west traffic to move laterally and access more systems.
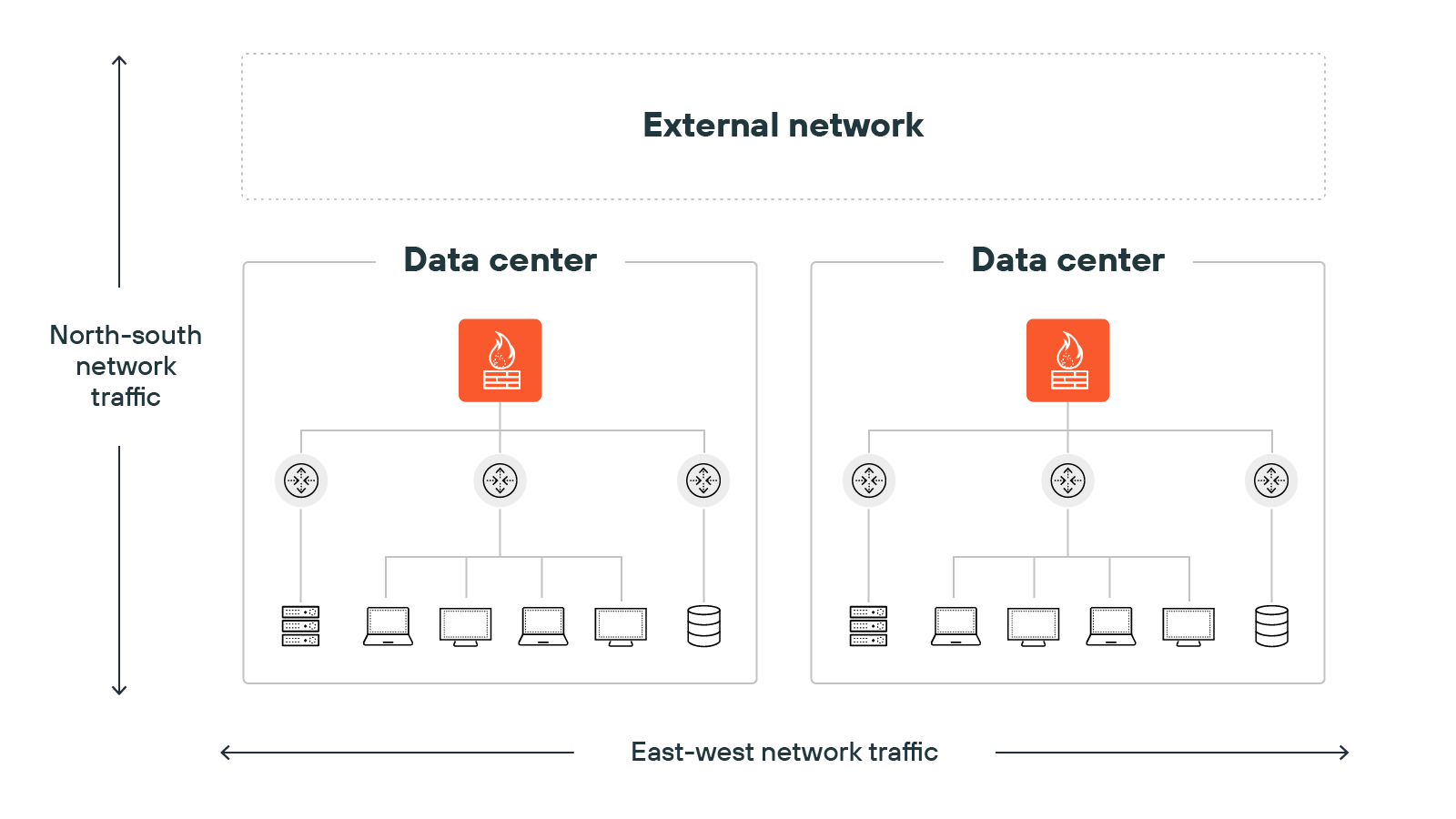
Which is why inspecting internal traffic is important too.
Not to mention:
Firewalls help enforce access control. Most organizations today follow the principle of least privilege so that users and devices only get access to what they need. No more, no less. It’s one of the most effective ways to limit risk.
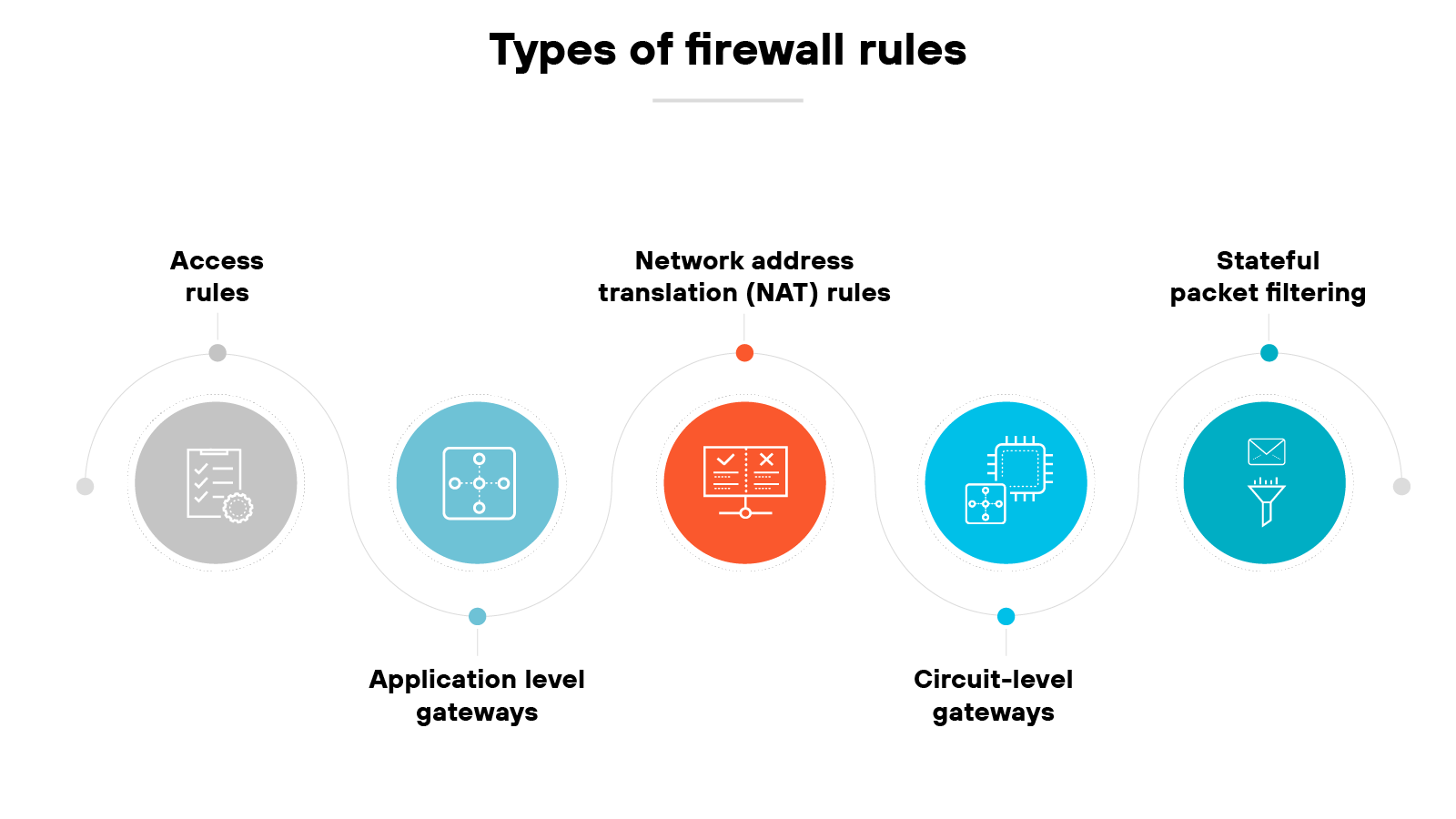
Firewall rules define how to handle network traffic.
These rules decide what to allow and what to block. They’re based on attributes like source and destination IP addresses, ports, and protocols.
There are several types of firewall rules, each handling a different aspect of traffic control:
Types of firewall rules
| Rule type | Description |
|---|---|
| Access rules | Manage traffic by evaluating parameters like source and destination addresses, protocol, and port number. Traffic is permitted, blocked or denied based on these evaluations. |
| Network address translation (NAT) rules | Alter IP addresses as traffic moves between networks. Facilitate routing and can help protect private networks from external threats. |
| Stateful packet filtering | Inspects data packets relative to existing network states. Decisions are made by comparing each packet to known connection sessions. |
| Application level gateways | Operate at layer 7 of the OSI model. Mediate traffic between external and internal networks and are often used to control access. |
| Circuit-level gateways | Work at layer 5 of the OSI model. Monitor TCP handshakes to verify session legitimacy without inspecting individual packets. |
What is firewall architecture?
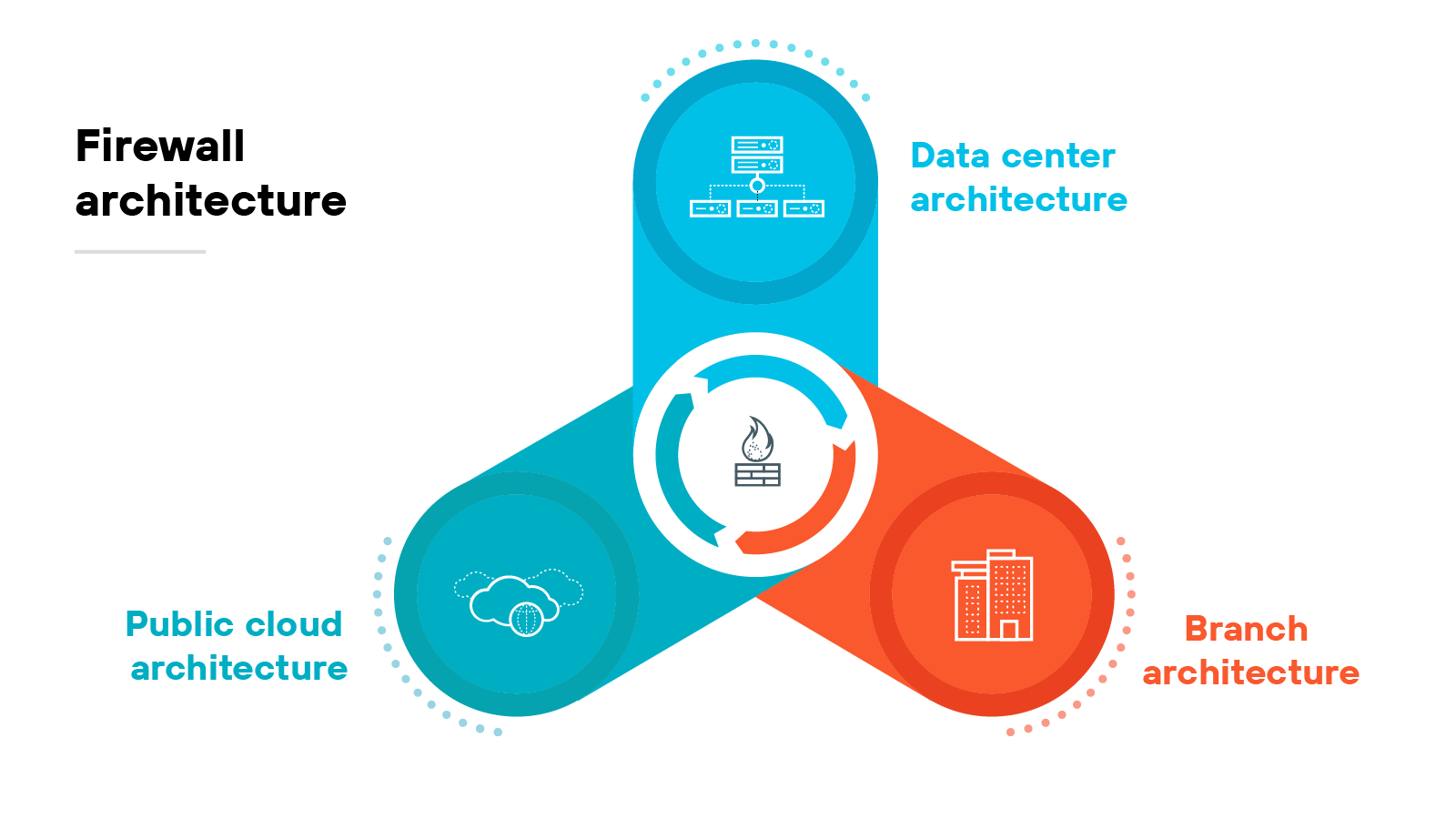
Firewall architecture refers to how firewalls are designed and deployed to protect applications, data, and network traffic.
The focus today is less about specific types and more about how firewall systems operate across different environments.
Modern architectures are shaped by where the firewall runs and what it protects.
Data center architecture
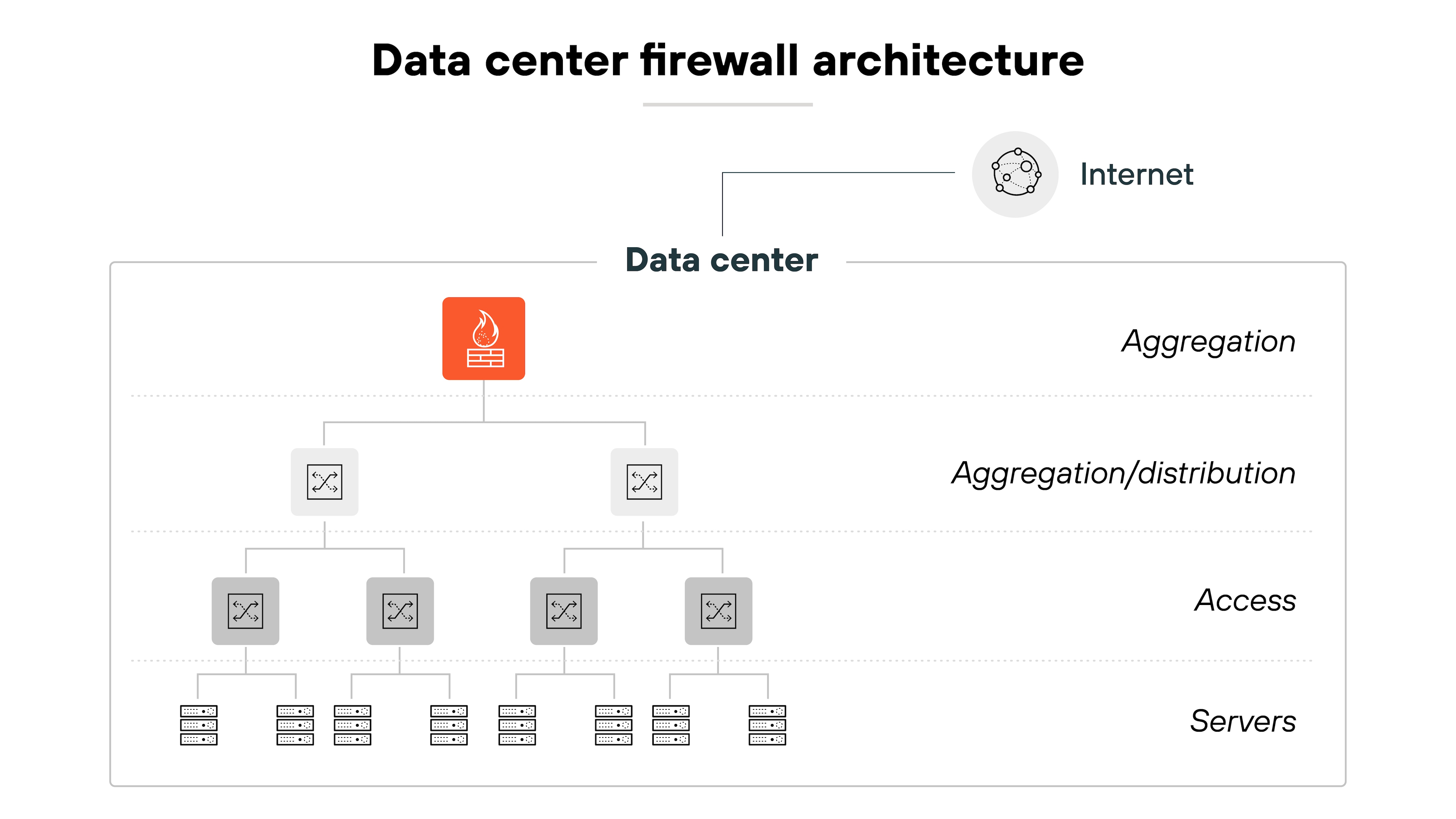
Firewalls in data centers are typically placed near workloads—often at the top of the rack. These devices need to support high throughput and low latency.
They also need strong security features. For example(s): Blocking malware and segmenting traffic between different server types.
Here’s why:
Not all servers face the same risks. Public-facing web servers need different protections than internal systems. And segmentation helps ensure each one gets the right level of control.
Public cloud architecture
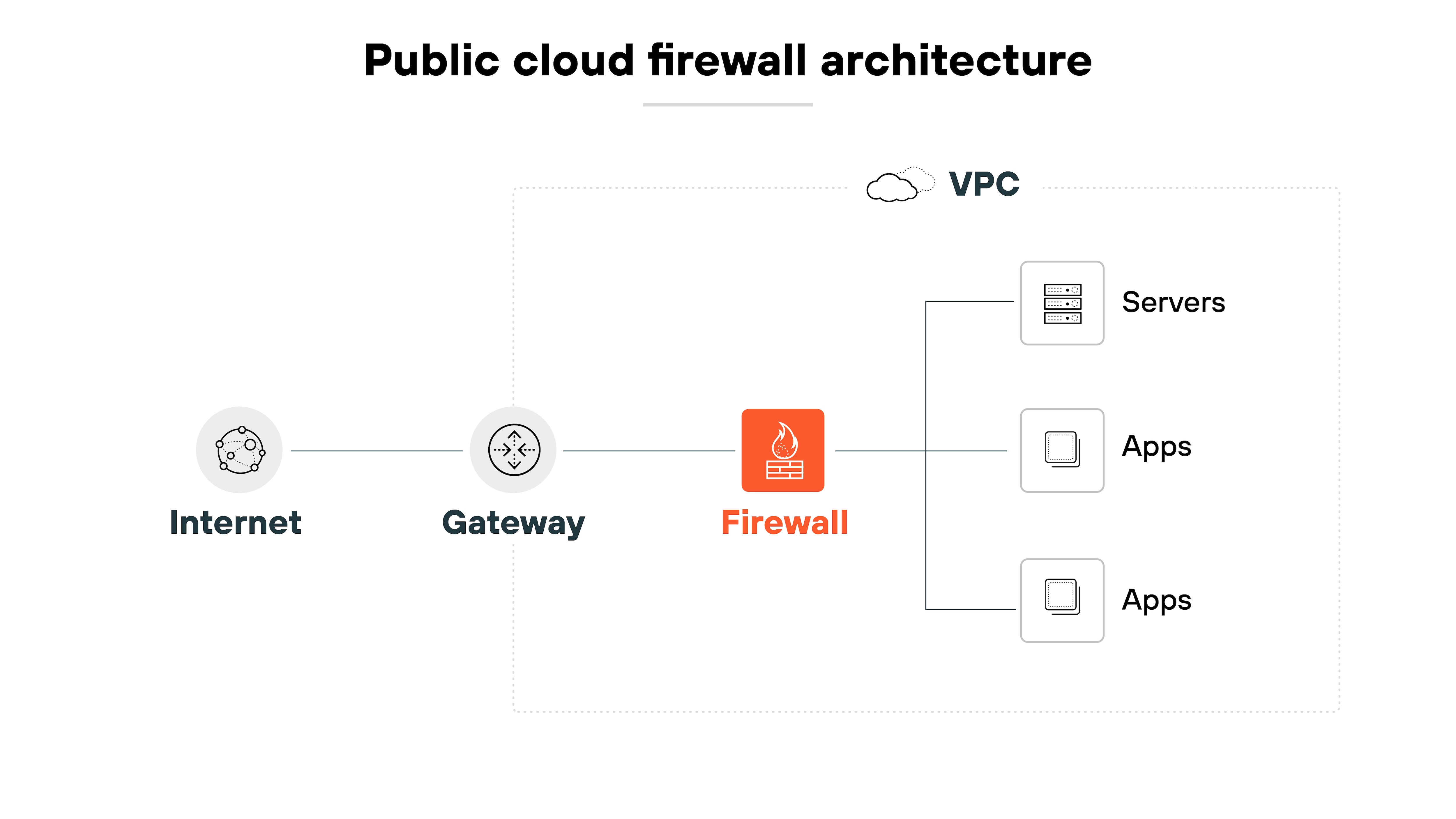
In cloud environments, firewall design has to support native cloud constructs. This includes integration with platform services and scalability.
Some firewalls now support containerized workloads. Others allow admins to define policies directly from cloud consoles.
The goal is the same: Apply consistent security while keeping operations manageable.
Branch architecture
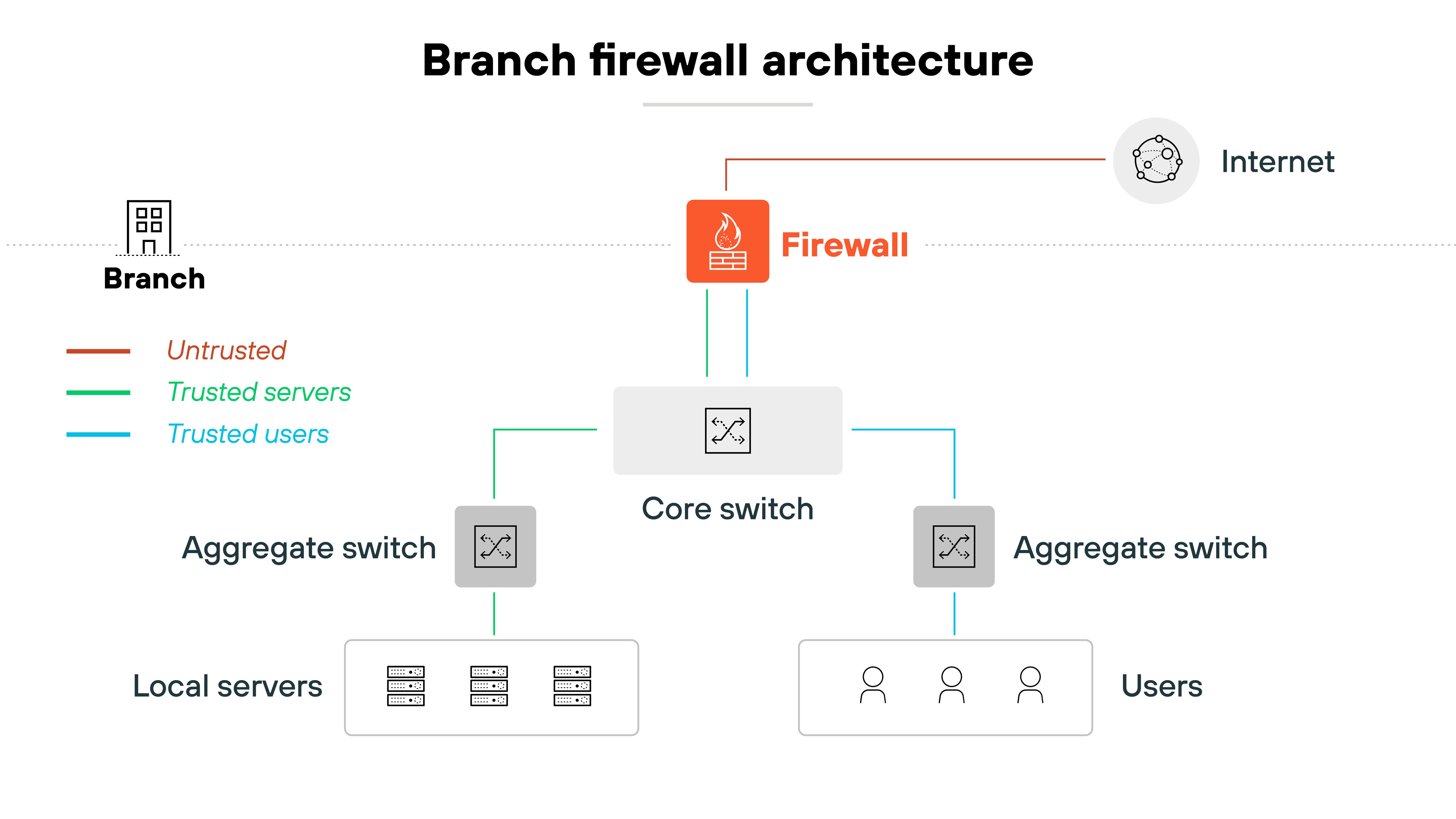
At branch locations, firewalls protect local users and systems from internet-based threats. Architecture here is more about positioning and control than physical layout.
That includes using identity- and application-based rules. And it may involve segmenting traffic into zones.
Modern branch firewalls must adapt to evolving user behavior and cloud connectivity. Visibility and control are both essential.
What are the different types of firewalls?
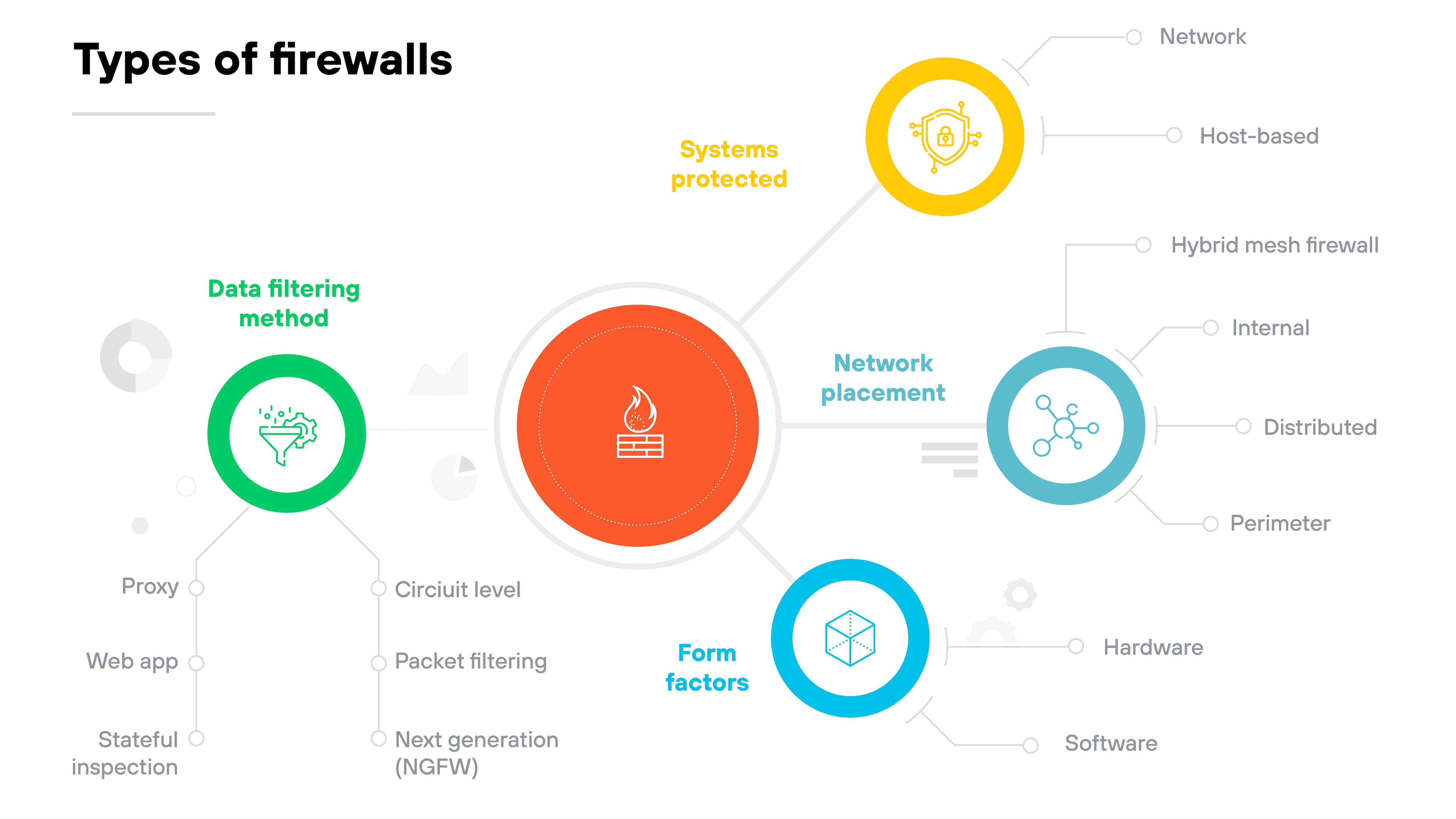
Not all firewalls work the same way. Some protect individual devices. Others monitor traffic for an entire network. Some are physical appliances. Others run in the cloud.
That’s why they’re generally categorized based on what they protect, how they’re deployed, where they sit in the network, or how they inspect traffic.
Below, we’ll break down the main types of firewalls across each of these categories:
Types of firewalls
| Category | Type | Description |
|---|---|---|
| Firewalls types by systems protected | Network firewall | Protects an entire network by inspecting incoming and outgoing traffic. |
| Host-based firewall | Installed on a specific device to monitor traffic to and from that host. | |
| Firewall types by form factors | Hardware firewall | A physical device placed between network elements and connected devices. |
| Software firewall | A software-based firewall deployed on servers or virtual machines. Includes container firewalls, virtual firewalls, and managed service firewalls. | |
| Firewall types by placement within infrastructure | Perimeter firewall | Placed at the edge of a network to manage traffic entering or leaving. |
| Internal firewall | Positioned within the network to monitor traffic between internal segments. | |
| Distributed firewall | A scalable approach where enforcement is applied across multiple devices. | |
| Hybrid mesh firewall | Firewalls deployed across on-premises and cloud environments in a coordinated, distributed architecture. | |
| Firewall types by data filtering method | Packet filtering firewall | Checks each packet against rule sets and allows or blocks based on criteria. |
| Stateful inspection firewall | Tracks the state of active connections to evaluate traffic in context. | |
| Circuit-level gateway | Verifies session-level connections before allowing ongoing communication. | |
| Proxy firewall | Intercepts and evaluates application-layer traffic between client and server. | |
| Next-generation firewall (NGFW) | Combines traditional firewall features with advanced capabilities like IPS and traffic decryption. | |
| Web application firewall | Filters HTTP traffic to and from web apps to block attacks like cross-site scripting or SQL injection. |
What are the features of a firewall?
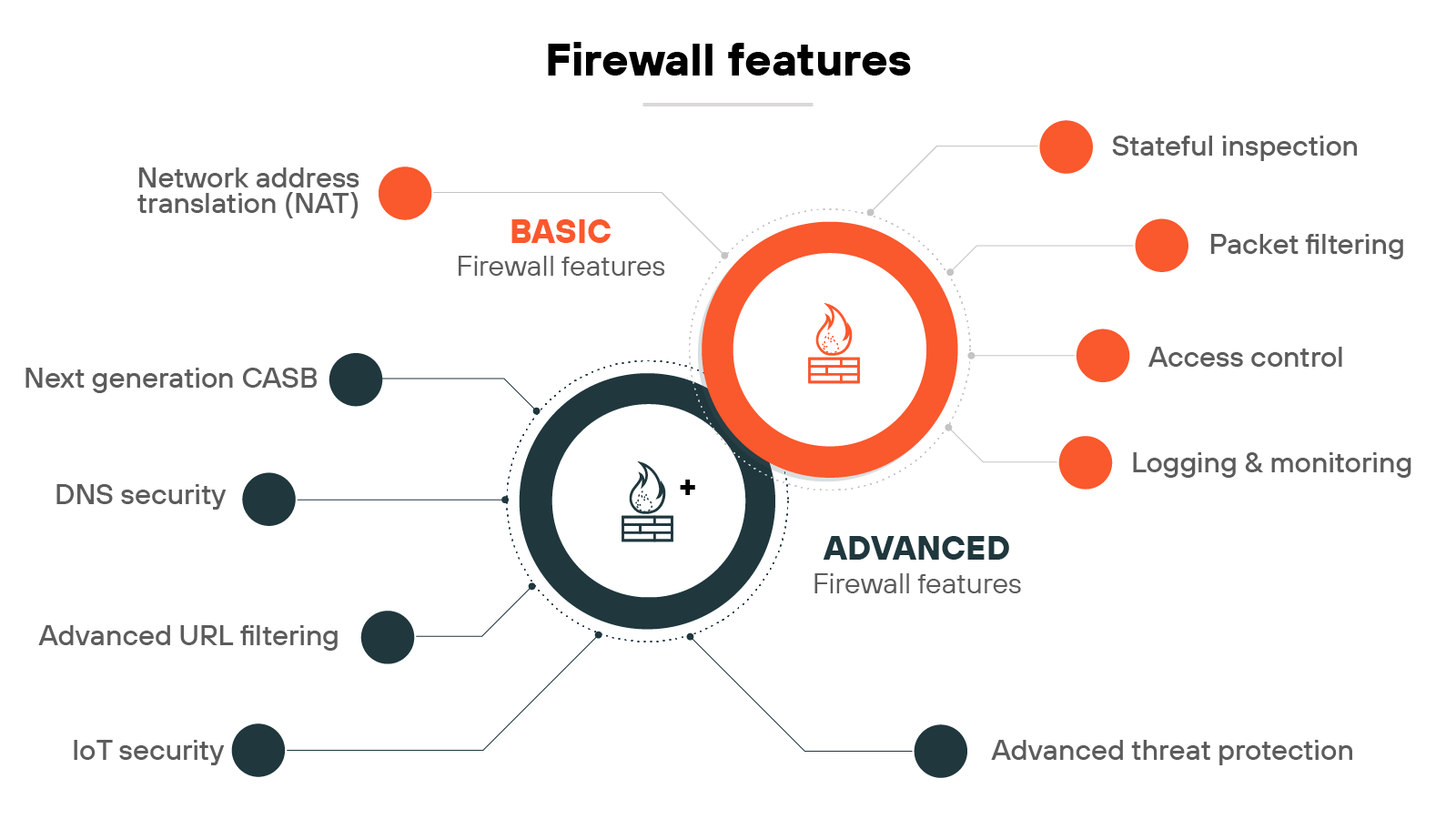
Firewalls have evolved. What started as basic traffic filtering has grown into a wide range of capabilities designed to meet different levels of risk.
Some features are foundational: packet filtering, logging, access control, etc.
Others are more advanced, using modern technologies like deep learning and automation to stop sophisticated threats in real time.
Let’s break down the primary firewall features into two categories—basic and advanced—and take a closer look at each:
Firewall features
| Category | Feature | Description |
|---|---|---|
| Basic | Packet filtering | Evaluates packets based on criteria like IP address or port to allow or block traffic. |
| Stateful inspection | Tracks the state of active connections to allow only legitimate traffic. | |
| Network Address Translation (NAT) | Modifies packet IP addresses to conserve addresses and hide internal network structure. | |
| Logging and monitoring | Records network activity for analysis and response to potential threats. | |
| Access control | Applies rules to regulate which users or systems can access network resources. | |
| Advanced | Advanced threat prevention | Uses deep learning to detect zero-day attacks and automate protection workflows. |
| Advanced URL filtering | Uses real-time deep learning to stop known and unknown web threats. | |
| DNS security | Applies ML and analytics to block advanced DNS-based attacks and reduce tool sprawl. | |
| IoT security | Segments and protects IoT devices using Zero Trust and contextual machine learning. | |
| Next-generation CASB | Secures SaaS apps in real time with deeper visibility and modern data protection. |
What are the benefits of a firewall?
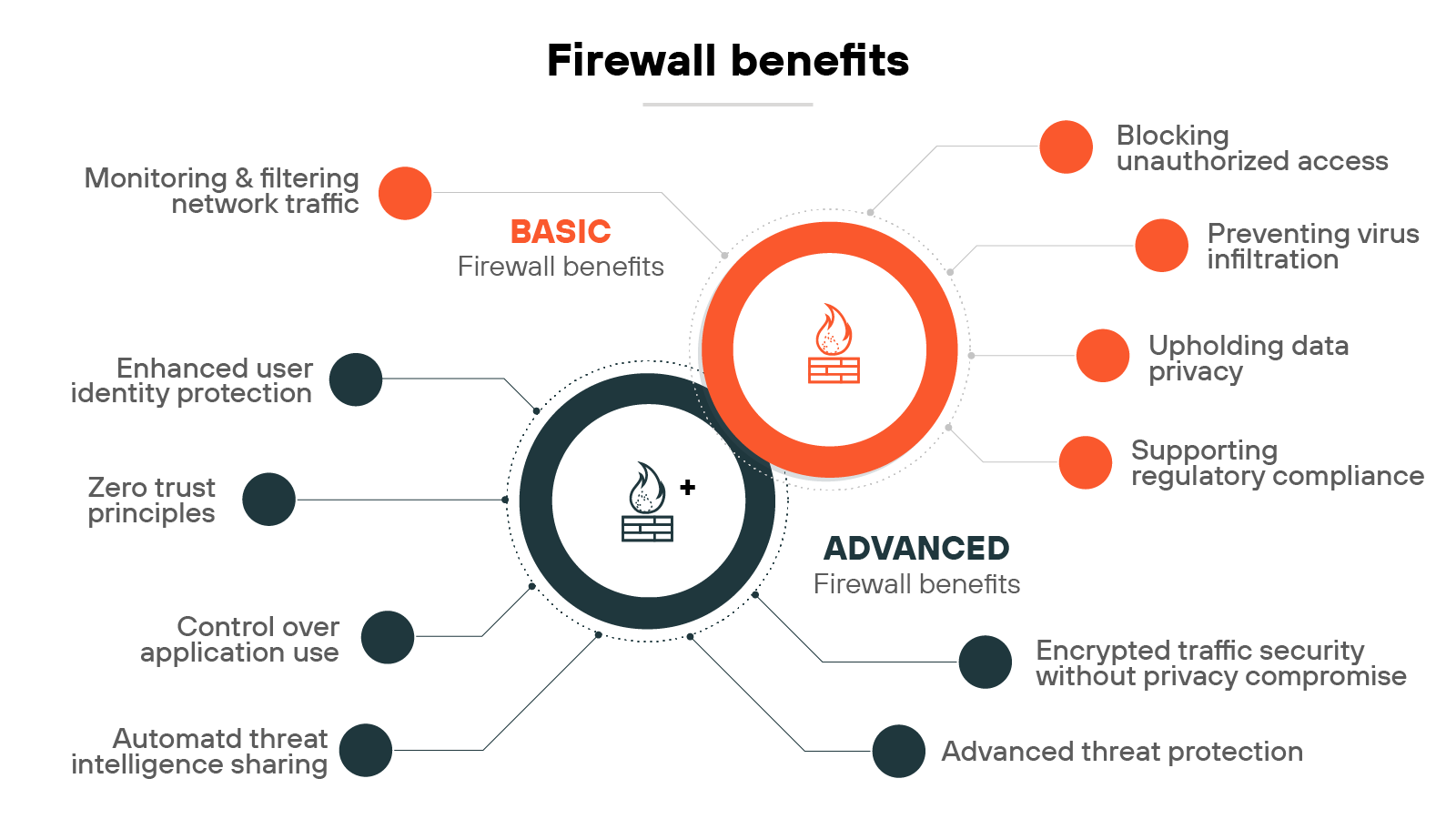
Firewalls help control traffic, reduce risk, and support compliance.
Some benefits are well established, like blocking malicious traffic, enforcing access controls, and maintaining data privacy.
Others reflect relatively newer capabilities: inspecting encrypted traffic, applying Zero Trust policies across the network, etc.
In other words:
The value of a firewall depends on what it can do and how it’s used.
Here, we’ll outline both basic and advanced firewall benefits:
Firewall benefits
| Category | Benefit | Description |
|---|---|---|
| Basic | Monitoring and filtering network traffic | Inspects data packets and blocks harmful patterns using stateful inspection. |
| Preventing virus infiltration | Blocks known virus patterns and supports antivirus tools. NGFWs improve detection of advanced threats. | |
| Blocking unauthorized access | Applies access controls to limit interactions to trusted sources only. | |
| Upholding data privacy | Prevents sensitive data exposure by monitoring inbound and outbound traffic. | |
| Supporting regulatory compliance | Logs and controls access to sensitive data to support audit readiness and compliance. | |
| Advanced | Enhanced user identity protection | Applies security policies based on user identity for more precise access control. |
| Control over application use | Identifies and restricts app usage to approved applications only. | |
| Encrypted traffic security without privacy compromise | Inspects encrypted traffic for threats while preserving user privacy. | |
| Advanced threat protection | Protects against known and emerging threats across multiple attack vectors. | |
| Automated threat intelligence sharing | Detects and responds to threats using shared global intelligence feeds. | |
| Zero Trust principles | Applies continuous authentication and verification to reduce implicit trust. |
The primary challenges commonly associated with firewalls include:
Selecting an appropriate firewall
Effective configuration
Regular updates
Managing rules and policies
Preventing false positives
Monitoring and alert management
Change management in dynamic environments
Robust patch management
Business logic translation to firewall rules
Layer 7 transition difficulty
Balancing security and performance
Managing firewalls isn’t just about deploying the right technology. It’s about keeping that technology aligned with changing environments, evolving threats, and organizational needs.
From choosing the right type of firewall to maintaining performance under load, each step comes with its own set of challenges.
Here are the key areas that can complicate firewall operations and where teams often face the most friction.
Selecting an appropriate firewall
As discussed, there are plenty of firewall types. Some are simple and packet-based. Others offer advanced threat detection and user-based policies.
Choosing the right one depends on what the organization needs to protect and how it operates. Most organizations use more than one type to balance coverage, cost, and performance.
Effective configuration
A firewall is only effective when configured properly. There’s no one-size-fits-all setup. Policies need to reflect specific requirements around segmentation, applications, and bandwidth.
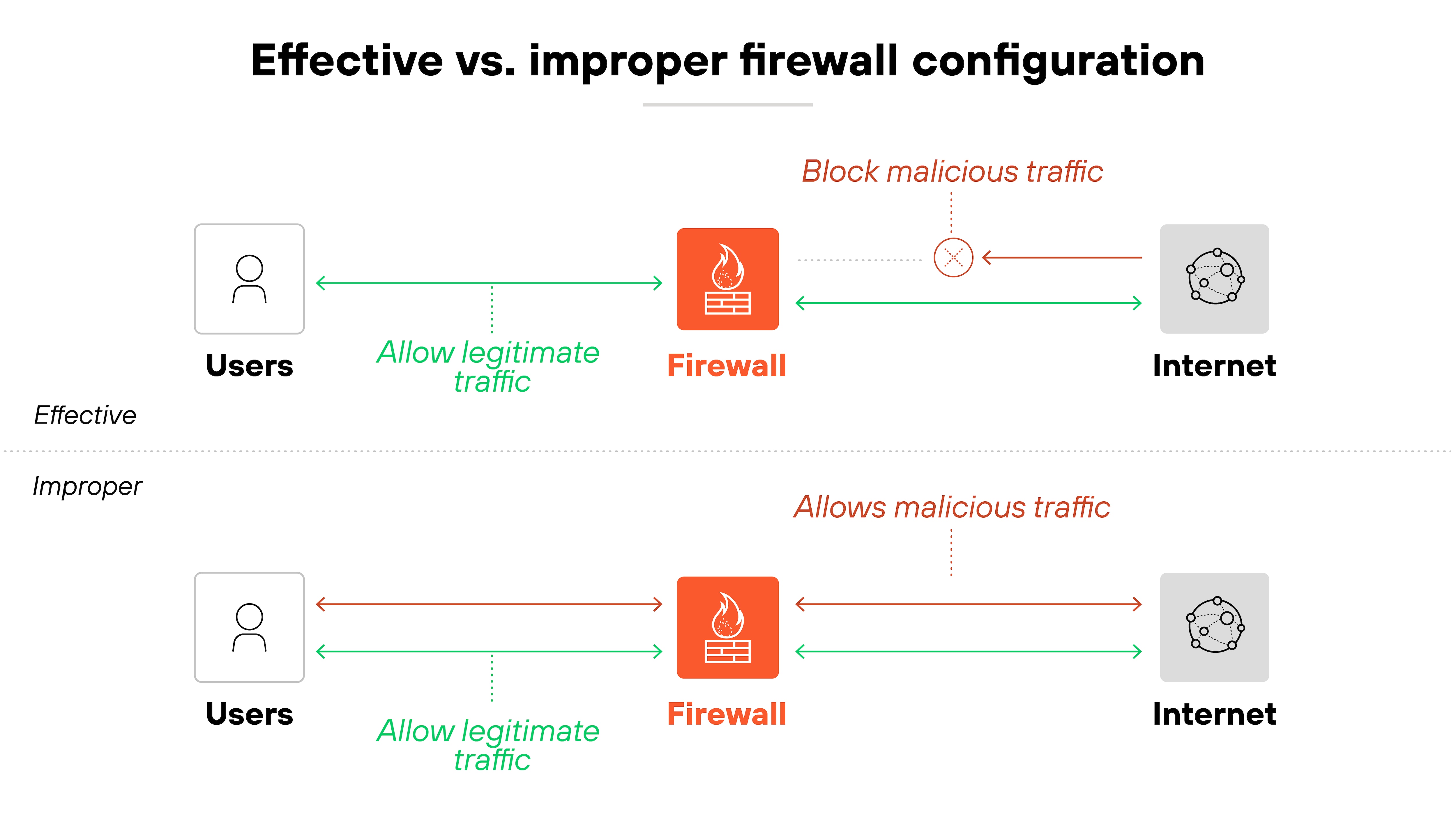
Unclear or broad rules can expose gaps or restrict legitimate access. Defining allowed services and applications upfront helps reduce these risks.
Regular updates
Firewalls have to be able to adapt to new threats. And that means regular software updates and threat signature updates are critical.
It’s worth noting, though, that updates can cause downtime or performance issues if not tested. So review the impact of each change before deploying it.
Management of rules and policies
Firewall rule sets can grow over time. New rules get added, but old ones often stay in place—even when they’re no longer needed.
Here’s the problem:
Too many overlapping or outdated rules can cause performance issues and make it harder to spot vulnerabilities.
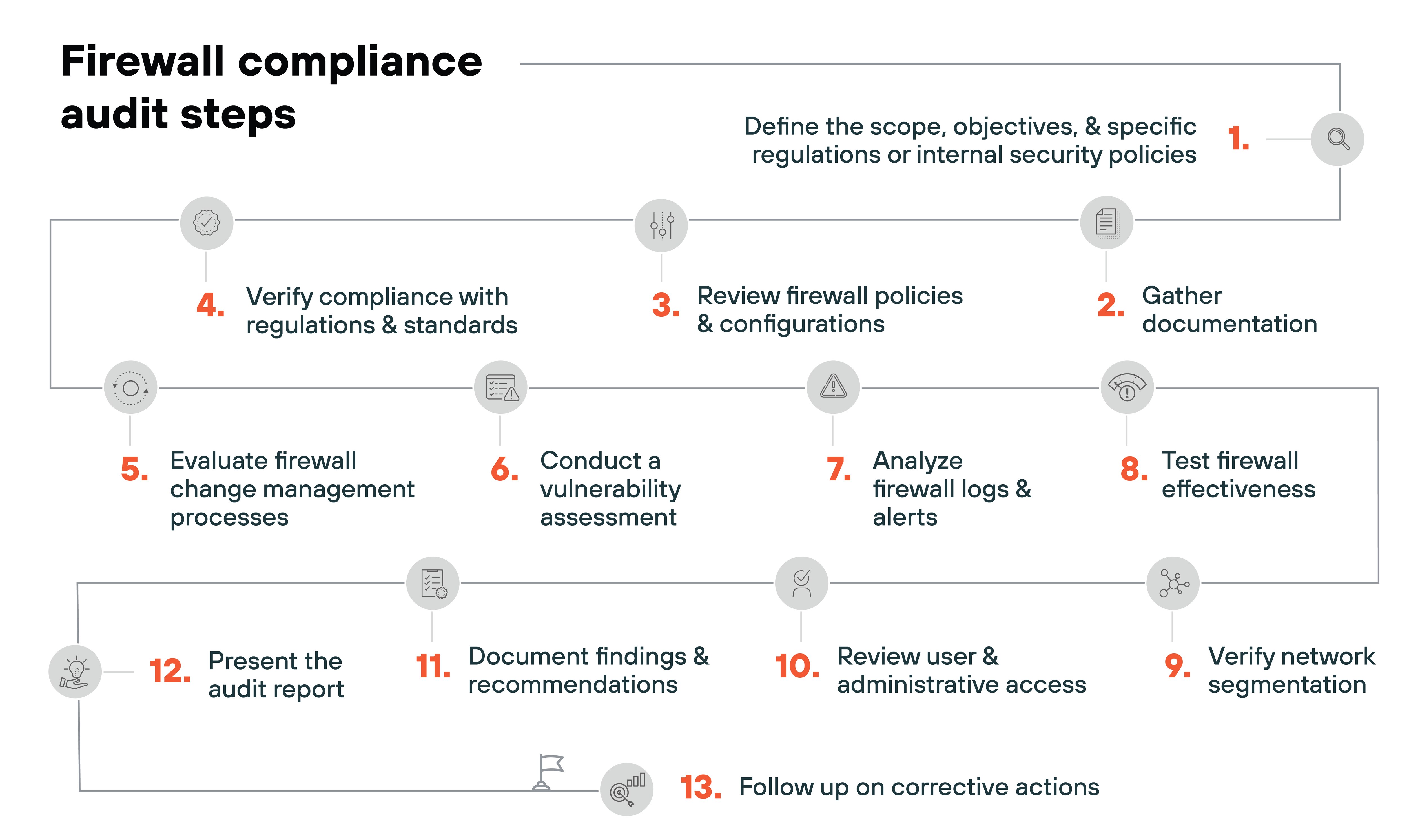
Regular audits help identify what to remove or optimize.
Preventing false positives
Strict policies are good in theory. But they can block legitimate activity if they’re too aggressive.
This causes frustration for users. It also creates more work for IT teams.
The solution?
Tuning rules to reflect known traffic behavior.
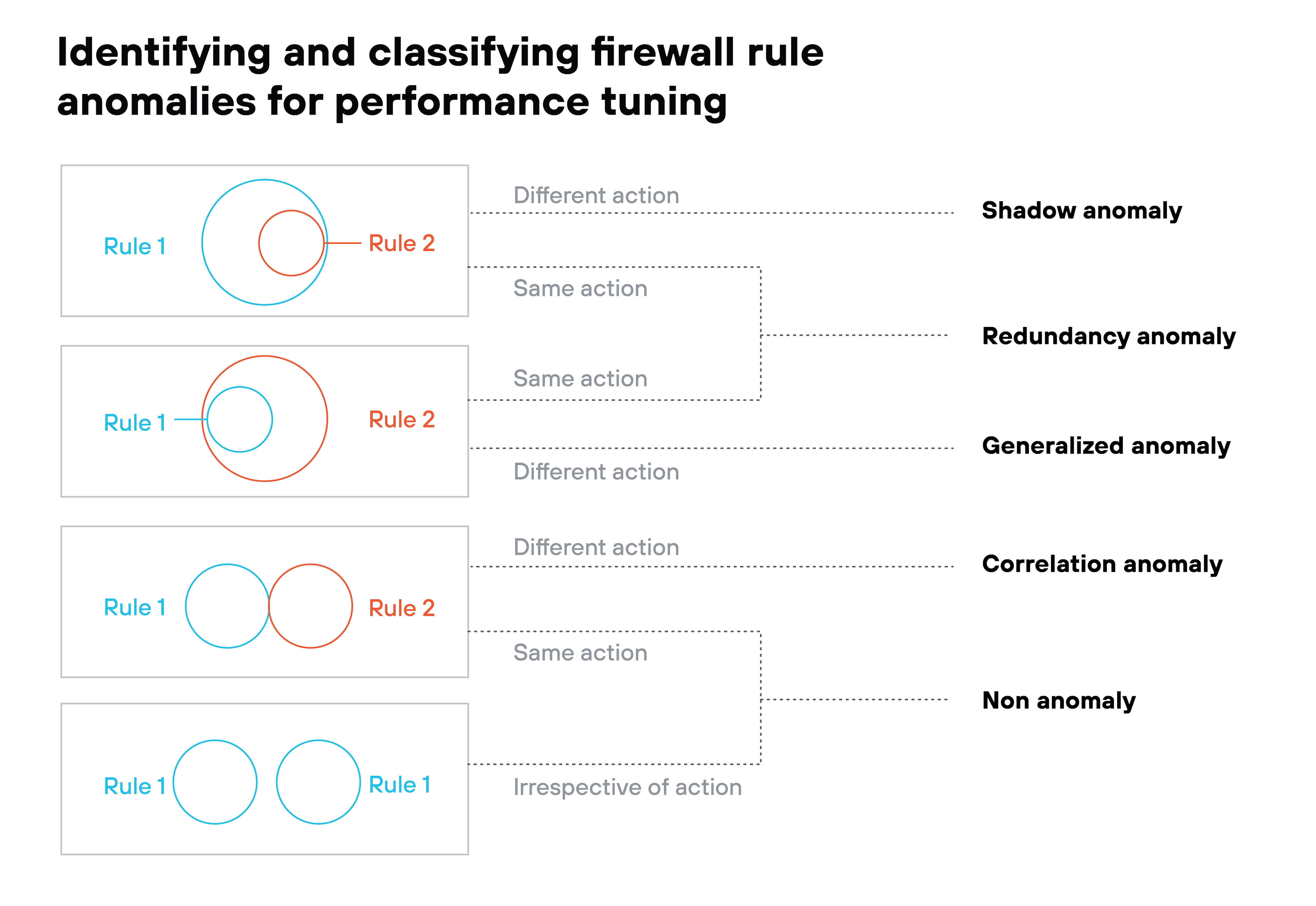
Over time, this reduces false positives while maintaining strong security.
Monitoring and alert management
Firewalls need ongoing monitoring. Metrics like CPU load, session count, or failover events help identify issues early.
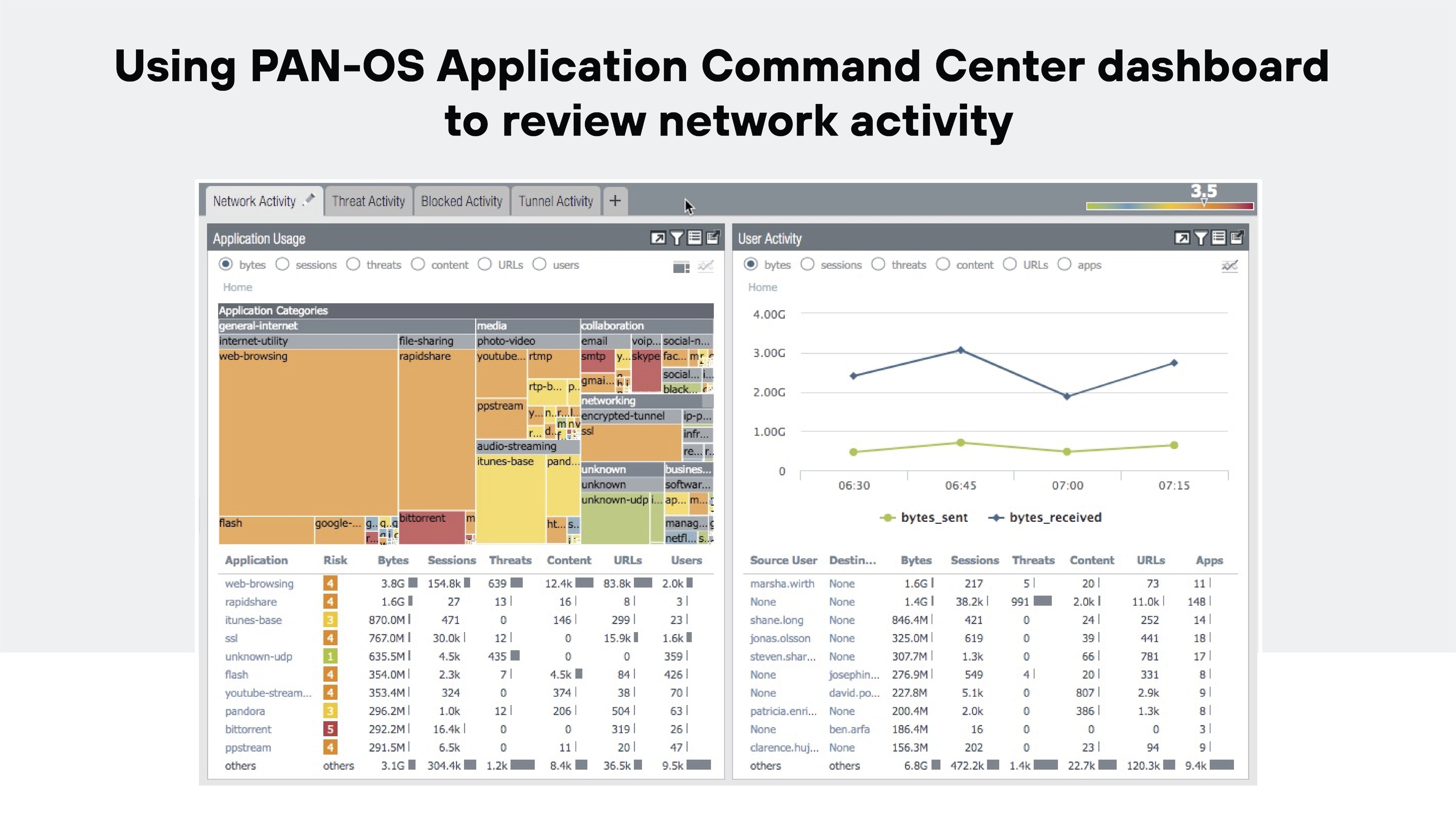
For example: Unusual failover activity could signal hardware problems or bugs that need investigation before they affect availability.
Change management in dynamic environments
Networks change constantly. New systems, apps, or users mean firewall rules need to change too.
The challenge is timing.
Some changes require trial and error. Documentation might not clearly explain which ports or protocols are in use. So admins need to be ready to troubleshoot.
Robust patch management
All systems have vulnerabilities. Firewalls are no exception.
It’s important to have a formal patching process for security devices. This includes monitoring vendor updates, applying patches promptly, and tracking which devices are affected.
Business logic translation to firewall rules
Security policies often come from business leaders. But translating those high-level goals into technical firewall rules can be difficult.
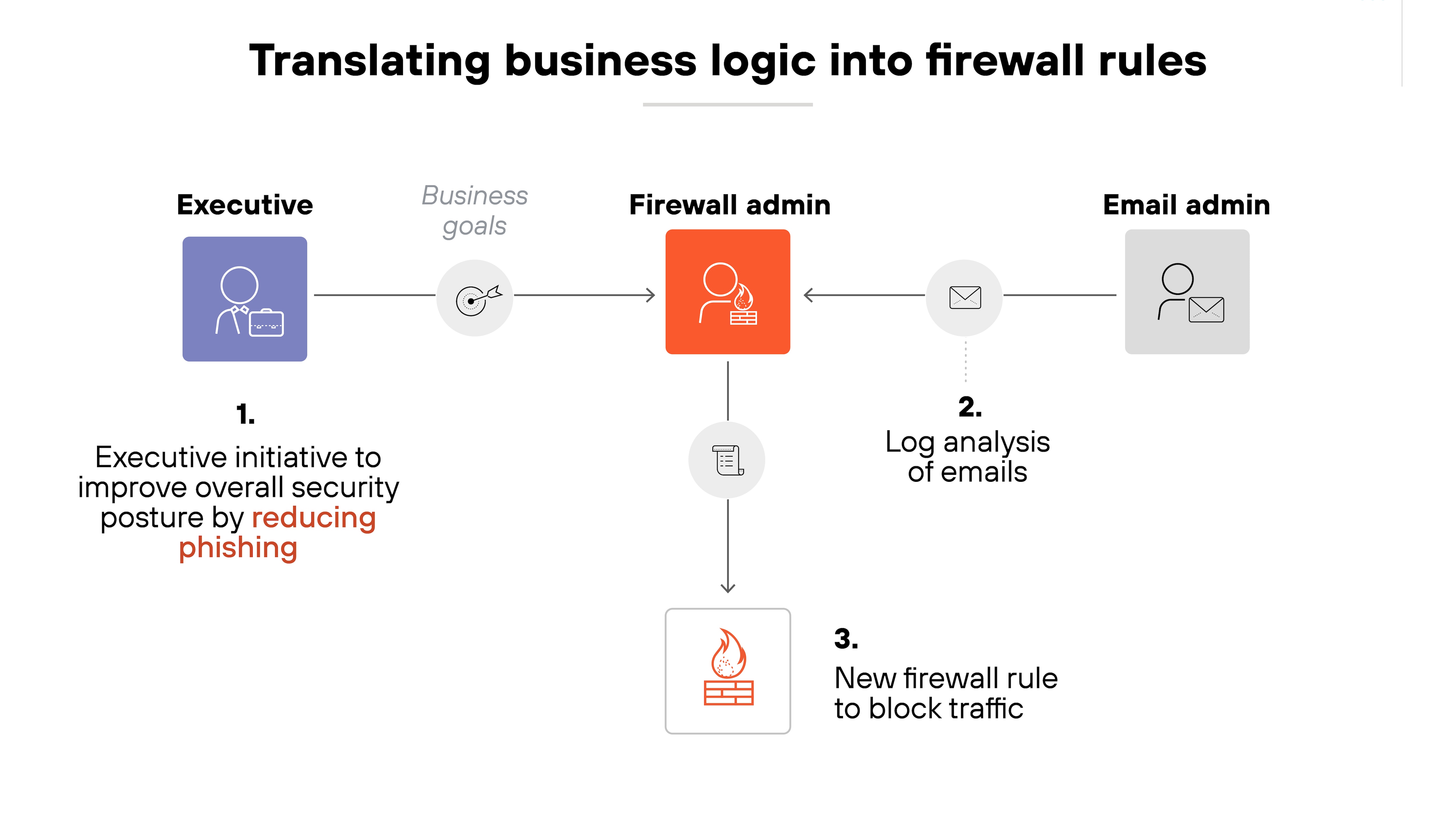
Why?
Some firewall platforms don’t support business logic directly or intuitively. That can lead to inefficient or overly complex rule sets.
Layer 7 transition difficulty
Some organizations do still rely on older Layer 3 and Layer 4 firewalls. And transitioning to a Layer 7 system can be hard—especially when legacy rules are involved.
This shift requires rethinking how policies are structured. It also requires time to test and validate the new approach.
Balancing security and performance
Firewalls inspect large volumes of traffic. That inspection can slow things down—especially if too many features are enabled at once.
There’s always a tradeoff. Stronger inspection might reduce throughput.
Modern tools like AIOps can help. They use predictive analytics to identify when firewalls are nearing capacity and suggest changes before performance becomes a problem.
- How to Troubleshoot a Firewall | Firewall Issues & Solutions
- What Is Firewall Management? | A Comprehensive Guide
What are the main firewall threats and vulnerabilities?
The main firewall threats and vulnerabilities encompass but aren’t limited to:
Misconfiguration
Outdated software
Inactive security features
Insufficient documentation
Internal threats
Weak password protocols
Basic inspection protocols
Over-reliance on firewalls
Evolving threat landscape
Advanced attacks on machine learning
Firewalls play a key role in protecting networks, but they’re not immune to risk. Like any security tool, their effectiveness depends on how they’re deployed, maintained, and monitored.
Missteps—whether technical, procedural, or strategic—can create vulnerabilities that attackers exploit.
Below are the most common threats and vulnerabilities that can weaken firewall defenses and introduce gaps in overall security posture.
Misconfiguration
Firewalls are only as effective as their configurations. Mistakes during setup can leave gaps. Default settings are a common risk.
Attackers often look for devices running with unchanged defaults.
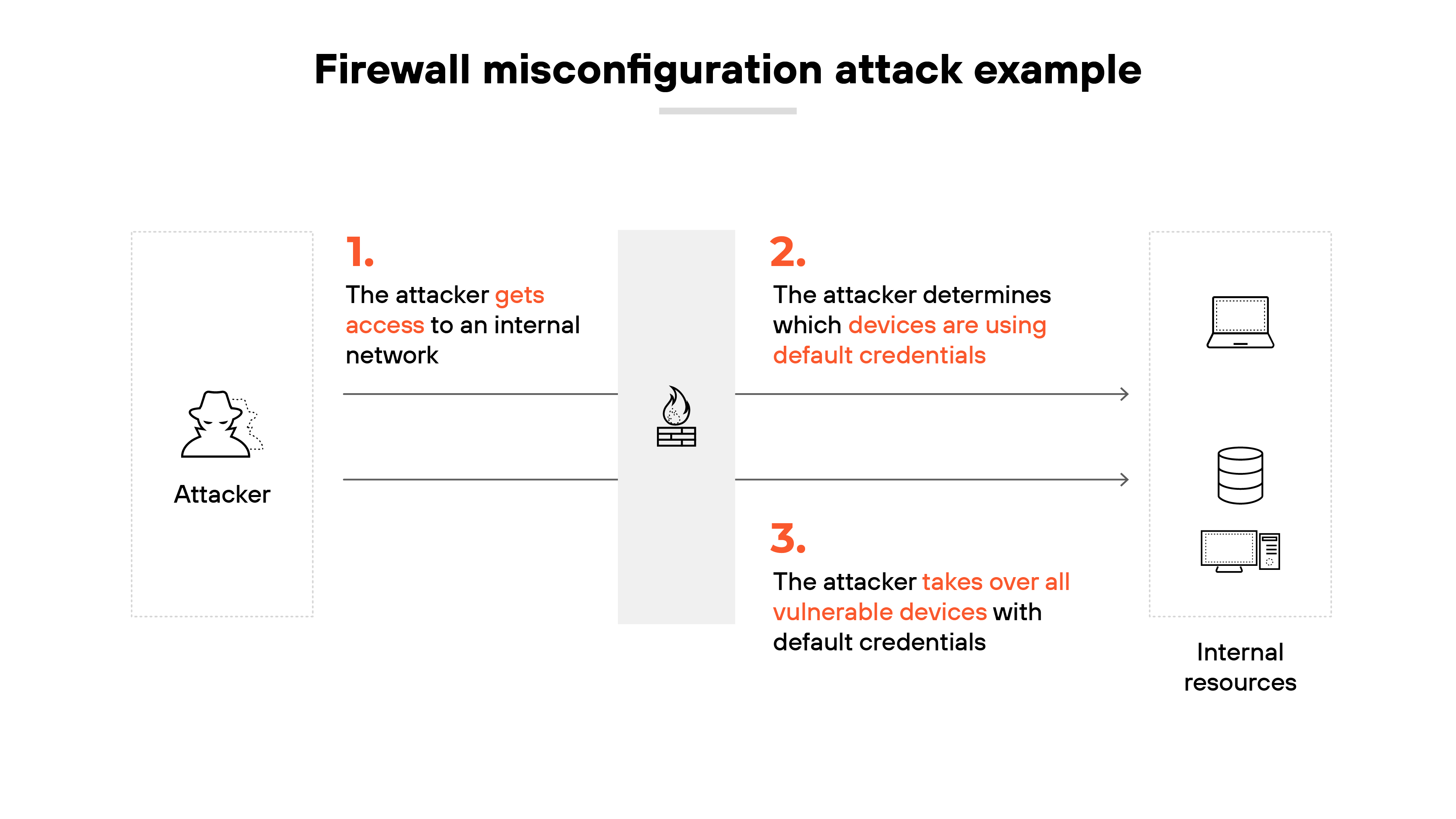
Regular reviews help close these gaps and strengthen security.
Outdated software
Firewall software needs updates. Vendors release patches to fix known bugs and close security holes.
Running an outdated version increases the risk of exploitation. It can also create compatibility issues with other systems.
Keeping software current is part of basic network security hygiene.
Inactive security features
Many firewalls ship with advanced capabilities. But some of those features are off by default.
Anti-spoofing tools are one example. If they’re not enabled, the firewall won’t block traffic from falsified sources.
System audits can help verify that important features are active.
Insufficient documentation
Firewall admins need clear documentation. That includes configuration settings, rule sets, and change history.
Without it, teams may miss important details—especially during handoffs or staffing changes. Poor documentation also makes it harder to audit or troubleshoot later.
Internal threats
Firewalls focus on external traffic. But insider threats still matter.
Employees with system access might bypass firewall protections.
Reviewing user access levels and monitoring internal traffic helps limit that risk.
Weak password protocols
Weak or reused passwords can undermine the entire system.
Some firewalls still ship with default credentials. Others allow simple passwords.
Enforcing strong password policies and regular changes is essential for basic access control.
Basic inspection protocols
Older firewalls inspect traffic based on source, destination, and port. But that’s not enough against modern threats.
Attackers use spoofing or encrypted payloads to bypass shallow inspection.
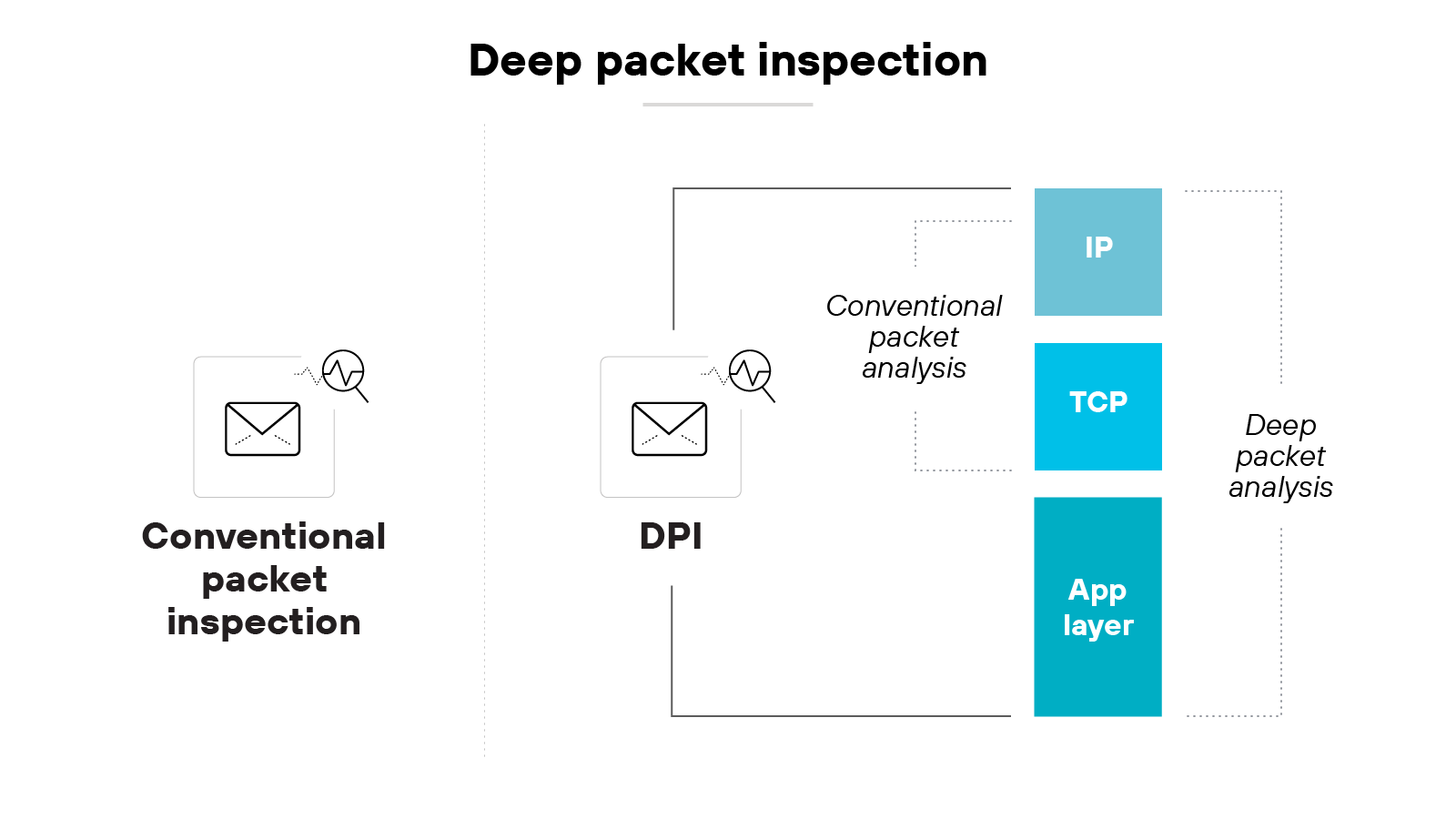
Deep packet inspection (DPI) gives a clearer view into actual content.
Over-reliance on firewalls
Firewalls are important—but they’re not enough on their own. A strong security posture uses multiple layers.
That includes endpoint protection, network monitoring, and incident response. Relying only on a firewall leaves other gaps exposed.
Evolving threat landscape
New threats emerge constantly. And traditional firewalls often rely on known signatures.
But attackers now use polymorphic code and zero-day techniques. Defenses need to evolve to keep pace with threats that don’t match existing patterns.
Advanced attacks and machine learning
Attackers are using machine learning to improve their techniques. These threats can adapt faster than signature-based tools can respond.
Like fileless malware, for instance:
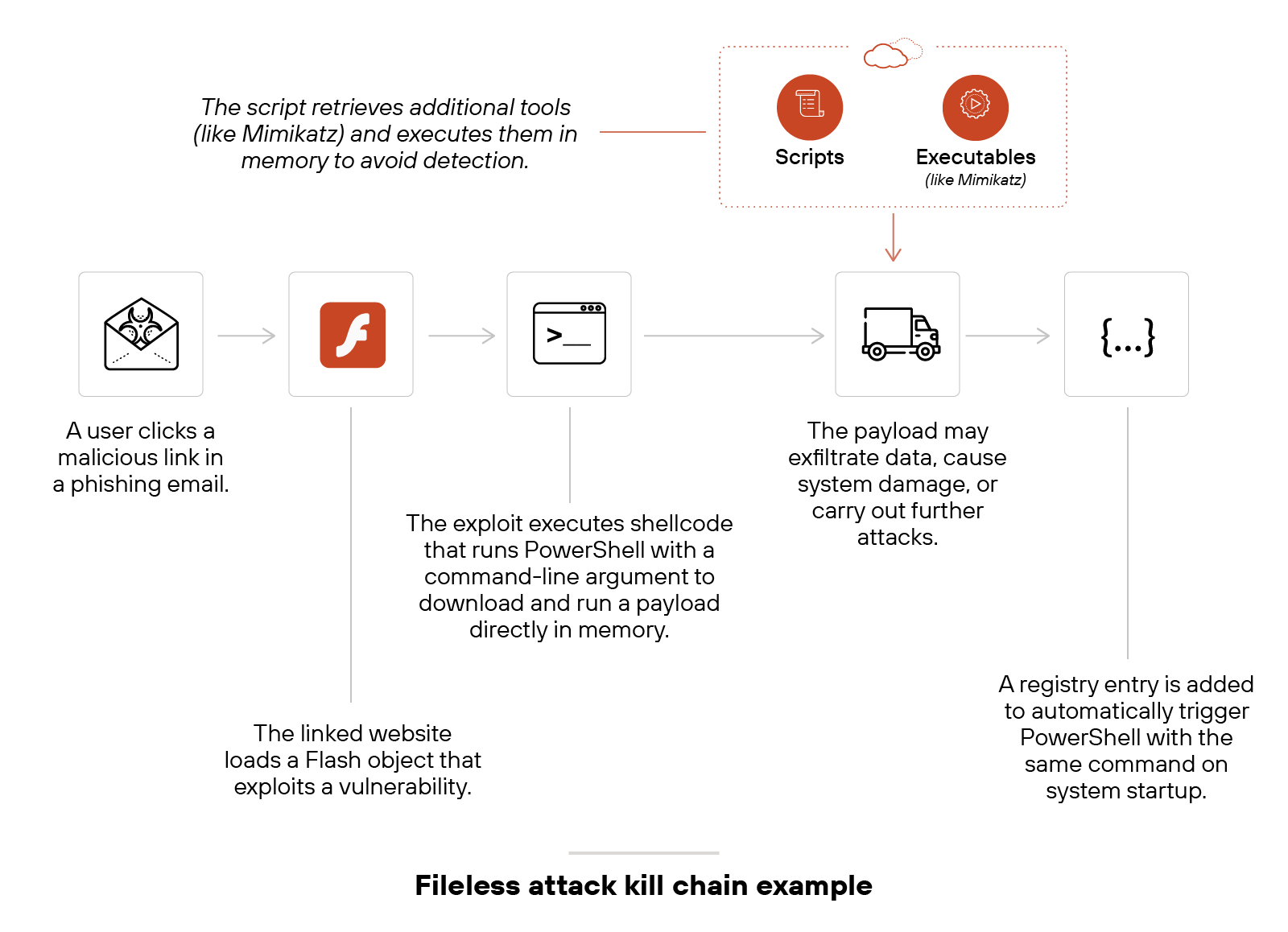
To keep up, firewalls need more proactive detection—like behavior analysis and anomaly detection—built into the core platform.
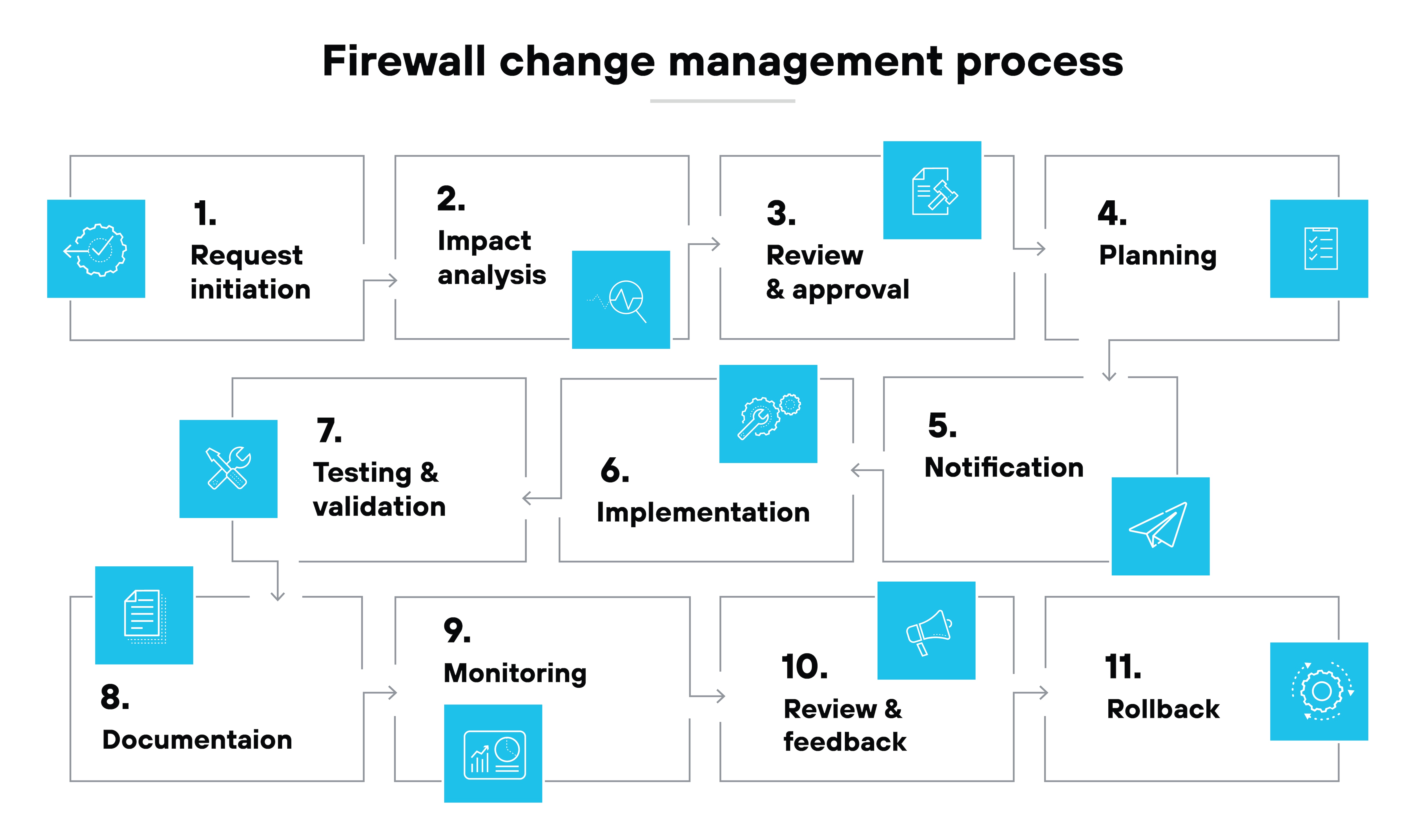
How to configure a firewall in 6 steps
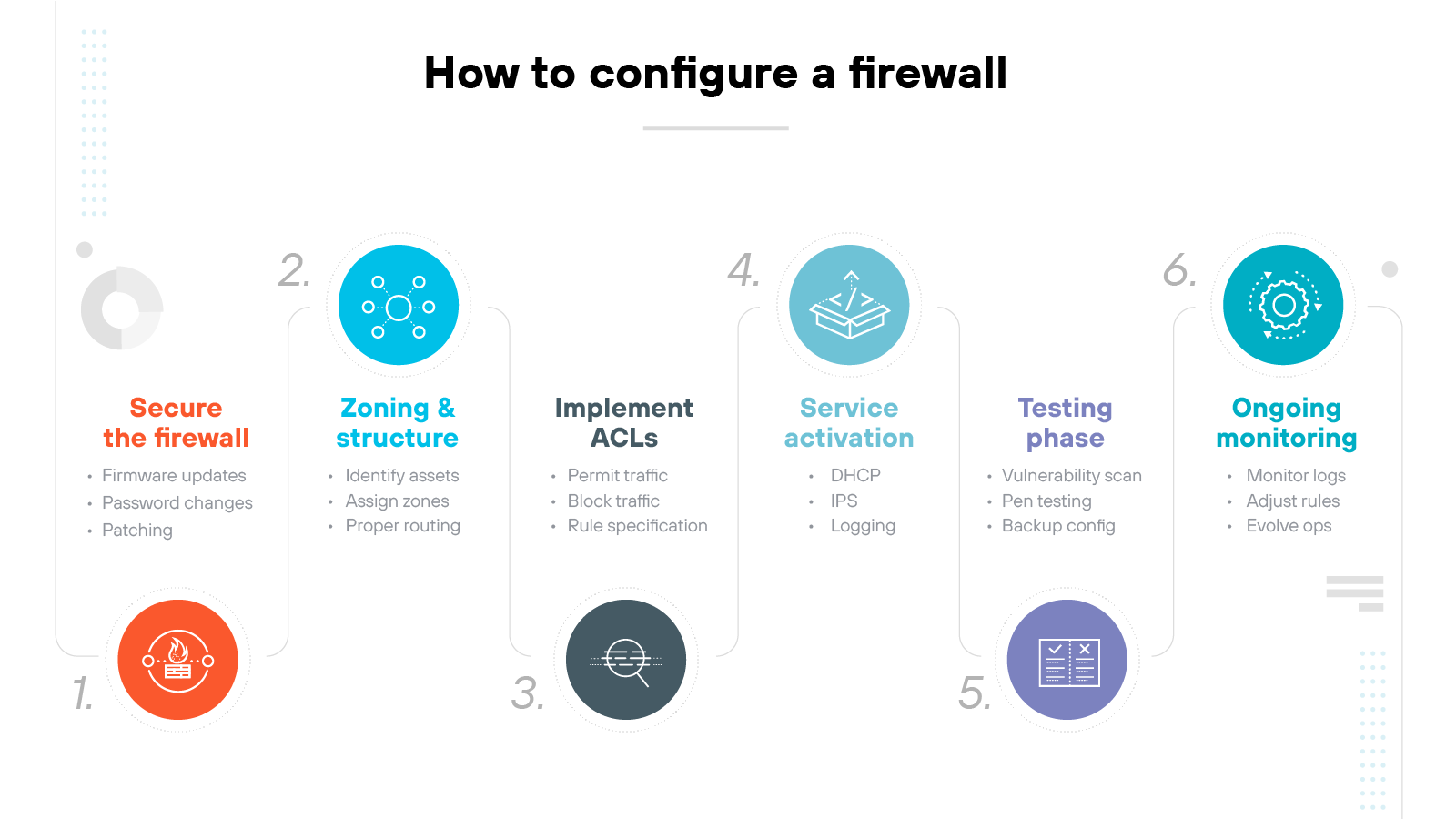
Firewall configuration is the process of setting specific rules and policies that govern how to monitor and control incoming and outbound traffic.
Firewall configuration steps include:
Securing the firewall
Designing firewall zones and IP address structure
Implementing access control lists (ACLs)
Activating additional services and logging
Testing the configuration
Ongoing monitoring and management
Remember: A firewall is only as effective as how it’s configured and maintained.
Step 1: Secure the firewall
Start by updating the firmware. This applies recent patches and reduces the risk of known exploits.
Remove or disable default accounts.
Change default passwords.
Restrict administrative access to specific systems and users.
Step 2: Design firewall zones and IP address structure
Group network assets based on role and risk level. For example: Public-facing servers should be placed in a DMZ.
Assign each zone to an interface. This ensures clear boundaries and proper routing between zones.
Step 3: Implement access control lists (ACLs)
Define what traffic is allowed between zones. Use specific source and destination IPs and ports.
Important: End each ACL with a default “deny all” rule. This blocks traffic that hasn’t been explicitly approved.
Step 4: Activate additional services and logging
Enable only the services that are needed—such as DHCP or intrusion prevention.
Set up logging. Logs should be sent to a centralized system for review and analysis. They help with monitoring and troubleshooting.
Step 5: Test the configuration
Use vulnerability scanners or penetration testing tools to validate the firewall. This confirms that blocked traffic stays out and legitimate traffic flows as expected.
Backup the configuration once it’s verified. This allows fast recovery if needed.
Step 6: Ongoing monitoring and management
Review logs and alerts regularly. Adjust policies when threats change or the network is updated.
Also, track firewall health. Metrics like CPU and memory usage help detect early signs of performance issues.
FYI: Tools like AIOps can help. They identify configuration drift and performance trends. Plus, they also provide guidance on maintaining alignment with security best practices.
Top 10 firewall best practices
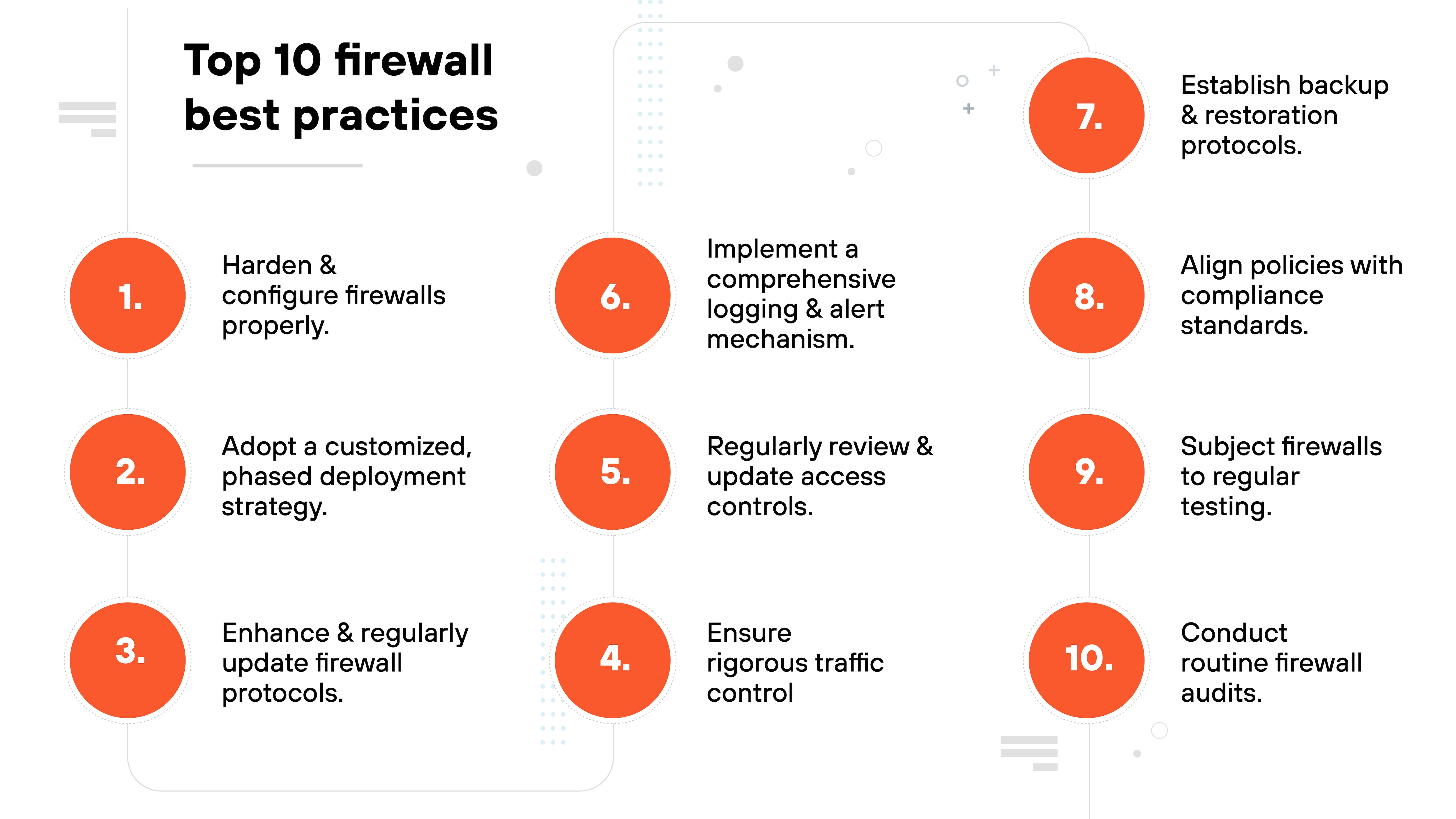
The top firewall best practices include:
Harden and configure firewalls properly.
Adopt a customized, phased deployment strategy.
Enhance and regularly update firewall protocols.
Ensure rigorous traffic control
Regularly review and update access controls.
Implement a comprehensive logging and alert mechanism.
Establish backup and restoration protocols.
Align policies with compliance standards.
Subject firewalls to regular testing.
Conduct routine firewall audits.
Firewall effectiveness depends on more than just installation.
It requires secure setup, continuous testing, and proactive management.
These best practices help reduce risk while keeping your configuration aligned with real-world needs.
1. Harden and configure firewalls properly
Start by hardening the operating system. This includes disabling unnecessary services and applying vendor patches.
Important: Firewalls protecting internet-facing services, like web servers, need extra scrutiny. Configuration mistakes here are common entry points.
After deployment, configuration is ongoing. Regularly review rules and settings to reflect changes in risk, usage, or business needs.
2. Adopt a customized, phased deployment strategy
Deployment should match the environment. That includes understanding Layer 2 and Layer 3 network design and assigning zones accordingly.
Here’s why:
A sudden rollout can disrupt access. But a phased approach reduces risk and allows testing along the way.
3. Enhance and regularly update firewall protocols
Disable legacy protocols like Telnet or unsecured SNMP. Use modern alternatives where possible.
But it’s not just technical. Admins should stay active in cybersecurity communities.
New vulnerabilities and patches come fast. Relying on automation is not enough.
4. Ensure rigorous traffic control
Use default deny rules. Only allow traffic that’s explicitly needed.
Classify traffic into categories—internal, external, or partner—and apply rules based on trust and function.
Then monitor for unexpected flows or access attempts.
5. Regularly review and update access controls
Only the right users should have admin access.
Review access lists often.
Remove unused accounts and update permissions when roles change.
The goal is balance:
Enough access for teams to function. But not so much that risk increases.
6. Implement a comprehensive logging and alert mechanism
Enable detailed logging for all inbound and outbound traffic.
Send logs to a central system for review.
Use real-time alerts to detect anomalies—logging isn’t enough on its own.
Then follow up with regular reviews to identify patterns and fine-tune rules.
7. Establish backup and restoration policies
Backups should include rules, configurations, and policy settings. They also need to be tested.
If a firewall fails or is misconfigured, you need a fast way to restore functionality. So test the process before it’s needed.
8. Align policies with compliance standards
Firewall settings should meet industry regulations. But they should also go beyond basic checklists.
Compliance evolves. Your policy reviews should evolve too. Keep up with regulatory changes and map your configurations to them regularly.
9. Subject firewalls to regular testing
Use tools like path analysis to confirm rules behave as expected. Then go further.
Run penetration tests to simulate attacks. This helps validate how the firewall performs under pressure—and where it can improve.
10. Conduct routine firewall audits
Schedule routine audits for software versions, log integrity, and rule accuracy. Document all policy changes.
Important: Audits aren’t just for compliance. They also make sure internal changes don’t introduce new risks.
Comparing firewalls with other network security technologies
Firewall vs. antivirus
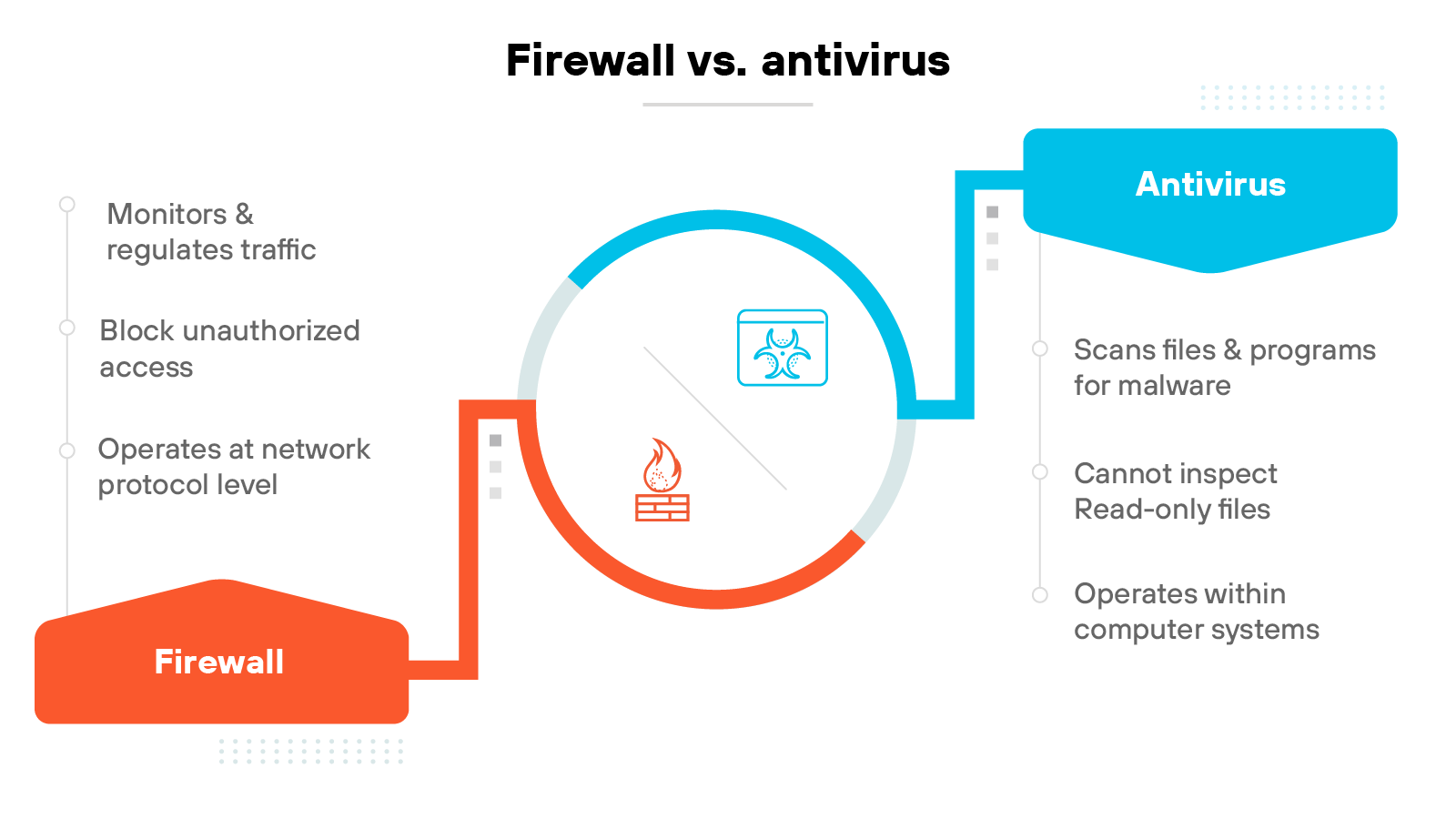
Firewalls and antivirus software serve different purposes. Firewalls focus on controlling traffic that enters or leaves a network. Antivirus tools focus on detecting and removing threats that already exist on a system.
So essentially: Firewalls protect at the network level. Antivirus protects at the device level.
Antivirus software scans files and programs for malware—like viruses, trojans, or worms. It removes or quarantines anything suspicious. Some antivirus tools have limitations, such as not inspecting read-only files.
It’s worth noting—these tools work best together. A firewall helps stop threats before they reach endpoints. Antivirus helps remove anything that gets through.
Firewall vs. IDS
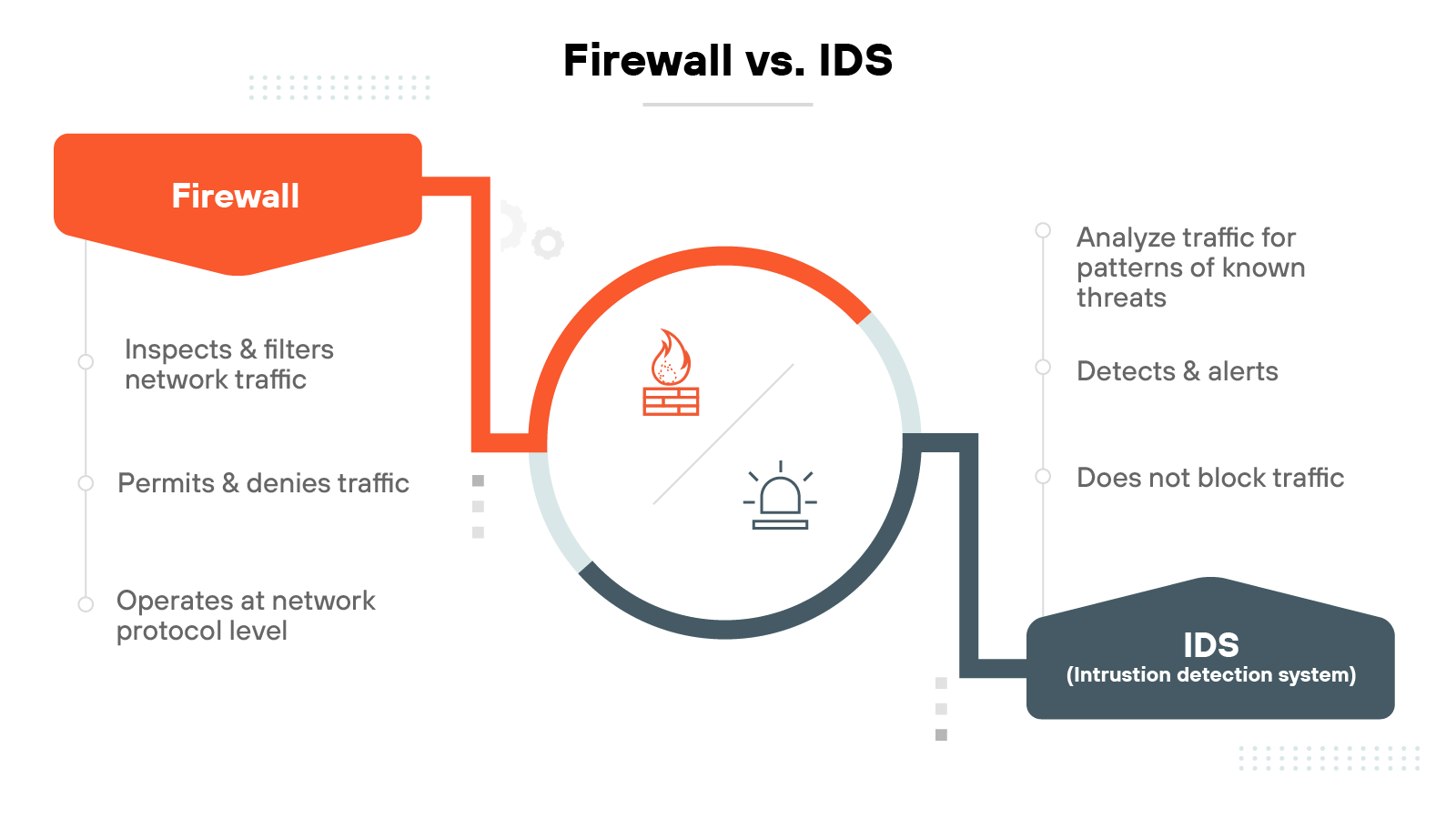
Firewalls and intrusion detection systems (IDS) also serve different roles. A firewall controls traffic based on defined policies. An IDS monitors traffic for signs of malicious behavior.
Here’s the key difference:
Firewalls act. IDSs observe.
A firewall enforces rules in real time.
An IDS, on the other hand, inspects traffic for threat patterns but doesn’t block it. It generates alerts when something suspicious is found.
In many environments, these tools are used together. Some modern network security systems combine detection and enforcement into one solution.
What is the history of firewalls?
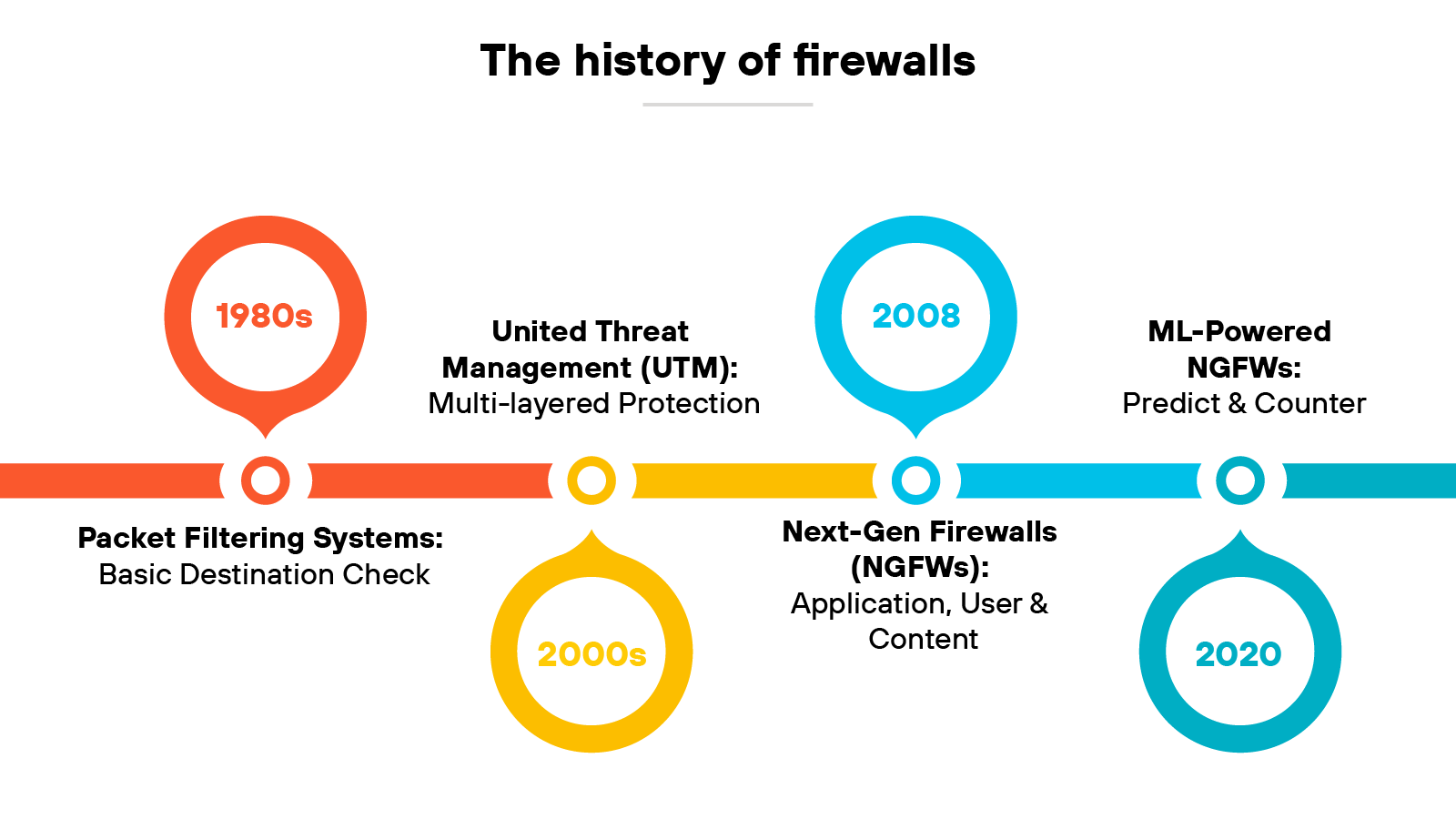
The earliest firewalls appeared in the late 1980s.
Packet filtering firewalls evaluated network traffic based on destination address, protocol, and port. If a packet didn’t match the rules, it was blocked or dropped.
Later, stateful firewalls added session awareness. Which means they could track the state of each network connection and evaluate whether incoming packets were part of an ongoing session or a new one. This made filtering way more accurate and easier to manage.
In the early 2000s, vendors introduced unified threat management (UTM) devices.
These platforms combined multiple security functions—like firewalling, antivirus, and intrusion prevention systems—into a single ecosystem. While UTMs simplified deployment, many struggled with integration and performance under load.
In 2008, Palo Alto Networks introduced a new kind of firewall technology: next-generation firewalls (NGFWs), which emphasized deeper visibility and control.
There was a shift toward inspecting traffic based on application, user identity, and content. NGFWs also included features like intrusion prevention and SSL decryption. One major area of focus was stopping credential-based threats by tying policies to user identity.
More recently, led by Palo Alto Networks, the industry moved toward ML-powered NGFWs.
These firewalls use machine learning to detect threats in real time, majorly increasing firewall security overall. ML is used to detect known threats and variants, recognize suspicious behavior, and recommend actions based on context.
Alongside this, cloud-delivered firewall services have grown in use. As more organizations shift to hybrid and remote work models, FWaaS products offer cloud-native security that follows users and workloads wherever they go.
