- 1. What's driving the need for next-generation CASBs?
- 2. What are the limitations of conventional CASBs?
- 3. What is next-generation CASB architecture?
- 4. What are the features of a next-generation CASB?
- 5. What are the differences between legacy and next-generation CASBs?
- 6. What is the role of a next-gen CASB in SASE architecture?
- 7. What to look for in a next-gen CASB solution
- 8. 7 next-gen CASB implementation best practices
- 9. Next-generation CASB FAQs
- What's driving the need for next-generation CASBs?
- What are the limitations of conventional CASBs?
- What is next-generation CASB architecture?
- What are the features of a next-generation CASB?
- What are the differences between legacy and next-generation CASBs?
- What is the role of a next-gen CASB in SASE architecture?
- What to look for in a next-gen CASB solution
- 7 next-gen CASB implementation best practices
- Next-generation CASB FAQs
What Is a Next-Generation CASB? | 102 Guide
A next-generation CASB is a cloud security solution that provides real-time visibility, control, and protection for SaaS applications, users, and data.
It integrates with existing security systems to enforce consistent policies across cloud and on-premises environments. It also inspects user activity and data flows to detect risks, prevent data loss, and support regulatory compliance.
- What's driving the need for next-generation CASBs?
- What are the limitations of conventional CASBs?
- What is next-generation CASB architecture?
- What are the features of a next-generation CASB?
- What are the differences between legacy and next-generation CASBs?
- What is the role of a next-gen CASB in SASE architecture?
- What to look for in a next-gen CASB solution
- 7 next-gen CASB implementation best practices
- Next-generation CASB FAQs
What's driving the need for next-generation CASBs?
Modern IT environments are built around speed and flexibility. That shift has been driven by cloud adoption, especially the rise of SaaS.
Today, SaaS applications support nearly every business function—from HR to DevOps.
Which means: data now lives in more places and moves in more ways than traditional tools were designed to handle.
At the same time, the hybrid workforce has become the norm. Employees are working from offices, homes, and everywhere in between.
As a result, organizations need to protect users and data without relying on perimeter-based controls. Traditional CASBs weren't built for that level of scale or fluidity.
There's also the problem of visibility. SaaS use is often decentralized. Different departments adopt their own tools, and IT doesn't always have full oversight. That leads to gaps in coverage, unmanaged risk, and potential compliance issues. It's a growing challenge—and it's happening fast.
Next-generation CASBs address this by providing consistent, context-aware controls across all apps, users, and devices. In other words: they close the gap between modern SaaS usage and enterprise-grade security.
What are the limitations of conventional CASBs?
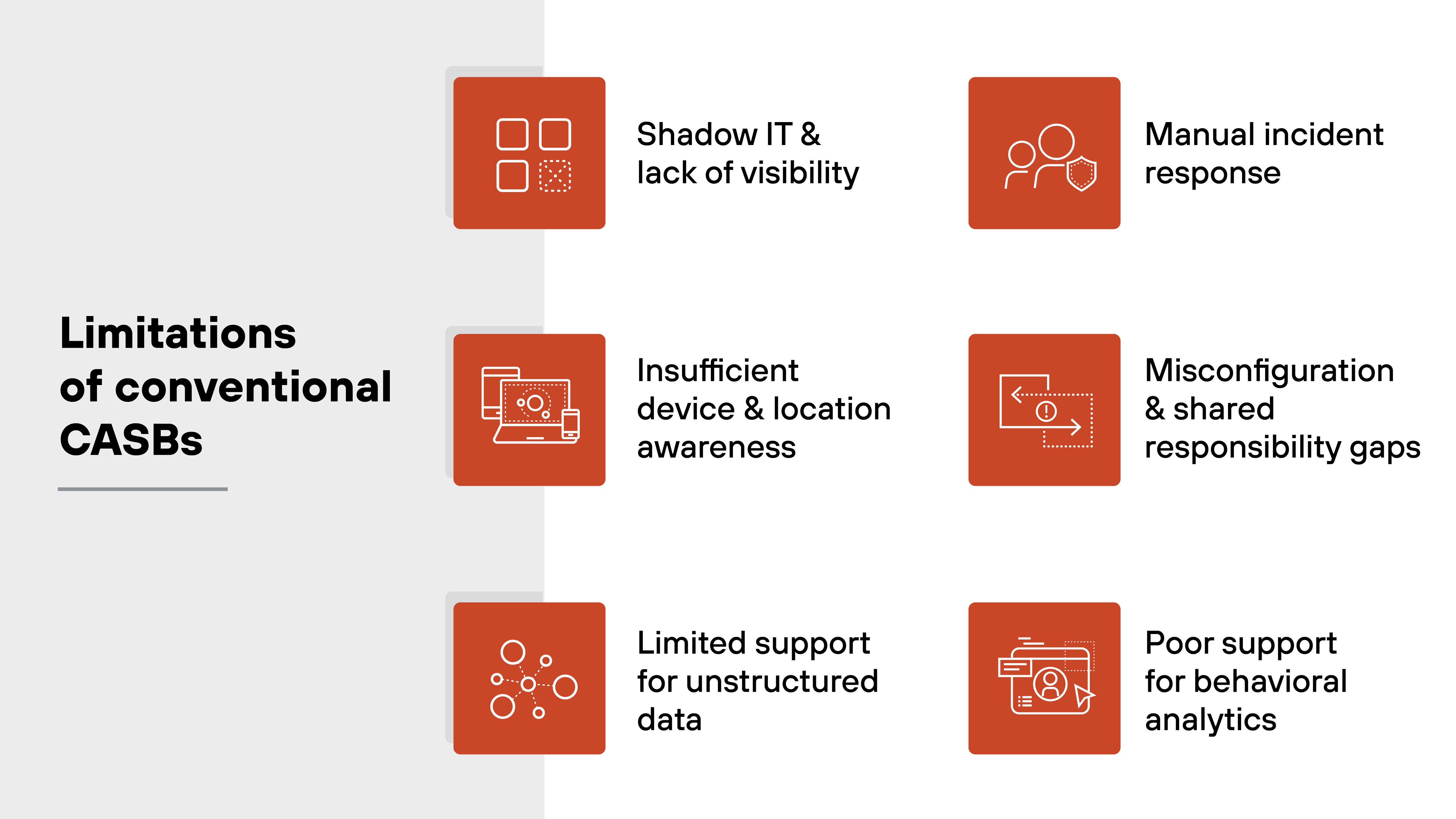
Legacy CASB solutions were designed for a different era of cloud adoption.
While they introduced important visibility and control capabilities, they no longer align with how modern SaaS environments operate.
Let’s break down why.
Shadow IT and lack of visibility
Conventional CASBs struggle with unmanaged SaaS usage. Employees can access apps directly without passing through the corporate network. Which means IT often doesn’t know what’s in use or how data is being shared.
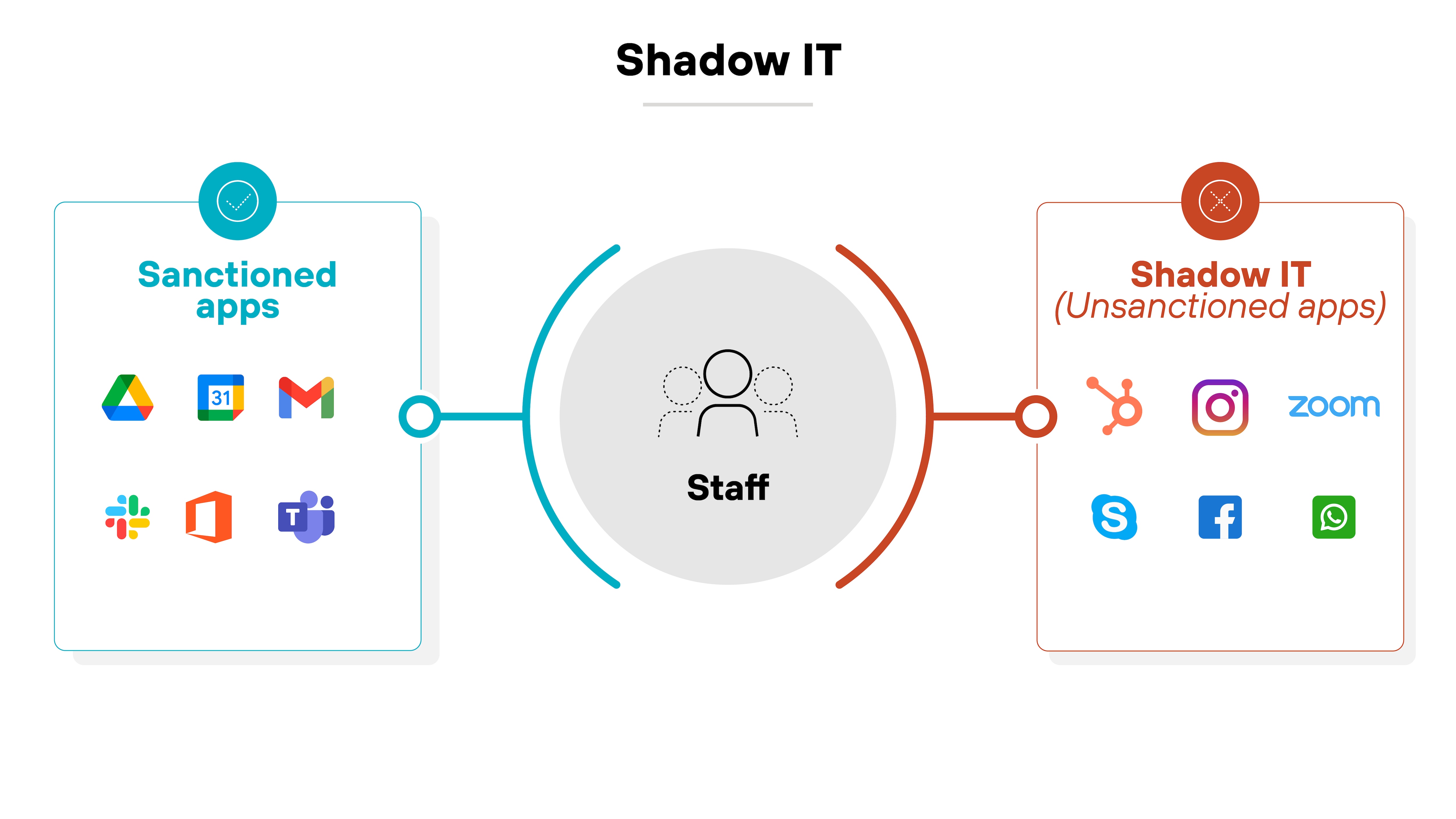
This creates serious gaps in visibility. When apps are unsanctioned, IT can’t enforce policy or ensure data security. It also increases the likelihood of noncompliance with data protection requirements.
On top of that, decentralized adoption across departments makes SaaS usage harder to track. The result is a growing attack surface—and limited ability to monitor or manage it effectively.
Insufficient device and location awareness
Traditional CASBs were built for a time when most users worked on managed devices inside the corporate perimeter. That’s no longer the case. Today, users access cloud apps from personal devices, public networks, and remote locations.
The problem: first-generation CASBs can’t always distinguish between legitimate access and risky behavior. They often lack the real-time context needed to make informed policy decisions. Especially when access patterns fall outside expected norms.
In other words, they weren't built to account for the fluid access models that define hybrid work today. That’s a serious limitation.
Limited support for unstructured data
Data loss prevention is a key part of any CASB. But older solutions were designed with structured data in mind. They rely on pattern matching, regular expressions, and fingerprinting to identify sensitive content.
That approach breaks down with modern communication tools. Apps like Slack, Teams, and Zoom introduce unstructured messages that don’t follow predictable formats. Conventional CASBs have trouble parsing this data, let alone classifying or protecting it.
The end result: slow, incomplete, or inaccurate detection. Which makes it difficult to keep up with today’s collaboration-heavy workflows.
Manual incident response
Speed matters in cloud security. Threats evolve fast, and slow response times give attackers more room to operate. But many older CASBs still rely on manual workflows for incident management.
That leads to delays. Investigations take longer. Containment and remediation aren’t consistent. And in the meantime, risks spread across the environment.
Automation is no longer optional. But conventional CASBs often weren’t built with that in mind.
Misconfiguration and shared responsibility gaps
Cloud apps offer flexibility. But that flexibility comes with complexity. Every new feature or permission introduces a new potential risk.
Conventional CASBs often fall short in detecting misconfigurations—especially in SaaS environments where responsibilities are shared. Many users assume cloud providers handle security end-to-end. That’s not the case.
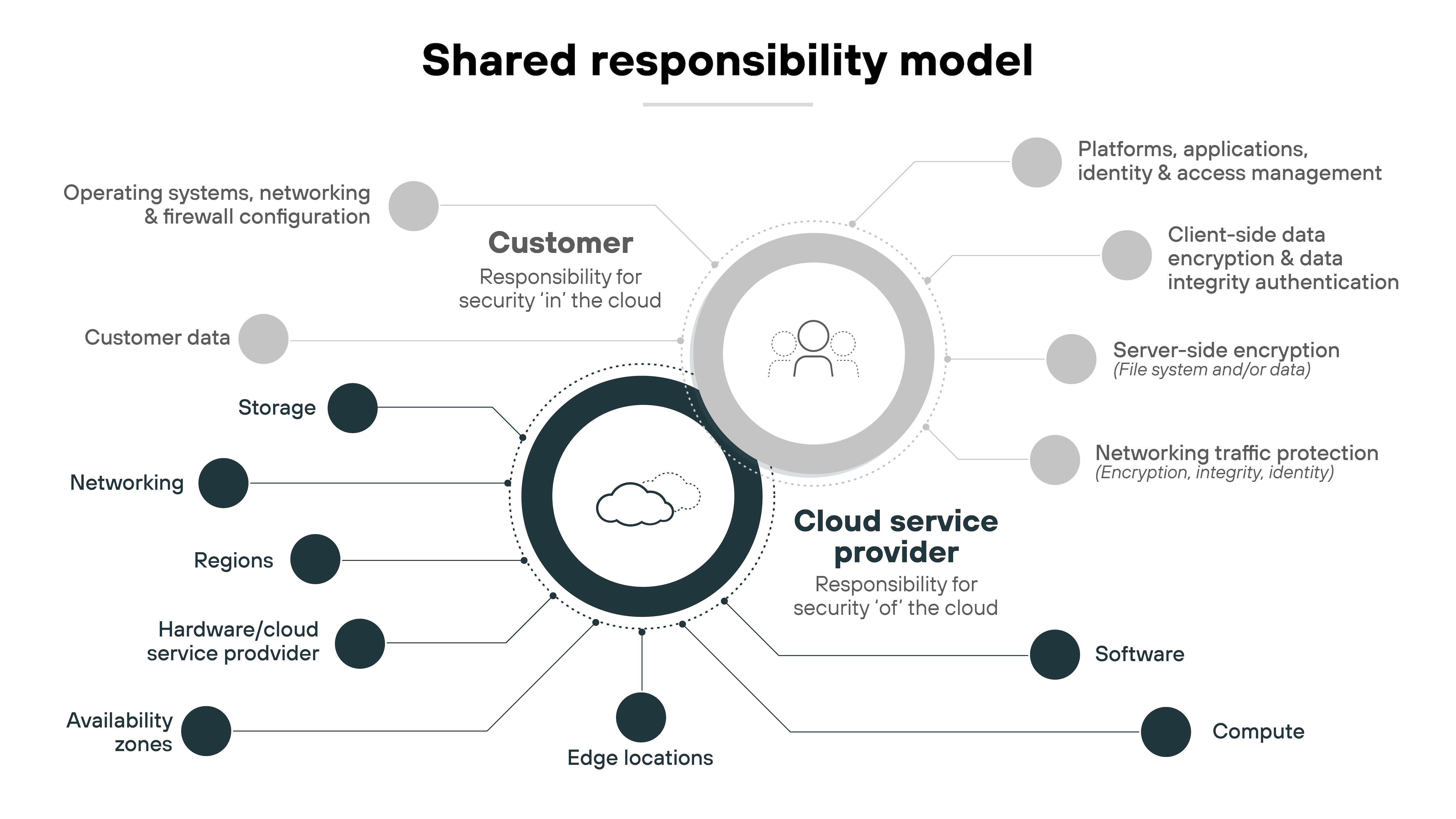
For example: A misconfigured sharing setting in a collaboration app can expose sensitive data to the public. Without real-time insight, these issues can go unnoticed.
Poor support for behavioral analytics
User behavior is more dynamic than ever. Hybrid work has changed access patterns, usage habits, and risk signals. That makes baselining “normal” behavior more difficult.
Legacy CASBs rely heavily on static rules. They don't adapt easily to shifts in user activity. Which means they often miss signs of insider threats, compromised accounts, or accidental data exposure.
Without strong behavioral analytics, organizations are left guessing. And in security, that's a problem.
What is next-generation CASB architecture?
Next-generation CASB architecture is built to support today's cloud-first environments. It brings together multiple control points, real-time analytics, and deep data protection—across users, apps, and devices.
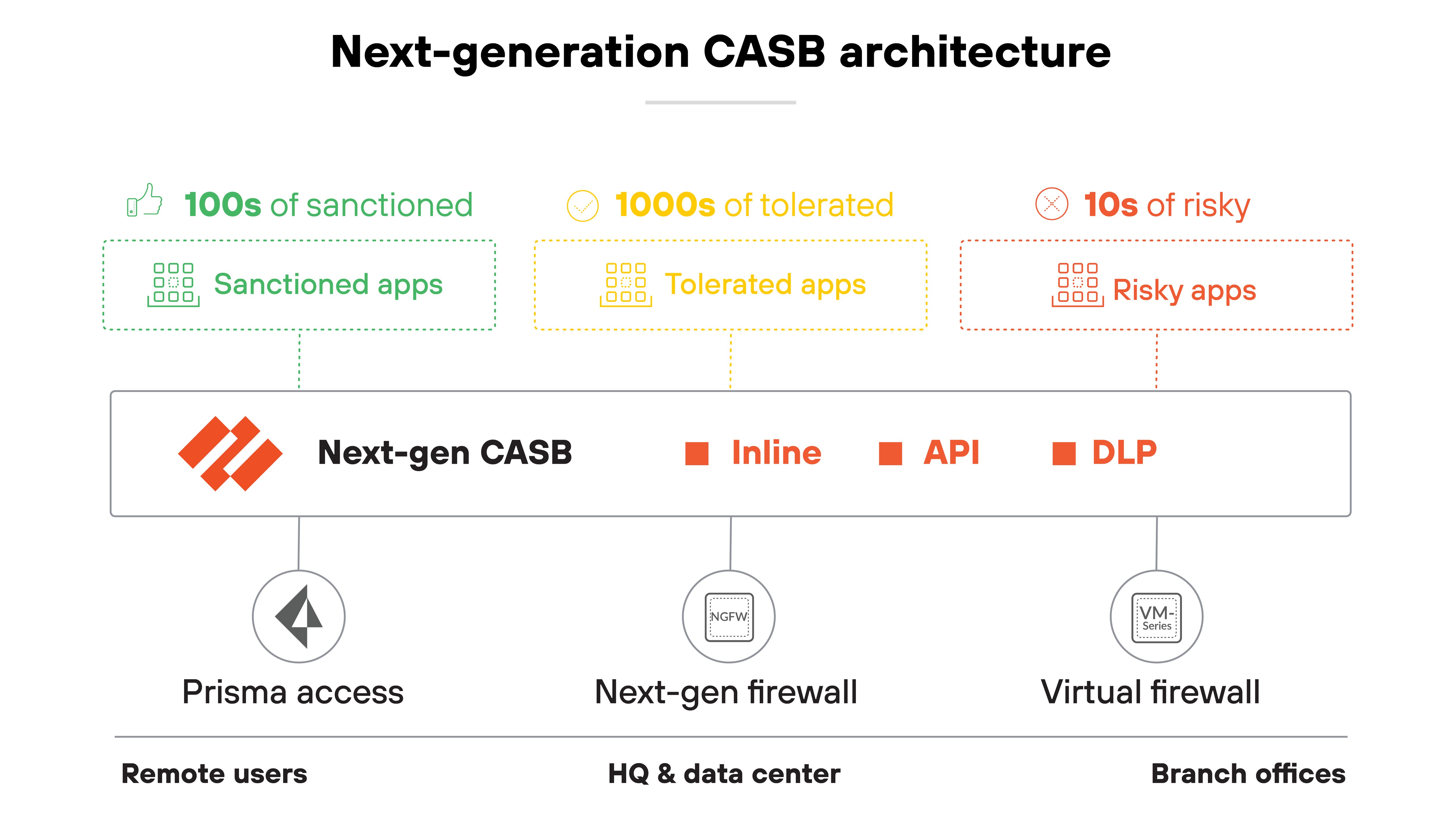
Here's how the core components work.
Multimode deployment
Multimode architecture combines both in-line and API-based methods. Each serves a different purpose and covers a different gap in SaaS visibility and control. Together, they provide broader protection than either approach alone.
In-line controls focus on traffic inspection. They sit between users and apps to enforce access controls and prevent risky behavior in real time. API integrations work directly with SaaS apps to scan data at rest and monitor user activity inside the apps.
In other words: Multimode support allows next-gen CASBs to protect both data in motion and data at rest. That makes the architecture more flexible and responsive to the needs of hybrid workforces.
API-based integration
API-based controls give direct access to sanctioned SaaS apps. This enables the CASB to monitor files, messages, permissions, and configuration settings—without depending on user traffic.
Here's why that matters:
It allows for continuous scanning, even when users access apps from unmanaged devices or external networks. The CASB can detect sensitive data exposure, malicious content, or misconfigured sharing policies in real time.
Because it's out-of-band, it also doesn't interfere with app performance. That makes it a critical piece of modern CASB architecture.
In-line enforcement
In-line controls inspect and enforce policies on live traffic. They look at data in motion between users and SaaS platforms. This enables policy enforcement on unmanaged apps or traffic that bypasses API integrations.
For example: If a user tries to upload sensitive data to an unsanctioned app, in-line controls can block or redirect the request. They also enable contextual access decisions based on device type, user identity, or location.
When paired with secure web gateways or broader SASE infrastructure, these controls expand coverage across the entire user environment.
Integrated data loss prevention (DLP)
Modern CASB architecture includes DLP that's built for the cloud. It can automatically discover, classify, and protect sensitive data—wherever it's stored or shared.
That includes both structured and unstructured formats. Think databases, but also chat messages, screenshots, and shared links in collaboration tools. The system uses advanced detection techniques to reduce false positives and streamline response.
Important:
The ability to classify content accurately is the foundation of effective policy enforcement. Without that, automation can break down or cause unnecessary disruptions.
Centralized analytics and threat detection
Next-gen CASBs use cloud-based machine learning to identify SaaS risks. They analyze usage patterns, flag anomalies, and detect threats across the environment. The architecture supports both pre-defined rules and adaptive models that respond to behavioral changes.
This helps uncover shadow IT and unusual activity. It also supports detailed reporting—so security teams have the insight needed for auditing and investigation.
In short:
Analytics turn raw activity into actionable risk signals. That's a key capability for scaling protection across today's decentralized cloud environments.
What are the features of a next-generation CASB?
Next-generation CASBs are designed to handle the speed, scale, and complexity of cloud-first environments. Each feature supports a specific function—visibility, data protection, threat detection, or control. Here’s what makes them different from older CASB models.
Visibility into sanctioned and unsanctioned SaaS apps
Next-gen CASBs continuously discover SaaS apps in use—whether they’re approved by IT or not. This includes sanctioned, tolerated, and unsanctioned apps across every user, device, and location.
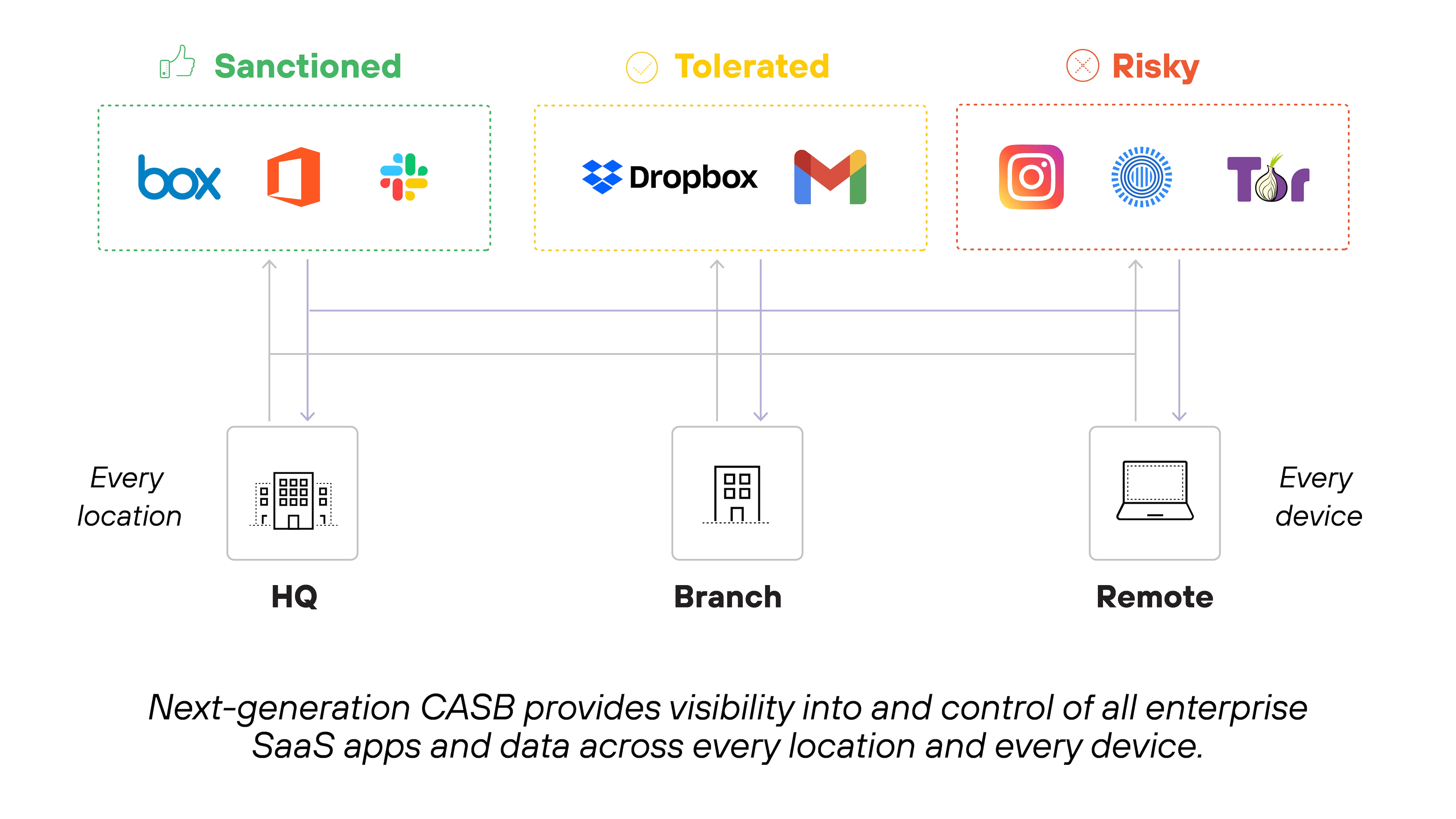
They do this by scanning all traffic, not just web-based protocols like HTTP or HTTPS. In other words: Visibility isn’t limited to known risks. It includes unknown and emerging apps too.
Cloud-delivered data loss prevention (DLP)
Modern DLP is core to next-gen CASBs. It identifies and protects sensitive data in motion and at rest across all SaaS applications. That includes structured records and unstructured content like messages, screenshots, and documents.
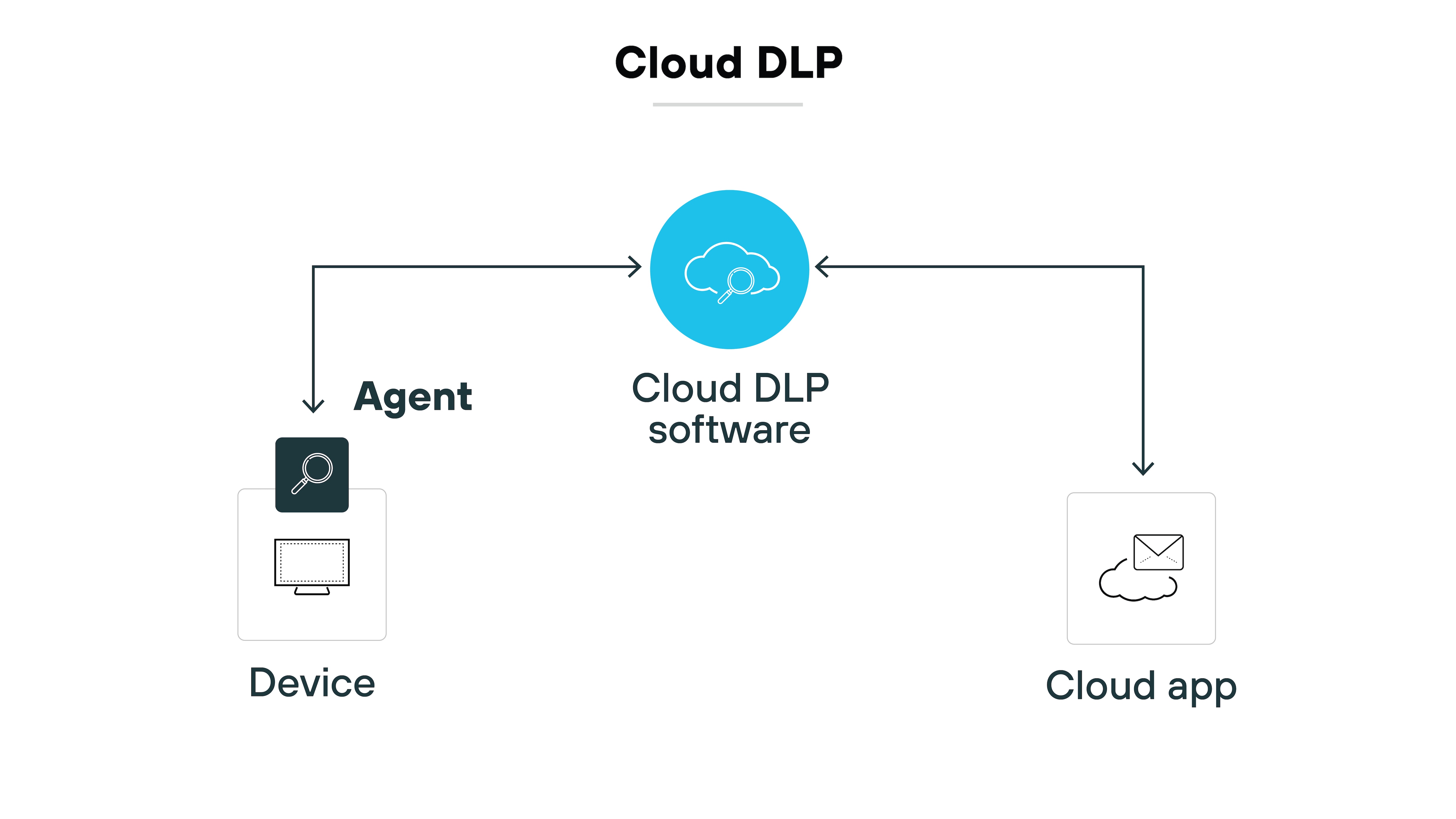
Detection accuracy matters. Which is why next-gen CASBs use ML-based classification, regex, and context-aware logic to reduce false positives. This supports consistent data protection policies—without disrupting users.
Threat prevention
Threat prevention combines DLP, user behavior monitoring, and policy enforcement. It applies across access points, user locations, and managed or unmanaged devices.
The goal is to stop known and unknown threats targeting SaaS apps. These could include malware, account takeovers, or excessive permissions. Importantly, this happens in real time—without adding complexity or relying on third-party tools.
Granular in-line controls
In-line controls are used to inspect traffic and enforce policy in real time. Granular controls let security teams apply specific rules to particular apps, users, or use cases.
For example: You can allow access to a file-sharing app but block uploads from unmanaged devices. This flexibility is important for enforcing security without blocking productivity.
Incident response and automation
Next-gen CASBs include automation to handle alerts and incidents faster. When a policy is triggered, the system can notify users, take protective action, and log the event for review.
This shortens response time and helps security teams scale. It also supports end-user alerting—so users understand what was blocked and why, with limited need for IT intervention.
Suspicious user activity detection
User and entity behavior analytics (UEBA) helps detect unusual activity. It builds a baseline of normal behavior, then uses that to spot anomalies—like a sudden spike in downloads or failed login attempts.
This can surface compromised accounts, insider threats, or risky behavior early. UEBA is especially useful in decentralized environments where traffic patterns are constantly shifting.
SaaS security posture management (SSPM)
SSPM focuses on the security of the SaaS apps themselves. It identifies misconfigurations, risky settings, or permission issues that could lead to data exposure.
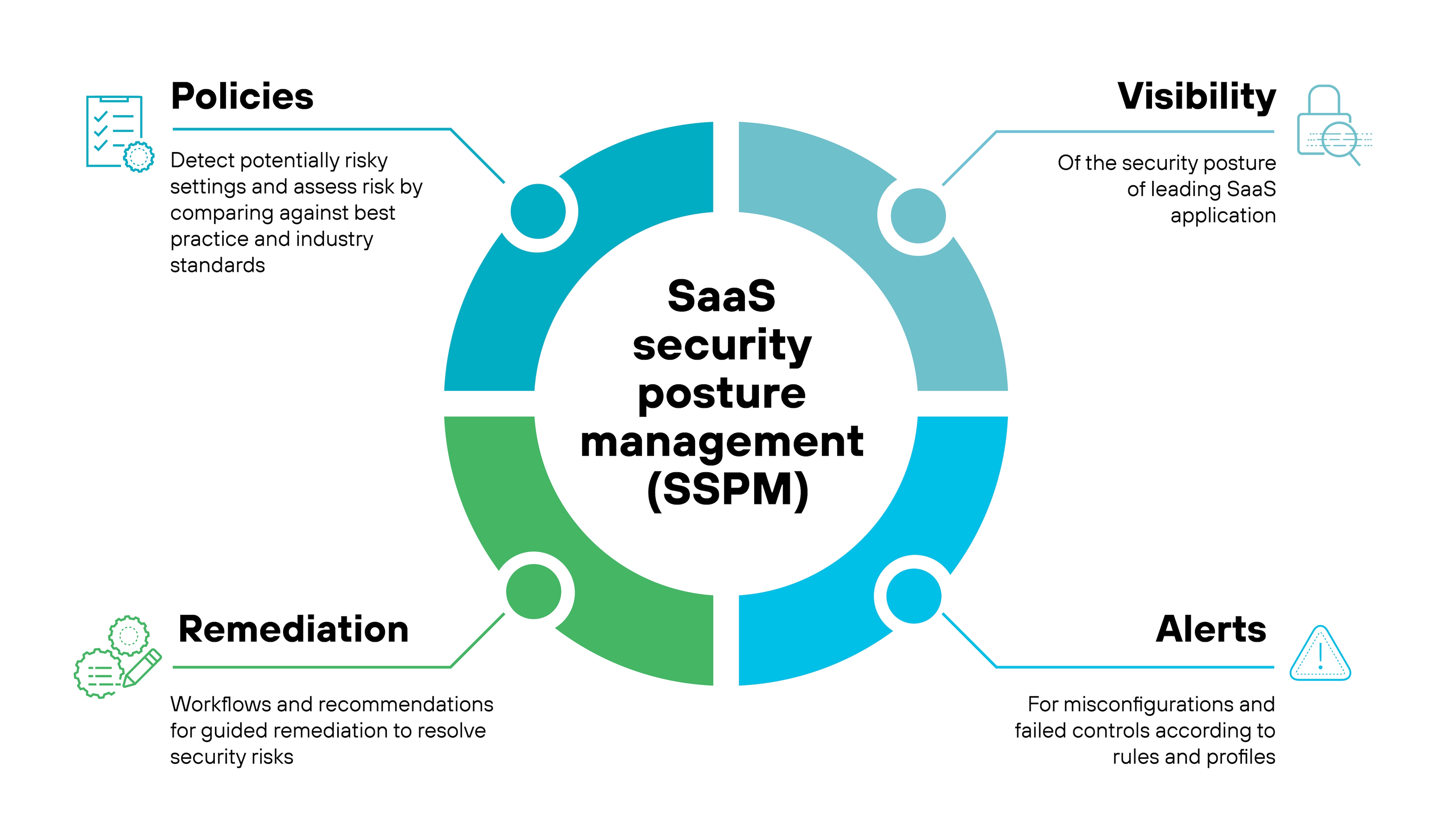
This is a gap in many legacy CASBs. As organizations use more SaaS apps, the number of settings grows—making it harder to configure everything securely. SSPM brings that visibility and control back to the security team.
What are the differences between legacy and next-generation CASBs?
Comparison: Legacy vs. next-gen CASBs
| Category | Legacy CASBs | Next-gen CASBs |
|---|---|---|
| Application coverage | Protect only HTTP/HTTPS apps. Limited to basic productivity tools. | Support all app protocols, including collaboration tools with chat and image content. |
| SaaS discovery | Manual discovery using static app libraries. No ML or automation. | Automated app discovery using ML and crowdsourced intelligence. |
| Architecture and integration | Proxy-based, disjointed from enterprise infrastructure. Complex to deploy and manage. | Unified platform with SASE and DLP integration. One-click deployment across all users. |
| Data protection | Basic, cloud-only DLP. Inaccurate, pattern-based detection not integrated with enterprise DLP | Comprehensive enterprise DLP across all environments. Accurate detection using ML and NLP. |
| Threat protection | Limited protection, relying on third-party sandbox. Only covers HTTP/HTTPS threats. | Integrated and proactive threat protection across SaaS, IaaS, network, and remote users. |
Legacy CASBs were introduced to fill an early gap in cloud visibility and control. At the time, they offered basic discovery and policy enforcement for sanctioned SaaS apps. But the cloud environment has changed. And those early tools haven't kept up.
For example: Legacy CASBs rely on static app libraries that must be updated manually. That limits their ability to discover new or unsanctioned SaaS apps in real time. In contrast, next-generation CASBs use machine learning and global threat data to detect and categorize apps dynamically—often before users report them.
Data protection is another major difference. Older CASBs apply basic DLP only within certain apps and often lack full integration with enterprise-wide policies. Next-gen CASBs extend data protection across all apps, users, and devices, using advanced detection techniques that adapt to unstructured data and modern collaboration tools.
Finally, legacy CASBs were often deployed as stand-alone proxies. That model required complicated traffic routing and didn't integrate well with other security tools. By comparison, next-generation CASBs are cloud-delivered, policy-driven, and designed to operate as part of a broader architecture—whether that's SASE, ZTNA, or another unified approach.
What is the role of a next-gen CASB in SASE architecture?
Next-generation CASBs play a central role in securing SaaS access within a SASE architecture. While SASE brings together networking and security into a unified, cloud-delivered model, CASBs focus specifically on protecting cloud applications and data. In other words: CASBs handle the SaaS-specific risks that SASE alone doesn't fully address.
A next-gen CASB enables real-time discovery of SaaS usage. This includes shadow IT, unsanctioned apps, and unmanaged devices. Visibility like this is critical to enforcing access policies and identifying potential compliance gaps across all users—no matter where they connect from.
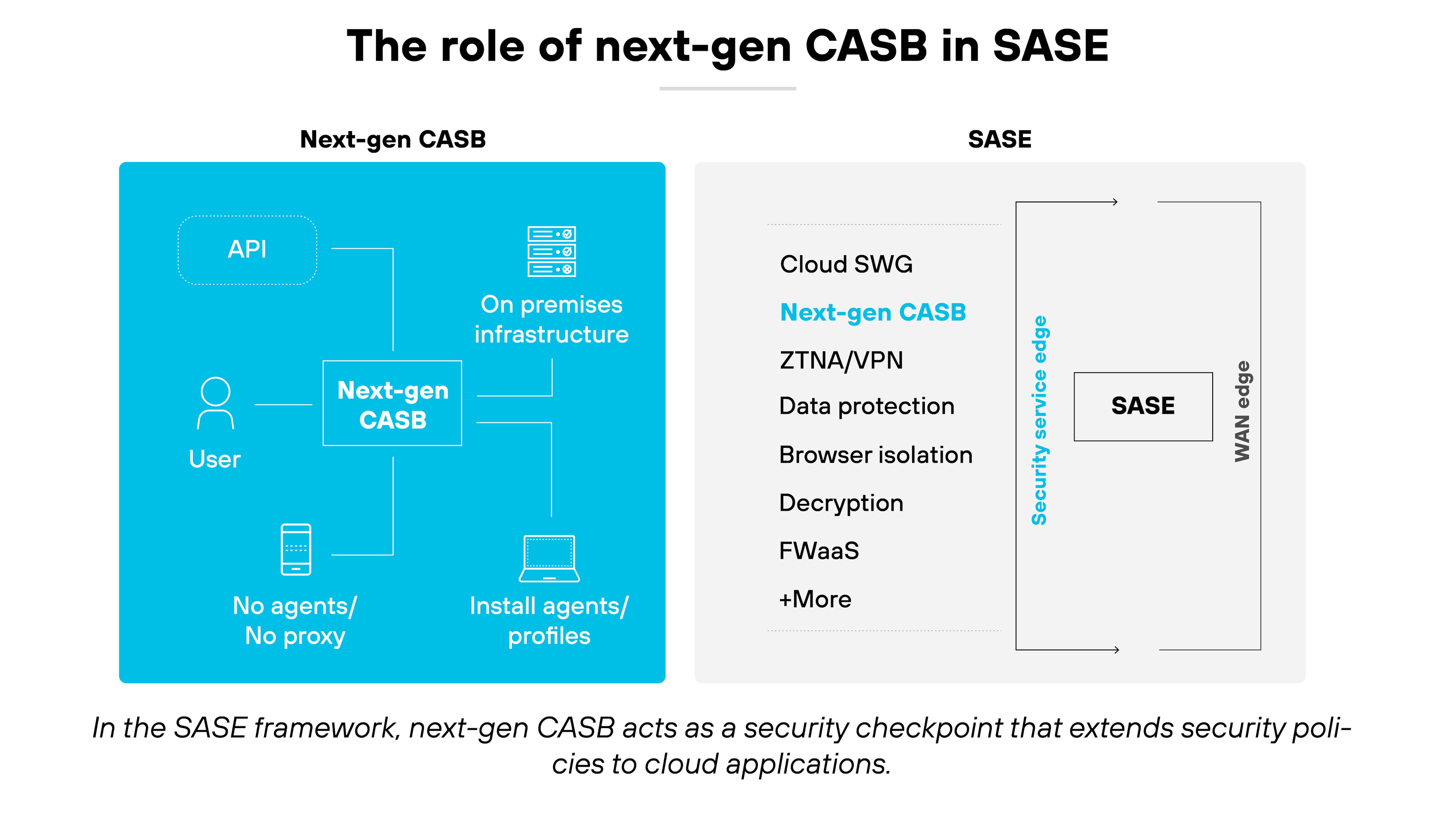
It also supports core Zero Trust principles. That means continuous validation of user behavior, real-time data classification, and dynamic policy enforcement. With these controls, SASE can adapt to different risk levels based on context—not just static rules.
Finally, next-gen CASBs bring advanced threat and data protection into the SASE framework. They inspect traffic and API activity to detect risky actions, suspicious behavior, or misconfigurations in SaaS apps. The result: SaaS-specific risks are managed as part of a broader, integrated security strategy.
- Cloud Access Security Brokers: A Key Capability of a Secure Access Service Edge Solution
- SASE vs. CASB: What Is the Difference?
- Secure Web Gateway vs. CASB: What Is the Difference?
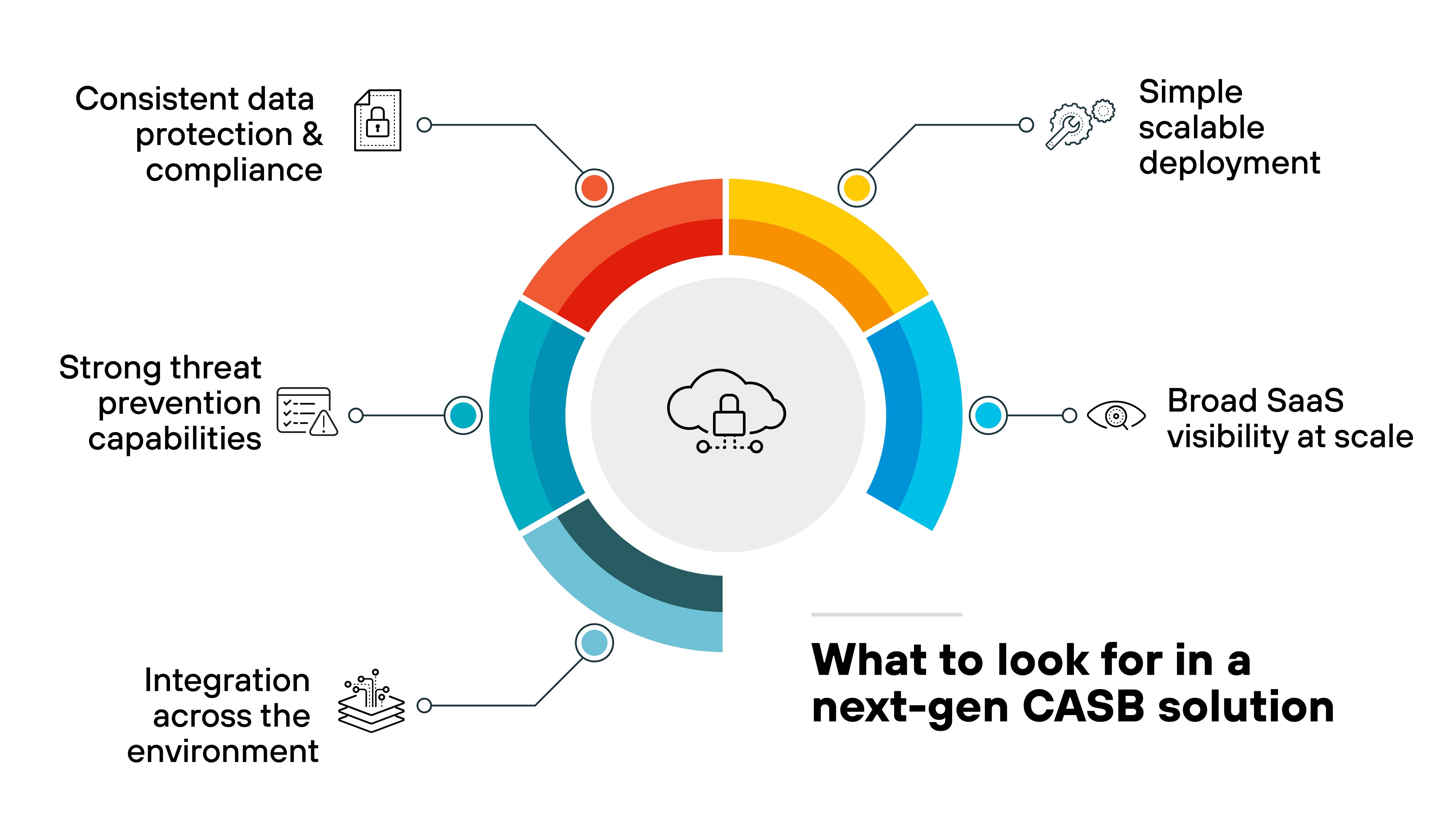
What to look for in a next-gen CASB solution
Selecting the right next-generation CASB starts with understanding the needs of your environment. Different teams, apps, and data types require different capabilities.
The right solution should provide visibility, protection, and policy control—at scale and without added complexity.
Broad SaaS visibility at cloud scale
A next-gen CASB should automatically detect both sanctioned and unsanctioned SaaS apps. That includes newer collaboration tools and shadow IT. It also needs to scan all traffic—not just web-based protocols—to ensure comprehensive coverage.
Look for solutions that use machine learning and application ID engines to continuously discover apps. These engines should assign customizable risk scores to support policy decisions. In other words: The solution should identify risks before they create problems.
Simple, scalable deployment
Legacy CASBs often require complex setups with proxies, PAC files, and endpoint agents. That doesn't scale well. A next-gen CASB should be cloud-delivered and easy to deploy across remote and on-site users.
It should provide a centralized dashboard, support native integrations, and reduce reliance on infrastructure changes. This helps security teams stay focused on enforcement—not configuration.
Strong threat prevention capabilities
Threats targeting SaaS apps aren't always file-based or known. A next-gen CASB should detect and block both known and unknown threats—without third-party tools. That means using inline machine learning, real-time analysis, and up-to-date global threat intelligence.
It should also support automated remediation workflows. This shortens response times and reduces manual effort for security teams.
Consistent data protection and compliance
Look for DLP that protects both structured and unstructured data. The CASB should classify and secure data in motion and at rest—across all users, apps, and locations. That includes content in modern chat-based collaboration tools.
Advanced features like exact data matching, NLP, and optical character recognition can improve accuracy. And built-in reporting helps meet compliance obligations without creating more work.
Integration across the environment
A good next-gen CASB won't operate in isolation. It should integrate with your broader security architecture and work consistently across all environments—cloud, on-premises, and remote.
Multimode deployment is key. That means combining inline controls with API-based inspection to cover both real-time traffic and out-of-band app activity. It should also protect data, apps, and users without introducing new security gaps or dependencies.
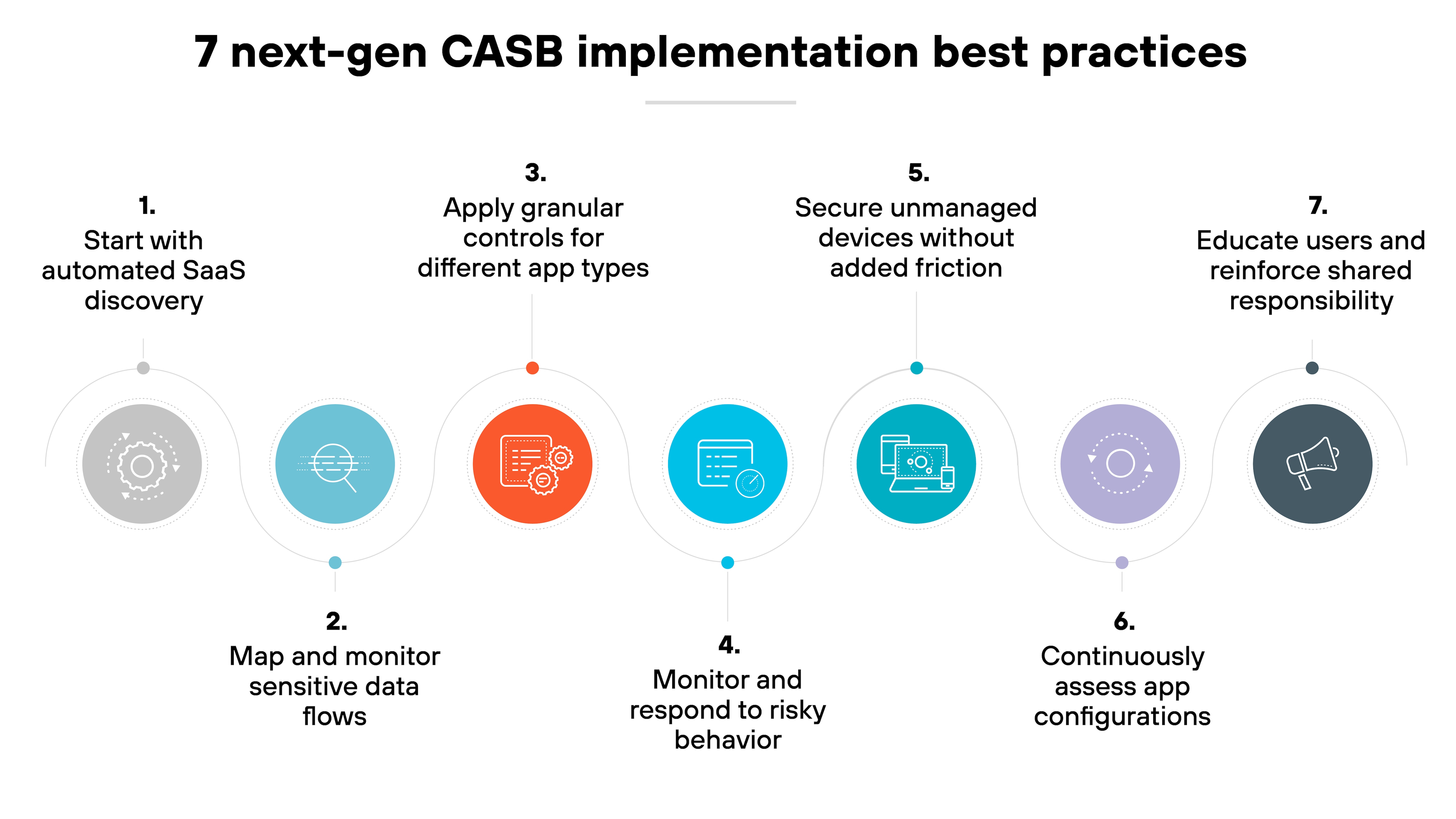
7 next-gen CASB implementation best practices
Rolling out a next-generation CASB isn’t just about turning on new technology. It’s about making sure the controls you enable are aligned with the way your organization actually works.
Here’s how to get started—and what to focus on.
1. Start with automated SaaS discovery
Before policies can be applied, you need to know what SaaS apps are in use. That includes sanctioned apps, tolerated apps, and unsanctioned apps across departments and remote users.
A next-gen CASB should automatically discover apps and categorize them by risk. In other words: you can’t protect what you can’t see—so visibility comes first.
2. Map and monitor sensitive data flows
SaaS usage creates complex data flows. Files are stored, shared, and edited in cloud platforms that often fall outside traditional controls.
The CASB should identify where sensitive data lives and how it moves across users and devices.
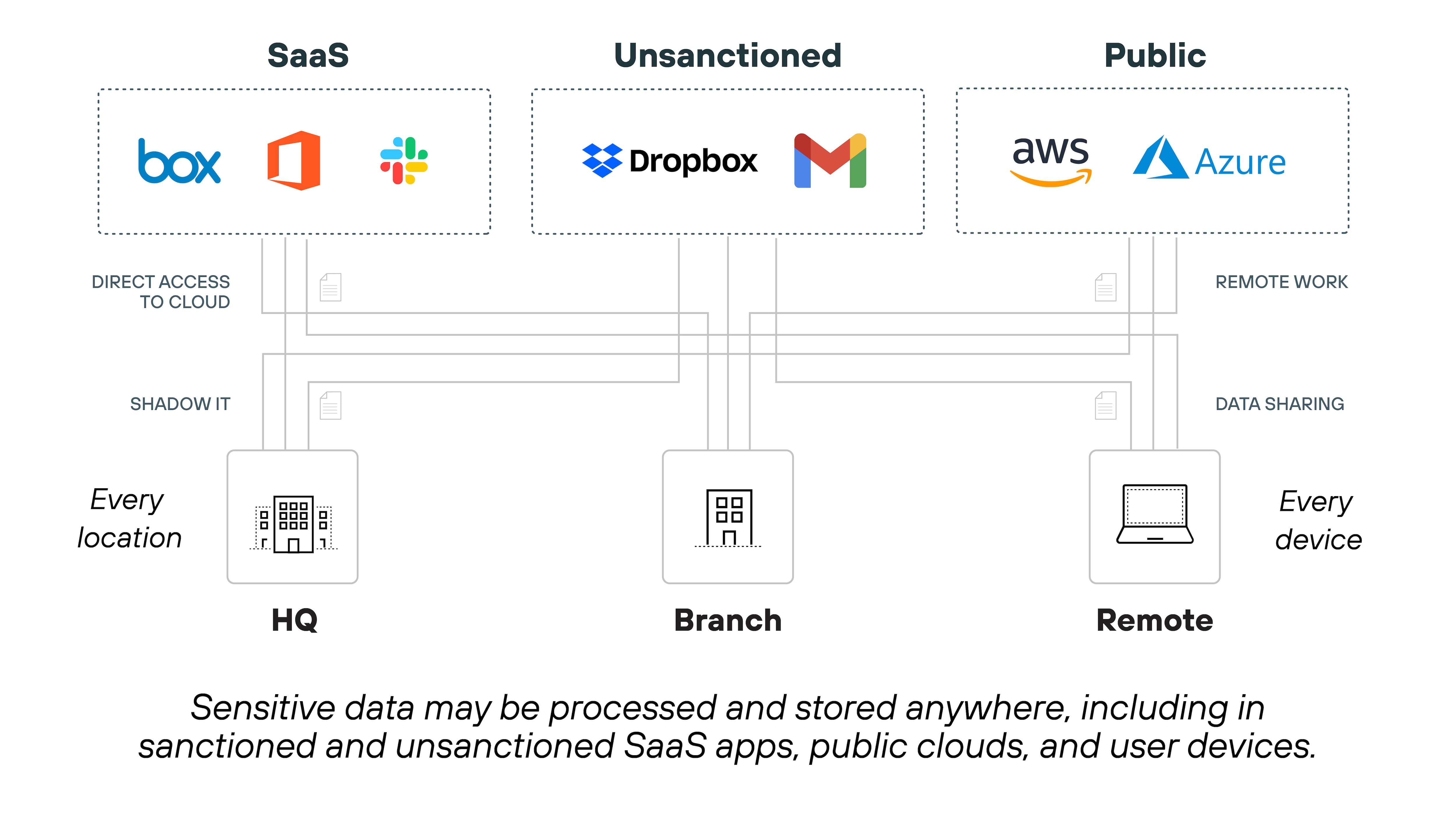
This is key for enforcing data loss prevention and regulatory compliance.
3. Apply granular controls for different app types
Not all apps should be treated the same. Some are business-critical. Others may be tolerated but risky. And some should be blocked altogether.
Next-gen CASBs let you define policies based on app type, risk score, or user role. This allows security to adapt to context rather than applying one-size-fits-all rules.
4. Monitor and respond to risky behavior
Well-meaning users often cause security issues without realizing it. Uploading a sensitive file to the wrong platform. Sharing data through a personal email account.
Use behavior analytics and activity monitoring to detect unusual access or usage patterns. Then trigger alerts or automated responses based on severity.
5. Secure unmanaged devices without added friction
Users increasingly connect from personal or unmanaged devices. That doesn’t mean they should have unrestricted access to sensitive data.
A next-gen CASB should enforce policy based on device trust level. For example: allow read-only access from unmanaged devices or block downloads entirely.
6. Continuously assess app configurations
Protecting SaaS apps isn’t just about users and data. It’s also about the app settings themselves. Misconfigurations can lead to exposure—even when policies are in place.
Look for CASB tools that provide SaaS security posture management (SSPM). These tools identify risky settings and help align them with best practices across apps.
7. Educate users and reinforce shared responsibility
Technology alone won’t eliminate all risk. Users still need to understand what behaviors put data at risk and why controls are in place.
Provide clear guidance on app usage and acceptable behaviors. And use in-product alerts to help users course-correct in real time—without relying entirely on IT.
