What is an Intrusion Detection System?
An Intrusion Detection System (IDS) is a network security technology originally built for detecting vulnerability exploits against a target application or computer.
The IDS is also a listen-only device. The IDS monitors traffic and reports results to an administrator. It cannot automatically take action to prevent a detected exploit from taking over the system.
Attackers are capable of exploiting vulnerabilities quickly once they enter the network. Therefore, the IDS is not adequate for prevention. Intrusion detection and intrusion prevention systems are both essential to security information and event management.
Intrusion Detection Systems vs. Intrusion Prevention Systems
The following table summarizes the differences between the IPS and the IDS deployment.
| Intrusion Prevention System | IDS Deployment | |
|---|---|---|
| Placement in Network Infrastructure | Part of the direct line of communication (inline) | Outside direct line of communication (out-of-band) |
| System Type | Active (monitor & automatically defend) and/or passive | Passive (monitor & notify) |
| Detection Mechanisms | 1. Statistical anomaly-based detection 2. Signature detection: - Exploit-facing signatures - Vulnerability-facing signatures |
1. Signature detection: - Exploit-facing signatures |

Diagram depicting the difference between an IPS and an IDS
How IDS Works
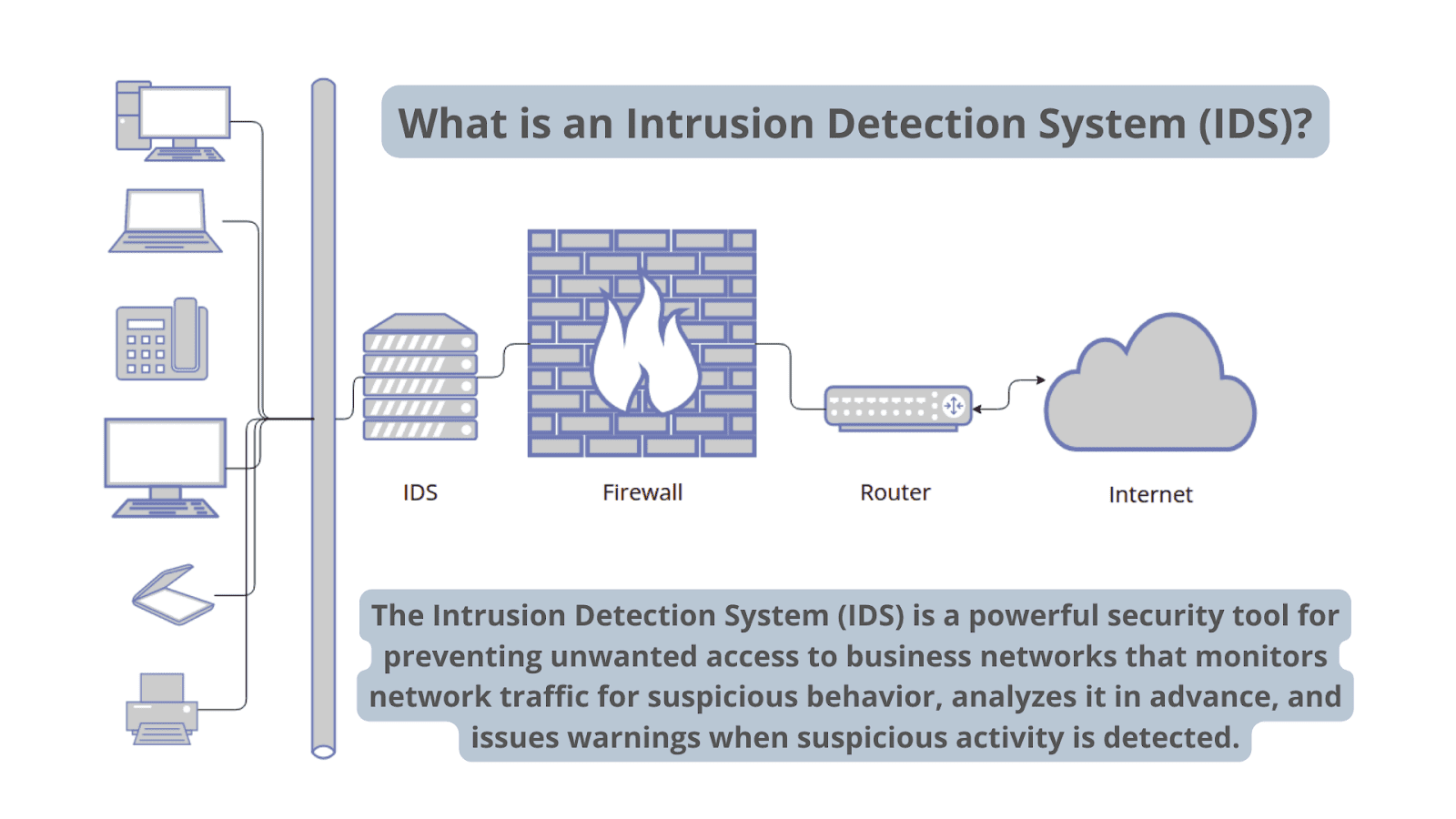
Diagram depicting the functionality of an intrusion detection system
An IDS only needs to detect potential threats. It is placed out of band on the network infrastructure. Consequently, it is not in the real-time communication path between the sender and receiver of information.
IDS solutions often take advantage of a TAP or SPAN port to analyze a copy of the inline traffic stream. This ensures that the IDS does not impact inline network performance.
When IDS was developed, the depth of analysis required to detect intrusion could not be performed quickly enough. The speed would not keep pace with components on the direct communications path of the network infrastructure.
Network intrusion detection systems are used to detect suspicious activity to catch hackers before damage is done to the network. There are network-based and host-based intrusion detection systems. Host-based IDSes are installed on client computers; network-based IDSes are on the network itself.
An IDS works by looking for deviations from normal activity and known attack signatures. Anomalous patterns are sent up the stack and examined at protocol and application layers. It can detect events like DNS poisonings, malformed information packets and Christmas tree scans.
An IDS can be implemented as a network security device or a software application. To protect data and systems in cloud environments, cloud-based IDSes are also available.
Types of IDS Detection
There are five types of IDS: network-based, host-based, protocol-based, application protocol-based and hybrid.
The two most common types of IDS are:
- Network-based intrusion detection system (NIDS)
A network IDS monitors a complete protected network. It is deployed across the infrastructure at strategic points, such as the most vulnerable subnets. The NIDS monitors all traffic flowing to and from devices on the network, making determinations based on packet contents and metadata. - Host-based intrusion detection system (HIDS)
A host-based IDS monitors the computer infrastructure on which it is installed. In other words, it is deployed on a specific endpoint to protect it against internal and external threats. The IDS accomplishes this by analyzing traffic, logging malicious activity and notifying designated authorities.
The remaining three types can be described as such:
- Protocol-based (PIDS)
A protocol-based intrusion detection system is usually installed on a web server. It monitors and analyzes the protocol between a user/device and the server. A PIDS normally sits at the front end of a server and monitors the behavior and state of the protocol. - Application protocol-based (APIDS)
An APIDS is a system or agent that usually sits inside the server party. It tracks and interprets correspondence on application-specific protocols. For example, this would monitor the SQL protocol to the middleware while transacting with the web server. - Hybrid intrusion detection system
A hybrid intrusion detection system combines two or more intrusion detection approaches. Using this system, system or host agent data combined with network information for a comprehensive view of the system. The hybrid intrusion detection system is more powerful compared to other systems. One example of Hybrid IDS is Prelude.
There is also a subgroup of IDS detection methods, the two most common variants being:
- Signature-based
A signature-based IDS monitors inbound network traffic, looking for specific patterns and sequences that match known attack signatures. While it is effective for this purpose, it is incapable of detecting unidentified attacks with no known patterns. - Anomaly-based
The anomaly-based IDS is a relatively newer technology designed to detect unknown attacks, going beyond the identification of attack signatures. This type of detection instead uses machine learning to analyze large amounts of network data and traffic.
Anomaly-based IDS creates a defined model of normal activity and uses it to identify anomalous behavior. However, it is prone to false positives. For example, if a machine demonstrates rare, but healthy behavior, it is identified as an anomaly. This results in a false alarm.
IDS vs. Firewalls
IDses and Next-Generation Firewalls are both network security solutions. What differentiates an IDS from a firewall is its purpose.
An IDS device monitors passively, describing a suspected threat when it’s happened and signaling an alert. IDS watches network packets in motion. This allows incident response to evaluate the threat and act as necessary. It does not, however, protect the endpoint or network.
A firewall monitors actively, looking for threats to prevent them from becoming incidents. Firewalls are capable of filtering and blocking traffic. They allow traffic based on preconfigured rules, relying on ports, destination addresses and the source
Firewalls reject traffic that does not follow firewall rules. However, if an attack is coming from inside the network, the IDS will not generate an alert.

Diagram depicting the functionality of an intrusion detection system and a firewall
IDS Evasion Techniques
There are numerous techniques intruders may use to avoid detection by IDS. These methods can create challenges for IDSes, as they are meant to circumvent existing detection methods:
- Fragmentation
Fragmentation divides a packet into smaller, fragmented packets. This allows an intruder to remain hidden, as there will be no attack signature to detect.
Fragmented packets are later reconstructed by the recipient node at the IP layer. They are then forwarded to the application layer. Fragmentation attacks generate malicious packets by replacing data in constituent fragmented packets with new data. - Flooding
This attack is designed to overwhelm the detector, triggering a failure of control mechanism. When a detector fails, all traffic will then be allowed.
A popular way to cause flooding is by spoofing the legitimate User Datagram Protocol (UDP) and Internet Control Message Protocol (ICMP). The traffic flooding is then used to camouflage the anomalous activities of the perpetrator. As a result, the IDS would have great difficulty finding malicious packets within an overwhelming volume of traffic. - Obfuscation
Obfuscation can be used to avoid being detected by making a message difficult to understand, thereby hiding an attack. The terminology of obfuscation means altering program code in such a way which keeps it functionally indistinguishable.
The objective is to reduce detectability to reverse engineering or static analysis process by obscuring it and compromising readability. Obfuscating malware, for instance, allows it to evade IDSes. - Encryption
Encryption offers multiple security capabilities including data confidentiality, integrity and privacy. Unfortunately, malware creators use security attributes to conceal attacks and evade detection.
For instance, an attack on an encrypted protocol cannot be read by an IDS. When the IDS cannot match encrypted traffic to existing database signatures, the encrypted traffic is not encrypted. This makes it very difficult for detectors to identify attacks.
Why Intrusion Detection Systems are Important
Cyberattacks are always increasing in complexity and sophistication, and Zero Day Attacks are common. As a result, network protection technologies must keep pace with new threats, and businesses must maintain high levels of security.
The objective is to assure secure, trusted communication of information. Therefore, an IDS is important to the security ecosystem. It operates as a defense for systems security when other technologies fail.
- Identify security incidents.
- Analyze the quantity and types of attacks.
- Help identify bugs or problems with device configurations.
- Support regulatory compliance (by means of better network visibility and IDS log documentation).
- Improve security responses (by means of inspecting data within network packets, rather than manual census of systems).
While IDSes are useful, they are extended in impact when coupled with IPSes. Intrusion Prevention Systems (IPS) add the ability to block threats. This has become the dominant deployment option for IDS/IPS technologies.
Better still is the blend of multiple threat prevention technologies to form a complete solution. An effective approach is a combination of:
- Vulnerability protection
- Anti-malware
- Anti-spyware
These technologies combined constitute advanced threat protection. The service scans all traffic for threats (including ports, protocols and encrypted traffic). Advanced threat prevention solutions look for threats within the cyberattack lifecycle, not just when it enters the network. This forms a layered defense — a Zero Trust approach with prevention at all points.