What Is Hybrid Cloud Security?
Hybrid cloud security is the totality of the technologies and procedures established to protect data, applications, and infrastructure in a hybrid cloud environment (which may include any combination of public and private clouds or on-premises data centers).
Effective hybrid cloud security typically requires:
- Next-generation firewalls (NGFWs)
- A centralized management system
- Security services that span environments
Why Is Hybrid Cloud Security Important?
“Gartner’s ‘cloud shift’ research includes only those enterprise IT categories that can transition to cloud, within the application software, infrastructure software, business process services and system infrastructure markets.
By 2025, 51% of IT spending in these four categories will have shifted from traditional solutions to the public cloud, compared to 41% in 2022. Almost two-thirds (65.9%) of spending on application software will be directed toward cloud technologies in 2025, up from 57.7% in 2022.”
We live in an age of cloud and digital transformation. Users and applications are moving outside the traditional network perimeter. An increasing number of application workloads are accessed from the public cloud, including: software-as-a-service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS):
- 53% of cloud workloads are hosted on public cloud platforms, an increase of 8% in the past year.
- The top reason organizations are moving to the cloud are building new and expanding existing products and services. The desire to increase efficiency and agility closely follows.
With increasing frequency, enterprises are choosing multicloud or hybrid models. A hybrid cloud allows organizations to enjoy the benefits of the cloud while maintaining the flexibility to use other environments. Consequently, organizations face the challenge of proactively protecting users, applications, and data from security threats without compromising user experience — and across multiple environments:
- Security considerations continue to impede the ability of enterprises to address risks and take advantage of the cloud.
Hybrid Cloud Security Challenges
Hybrid cloud environments come with complicated security problems. The combination of cloud security requirements, the shared responsibility model, and a constantly evolving threat landscape contribute to hybrid cloud security challenges.
Cloud Security and the Shared Responsibility Model
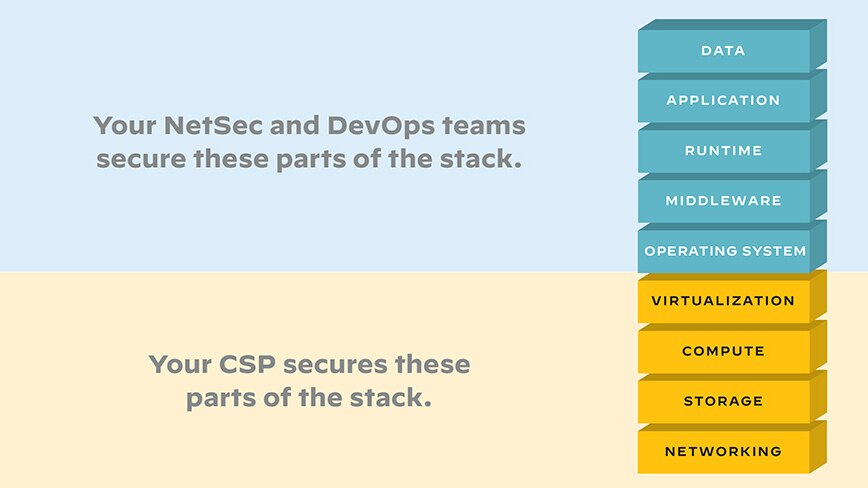
Figure 1: Shared security responsibility across private, public, and SaaS cloud services
- Cloud security can come with trade-offs.
As the cloud has become an integral part of enterprise environments, many organizations face compromises with public and private cloud environments. Network security controls are often “streamlined” out of the cloud design. Consequently, cloud security trade-offs often include:
- Simplicity vs. function
- Efficiency vs. visibility
- Agility vs. security
- Attractive cloud computing features are often counter to network security.
Cloud computing technologies afford organizations dynamic, automated environments with on demand cloud resources. However, many features are counter to network security, including:
- Cloud computing doesn’t mitigate existing network security threats.
- Separation and segmentation are fundamental to security. However, the cloud relies on shared resources.
- Security deployments are process oriented. On the contrary, cloud computing environments are dynamic.
- Cloud-based apps and their data are becoming increasingly distributed.
The concern over data exposure has made cloud security a priority. The challenge has become balancing agility while improving application security and securing data as it moves among clouds. Visibility and preventing attacks are imperative across all locations where applications and data reside.
Dynamic Nature of Modern Threats
- The modern threat landscape is constantly evolving, and many sophisticated new threats have emerged in recent years.
- Port hopping
- Use of nonstandard ports
- Tunneling within commonly used services
- Hiding within Secure Sockets Layer (SSL) encryption
Threats that directly target applications can pass through most enterprise defenses, historically built to provide network-layer protection.
Threat developers exploit various methods to infiltrate networks, including:
- Many of today’s threats are built to run covertly on networks and systems.
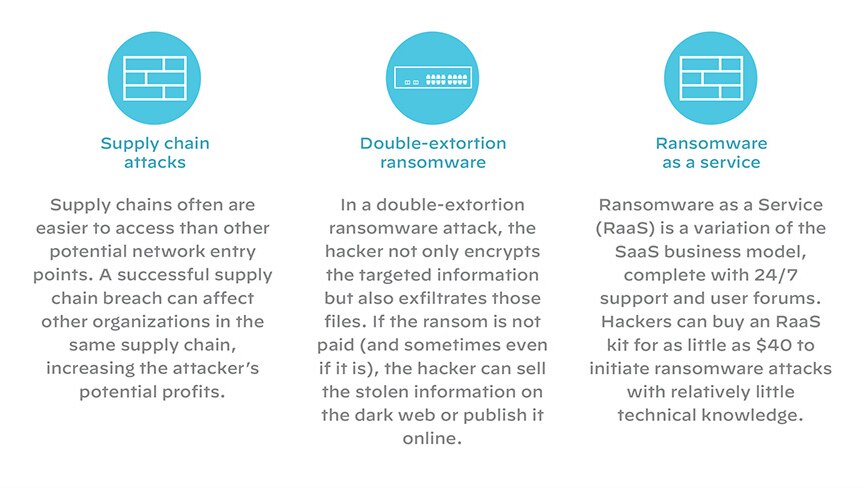
Figure 2: Recent trends in ransomware attacks
Such threats are designed to quietly collect sensitive data and remain undetected indefinitely. This approach preserves the value of stolen data and enables repeated use of the same exploits and attack vectors.
Threats to hybrid cloud environments include:
- Ransomware
- Credential theft
- Domain Name System((DNS)-based attacks)
- Targeted “low-and-slow” attacks
- Advanced persistent threats (APTs)
Hybrid Cloud Security Architecture
Hybrid cloud security must be ubiquitous. It starts with NGFWs, which identify and control applications, data, and workloads. While hardware firewalls are important components of on-premises environments, software firewalls are particularly helpful with hybrid cloud security.
Software firewalls include:
- Virtual firewalls (also known as cloud firewalls or virtualized NGFWs)
*Virtual firewalls are network security solutions designed specifically for environments in which deploying hardware firewalls is difficult or impossible. This includes public and private cloud environments; software-defined networks and software-defined wide area networks. - Container firewalls
- Managed service firewalls
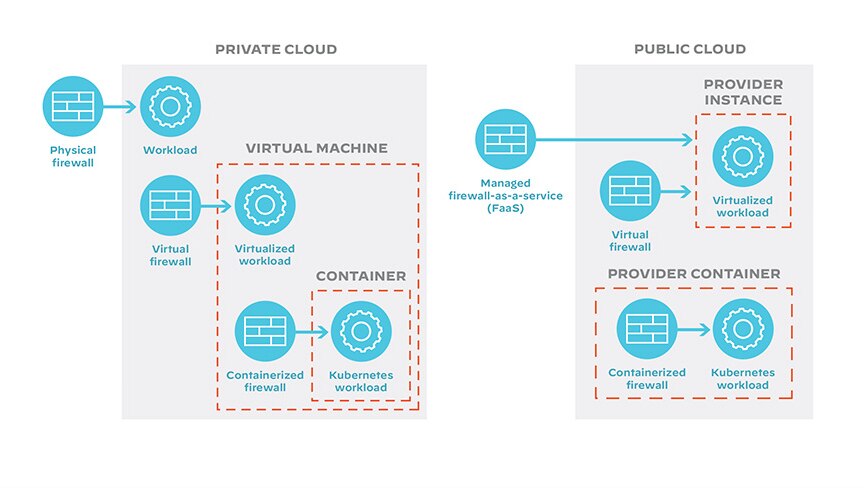
Figure 3: Software firewalls in hybrid/multicloud security
To tie these components together and secure hybrid environments, organizations should prioritize these capabilities:
- Consistent security in physical and virtualized form factors
- Segment business applications using Zero Trust principles
- Centrally managed security deployments and streamlined policy updates
Hybrid Cloud Security Best Practices
Hybrid cloud computing has become a popular approach for organizations looking to leverage the benefits of both public and private cloud environments. However, the security risks of hybrid cloud can be complex and multilayered, requiring a comprehensive and dynamic approach.
With the growing adoption of hybrid cloud solutions, it has become increasingly important to implement effective security measures that mitigate the risk of cyberthreats and data breaches. However, securing a hybrid cloud environment requires careful planning, solution selection, and implementation.
The following sections describe the critical best practices hybrid cloud security solutions should incorporate.
Safe Enablement of Applications in the Hybrid Cloud
- Security admins must be able to set policy to allow certain types of applications and functions while denying others.
- Network security platforms for hybrid cloud environments must classify traffic by application on all ports by default.
- Security teams must have complete visibility into application usage.
Identify Users and Enable Appropriate Access
- Users should be identified beyond Internet Protocol (IP) address.
- User and group information must be directly integrated into the technology platforms that secure hybrid cloud environments. (This is because when users move around, policy doesn’t follow them.)
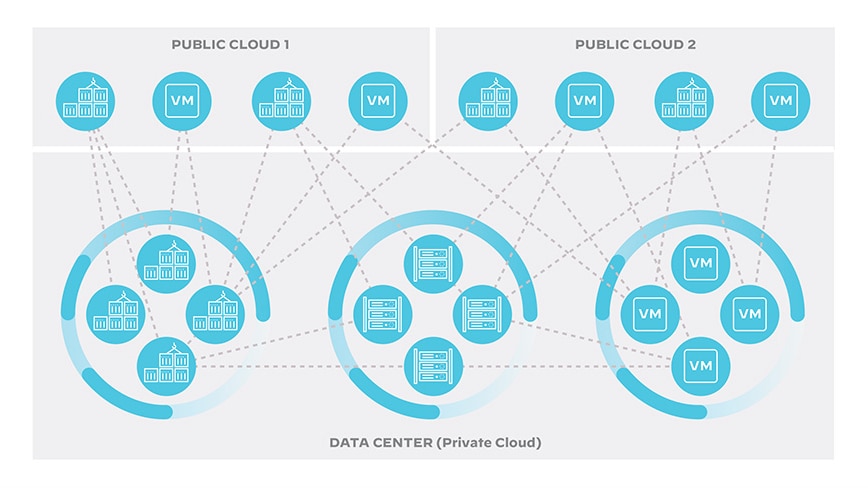
Figure 4: Hyperconnected enterprise infrastructure
Comprehensive Threat Protection
- Exerting application-level control between workloads reduces the threat footprint in the data center. So does segmenting traffic based on Zero Trust principles.
- Network security solutions should provide the ability to:
- Directly analyze unknown executables for malicious behavior
- Automatically block known threats
- Automatically analyze and counter unknown threats
- Look for threats at all points within the cyberattack lifecycle
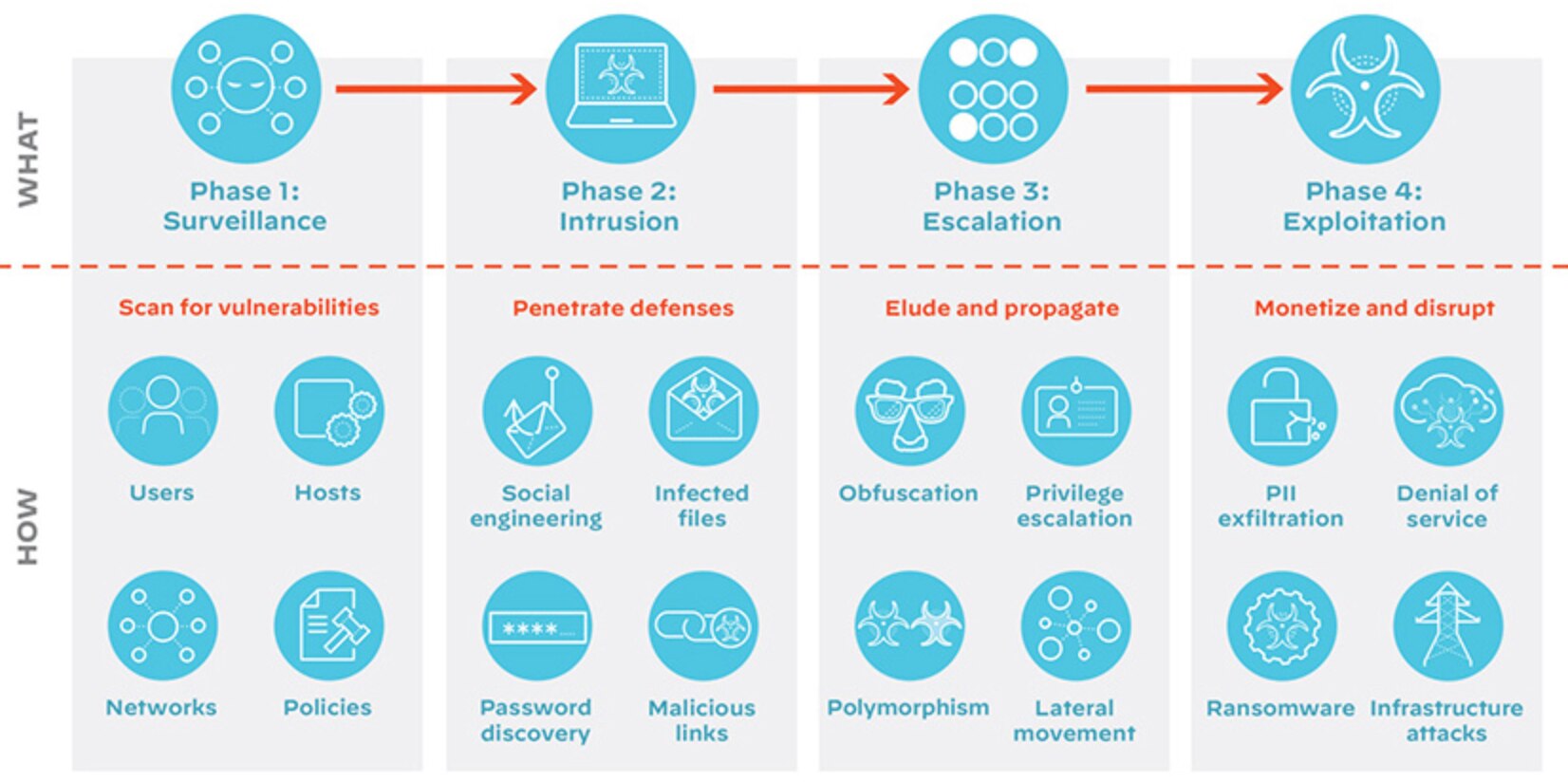
Figure 5: Anatomy of a modern cyberattack
Flexible, Adaptive Integration
- One of the key integration challenges in the data center is security design. A new paradigm that enables flexible, adaptive network security is needed. Networking flexibility helps ensure compatibility with practically any organization’s environment.
- Enabling integration depends on supporting a wide range of networking features and options, including:
- Port-based virtual local area networks (VLANs)
- The ability to integrate at the Open Systems Interconnection (OSI) Reference Model Layer 1 (Physical), Layer 2 (Data Link), or Layer 3 (Network)
- In addition, the network security solution should be able to turn on additional security features as security posture changes. It must also support multiple hypervisor types and potentially SDN-driven provisioning.
Secure Access for Mobile and Remote Users
- The mobile workforce requires access to applications from geographically disparate locations beyond the network. Consequently, mobile and remote users must be protected.
- This requires consistent security. Therefore, network security platforms must:
- Enable required levels of visibility, threat prevention, and security policy enforcement.
- Protect distributed across physical and virtualized workloads spanning hybrid cloud environments.
- Deliver secure access for mobile/remote users to the data center and cloud
- Address the use of endpoint devices other than standard corporate-issued equipment.
One Comprehensive Policy, One Management Platform
Aim to simplify security with a single management platform that can “do it all,” including:
- Scale firewall onboarding.
- Maintain consistent security policies.
- Deploy emergency change across thousands of firewalls.
Cloud Readiness
To succeed in hybrid cloud security, solutions must deliver on the following cloud-first objectives:
- Extend policy consistently from network to cloud.
- Stop malware from accessing and moving laterally within the cloud.
- Simplify management.
- Minimizes the security policy lag as virtual workloads change.
- Protect resident applications and data with the same security posture established on the physical network.
- Support diverse cloud and virtualization environments (including major public cloud providers and virtualized private clouds).
- Integrate with native cloud services and automation tools.
- Automate provisioning of network security capabilities in line with orchestration elements of the hybrid environment.
Automation
Security teams often rely on excessive manual processes for daily operations. Manual security slows mitigation, increases the chance for error, and is difficult to scale.
By using precise analytics to drive automation, security teams are given the power to:
- Operate security best practices like Zero Trust.
- Streamline routine tasks.
- Focus on business priorities (like application delivery, improving processes, or hunting for threats).
There are three areas where automation is key in a hybrid cloud environment:
- Workflow automation
- Policy automation
- Security automation
A firewall platform must incorporate machine learning ML) and automation to protect against known and unknown threats, including ransomware, cryptoworms, cryptojacking and more.
Threats to enterprise data center and hybrid cloud environments include:
- Ransomware
- Credential theft
- Domain Name System (DNS)-based attacks
- Targeted “low-and-slow” attacks
- Advanced persistent threats (APTs)