-
- What is an ICS?
- Why is ICS security important?
- How does ICS security work?
- What is the role of IT/OT convergence in ICS security?
- What kinds of cyberthreats commonly impact ICSs?
- What are the main ICS security challenges?
- What are the primary ICS protocols?
- How to achieve ICS security step-by-step
- 10 ICS security best practices
- What are the primary ICS security frameworks, standards, and regulations?
- What is ICS supply chain security?
- 2025 ICS security market and trends
- What are the different types of industrial control systems?
- What are the components of an industrial control system?
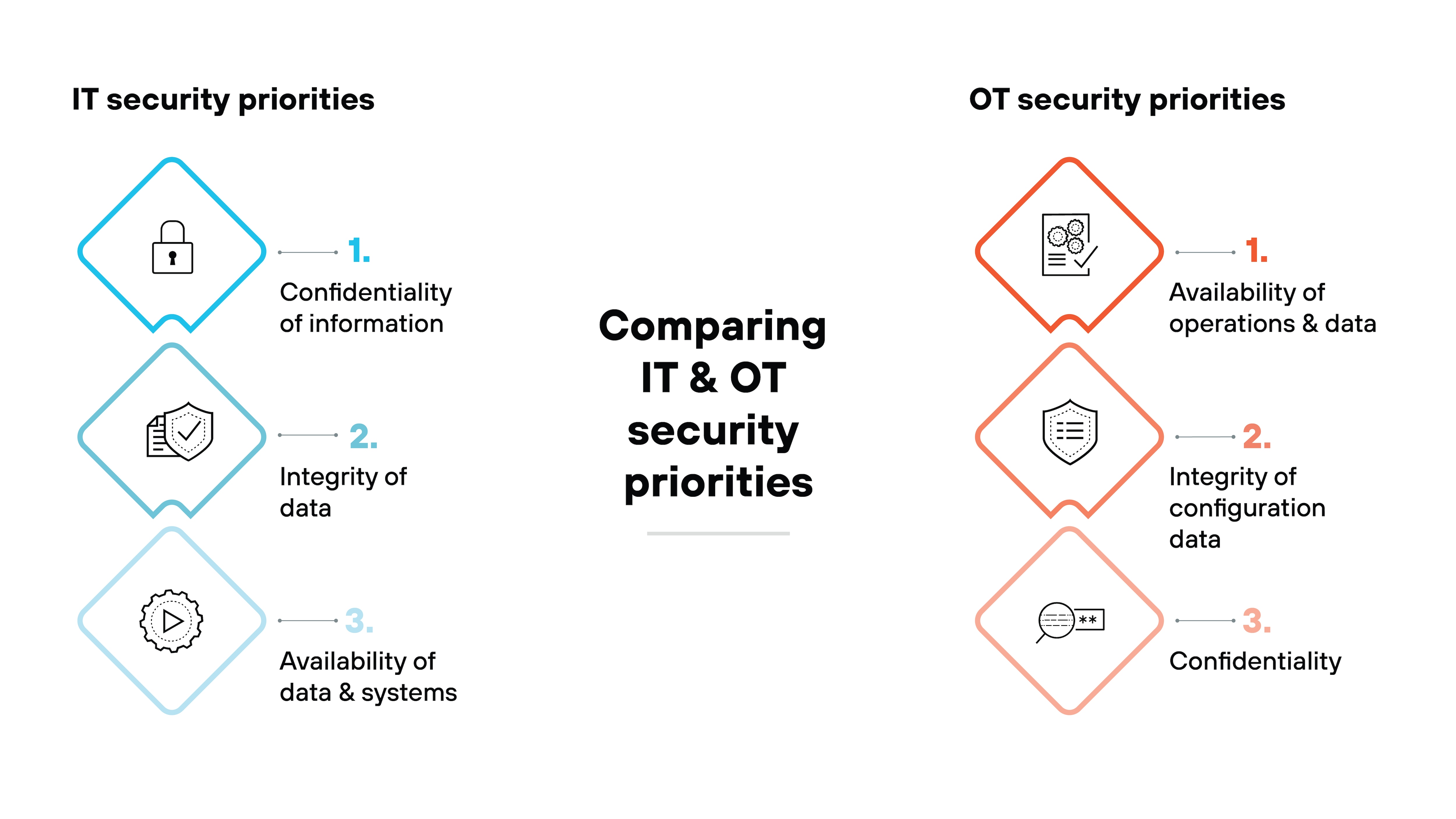
- What are the differences between OT, ICS, SCADA, and DCS?
- How does ICS security compare with OT and SCADA security?
- What is the history of industrial control systems?
- ICS security FAQs
Table of contents
- What Is the Difference Between IoT and OT Security?
- What is OT security?
-
What Is IT/OT Convergence?
- What Is OT?
- What Is the Difference Between IT and OT?
- How and Why IT and OT Are Converging
- Types of IT/OT Convergence
- The Role of IoT and IIoT in IT/OT Convergence
- IT/OT Security Convergence
- Impacts of IT/OT Convergence on ICS Security
- IT/OT Convergence Benefits
- IT/OT Convergence Challenges
- IT/OT Convergence Use Cases and Examples
- IT/OT Convergence Best Practices
- IT/OT Convergence FAQs
-
What Is Internet of Medical Things (IoMT) Security? Overview
- What is the Internet of Medical Things (IoMT)?
- Why is IoMT security important?
- What are some examples of IoMT devices?
- What are the primary IoMT security risks and challenges?
- What are the most common IoMT attack methods?
- How does IoMT security work?
- How does IoMT security fit into a broader healthcare cybersecurity strategy?
- What frameworks, standards, and regulations guide IoMT security?
- IoMT security FAQs
- What Is Critical Infrastructure? Why Does Critical Infrastructure Security Matter?
-
The Impact of IT-OT Convergence on ICS Security
-
Building Secure Smart Cities in the Age of 5G and IoT
- IT vs. OT Security | What Are the Differences?
- What Are the Differences Between OT, ICS, & SCADA Security?
- What Is the Difference Between IT and OT? | IT vs. OT
-
How to Secure IoT Devices in the Enterprise
-
What Is 5G Security? A Primer on 5G Network Security
- What is the difference between 4G and 5G security?
- What makes 5G networks harder to secure?
- What exactly needs protecting in a 5G network?
- What are the biggest 5G security risks?
- What security features are built into 5G?
- Who's responsible for keeping 5G secure?
- Which environments demand the strongest 5G security?
- What's next for 5G security?
- 5G security FAQs
-
What Is the Purdue Model for ICS Security? | A Guide to PERA
- How does the Purdue Model for ICS Security work?
- What are the Purdue Model layers?
- What are industrial control systems?
- What are the main ICS architecture security challenges?
- What kinds of cyberthreats commonly impact ICS?
- What is the history of the Purdue Model?
- Examining the Purdue Model’s role in modern ICS security
- Purdue Model for ICS Security FAQs
What Is ICS Security? | Industrial Control Systems Security
16 min. read
Table of contents
ICS security focuses on protecting industrial control systems, which combine hardware and software to manage machinery and processes in various industries. These systems are critical to the operation of power plants, manufacturing facilities, and other key infrastructure.
ICS security ensures the safe and continuous operation of these environments by protecting against cyber threats that could compromise data or disrupt operations. Security in ICS isn't just digital—it also includes physical safety measures to protect the machinery and the environment where ICSs operate.
What is an ICS?
An industrial control system (ICS) refers to a combination of hardware and software that manages and automates industrial processes.
Industrial control systems are used across a wide range of industries, including:
- Manufacturing
- Chemical processing or production
- Oil processing
- Telecommunications
- Food and beverage production
- Automotive
- Pharmaceuticals
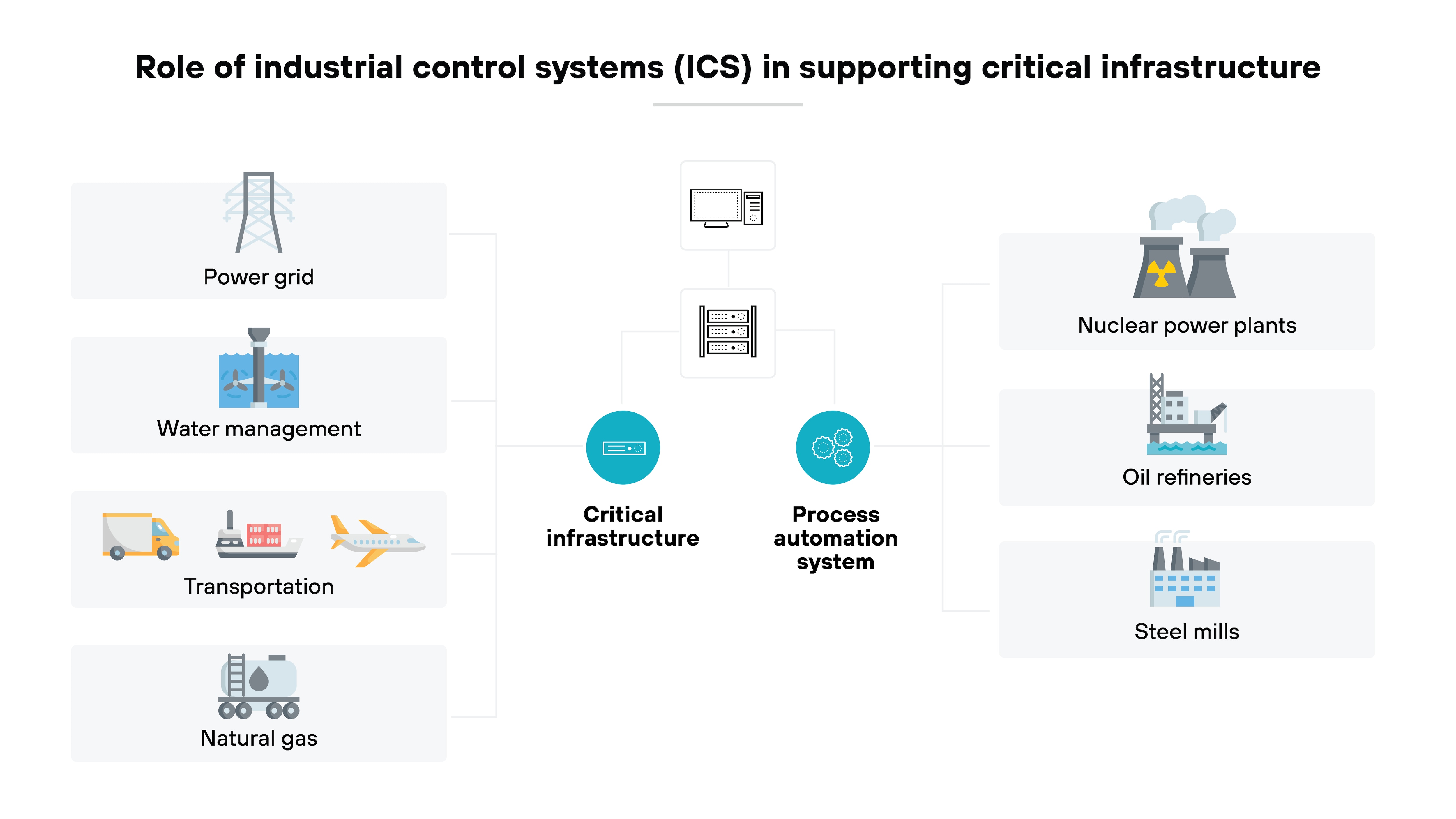
Additionally, ICSs support critical infrastructure, such as:
- Electrical grids
- Public transportation
- Water treatment facilities
- Oil and gas pipelines
An ICS includes devices such as sensors, control systems, and networks that work together to ensure smooth operations. They can range from small, localized systems using programmable logic controllers (PLCs) to large systems like supervisory control and data acquisition (SCADA) that manage operations across wide geographic areas.
Each ICS is tailored to the needs of the specific industry it supports.
Here’s what it looks like:
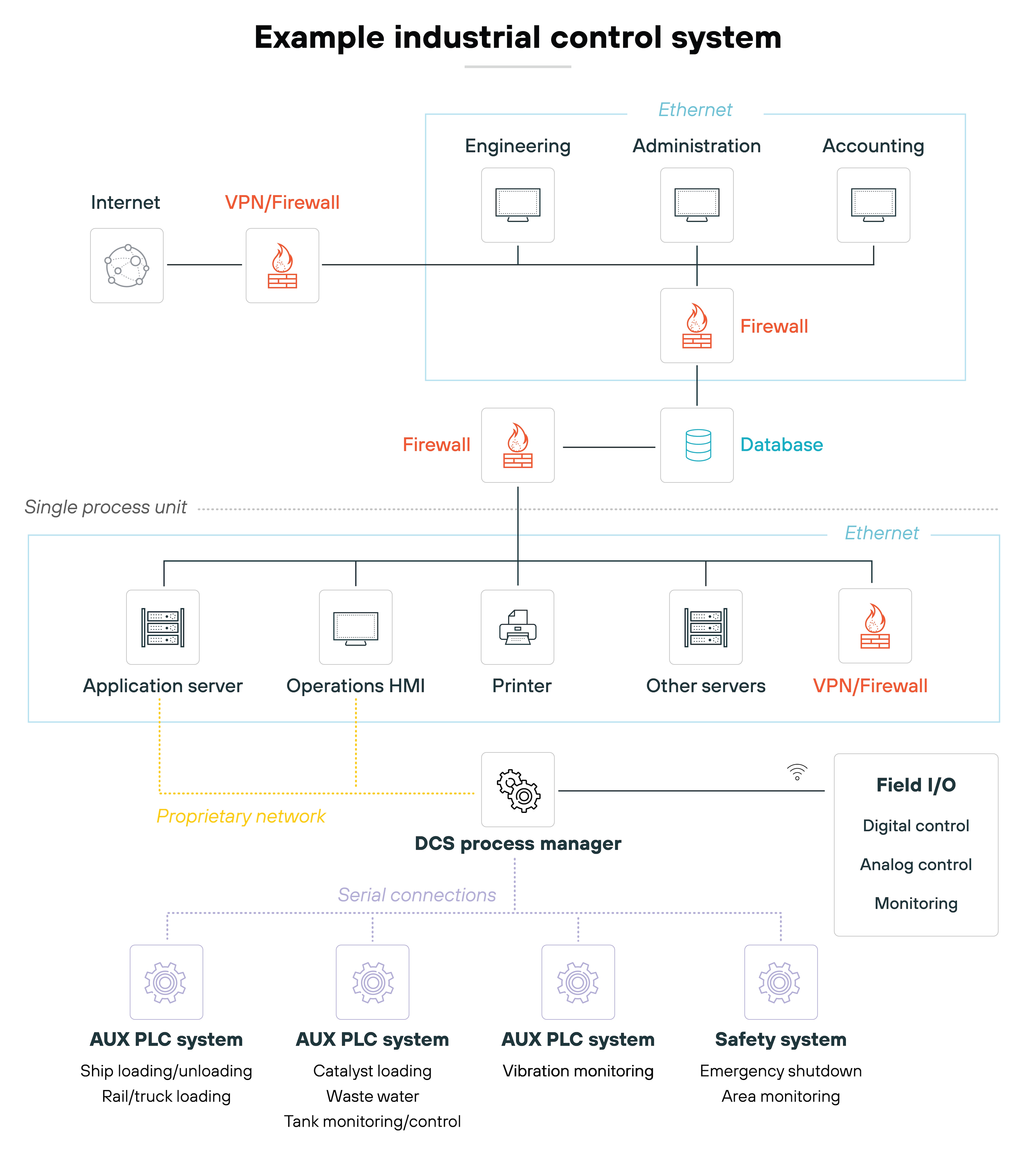
ICSs operate by receiving data from sensors, processing it, and then triggering commands to control the machinery or processes involved. The objective is to automate and optimize industrial tasks while maintaining safety and efficiency.
Because industrial control systems are critical to industrial infrastructure, they require strong security measures to protect against potential cyber threats and system malfunctions.
Each ICS is designed to manage specific tasks electronically. The exact function of an ICS depends on its configuration and the industry it serves.
Why is ICS security important?
ICS security is important because industrial control systems (ICS) play a crucial role in managing the operations of critical infrastructure.
More specifically, ICS security protects essential services from disruptions that could impact public safety and the operations of the organizations managing these systems. It helps prevent failures that could result in service outages or physical harm to workers and the public.
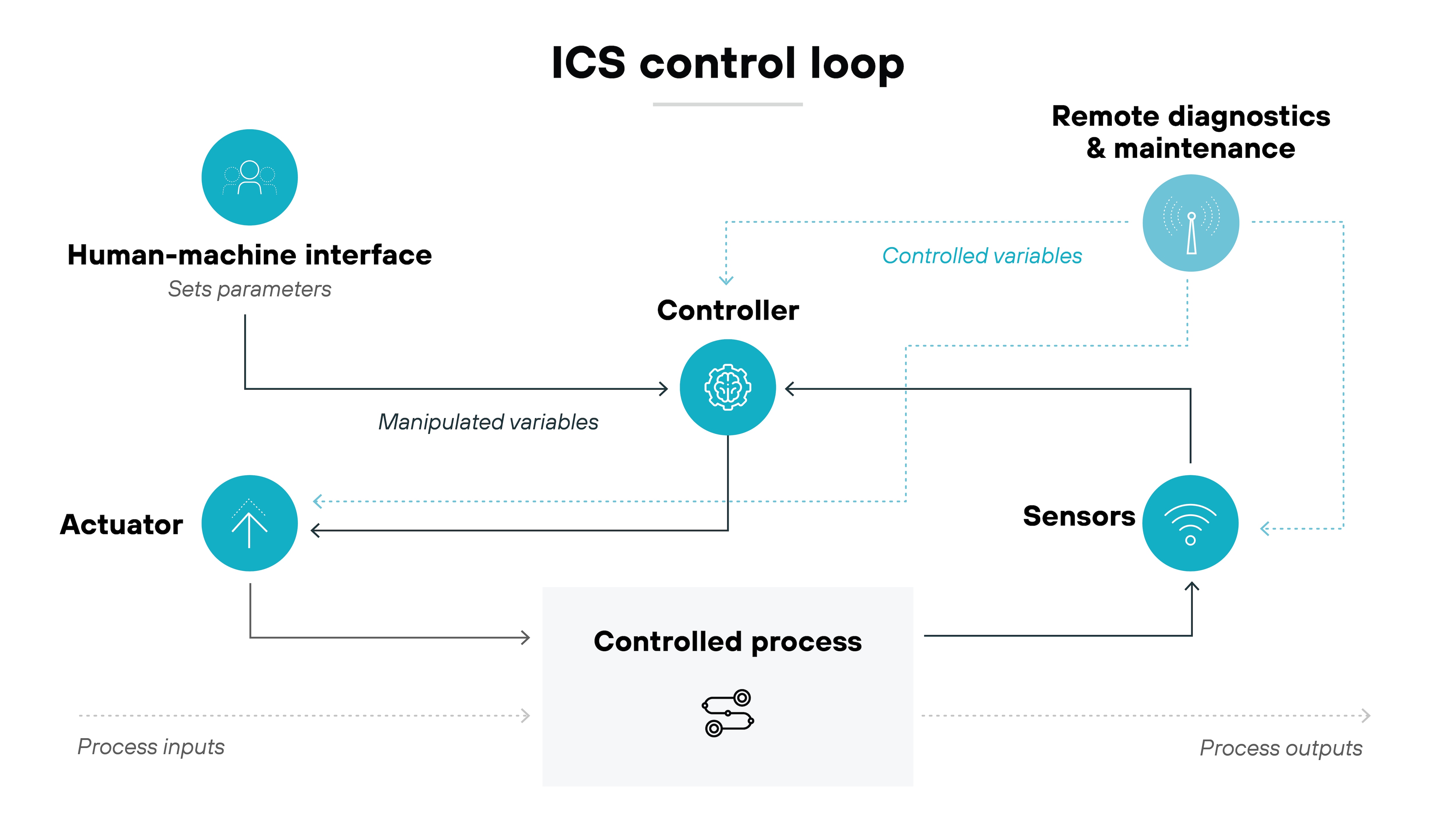
Essentially, ICS security is about maintaining operational continuity and safety.
Without proper safeguards, cyber incidents can lead to significant downtime, causing severe financial losses and damaging an organization's reputation.
Beyond financial risks, there's also the threat of physical damage to infrastructure if a system is compromised.
There’s also effective ICS information security to consider. Unauthorized access to sensitive operational data could result in manipulation of the systems, putting the organization at risk.
By maintaining strong security measures, companies can ensure operations run smoothly, keeping both their systems and the people relying on them safe.
In summary, ICS security is essential to protect critical infrastructure from cyber threats, ensure operational continuity, and maintain public and worker safety.
How does ICS security work?
ICS security ensures that critical industrial processes remain safe, operational, and protected from cyber threats.
At its core, an ICS security program focuses on safeguarding both the physical and digital components of control systems—making sure the communication between devices is secure, and operational data is accurate.
Here’s how it works:
- Network segmentation: ICS networks are often segmented from corporate and external networks. This reduces the attack surface and limits the potential damage that can be caused by a cyber intrusion.
- Intrusion detection and prevention systems (IDPS): ICS security relies on continuous monitoring to detect suspicious behavior or unauthorized access attempts. In other words, IDPS helps catch any malicious activity early, allowing for swift responses to prevent further damage.
- Role-based access control (RBAC): Access to ICS environments is restricted based on user roles and responsibilities. This way, only authorized personnel can access specific systems or data, reducing the risk of insider threats or accidental damage.
- Encryption and secure communication protocols: Secure data exchange between ICS components is essential. Encryption helps protect data as it moves between devices. Which prevents unauthorized parties from intercepting and tampering with critical information.
- Patch management: Keeping ICS software and firmware up to date is crucial. Timely patches close vulnerabilities that cyber attackers might exploit. It’s a proactive measure that minimizes the risk of known security gaps being used against ICS environments.
ICS security also involves ongoing monitoring and incident response planning. Continuous oversight ensures that any security incidents are quickly identified and managed, minimizing downtime and maintaining the integrity of industrial operations.
What is the role of IT/OT convergence in ICS security?
IT/OT convergence, accelerated by the Industrial Internet of Things (IIoT), connects ICS devices with both IT and OT networks. While this improves operational efficiency, it also increases exposure to cyber threats. Sensors, devices, and human-machine interfaces (HMIs) linked to IT systems can become entry points for attackers, especially when internet-facing connections lack proper security.
Weak session management, unsecured communication protocols, and insufficient encryption in these systems make them vulnerable. Threat actors often exploit these gaps using malware, which can lead to denial-of-service (DoS) incidents, ransomware attacks, or even sabotage of critical infrastructure.
This is where ICS secure connectivity becomes vital. Implementing secure communication protocols and robust access controls helps mitigate risks and protect against attacks that could disrupt essential services or cause physical damage.
By securing IT/OT convergence, organizations can protect industrial operations and critical infrastructure.
| Further reading: The Impact of IT-OT Convergence on ICS Security
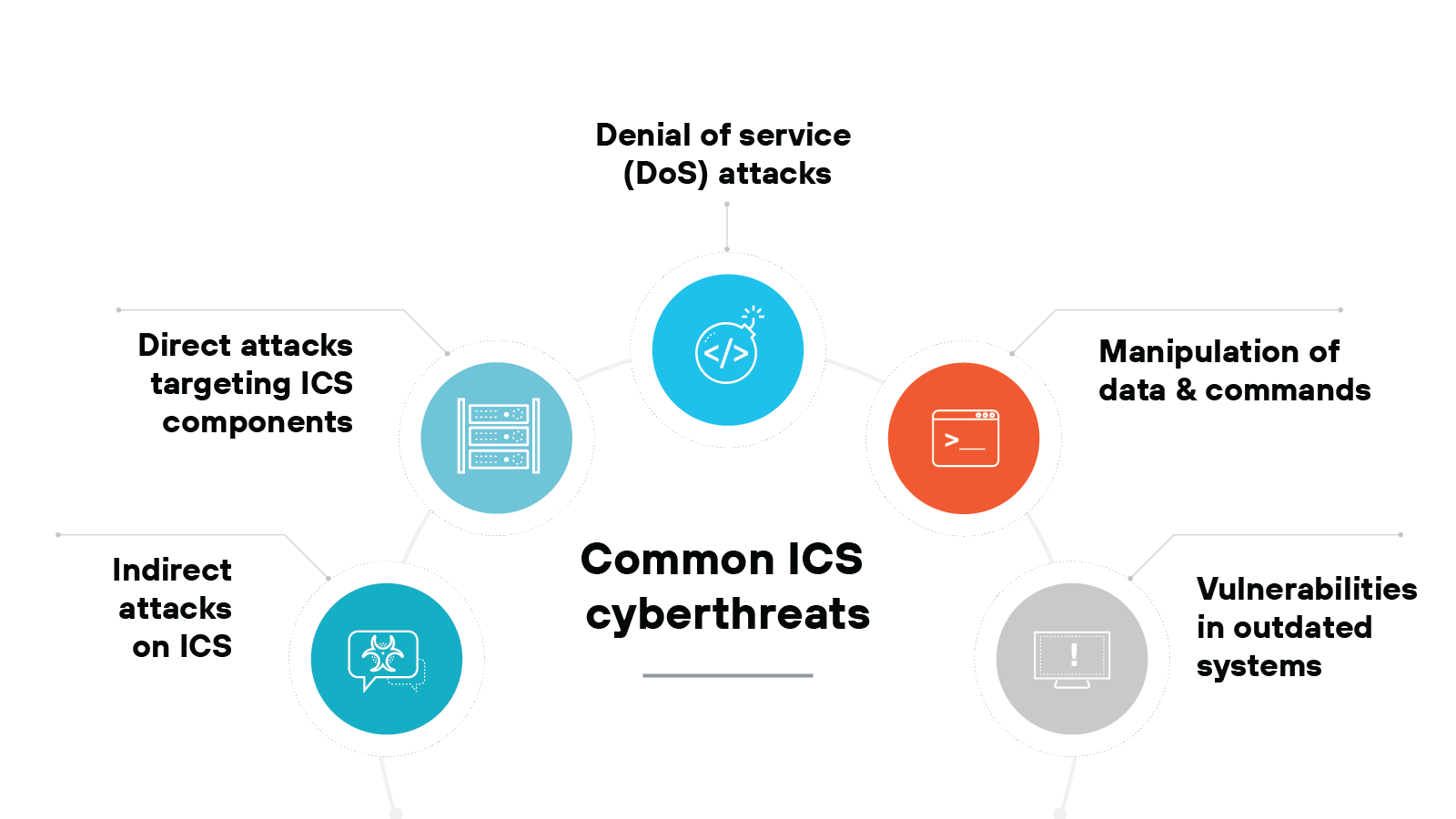
The frequency and complexity of ICS cyberthreats have grown significantly. Once isolated from external networks, ICSs are now more connected than ever, making them vulnerable to a range of cyberattacks.
While advancements in operational efficiency have benefited ICSs, they also come with cybersecurity risks. Achieving cyber security for ICS systems requires a thorough understanding of these threats.
Let’s take a closer look at the key threats ICS environments face:
- Indirect attacks on ICS
- Direct attacks targeting ICS components
- Denial of service (DoS) attacks
- Data and command manipulation
- Vulnerabilities in legacy systems
Indirect attacks on ICS
Some of the most common ICS cyberattacks are indirect, starting in the IT environment but ultimately affecting OT systems.
For instance, malware designed for traditional IT environments, like Windows, can breach a corporate network and spread to ICS systems.
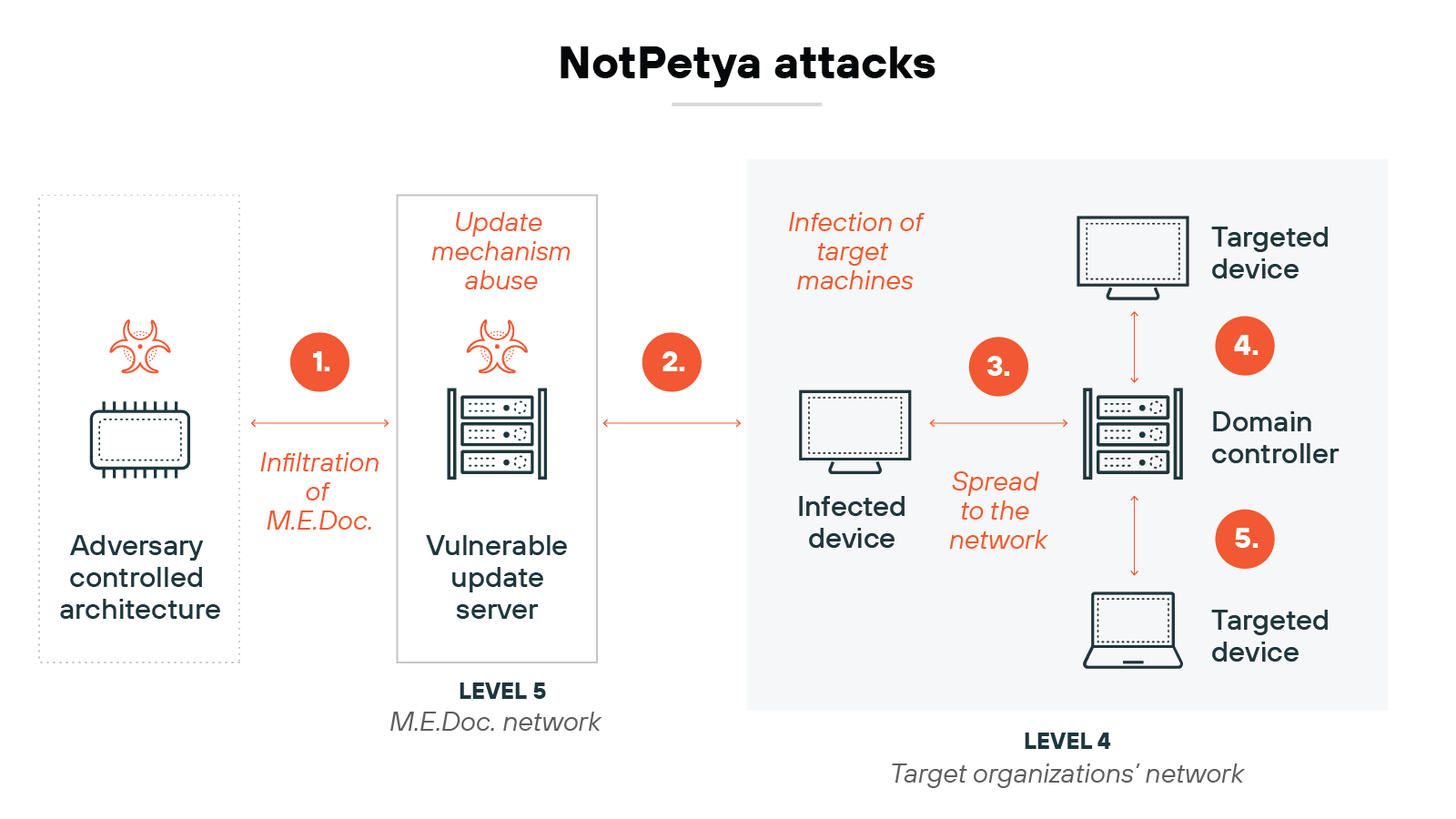
Example: The NotPetya ransomware attack in 2017 is a relevant example. Although it started in corporate IT environments, it spread quickly to OT operations, causing massive disruptions to industries, including those relying on critical infrastructure. This showed how vulnerable ICS can be if IT systems aren’t properly secured.
Direct attacks targeting ICS components
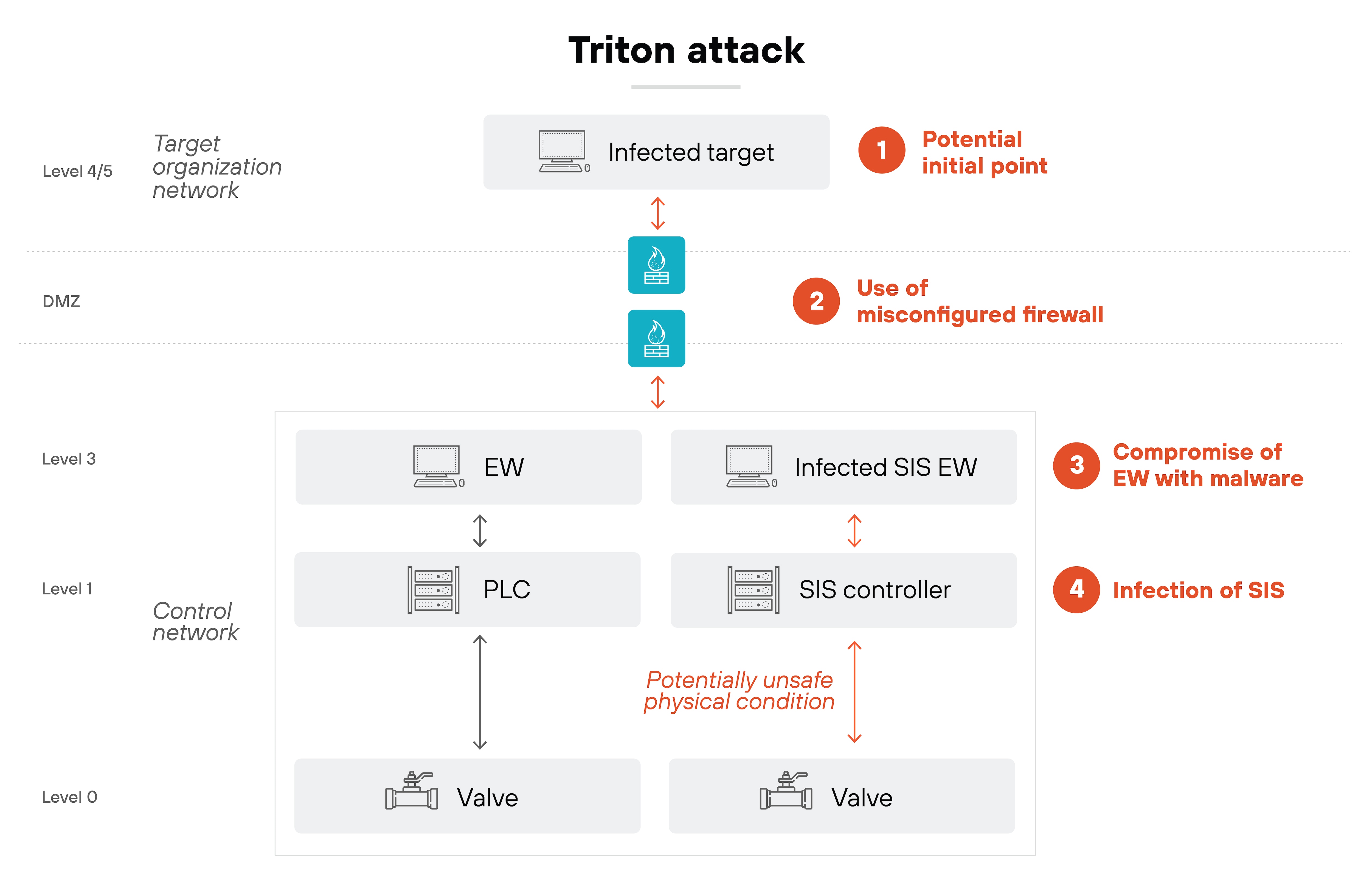
Unlike indirect attacks, direct attacks aim to target the actual components of ICS, such as PLCs or RTUs.
These attacks seek to disrupt the physical processes controlled by ICS, often leading to operational damage or compromised safety.
Example: The Triton/Trisis malware attack in 2017 targeted safety controllers from Schneider Electric’s Triconex system. The attackers tried to manipulate the safety mechanisms that could have disabled critical safety functions. Fortunately, the attack was halted before any real damage occurred, but it underscored the evolving nature of ICS threats.
DoS and DDoS attacks
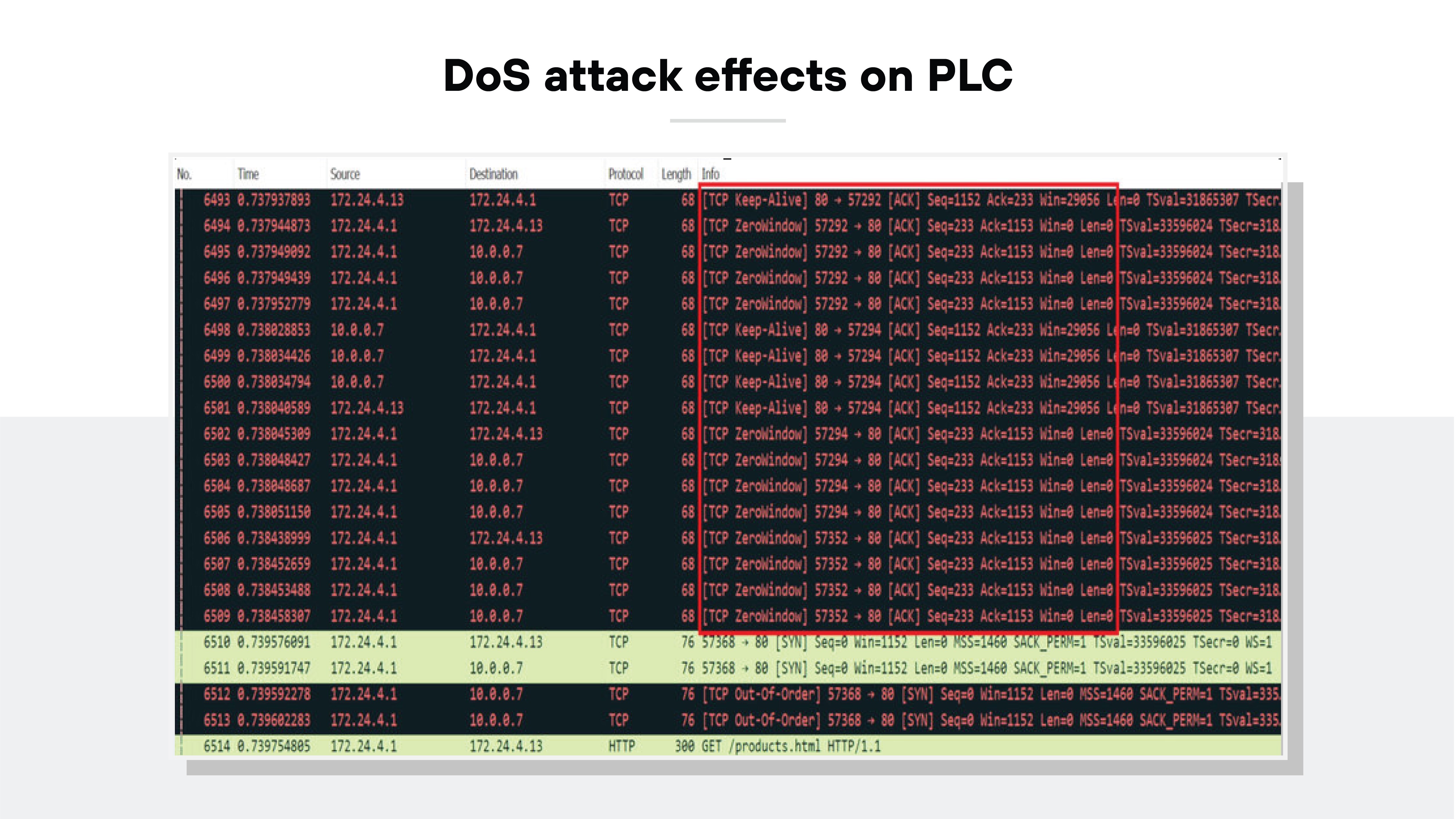
Denial of service (DoS) and distributed denial of service (DDoS) attacks work by overwhelming ICS networks with malicious traffic, causing disruption or total shutdown.
DoS attacks typically come from one source, while DDoS attacks use multiple compromised systems. Both types are disruptive and can lead to downtime in environments that depend on continuous operation, such as energy or water utilities.
Example: A 2018 study simulated DoS attacks against PLCs, revealing that the attacks caused significant delays in system responses—up to 5280 ms in some cases "Cyber Security in Industrial Control Systems: Analysis of DoS Attacks against PLCs and the Insider Effect" (Yılmaz et al., 2018). This shows how DoS attacks can impact the performance of critical ICS components, leading to operational delays or failures.
Manipulation of data and commands
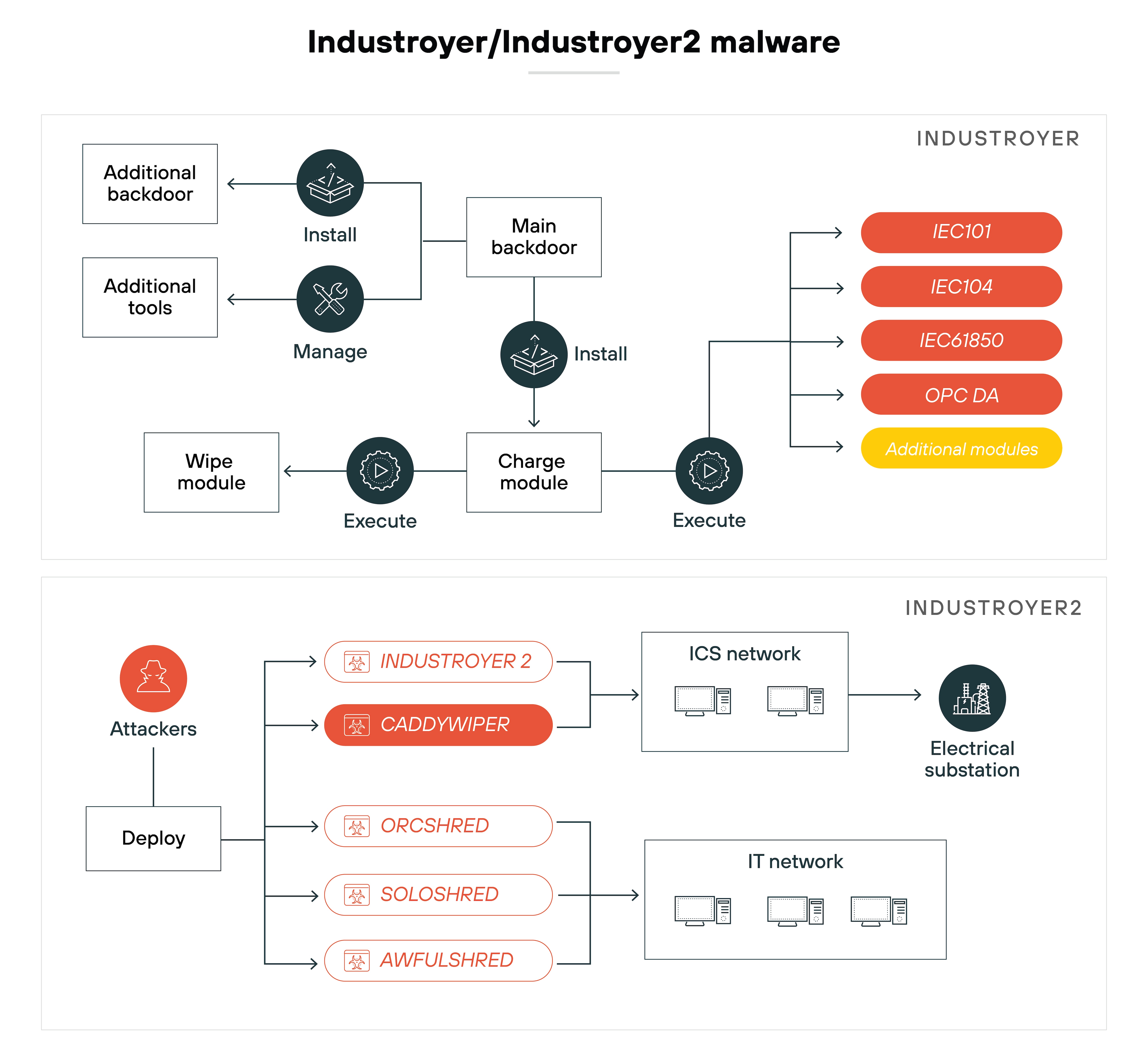
Cybercriminals can also inject false data into ICS or send malicious commands that operators may not notice immediately.
This type of attack is dangerous because the system could keep running on faulty data, causing inefficiencies, equipment damage, or safety risks. For instance, an attacker could manipulate the pressure in a pipeline, potentially causing it to malfunction or fail.
Example: The Industroyer malware, which targeted Ukraine’s power grid in 2016, manipulated data and sent unauthorized commands to RTUs. This led to power outages and significant disruptions, demonstrating how damaging data manipulation can be in an ICS environment.
Vulnerabilities in legacy systems
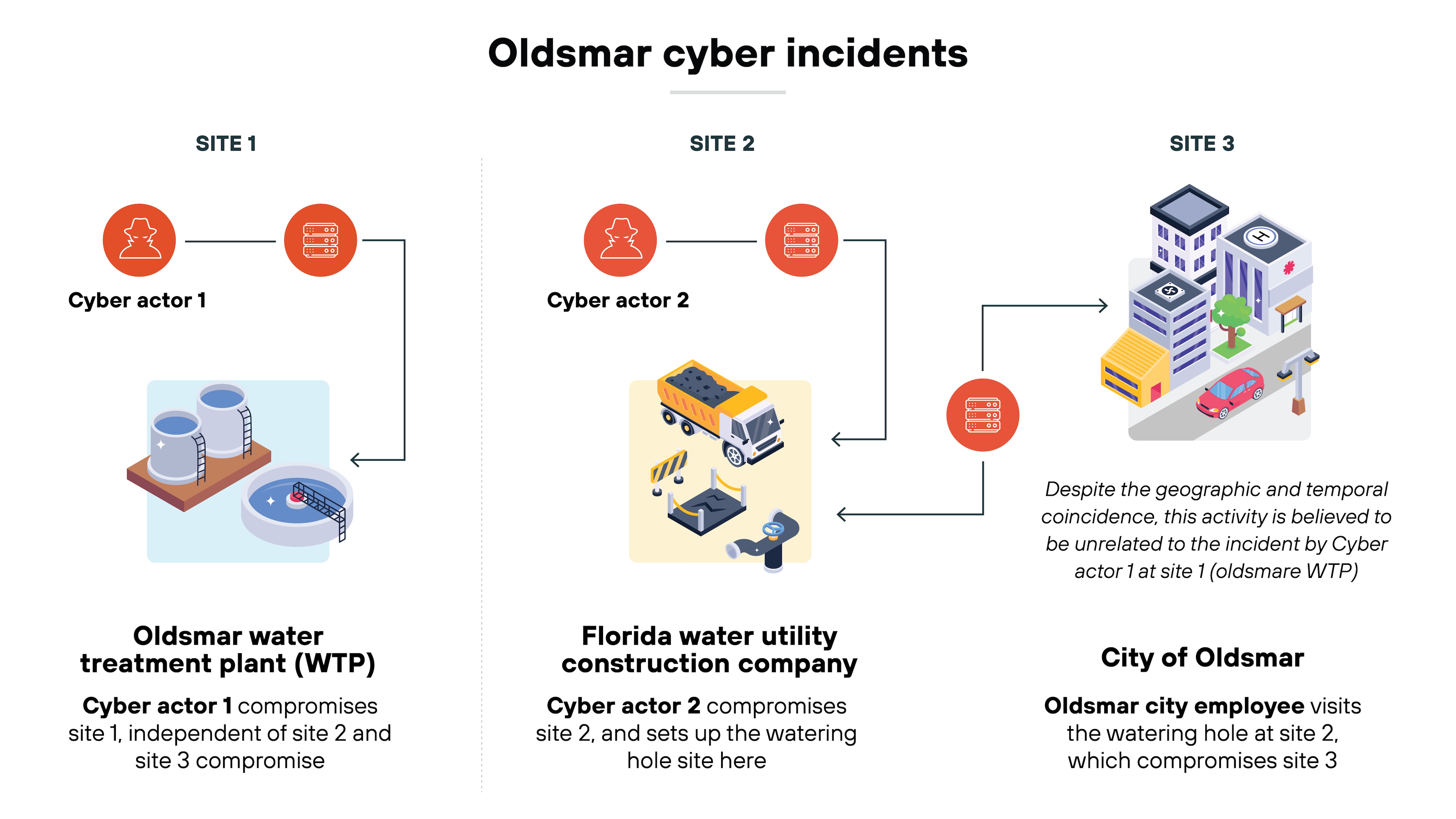
Many ICS still rely on legacy infrastructure that wasn’t designed to handle modern cybersecurity threats. These systems often run outdated software, making them an easy target for attackers.
Patching these systems can be tricky, as updates may disrupt the system’s functionality. This leaves many ICS environments exposed to attacks that exploit known vulnerabilities.
Example: In 2021, attackers gained access to the Oldsmar water treatment plant’s control systems, which were outdated and lacked proper security measures. They attempted to increase the level of sodium hydroxide in the water, which could have posed serious health risks. Thankfully, a quick-thinking operator caught the change in time to prevent any harm. This incident highlights how vulnerable legacy systems can be to serious attacks.
What are the main ICS security challenges?
Industrial control systems (ICS) present distinct security challenges due to their purpose, structure, and the environments in which they function.
Key ICS security challenges include:
- Real-time operational demands
- Outdated infrastructure
- Integration with IT systems and the associated risks
- Environmental constraints
- Physical security
- Compliance with regulatory requirements
- Proprietary systems and protocols
- Supply chain risks
- Lack of standardization across systems
- Budget limitations
- Lack of cybersecurity expertise in ICS environments
Unlike traditional IT systems, ICSs are responsible for managing real-time processes that are vital to industries such as manufacturing, energy, and utilities. This adds multiple layers of complexity to securing these systems effectively.
Let’s take a closer look at the key ICS architecture security challenges.
Real-time operational demands
A primary challenge with ICS security stems from the need to meet real-time operational demands. ICS environments control physical processes where any delay can have serious consequences.
For example: If an ICS regulates the temperature of machinery or manages a power grid, any disruption or latency could lead to equipment damage, production loss, or even pose risks to public safety.
Like this:
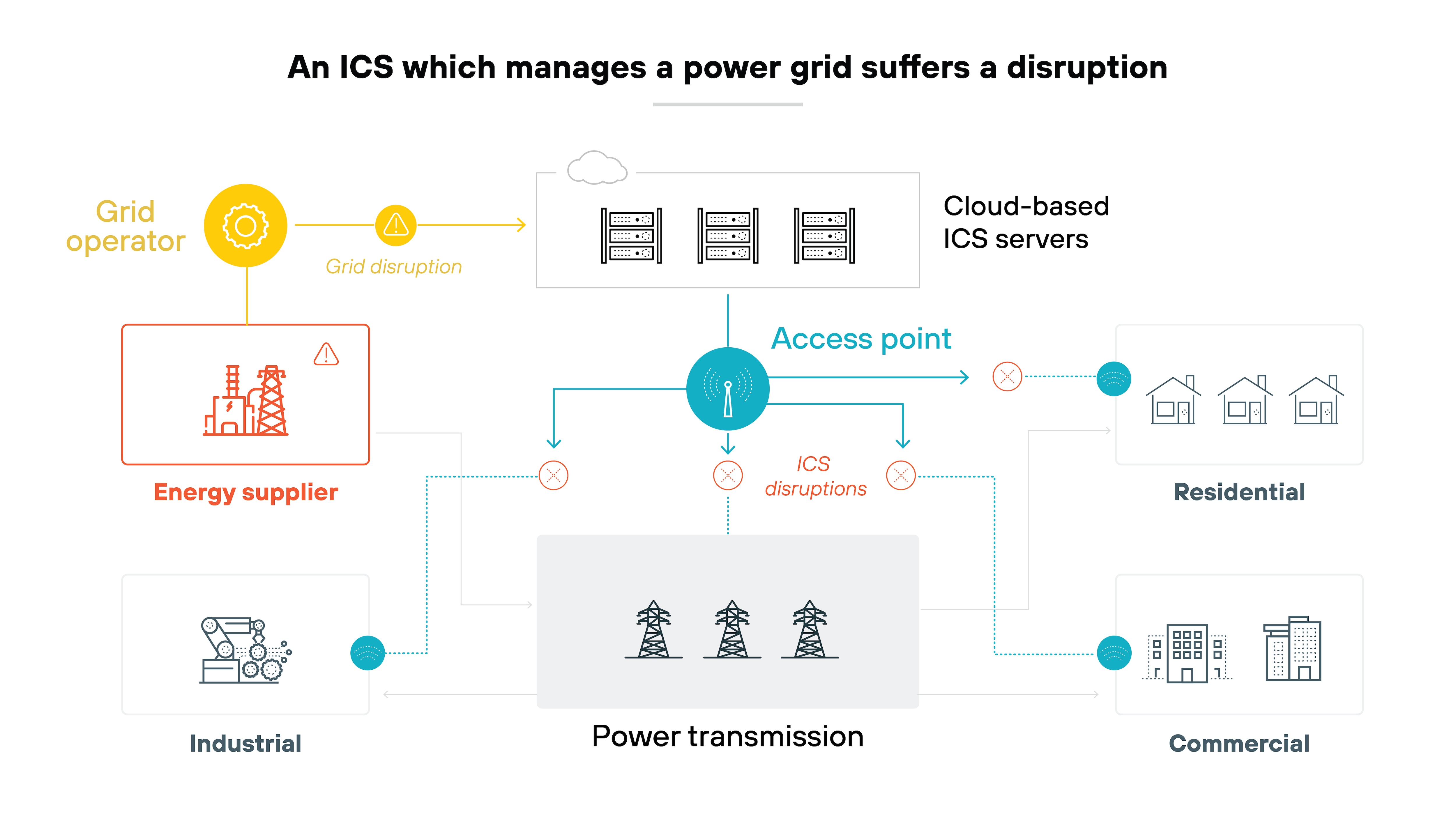
Security measures like patches or scans can potentially disrupt real-time operations. And that makes implementing security solutions more difficult than in conventional IT systems.
Outdated infrastructure
Many ICSs still rely on older infrastructure that wasn’t designed with modern cybersecurity in mind. When initially developed, ICSs were often isolated from the internet and protected from external threats through physical separation.
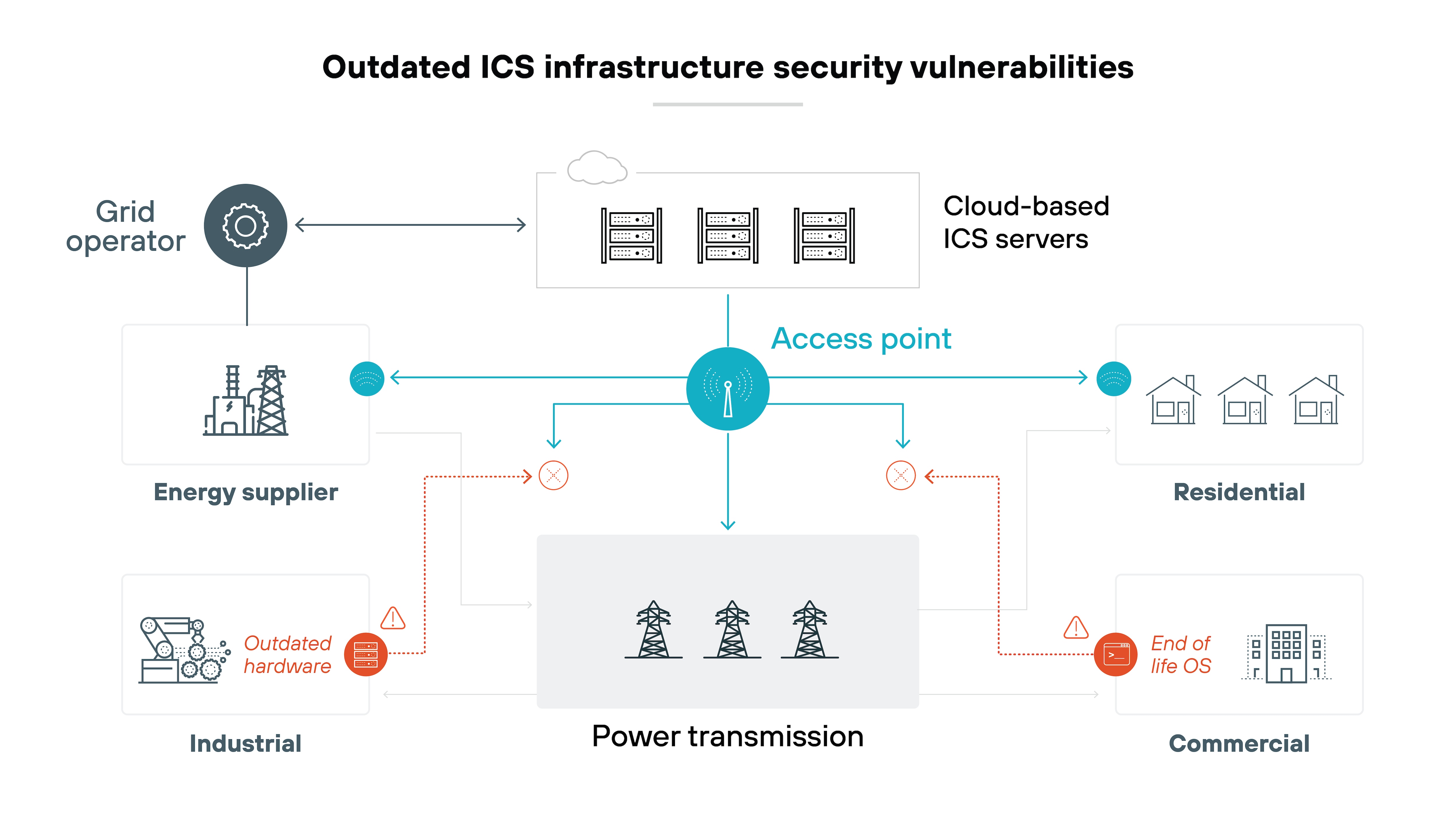
However: As organizations increasingly connect ICS to corporate networks for easier remote management and monitoring, legacy systems create significant vulnerabilities.
Older systems may not support current security protocols or updates. Retrofitting them with necessary ICS network security measures can be complex, expensive, or even impossible without complete system overhauls.
OT/IT convergence and the associated risks
Typically managed by separate teams, the convergence of IT and OT systems requires substantial reorganization and a shift in management approaches.
The merging process demands a more efficient exchange of information but also significantly increases the cybersecurity attack surface.
Vulnerabilities in IT systems, often more exposed to cyber threats due to their connectivity, can lead to potential compromises in ICS environments. The interconnectedness requires a strategic approach to cybersecurity that encompasses both IT and OT. One that aims to protect essential services from disruption while maintaining system integrity across different technological platforms.
Environmental constraints
Industrial environments are often harsh, subject to factors like electrical noise, dirt, or extreme temperatures. These conditions impact how and where security solutions can be deployed.
Traditional network security tools, like firewalls or intrusion detection systems, are typically built for cleaner, more controlled environments, making them harder to implement in ICS settings.
Plus, the need for continuous operation in industrial environments means there’s little room for downtime. Which makes regular security maintenance or updates a challenge.
Compliance with regulatory requirements
Compliance with regulatory requirements in ICS environments is vital for protecting critical infrastructure.
Standards like ISA/IEC 62443 specify procedures for securing industrial control systems and maintaining operational continuity. Operators have to continuously monitor and adapt to evolving standards to mitigate risks effectively and ensure safe operations.
Proprietary systems and protocols
ICS environments often use a variety of proprietary systems and communication protocols, complicating the application of standardized security practices.
Each vendor may have its own software, hardware, and protocols, making it difficult to integrate with standardized security solutions.
Additionally: Many ICS protocols—such as Modbus or DNP3—were developed with functionality as the priority, not security. As a result, these protocols may lack critical security features like encryption or authentication.
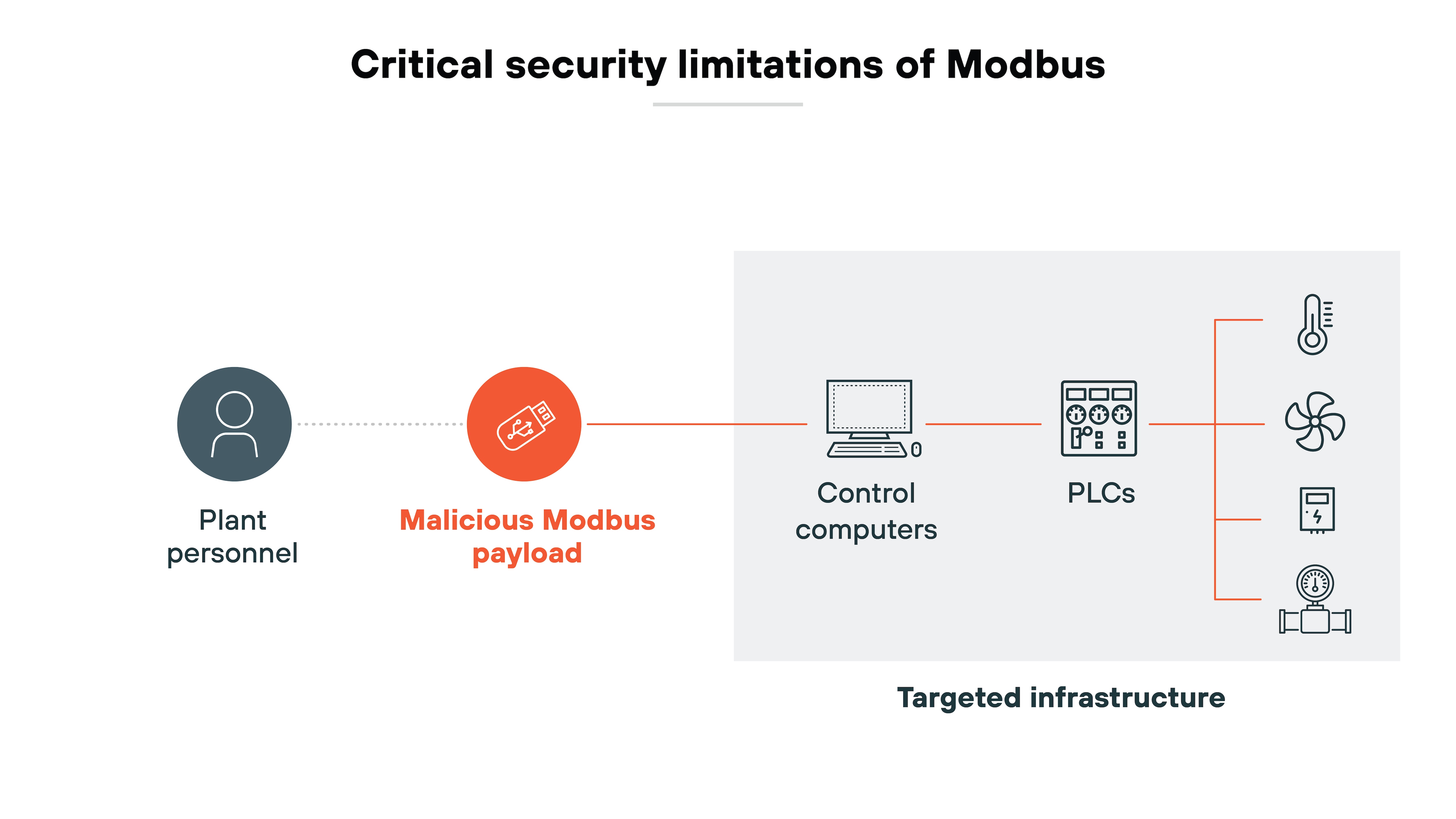
Lack of cybersecurity expertise in ICS environments
Another major challenge is the gap in cybersecurity knowledge among professionals managing ICS environments.
Engineers and operators who operate ICS environments are usually skilled in managing physical processes but may lack cybersecurity knowledge.
Conversely, cybersecurity professionals might not fully understand the nuances of industrial processes.
This gap can result in conflicting priorities, where ensuring the system runs smoothly might take precedence over implementing strong security measures.
What are the primary ICS protocols?
Industrial control systems differ significantly from IT systems. They require unique communication protocols that traditional IT frameworks cannot support.
Initially designed for serial communications, ICS protocols have adapted over the years to operate on TCP/IP networks using Ethernet. In typical ICS environments, specialized protocols enable real-time communication and command execution among various devices and interfaces.
For these reasons, ICS protocol security is an important part of securing ICSs overall.
Here are the protocols most widely used in typical ICS systems:
Common ICS protocol families
| Protocol family | Description | Common use | Encryption | Vulnerabilities |
|---|---|---|---|---|
| OPC | Standards for communication between industrial systems using Windows operating system technologies like OLE, COM, and DCOM. | Process automation and factory control systems. | TLS | Susceptible to DCOM-based attacks, Windows vulnerabilities. |
| Modbus | One of the oldest ICS protocols, supporting serial and TCP/IP communication between devices like PLCs. | Device communication in SCADA and process automation systems. | TLS (Modbus TLS) | Lacks native encryption and authentication, vulnerable to MitM attacks. |
| DNP3 | A three-layer protocol widely used in SCADA systems, especially for electric and water utilities. | Real-time data exchange in utility systems. | TLS (Secure DNP3) | Vulnerable to replay attacks, MitM, and lacks native encryption. |
| IEC 61850 | Designed for automation and control in electric substations. | Substation automation. | TLS | Requires external encryption methods, vulnerable without native security. |
| IEC 60870-5 | A protocol for telecontrol between substations and control centers in electrical engineering. | Power grid management. | None | Vulnerable to replay attacks and tampering due to lack of built-in security. |
| HART | Combines analog and digital signals for remote communication with field devices. | Process automation in remote field areas. | None | Susceptible to spoofing, lack of encryption, and MitM attacks. |
| Foundation Fieldbus | Protocol for automation in industries like oil, gas, and chemicals. | Process automation. | None | Lacks built-in security controls, vulnerable to cyber attacks. |
| Profibus | Used for communication between sensors, actuators, and controllers. | Device-to-device communication in process control environments. | None | Vulnerable to unauthorized access due to lack of authentication. |
| Profinet | Ethernet-based protocol for high-speed communication in industrial automation. | Real-time control in industrial environments. | TLS | Network-based attacks possible if encryption is not implemented. |
| BACnet | A protocol for building automation systems, including HVAC and access control. | Building automation. | TLS | Vulnerable to MitM attacks if security features are not enabled. |
| CIP | A protocol for control, synchronization, and configuration in industrial automation. | Industrial environments for secure communication. | None | Susceptible to denial-of-service (DoS) and replay attacks. |
| EtherCAT | High-performance Ethernet protocol for automation with fast update rates. | Automation requiring fast cycle times. | TLS/DTLS | Network-based attacks possible without encryption. |
| CAN | Protocol for communication between devices in automotive and embedded systems. | Automotive and embedded systems. | None | Lacks encryption, vulnerable to unauthorized access. |
| Sercos | Real-time protocol for motion control in automation. | Motion control in robotics and CNC machines. | None | Vulnerable to tampering due to lack of encryption. |

Securing industrial control systems (ICS) requires a clear, structured process.
The ICS security process should ensure that all potential security risks are mitigated while maintaining the integrity of the system's operations.
Below, we'll walk through each.
Step 1: Conduct an asset inventory
First, you need to identify what requires protection.
Start by cataloging all ICS assets, including hardware, software, and associated data. This includes any systems or devices that control operations, such as PLCs, HMIs, or SCADA systems.
A comprehensive inventory helps you understand the full scope of what’s at stake.
Step 2: Prioritize assets by criticality
Once you've completed your inventory, assign each asset a priority based on its importance to operations.
Note: Some systems, such as those that control critical infrastructure, will naturally require higher levels of security. Ranking assets helps in focusing resources where they are most needed.
Step 3: Identify security risks
At this stage, evaluate all potential vulnerabilities within your ICS environment.
These risks could stem from outdated software, lack of network segmentation, or insufficient authentication protocols.
Tip:
Don’t forget to include both internal and external threats, and factor in any human-related risks such as insider threats.
Step 4: Implement segmentation and network zoning
Divide your ICS network into zones to isolate critical systems from less sensitive ones. Segmenting networks limits the spread of potential intrusions.
Place key systems in high-security zones and limit their interaction with external networks. Use demilitarized zones (DMZs) where needed to separate IT and ICS environments.
Step 5: Harden access controls
Make sure that only authorized personnel can access critical ICS components. ICS security access control systems should enable multi-factor authentication, strong password policies, and limiting access based on user roles.
Additionally, assign separate credentials for accessing different security zones to reduce exposure in case of credential compromise.
Step 6: Update systems and patch vulnerabilities
It’s crucial to keep your ICS components up to date.
However: Since applying patches directly to operational environments can disrupt processes, always test patches in a non-production environment first. Once validated, apply them during scheduled maintenance windows.
Step 7: Secure remote access
Minimize remote access to your ICS network. Where it’s necessary, ensure connections are secure, time-limited, and operator-controlled.
Use strong encryption protocols for remote access.
Tip:
Consider employing jump servers or diodes to further protect ICS systems from unauthorized external access.
Step 8: Monitor and respond to threats
Implement continuous monitoring tools to detect any anomalies or threats within your ICS network. This includes monitoring IP traffic, user logins, and system activity.
Establish an incident response plan to quickly address any detected intrusions and minimize the impact on operations.
Step 9: Regularly test and validate security measures
Finally, regularly test your ICS security controls to ensure they are functioning as intended.
This includes conducting penetration testing, running security drills, and simulating cyberattacks to identify any gaps in your defenses.
Tip:
Ensure that your backup and recovery plans are also tested and ready to execute in the event of a compromise.
10 ICS security best practices
Industrial control systems require distinct cybersecurity measures to ensure the resilience of critical infrastructure. These best practices outline the fundamental strategies to mitigate risks while maintaining system availability.
1. Secure physical access
Physical access to ICS systems remains a critical threat vector. Attackers can introduce malware or manipulate systems if they gain unauthorized physical access.
Ensure all critical areas are restricted and monitored with physical security controls, including locks, surveillance cameras, and personnel verification systems.
2. Define your baseline
Developing a network baseline is key to detecting abnormal behavior.
By understanding the normal operations of your ICS network, you can identify deviations that may indicate cyber threats or attacks.
Tip:
Regularly update the baseline to adapt to changes in the environment and detect anomalies effectively.
3. Implement least privilege
Reduce permissions for all users, devices, and applications to the minimum necessary to perform their functions. This minimizes the risk of unauthorized access or misuse by malicious actors.
4. Master intrusion prevention systems (IPS)
Your ICS security solution should offer intrusion prevention to help protect ICS environments by detecting and blocking known threats. Since ICS systems often run legacy software that cannot be easily patched, IPS is critical for preventing exploits targeting unpatched vulnerabilities.
Tip:
Ensure that your IPS is regularly updated to protect against the latest threats.
5. Know your remote access risks
Remote access to ICS is often necessary but can introduce significant risks.
All remote connections should be closely monitored and encrypted, with multi-factor authentication enforced. Establish strict policies around who can access systems remotely and under what conditions.
Tip:
Disconnect inactive remote connections to reduce exposure.
6. Implement application allowlisting
Application allowlisting is an effective way to prevent unauthorized software from running on ICS systems.
By only allowing pre-approved applications to execute, you can minimize the risk of malware or malicious scripts compromising your system.
Tip:
Update allowlists frequently and tailor to your operational requirements.
7. Manage authentication carefully
Strong authentication mechanisms are essential in preventing unauthorized access to ICS systems.
Implement multi-factor authentication where possible and regularly rotate credentials. Ensure that user accounts are monitored for suspicious activity and restrict the use of shared or default passwords.
8. Reduce your attack surface
Minimizing the number of entry points that adversaries can exploit is a key ICS security best practice.
Isolate ICS networks from external and untrusted networks, disable unnecessary services, and close unused ports.
Don’t forget to limit real-time communication with external systems to the bare minimum necessary for operations, and employ one-way communication methods, like data diodes, when possible.
9. Build a defendable environment
Create security zones within your ICS network and restrict host-to-host communication pathways. This segmentation prevents attackers from easily spreading within your environment after initial entry.
Enclaving and network segmentation strategies can contain threats and reduce the costs of incident cleanup and recovery.
10. Monitor and respond
Effective ICS security requires continuous monitoring of traffic, user behaviors, and system operations.
Implement an ICS security system with comprehensive monitoring functionality to track abnormal activities and identify potential threats in real time.
Additionally, have an incident response plan in place that includes clear steps for isolating affected systems, restoring operations, and mitigating future risks.
What are the primary ICS security frameworks, standards, and regulations?
Industrial control systems operate under an array of cybersecurity frameworks, standards, and regulations designed to safeguard critical components from threats and ensure operational continuity.
ICS guidelines recognize the strategic importance of these systems. They establish robust processes for risk assessment, system integration, and security management.
Let’s take a high-level look at the primary ICS security frameworks, standards, and regulations:
ICS cybersecurity frameworks
| Standard | Description | Focus areas |
|---|---|---|
| NIST Cybersecurity Framework (CSF) | A voluntary framework for managing cybersecurity risks across sectors, with specific ICS guidance through NIST SP 800-82 to address ICS-specific risks and constraints. | Identifying ICS-specific risks, protection strategies, threat detection, and incident response. |
| C2M2 (Cybersecurity Capability Maturity Model) | Developed by the U.S. Department of Energy, this framework is designed to help organizations (particularly in the energy sector) evaluate and improve their ICS security maturity. | Evaluating cybersecurity capabilities and setting clear paths for improving ICS security over time. |
| CIS Controls for ICS | A tailored version of the Center for Internet Security’s (CIS) critical security controls designed specifically for industrial environments. | Practical guidelines for implementing cybersecurity measures in ICS environments, including asset inventory and access control. |
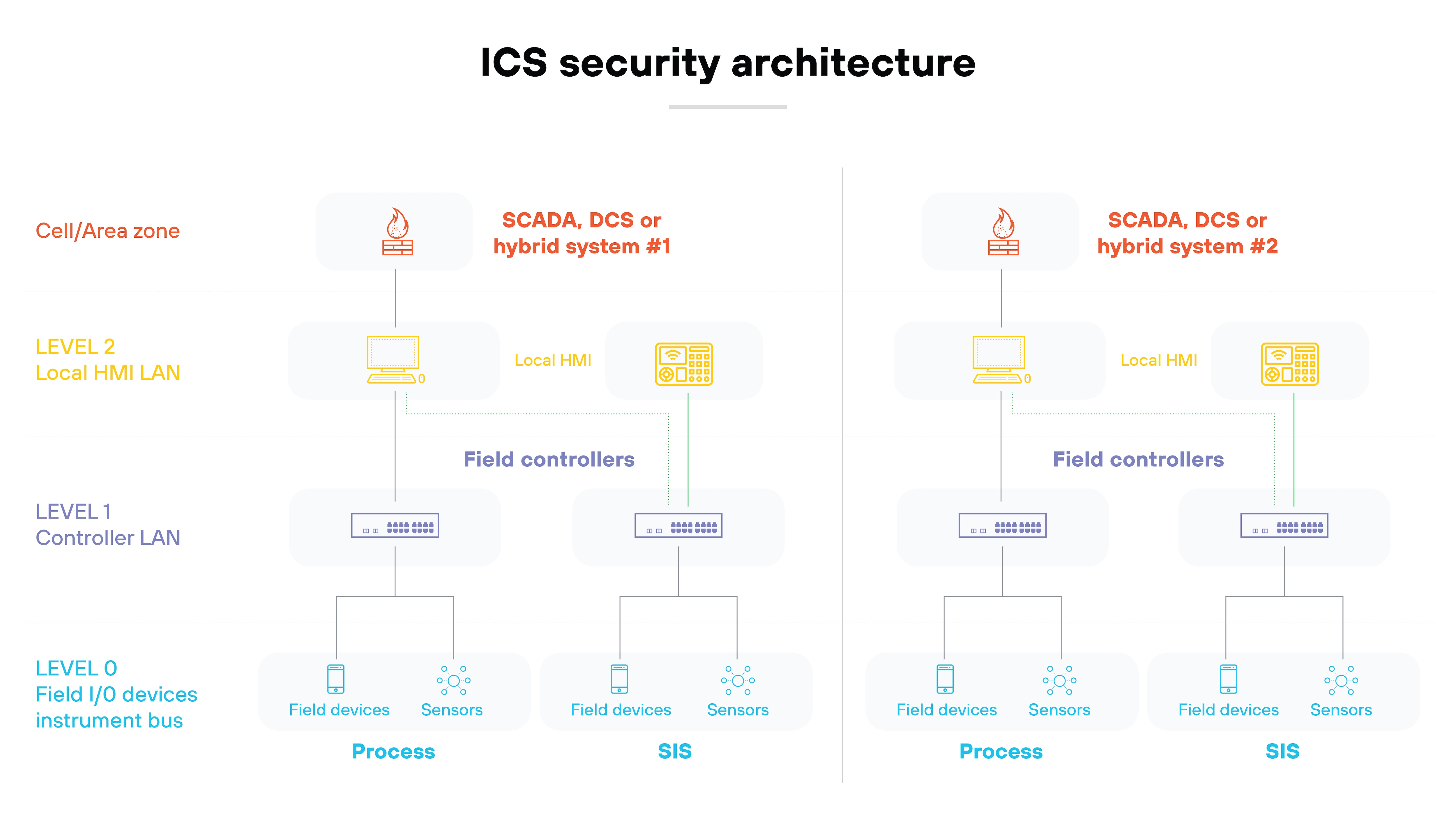
| Purdue Model for ICS Security | A hierarchical architecture that segments industrial control systems into layers, from physical processes at the base (Level 0) to enterprise IT systems at the top (Level 5). | Defining security zones and conduits to isolate and protect critical ICS components and facilitate network segmentation. |
ICS cybersecurity standards
| Standard | Description | Focus areas |
|---|---|---|
| ISA/IEC 62443 | Widely recognized set of standards for ICS security, targeting operators, service providers, and manufacturers. | Risk assessment, secure system integration, product security requirements, and security program management for ICS environments. |
| NIST SP 800-82 (National Institute of Standards and Technology Special Publication) | Focuses on securing ICS, including SCADA, Distributed Control Systems (DCS), and other control systems. | Provides guidance on securing ICS environments in the context of cybersecurity and risk management. |
| ISO/IEC 27019 | Extends ISO/IEC 27001 for process control systems in the energy industry, which commonly use ICS. | Security management and technical controls for the energy sector’s control systems. |
| ANSI/ISA-99 (precursor to ISA/IEC 62443) | U.S. standard that became the foundation for the IEC 62443 standards, focusing on industrial automation security. | Risk-based security assessments, security policies, and procedures for control systems. |
ICS cybersecurity standards
| Standard | Description | Focus areas |
|---|---|---|
| NERC CIP (North American Electric Reliability Corporation Critical Infrastructure Protection) | A set of mandatory standards regulating the security of ICS within the North American power grid. | Focuses on asset management, electronic security perimeters, incident reporting, and recovery planning for ICS in the electricity sector. |
| U.S. Presidential Executive Order 13636 (Improving Critical Infrastructure Cybersecurity) | Directs the NIST Cybersecurity Framework for improving ICS security in U.S. critical infrastructure sectors. | Encourages organizations to adopt the NIST CSF for securing ICS, particularly in critical infrastructure sectors. |
| FISMA (Federal Information Security Management Act) | Applies to ICS environments used in U.S. federal government facilities, mandating specific security measures. | Risk management, reporting, and incident response for government ICS. |
| European NIS Directive (Network and Information Security Directive) | While this regulation covers critical infrastructure broadly, it places specific emphasis on securing ICS in sectors like energy, transportation, and water. | Cybersecurity risk management and incident reporting obligations for ICS used in critical infrastructure sectors. |
| UK NIS Regulations (NIS Directive Implementation in the UK) | Enforces similar requirements to the European NIS Directive, focusing on ICS within critical national infrastructure sectors in the UK. | Securing ICS in sectors such as energy, health, water, and transportation, with specific guidelines for risk assessment and incident reporting. |
| Further reading: What Is the Purdue Model for ICS Security? | A Guide to PERA
What is ICS supply chain security?
ICS supply chain security ensures the security of software and hardware components throughout the procurement, development, and deployment process. Given the reliance on multiple vendors and global suppliers, managing these complex supply chains is essential to maintaining operational safety and integrity.
Vulnerabilities in the supply chain—such as compromised parts, insecure software, or poor vendor practices—can lead to cyberattacks that disrupt critical infrastructure and jeopardize public safety.
Effective ICS supply chain security includes:
- Verifying the authenticity of components.
- Enforcing cybersecurity standards across vendors.
- Regularly testing for vulnerabilities.
Close collaboration with suppliers is key to ensuring secure design, development, and delivery, reducing risks from third-party components.
2025 ICS security market and trends
The ICS security landscape in 2025 continues to evolve as industrial environments become more connected.
Organizations are prioritizing secure-by-design practices, integrating security from the start of product development rather than addressing vulnerabilities later. Regulatory compliance is also a major driver, with frameworks like NERC CIP and IEC 62443 influencing security decisions.
Meanwhile, AI-driven threat detection and zero trust architectures are becoming more common, helping organizations improve resilience against sophisticated cyber threats.
At the same time, legacy infrastructure remains a challenge.
Many ICS systems were never designed for modern cybersecurity needs, making updates and patches difficult. Organizations are working around these constraints by adopting segmentation strategies and intrusion prevention systems to mitigate risks.
Public-private partnerships and increased threat intelligence sharing are also playing a growing role in strengthening ICS security.
Looking ahead, IT/OT convergence will continue to expand the attack surface, making ICS secure connectivity a critical priority.
Vendors and operators are focusing on better visibility into industrial networks, improving supply chain security, and addressing software vulnerabilities more proactively. As cybersecurity risks grow, the push for stronger, built-in security measures is reshaping how industrial environments are protected.
What are the different types of industrial control systems?
The most common types of ICS systems include:
- Supervisory control and data acquisition (SCADA)
- Distributed control systems (DCS)
- Industrial automation and control systems (IACS)
- Actual ICS implementation
Each type of ICS system is designed to handle different operational needs, from large-scale remote operations to localized production control. Plus, each presents distinct security challenges.
Let’s break down each.
Supervisory control and data acquisition (SCADA) systems
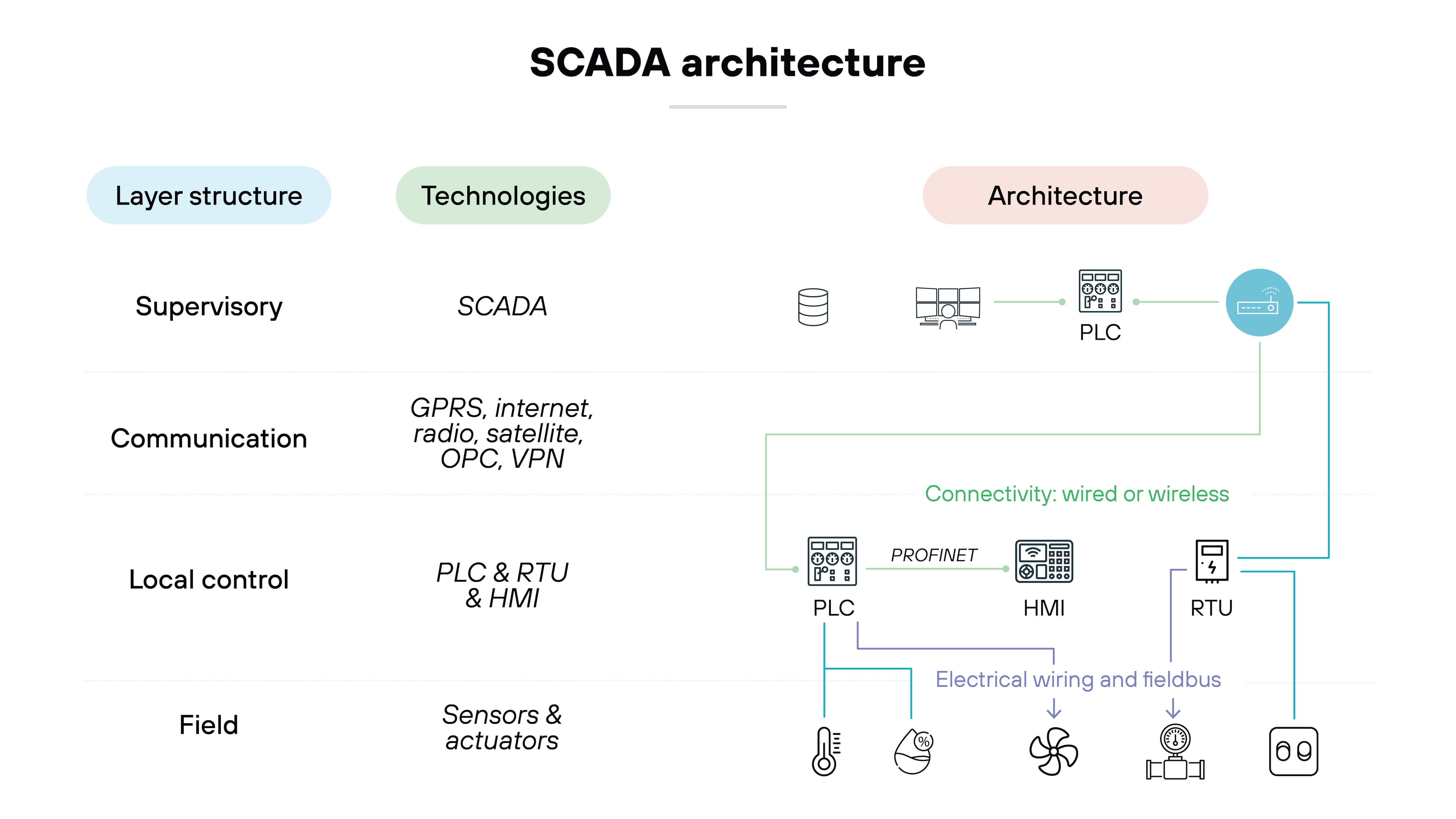
SCADA systems monitor and control processes across large geographic areas, offering centralized control for industries like power distribution, water treatment, and pipeline monitoring. They collect data from sensors and PLCs, relaying it to central control rooms for real-time adjustments.
Security considerations: SCADA systems are vulnerable to unauthorized remote access and data manipulation due to their reliance on wide-area networks. Effective security requires strong network segmentation, encrypted communications, and robust access controls to safeguard centralized operations.
Distributed control systems (DCS)
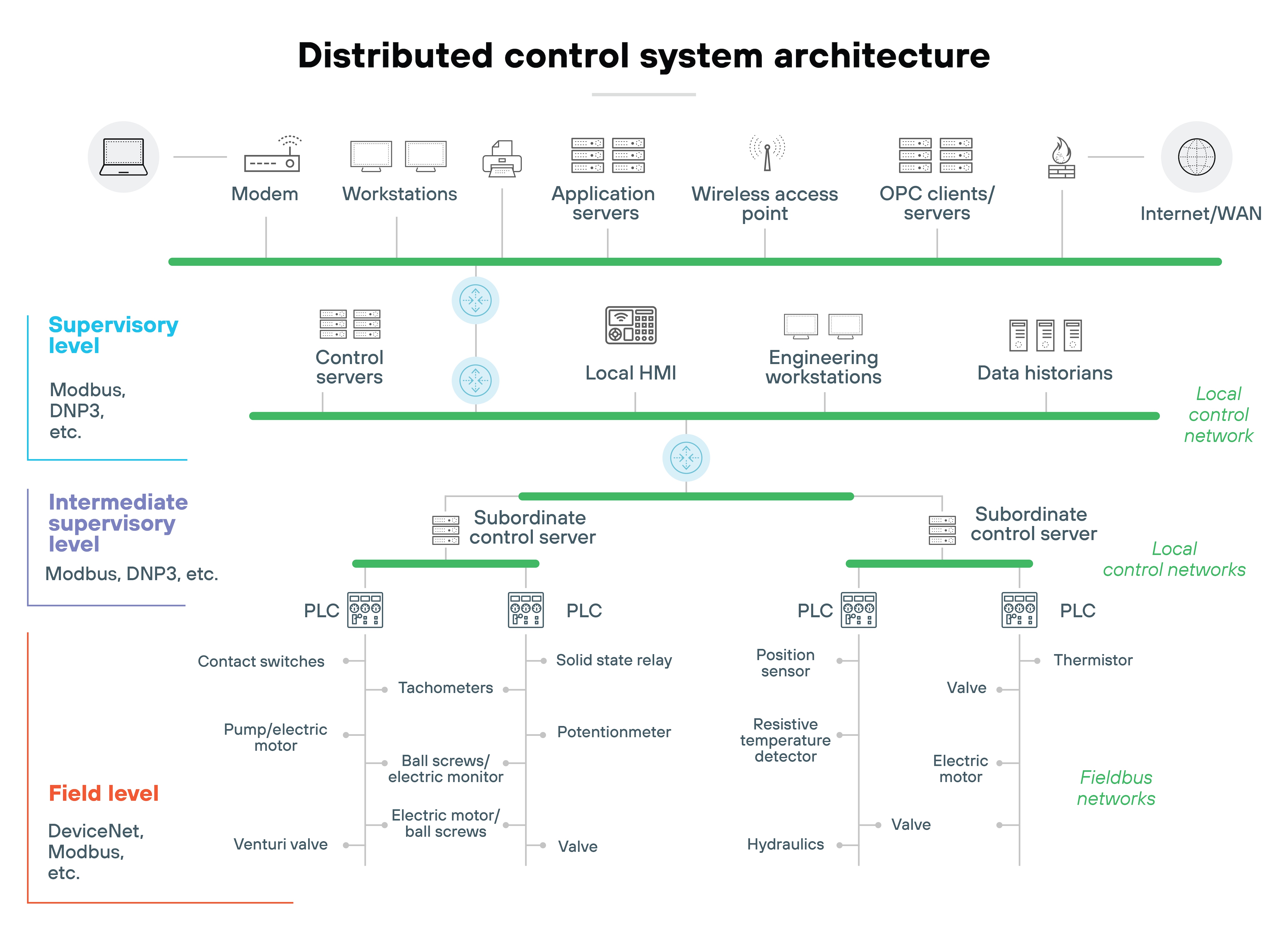
DCS systems manage localized production environments, commonly used in industries like chemical production and oil refineries. They connect multiple controllers to a centralized supervisory control loop for managing processes efficiently and ensuring fast, reliable control.
Security considerations: Though confined to single sites, DCS systems face risks like malware and insider threats. Securing DCS requires strict access controls, monitoring internal traffic, and hardening controllers to prevent unauthorized changes.
Industrial automation and control systems (IACS)
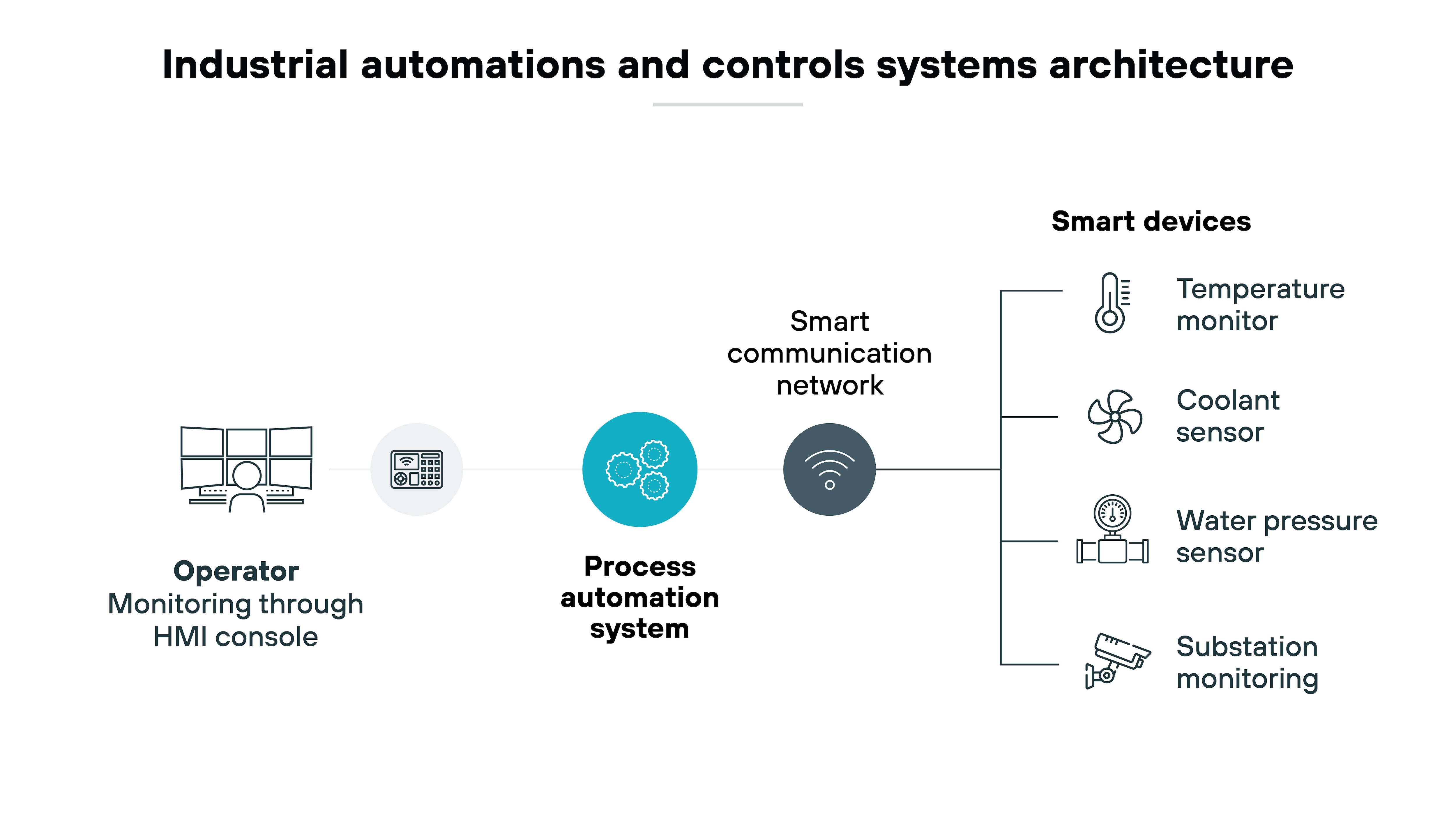
IACS automate industrial processes, integrating hardware, software, and communication systems to handle tasks from basic production to real-time performance optimization. These systems are key to industries requiring seamless integration across operations.
Security considerations: The interconnected nature of IACS expands the attack surface. Securing them requires protecting communication channels, implementing secure-by-design components, and addressing vulnerabilities in older equipment.
Actual ICS implementation
Many ICS implementations combine SCADA's large-scale monitoring with DCS's localized control for a hybrid approach tailored to operational needs. This enables automation of complex processes while retaining real-time monitoring and adjustment capabilities.
Security considerations: Hybrid systems face both external network-based threats and internal vulnerabilities. Coordinated security measures are essential, including protecting wide-area SCADA communications and securing localized DCS operations to ensure system integrity and availability.
What are the components of an industrial control system?
Industrial control systems are made up of various components that work together to monitor, control, and automate industrial processes. Each component plays a specific role in ensuring the system operates efficiently and safely.
Here’s a breakdown of the key ICS components:
ICS environment components
| Component | Description |
|---|---|
| Programmable logic controllers (PLCs) | These are small, specialized computers used to automate processes. They interpret input from sensors and make decisions based on pre-programmed logic to control equipment such as motors or valves. PLCs are widely used in both SCADA and DCS systems. |
| Remote terminal units (RTUs) | RTUs are field devices that gather data from sensors and send it to the central control system. They also execute commands from the master terminal unit (MTU) to control field equipment. RTUs are commonly used in remote locations where local control and data collection are essential. |
| Human-machine interfaces (HMIs) | HMIs provide the graphical interface that allows operators to interact with the ICS. Through the HMI, operators can monitor system status, adjust settings, and control processes. HMIs play a key role in centralized control rooms for both SCADA and DCS environments. |
| Control servers | Control servers host the software that runs the supervisory control systems in a DCS or SCADA environment. They act as a communication hub, linking the control system to field devices, collecting data, and issuing commands to ensure processes are running as expected. |
| Sensors | Sensors collect real-time data from the physical environment, such as temperature, pressure, or flow rate. This data is sent to the ICS controller, where it is used to make decisions that ensure processes operate within set parameters. |
| Actuators | Actuators take control commands from the PLCs or RTUs and convert them into physical actions, such as opening a valve or starting a motor. They are responsible for executing the decisions made by the control system. |
| Data historians | A data historian is a centralized database that logs all process data from the ICS. This historical data is used for analysis, reporting, and decision-making to optimize system performance and troubleshoot issues. |
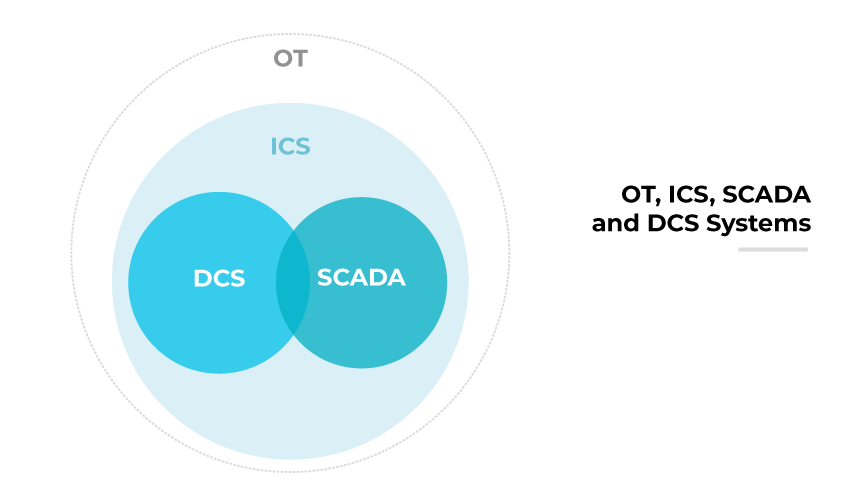
All OT technologies play crucial roles in modern industrial operations. But their specific applications, infrastructure, and focus areas vary.
Operational technology includes all systems that monitor and control physical processes in industries like manufacturing, energy, and utilities. Unlike IT, which is data-focused, OT manages real-world operations.
As explained, industrial control systems are a subset of OT. ICSs are designed to automate and regulate industrial processes using control devices, networks, and sensors to improve efficiency and safety.
Within ICS, supervisory control and data acquisition systems (SCADA) focus on real-time monitoring across large distances. SCADA systems collect sensor data to oversee operations in geographically distributed infrastructure like power grids, water treatment, and gas distribution.
Also within ICS, distributed control systems (DCS) are used in continuous or batch manufacturing. DCSs keep control elements near the process to regulate production flow and ensure plant safety—unlike SCADA, which emphasizes remote monitoring.
How does ICS security compare with OT and SCADA security?
In the realm of technology security, ICS security, OT security, and SCADA security each play pivotal roles.
Let’s break down how each of these security disciplines contrasts with one another.
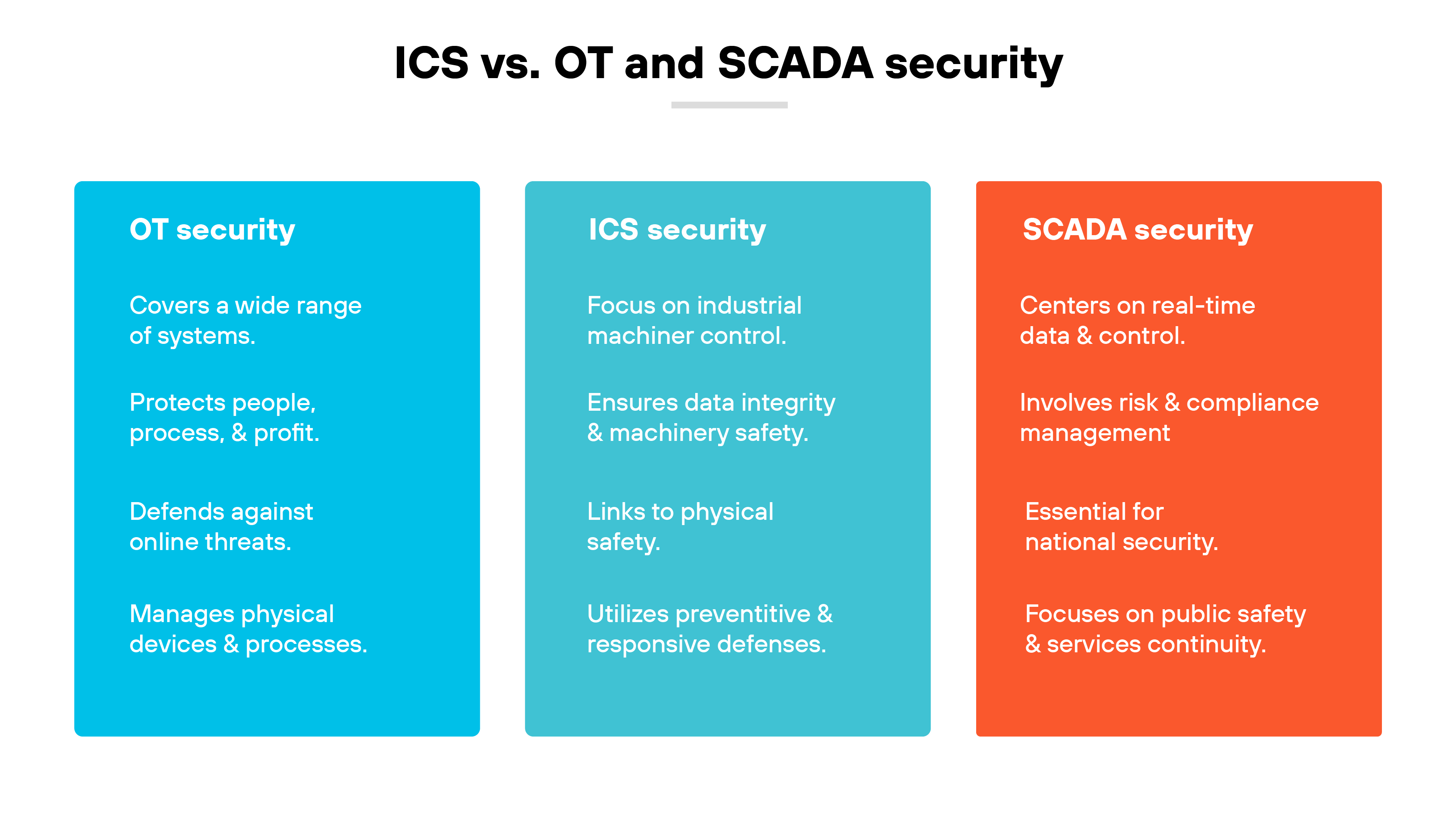
ICS security focuses on systems directly managing industrial processes, vital for sectors such as manufacturing and power generation. It aims to protect the interfaces and hardware that manipulate physical operations. OT security, however, spans a broader range, safeguarding technologies that support various infrastructural operations, which may not directly influence industrial processes but are crucial for operational continuity.
ICS security is tailored to environments controlling physical industrial operations, where disruptions can have immediate physical and critical impacts. Information technology (IT) security, in contrast, protects information systems handling data, focusing more on safeguarding information against loss and theft, with priorities on confidentiality and data integrity. The convergence of IT and ICS systems introduces complexities that necessitate nuanced security measures to address both data and physical process vulnerabilities.
SCADA security, a subset of ICS, specifically targets the systems that monitor and control industrial processes in real time. It is crucial for the uninterrupted operation of utilities and other critical services. While SCADA systems focus on real-time data processing and control, broader ICS security includes various industrial controls that might not require real-time monitoring but are essential for overall industrial functionality.
| Further reading: What Are the Differences Between OT, ICS, & SCADA Security?
What is the history of industrial control systems?
Industrial control systems have evolved over centuries, shaped by technological advancements and changing industrial needs.
Early automation dates back to the 1700s, with innovations like James Watt’s flyball governor for regulating steam engines and basic feedback mechanisms in windmills. The 20th century saw major shifts with relay logic in the 1920s, followed by distributed control systems (DCS) and programmable logic controllers (PLC) in the 1970s, which improved precision and automation.
By the late 20th century, cyber integration introduced new risks. The 1982 Soviet pipeline explosion, caused by malware, underscored the vulnerabilities of ICS to cyber threats, making security a key priority.
Today, ICS continues to evolve, blending mechanical, electrical, and digital technologies to enhance efficiency—while requiring robust cybersecurity to protect critical infrastructure.
ICS security FAQs
ICS security’s meaning is the practice of protecting industrial control systems—critical hardware and software that manage industrial machinery and processes—from cyber threats and physical risks to ensure safe, continuous operations in industries like energy, manufacturing, and infrastructure.
IC security pertains to protecting the hardware and software systems that manage and automate industrial processes. The focus is on ensuring the integrity and availability of these systems to prevent disruptions or data compromises.
ICS refers to systems comprising both hardware and software that control and manage industrial processes. These systems are fundamental in sectors like manufacturing and energy, aimed at optimizing process efficiency and safety.
IT security focuses on protecting data and information systems mainly from theft and disruption, prioritizing confidentiality and integrity. Conversely, ICS security targets systems controlling physical operations, emphasizing availability and safety to prevent physical disruptions.
In technology, ICS stands for industrial control systems, which are crucial for automating and managing industrial operations. These systems include a mix of software and hardware that helps in process control and decision-making.
The industrial control systems (ICS) cyber security strategy involves multiple layers of protection, including network segmentation, real-time threat monitoring, and robust access controls. This comprehensive approach is designed to shield both the physical and digital aspects of industrial control systems.
In cyber security, ICSs are hardware and software systems that monitor and control industrial processes in sectors like energy, manufacturing, and utilities. ICS cybersecurity focuses on protecting these systems from threats that could disrupt operations, compromise data, or harm critical infrastructure.
An ICS security engineer specializes in protecting industrial control systems against cyber threats. Their role includes assessing vulnerabilities, implementing security measures, and managing incident responses to maintain the operational integrity of ICS environments.
The primary difference between ICS and IoT security is that ICS security focuses on protecting industrial systems that manage critical processes and physical operations, while IoT security focuses on safeguarding interconnected consumer or commercial devices that communicate over networks.
ICS application security is a subset of OT security that specifically focuses on securing the applications and software used within industrial control systems (ICS). This includes preventing vulnerabilities in ICS-specific applications like HMIs, SCADA software, and control logic.
ICS computer security focuses specifically on protecting the computers, servers, and other digital systems used within ICS environments.
User management in ICS security involves controlling and monitoring user access to industrial control systems to ensure only authorized personnel can interact with critical systems. This includes implementing role-based access controls, multi-factor authentication, and activity monitoring to prevent unauthorized access, insider threats, and accidental misconfigurations that could compromise the safety and functionality of ICS environments.