What Is a Proxy Server?
A proxy server is a digital intermediary, routing internet traffic between users and online resources, ensuring secure and controlled data exchange.
How Does a Proxy Server Work?
Proxies execute a pivotal role in processing web requests and responses within the cyberspace realm. Every internet-connected device possesses a unique Internet Protocol (IP) address. A proxy service engages with this digital address to facilitate its role of routing and securing internet traffic.
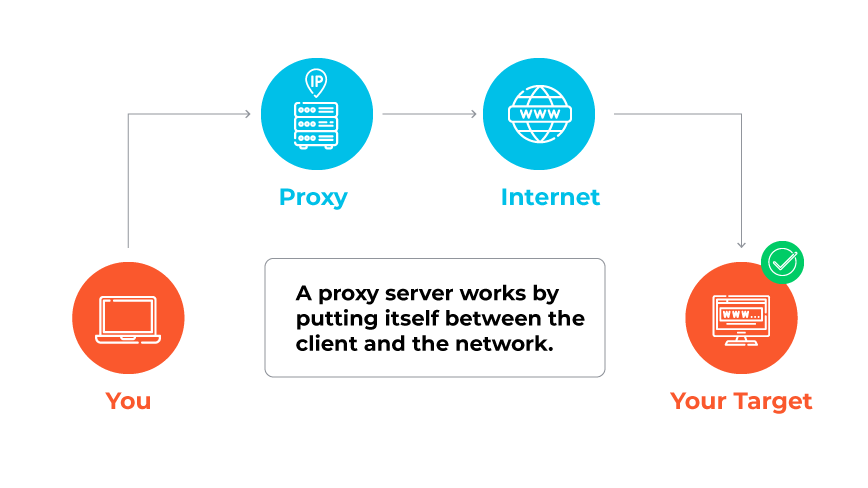
The operational cycle encompasses several steps:
- The process initiates when a device submits a request to access online content or a web resource, generally by entering a website's URL in a web browser.
- The request, instead of being directly forwarded to the web server hosting the content via the internet service provider (ISP), is first routed to the proxy server.
- The proxy server, possessing its distinct IP address, subsequently transmits the request to the intended web server, thereby concealing the original user's IP address.
- The web server then processes the request, oblivious of the original IP address, and sends the requested data or website back to the proxy server.
- The proxy server performs an essential security function by scanning the returned data for potential threats, such as malware, prior to forwarding it to the requesting device.
Additionally, proxies possess the capability to store frequently accessed webpages in a local cache. This feature allows them to swiftly provide these pages to users without necessitating a direct request to the internet, thereby accelerating the data retrieval process.
Proxies are extensively employed for network security and performance, facilitate administrative control, and enable user privacy and anonymous web surfing. However, it is possible to use proxy servers for contrary intentions, such as invading user privacy or obstructing traffic. The type utilized, such as shared or dedicated, and its configuration options, like HTTP, SSL, FTP, and SOCKS, depend on the intended usage and user preference.
While proxies function as a veil, they are not entirely invisible. Proxy IP addresses must be specified in the browser or other protocol program's configuration settings. Hence the credibility of the provider is a crucial factor, particularly for proxies offering encrypted traffic and anonymity services.
Lastly, some proxies can manipulate IP addresses to appear as though the traffic originates from a different geographical location. Malicious actors can exploit this function for circumventing regional restrictions or enhancing online privacy.
Benefits of Proxy Servers
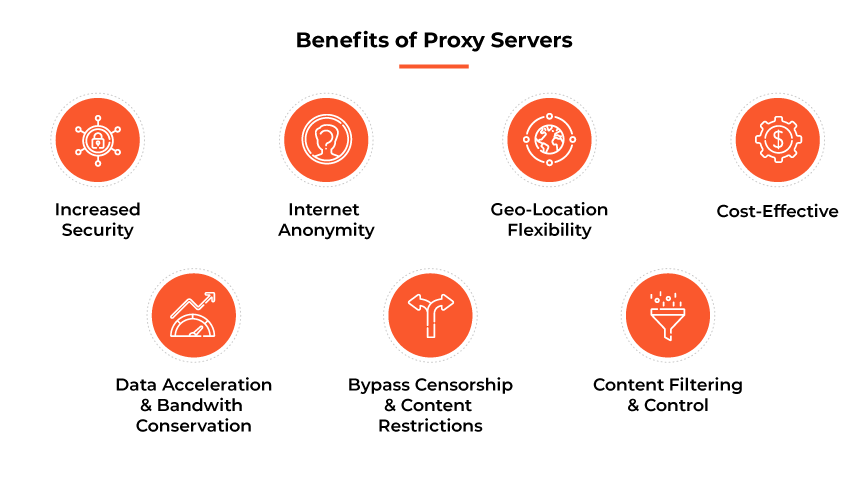
Increased security: Proxies significantly augment the security of internet connections. They act as an intermediate between user systems and the internet, effectively functioning like a firewall. This protects the user's IP address from potential hackers who might seek to infiltrate systems. Furthermore, some types of proxies offer enhanced protection, such as HTTPS proxies that provide encryption for secure connections and SMTP proxies which block malicious emails. Additionally, reverse proxies block suspicious and repeated requests, mitigating cyberattackers and threats like Distributed Denial of Service (DDoS) attacks and man-in-the-middle (MitM) attacks.
Internet anonymity: Proxies provide the ability to browse the internet anonymously. This anonymity is achieved by hiding the user's IP address. This ensures a more private browsing experience, safeguarding the user from unwanted ads and data collection. Moreover, it protects sensitive company data, essential for maintaining a competitive edge in the corporate world, from potential theft.
Geo-location flexibility: Proxies permit users to access location-specific content, a key asset when certain information or services are regionally restricted. Users can set their proxy server to use an IP address associated with a different country, which can "trick" websites into thinking the user is browsing from that location. This can enable access to otherwise restricted content and is especially beneficial for companies conducting internet-based marketing activities that rely on geo-location data.
Content filtering and control: In an organizational context, proxies provide a degree of control over internet usage. Administrators can block access to websites that might be inappropriate, distracting, or contrary to the organization's policies. Transparent proxies can log user activity, enabling companies to monitor employees' internet usage at work. This control can maintain productivity and prevent misuse of resources.
Data acceleration and bandwidth conservation: Proxies can improve internet speed and conserve bandwidth by caching frequently accessed websites. By storing a copy of frequently requested data, a proxy server can quickly fulfill subsequent requests without having to retrieve the data from the original server again. This results in faster data retrieval for the user and reduced bandwidth usage.
Bypassing censorship and content restrictions: Proxies enable users to bypass internet censorship and access-blocked resources. This can be especially useful in regions where internet use is heavily regulated, or in situations where certain services are available only in specific countries.
Cost-effectiveness: Many proxies, particularly web proxies, are freely available. While their performance and security might not be as robust as paid alternatives, they can be a cost-effective solution for small organizations who require the aforementioned benefits on an occasional basis.
Disadvantages of Proxy Servers
Proxy servers, although useful in certain contexts, pose substantial drawbacks organizations must be cognizant of in strategic planning for internet security and performance.
A critical disadvantage is limited security. Proxies typically do not have encryption capabilities, making the data that transits through them vulnerable to interception. This risk factor heightens the potential for the compromise of business-sensitive data, such as login credentials or proprietary information.
Another issue lies in data logging. Proxies capture and store IP addresses alongside web request data, some of which might not be encrypted data. Depending on the server's management, this logged data could potentially be sold to external parties, thereby threatening corporate data privacy, and potentially leading to data breaches.
Moreover, proxy servers generally operate on open ports, increasing potential attack vectors that malicious actors can exploit due to security vulnerabilities. This operational model amplifies the overall cyberthreat landscape for an enterprise.
Additionally, proxies offer limited privacy. While capable of anonymizing an IP address, their protective measures often do not extend beyond web requests. Given that many free proxies function on unsecured networks and use ad-based revenue models, the possibility of ads laden with viruses or malware penetrating corporate networks is a significant concern.
Performance inconsistency is another drawback. Free proxies in particular may lack sufficient bandwidth to support numerous simultaneous users without compromising on speed and performance, which could significantly impact business operations.
Finally, proxy servers have limited functionality because they typically function on an app-by-app basis. This configuration necessitates individual proxy settings for each application, in stark contrast to more comprehensive alternatives such as VPNs that can protect an entire network.
Types of Proxy Servers
1. Forward Proxies
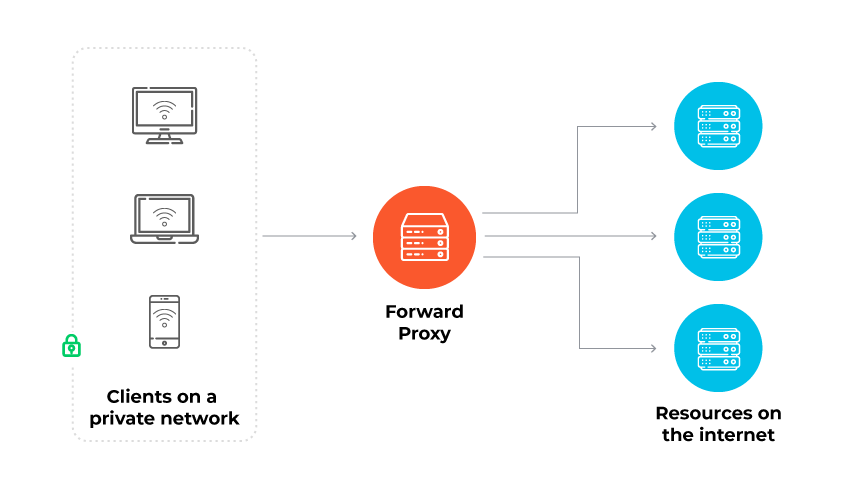
Act on behalf of the client, sending client requests to web servers. They are mainly used to bypass restrictions and enhance user privacy.
2. Reverse Proxies
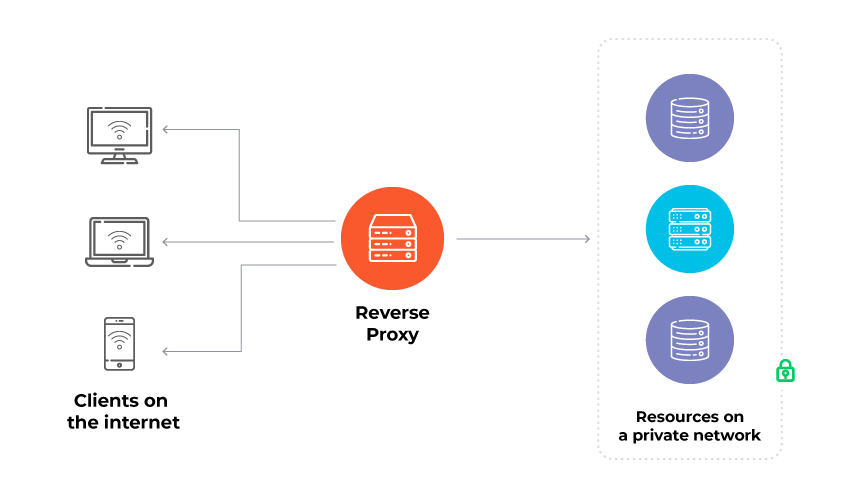
Operate on behalf of servers, managing requests from clients to a server. They are often used for load balancing, indirect server access, and content streaming.
3. Transparent Proxies
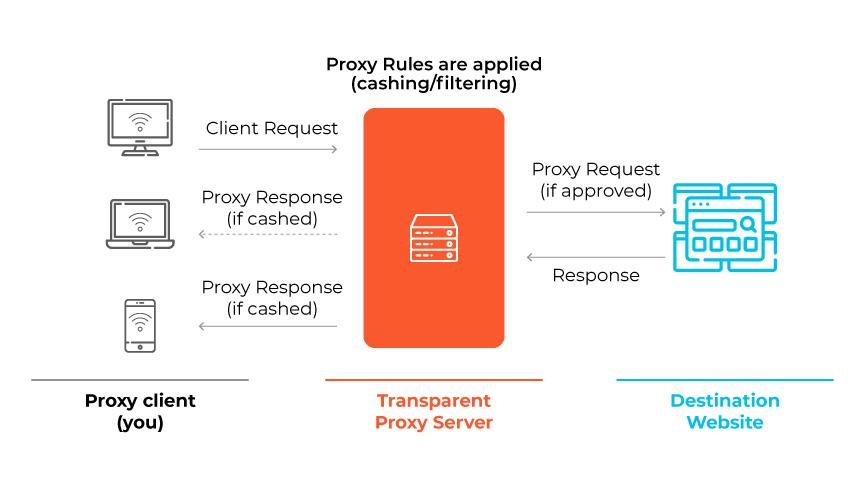
Centralize network traffic, typically in a corporate internal network setting, to monitor and control network traffic. They do not provide user anonymity.
4. Anonymous Proxies
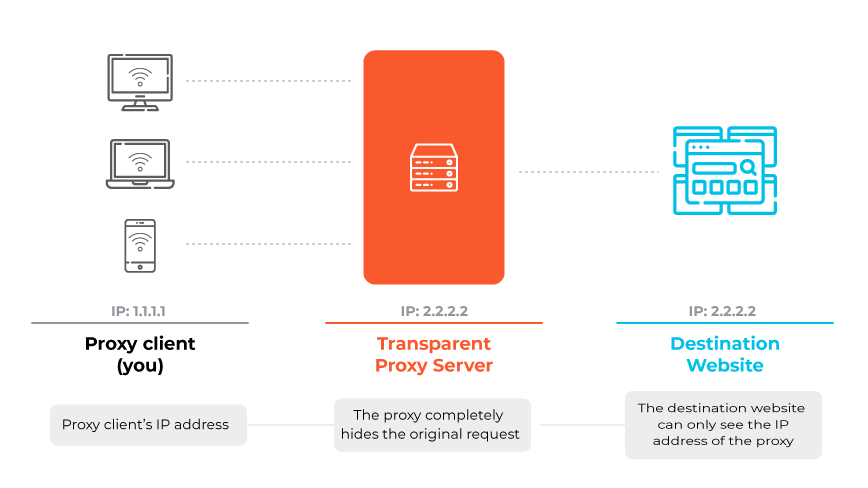
Anonymous proxy servers conceal the client's IP address for privacy enhancement and access to blocked content. They may, however, still be detectable.
5. Socks Proxies
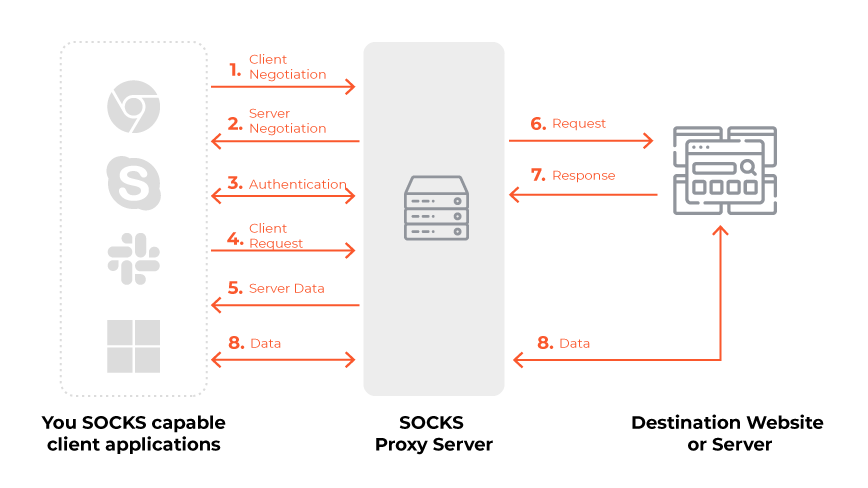
Facilitate the processing of all types of traffic, including web traffic, UDP data, and DNS lookup operations, offering higher anonymity levels.
Proxy Servers vs. VPNs

Proxies and VPNs (virtual private networks) both serve as intermediaries in the communication between a user's device and the internet, yet they operate in distinct ways and offer differing levels of privacy and security.
A proxy server acts as a gateway, rerouting internet traffic and concealing a user's location and connection information by altering the IP address. However, encryption, a critical feature for secure data transmission, is absent in a typical setup. This means that while a proxy hides the user's location, the information sent and received may still be vulnerable to interceptions or prying eyes. In addition, they are often set up individually on an application level, requiring specific configurations for each application to use it.
On the other hand, a VPN creates an encrypted tunnel between a user's device and the VPN server, through which all network traffic passes. This system-level setup results in 100% data encryption, regardless of the application. This encryption feature makes VPNs more, safeguarding users' data from potential intrusions or interceptions. Unlike proxies, a VPN provides comprehensive privacy protection, as it hides both the user's location and the content of their communications.
Furthermore, VPNs and proxies differ in performance and use cases. Proxy servers can use caching to accelerate internet access, a feature that VPNs do not offer. For individual users with less sensitive data and more concern for internet speed, a proxy may suffice. However, for business scenarios where data breaches can lead to substantial losses, a VPN is generally the preferred choice, thanks to its comprehensive data encryption capabilities.
Proxy Servers and Secure Web Gateways (SWG)
Enterprises often use proxies as part of a secure web gateway (SWG) implementation. This provides security inspection of HTTP and HTTPS web protocols along with web filtering and malware prevention. Organizations can also use proxies instead of deploying agents on user devices. However, because proxies can only inspect web-based traffic, they are typically part of a more comprehensive security platform strategy or by organizations looking to gradually transition to a more secure method of remote access. Alternative onboarding methods include IPsec or GRE tunneling and firewall port forwarding.
Proxy Servers and SASE
While security inspection of all device traffic and protocols is ideal, organizations can achieve a balance of architectural flexibility and security by implementing proxies as part of a secure access service edge (SASE) approach. A SASE solution provides all the networking and security capabilities an organization needs in a single cloud-delivered service.
