-
Guide: How to Reduce Security Alert Fatigue
- Security Alert Fatigue Explained
- Exploiting Alert Fatigue: A Critical Vulnerability
- The Root Causes of Security Alert Fatigue
- The Impact of Alert Fatigue on Cybersecurity Operations
- Mitigation Strategies: Fighting Fatigue with Technology and Process
- Best Practices for Sustainable Security Operations
- The Future of Alert Management
- Security Alert Fatigue FAQs
- How Do I Improve SOC Effectiveness?
-
How AI-Driven SOC Solutions Transform Cybersecurity: Cortex XSIAM
- How Cortex XSIAM 2.0 Revolutionizes Security Operations
- Cortex XSIAM Solutions and Advantages
- Addressing Critical Issues in Current SOC Solutions
- How Cortex XSIAM Transforms the SOC
- Distinctive Features of Cortex XSIAM
- Comprehensive SOC Solutions: Single Platform Delivery Highlights
- Integrated Capabilities: The XSIAM Solutions Delivery
- Ready to Transform Your Cybersecurity Landscape?
- What is SOC as a Service (SOCaaS)?
- Security Operations Center (SOC) Roles and Responsibilities
What Is a Security Operations Center (SOC)?
A security operations center (SOC) is a central team that oversees and manages an organization's security stance. This unit usually comprises security experts tasked with detecting, addressing, and reducing security threats. In essence, the SOC team ensures that the organization functions securely.
The four primary functions of security operations are:
- Identify – Identify an alert as potentially malicious and open an incident.
- Investigate – Investigate the root cause and impact of the incident.
- Mitigate – Recommend mitigation options to isolate and remove a threat.
- Continuous Improvement – Constantly adapt to process, visibility, and technology to improve in real time as incidents occur.
SOC teams often work around the clock, continuously safeguarding an organization's digital infrastructure and maintaining peace of mind for stakeholders. These security experts utilize advanced tools to analyze network traffic and identify suspicious activities, allowing for swift incident response.
SOC Challenges
While well-funded threat actors are investing in new tools like machine learning (ML), automation, and artificial intelligence (AI), SOCs built around legacy security information and event management fail to provide a flexible and scalable solution that keeps pace with digital transformation, cloud initiatives, and advanced attack campaigns.
Today’s expanded enterprise attack surface generates much more security data, which is both more complex and siloed, than only a few years ago. Network, endpoint, identity, and cloud data remain in separate systems. Endpoint telemetry is locked in an endpoint detection and response (EDR) system, and cloud data is in a separate cloud security tool.
As a result, SOC analysts must manually analyze data to triage alerts and take effective action. Alerts overload analysts, so threats are missed, and dwell times remain long. Security engineers struggle to integrate new data streams and create new detection rules and playbooks, while security architects integrate the latest new point product. The results are predictable: alert fatigue, slow investigations, and attackers who hide in networks for months.
The modern way to scale an effective SOC is with automation, leveraging AI and ML as the foundation, and analysts working on a small set of high-risk incidents. Just as operating a self-driving vehicle no longer requires constant, hands-on control by the operator, an automation-led SOC handles the bulk of low-risk, repeated alerts, analysis tasks, and mitigations.
This frees the analysts to work on urgent, high-impact incidents. At the same time, the underlying platform autopilots the SOC to safe outcomes, learning from each activity and offering information and practical recommendations to the SOC manager.

SOC Roles and Responsibilities
A SOC needs a well-structured team to handle the growing complexity of modern threats. The team collaborates with other departments or teams to share information about incidents with relevant stakeholders. Typically, SOC roles and responsibilities involve various skilled personnel working together to manage security incidents effectively. This team includes:
- SOC manager: This person manages the SOC's day-to-day operations, including developing and implementing security policies and procedures and providing security awareness training to employees.
- Advanced security analyst: Proactively hunts for threats and vulnerabilities in an organization's environment. This includes analyzing logs, network traffic, and other data sources to identify potential threats and vulnerabilities.
- Incident responder: This person responds to security incidents, including identifying the source, determining the scope, and assessing the impact.
- Security engineer/architect: Designs and implements security solutions to protect an organization's environment. This includes network security solutions like firewalls, intrusion detection systems, and antivirus software.
- Security investigator: Responsible for investigating security incidents and determining the incident's root cause. This includes analyzing logs, network traffic, and other data sources to identify the source of the incident.
The SOC splits tasks to promote specialization and flexibility. By grouping staff according to their skills, SOCs can respond quickly to incidents, investigate thoroughly, and identify new threats. This arrangement boosts efficiency, allowing for faster decision-making and stronger security measures that align with the organization's cybersecurity strategy.
Learn more about SOC Roles and Responsibilities, the key to your security operations success.

Key SOC Functions and Tools
A SOC acts as the command center for cybersecurity operations, with a range of critical functions designed to detect, respond to, and prevent cyber threats. By leveraging the latest tools, technologies, and techniques, a SOC ensures that the organization remains secure and resilient against evolving threats. Here are its key functions and tools utilized for each:
24/7 Monitoring
- Overview: Security Operation Centers (SOCs) work 24/7 to monitor an organization’s network and systems for unusual activity or threats. Their main goal is to detect incidents and reduce response time quickly.
- Details: This constant monitoring includes checking logs, traffic patterns, and data from firewalls, Intrusion Detection Systems (IDS), and endpoint security tools. Analysts search for signs of malware, unauthorized access, or security breaches.
- Tools Used: The primary tools include Security Information and Event Management (SIEM) systems, Intrusion Detection and Prevention Systems (IDS/IPS), and Endpoint Detection and Response (EDR) tools.
SIEM Solutions in a SOC
Security Information and Event Management (SIEM) solutions are a type of security solution that helps businesses monitor and analyze their security data in real time. SIEM solutions collect data from multiple sources, including network devices, applications, and user activity, and use analytics to detect potential threats.
SIEM solutions allow businesses to respond quickly to security incidents and take corrective action. For many SOCs, this is the core monitoring, detection, and response technology utilized to monitor and aggregate alerts and telemetry from software and hardware on the network and analyze the data for potential threats.
Incident Detection and Response
- Overview: When a security issue is detected, the SOC quickly assesses its seriousness, finds out where it came from, and takes steps to limit the damage.
- Details: Incident response teams use established procedures to tackle threats like viruses, ransomware, service outages, and data breaches. The first action is to contain the threat by isolating affected systems and stopping its spread. After that, the SOC works to fix the problem to restore normal operations and prevent it from happening again.
- Tools Used: Tools like SIEM help with event tracking and alerting, while automation tools like SOAR assist in managing incidents.
Threat Intelligence
- Overview: Threat intelligence collects and analyzes information about possible security threats to enhance protection.
- Details: SOCs gather intelligence from various sources, including public and paid services and industry collaborations. This information can include current attack methods and strategies attackers use, helping SOCs find weaknesses and defend against new threats.
- Tools Used: Various platforms, information feeds, and machine learning techniques to analyze and prioritize threats.
Event Correlation
- Overview: Event correlation connects different security events and incidents to uncover patterns or signs of a more significant attack.
- Details: A single security event (e.g., a failed login attempt) might seem insignificant in isolation, but multiple events across different systems or times might point to a coordinated attack (e.g., credential stuffing leading to a breach). By correlating data from various security tools, SOC teams can identify complex, hidden attacks that might otherwise go unnoticed.
- Tools Used: SIEM systems are key here, as they aggregate data from various sources and apply correlation rules to identify potential threats.
Forensic Analysis
- Overview: Forensic analysis is conducted after an incident to understand what happened, how it happened, and the impact.
- Details: The SOC investigates the attack by analyzing affected systems, reviewing logs, recovering deleted data, and sometimes even reversing malware. The goal is to build a timeline of the attack, identify exploited vulnerabilities, and understand the attacker’s methods. The findings help improve future defenses and provide information for legal or regulatory reporting.
- Tools Used: Forensic analysis tools include disk/data capture tools, file viewing tools, network and database forensics tools, and specialized analysis tools for file, registry, web, Email, and mobile device analysis, combined with SIEM and system logs.
Compliance Management
- Overview: Many organizations must adhere to industry standards and regulatory frameworks to maintain their cybersecurity posture. The SOC plays a crucial role in ensuring compliance with these requirements.
- Details: SOCs ensure the organization complies with regulations like GDPR, HIPAA, PCI-DSS, and others. This includes maintaining the required security controls, conducting regular audits, and generating reports for external auditors or regulators. Non-compliance can lead to fines, legal issues, and loss of customer trust.
- Tools Used: Compliance management software, SIEM systems, and reporting tools.
Vulnerability Management
- Overview: Vulnerability management is identifying, classifying, and remediating vulnerabilities in systems, software, and hardware.
- Details: This includes conducting regular vulnerability scans, reviewing patch management practices, and addressing weaknesses before attackers can exploit them. Vulnerability management also involves prioritizing risks based on severity, exploitability, and potential impact on the business.
- Tools Used: vulnerability scanners (e.g., Nessus, Qualys), patch management solutions, and risk assessment frameworks.
Proactive Threat Hunting
- Overview: Unlike traditional monitoring, which responds to alerts, threat hunting is a proactive approach to seek out hidden threats within the network before they cause harm.
- Details: Threat hunters look for indicators of compromise (IOCs) that haven’t yet triggered alerts. This includes searching for early signs of attack (like abnormal system access patterns or unusual data traffic). Threat hunters often use behavioral analytics and machine learning to identify anomalies and discover sophisticated threats like advanced persistent threats (APTs).
- Tools Used: Threat-hunting platforms, endpoint detection tools, and threat intelligence feeds.
Collaboration and Coordination
- Overview: The SOC doesn’t operate in isolation; it coordinates with other departments and may collaborate with external agencies or other SOCs.
- Details: SOC teams work closely with IT, legal, compliance, and executive teams to ensure a holistic approach to cybersecurity. For example, IT teams may help isolate affected systems, legal teams handle breach notifications, and management teams make strategic decisions. External collaboration might involve working with law enforcement or industry-sharing groups during an investigation.
- Tools Used: Communication and incident management platforms (e.g., Slack, Microsoft Teams, and case management tools).
Explore how SIEM tools empower SOC teams: How Do SIEM Tools Benefit SOC Teams?, and What is a SIEM Solution in a SOC?
SOC Delivery Models
Key factors, including the business's needs, global presence, access to resources, and funding, usually drive security operations. These factors can influence whether a business chooses in-house or outsourced security operations.
In-House, Next-Generation SOC
An in-house, next-generation SOC keeps the knowledge and control of the environment within the business, provides flexibility in alerting, automates repetitive tasks, utilizes AI with ML to prioritize and generate high-value alerts, and applies continuous improvement. It can require a considerable investment upfront and will require all 84 elements of security to be implemented.
SOC as a Service
Outsourced security operations, or SOC as a service, provide access to experts, advanced technology, mature processes, and quick implementation. However, they still require in-house resources to carry out remediation activities and can reduce the number of custom processes that can be implemented.
SOC-as-a-service also requires detailed service-level agreements (SLAs) and consistent monitoring and testing of the SLAs to ensure quality. This setup may also cause concerns around compliance at different global locations, gaps in visibility, and a lack of internal knowledge.
Find out more about the subscription-based SOC-as-a-service delivery model.
Hybrid Solution
Many organizations choose a hybrid solution with some functions outsourced, such as using level-one analysts to identify priorities. This solution provides access to subject matter experts that may not be present in-house and can provide flexibility and scalability. It requires stringent communication agreements and tight processes around escalations so that external and internal staff have the flexibility and ability to respond quickly to incidents.
How Does a MSSP Differ from a SOC?
A managed security service provider (MSSP) is a third-party vendor that provides security services to multiple clients. It may offer SOC-like functions, but its primary role is service delivery versus organizational integration.
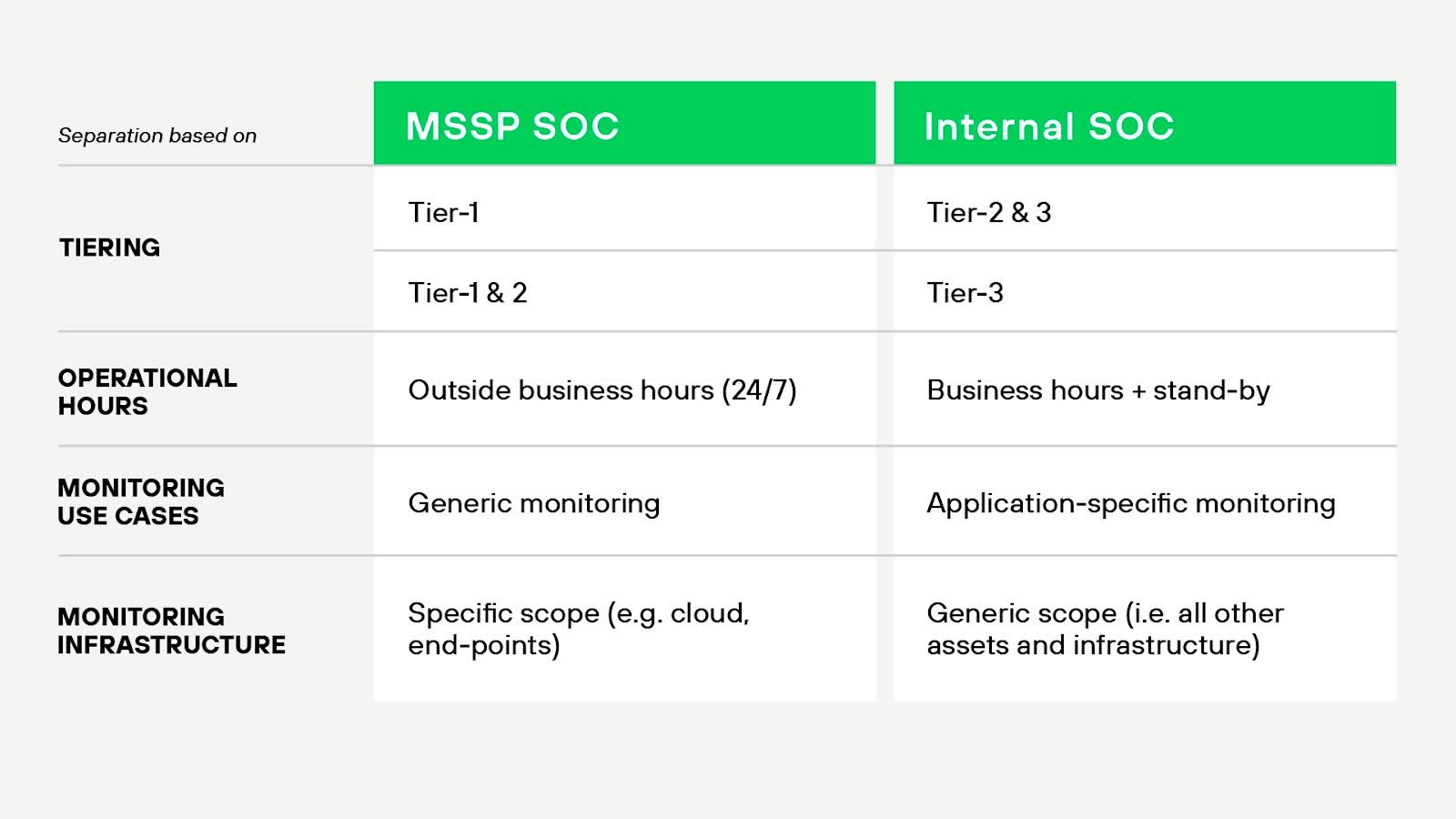
Operational Control
Organizations retain full control over their SOC. They dictate staffing, tooling, data handling, workflows, and escalation paths. SOC teams often embed deeply within the broader IT or security organization.
An MSSP operates externally and follows contract-defined workflows. Customers may receive dashboards or reports, but they don't manage day-to-day operations. Response decisions often require customer approval unless explicitly defined in the SLA.
Scope of Service
SOC teams handle a broad range of activities across detection, response, threat hunting, and incident analysis. They typically ingest telemetry from across the IT stack — network, endpoint, cloud, identity, and more.
MSSPs often focus on predefined services: perimeter monitoring, log aggregation, alerting, and basic triage. Some provide more advanced offerings like managed detection and response (MDR), but many stop short of full-spectrum investigation and threat hunting.
Visibility and Context
SOC teams operate within the organization’s environment. They have direct access to telemetry, asset inventories, and user data. This context improves triage accuracy and speeds up investigations.
MSSPs rely on what the client provides — usually limited to log forwarding or third-party integrations. Without full context, they may miss attack paths or escalate false positives more frequently.
Responsiveness
Internal SOCs can respond to threats immediately. Analysts interact directly with infrastructure, security tools, and leadership.
MSSPs follow escalation protocols. Response times may depend on SLA tiers or ticket-based workflows. Delays in communication or approval can slow containment.
Customization and Integration
SOCs integrate with internal development, cloud, and IT teams. They tailor detection logic and workflows to match the organization’s environment and risk profile.
MSSPs tend to standardize service delivery across customers. Custom detections or integrations may cost extra or fall outside their scope.
Best Practices for Optimizing SOC Performance
You should follow several best practices to make your Security Operations Center (SOC) run like a well-oiled machine. These practices help streamline operations, enhance team efficiency, and improve your organization’s security posture.
1. Leverage Automation and AI
Integrating automation and artificial intelligence (AI) into SOC workflows can significantly improve incident detection and response times. Machine learning algorithms can sift through massive data sets to spot patterns and anomalies, helping your team respond faster and more accurately—without being bogged down by manual analysis.
2. Encourage Collaboration and Information Sharing
Effective collaboration is the foundation of excellent SOC performance. Fostering communication within the organization and with external partners can improve situational awareness, enabling quicker and more accurate responses to incidents.
3. Update Security Policies Regularly
Cyber threats are constantly evolving, and so should your security policies. Make it a priority to regularly update procedures and protocols to keep pace with new challenges. Continuous learning and training for SOC staff will ensure they’re equipped to handle the latest threats.
4. Align with Security Frameworks
Align your SOC practices with widely recognized security frameworks like the NIST Cybersecurity Framework or ISO/IEC 27001. This ensures your operations are part of a comprehensive, holistic security strategy that covers risk management, governance, and compliance.
The Future SOC Solution
With the expansion of attacker capabilities, adversaries have begun incorporating their ML and AI technologies to enhance their arsenal of attacks. This includes leveraging ML algorithms for sophisticated phishing campaigns and employing AI-driven techniques for effective end-user social engineering. Defenders must adapt and counter these emerging threats as attackers evolve and refine.
In response, the defender’s strategy is shifting toward leveraging generative AI, which empowers SOCs to detect, analyze, and mitigate cyberthreats proactively. By harnessing the capabilities of generative AI, defenders can stay one step ahead of adversaries and strengthen their overall cybersecurity posture.
Generative AI
Generative AI is about to revolutionize the SOC, ushering in a new era of cybersecurity capabilities and transforming how organizations defend against threats. With its ability to analyze vast amounts of data, detect patterns, and make informed decisions, generative AI will empower SOC teams to stay one step ahead of cybercriminals and proactively protect critical assets.
AI algorithms excel at analyzing large volumes of data in real time. By continuously monitoring network logs, system activities, and user behaviors, AI can swiftly identify suspicious patterns and indicators of potential threats. This enables SOC analysts to proactively detect and respond to emerging threats, minimizing the risk of security breaches.
Generative AI will serve as a dedicated assistant to analysts, working together to swiftly identify, thoroughly investigate, and effectively mitigate security threats. With its advanced capabilities, generative AI provides valuable insights, automates time-consuming tasks, and assists analysts in making informed decisions, bolstering the overall effectiveness and efficiency of security operations.
Generative AI will innovate how cyberattack victims are supported by providing personalized responses that assist them in navigating the remediation process and gaining valuable lessons for future resilience. Imagine every end user having their own cybersecurity expert to review suspicious emails and provide a customized response to their concerns.
Modern security operations will reduce or eliminate repetitive activities in the SOC and contain:
- ML-curated alerts to identify attackers in the weeds.
- Correlation of low-confidence alerts to produce high-confidence alerting.
- Documented roles and responsibilities to clearly define who owns each element of security operations.
- Continuous improvement is applied to every incident.
- Processes designed to ease the adoption of automation while accommodating manual response activities.
- Consistent protection across the network, cloud, and endpoints.
- Automated threat prevention for updates to security controls in minutes, not days.
Learn how to stay ahead of the increasingly complex threat landscape: How AI-Driven SOC Solutions Transform Cybersecurity.
Palo Alto Networks Approach to Establishing a SOC
At Palo Alto Networks, our SOC story is highly optimized. We actively broke away from the traditional four-tier SOC approach, ranging from Tier 1 analysts who monitor, prioritize, and investigate SIEM alerts to Tier 4 SOC managers responsible for recruitment, security strategy, and reporting to management.
Taking more of a hybrid approach, the Palo Alto Networks SOC team follows this general philosophy:
- Staff the SOC, so 80% of staff have previous SOC experience.
- Cross-train the SOC team in all domains, including alert triage, incident response, threat hunting, and automation.
- Provide a well-funded annual training budget for all analysts.
Our rationale is that we can:
- Maintain a nimble team that can pivot between responsibilities (and tiers)
- Support business continuity
- Provide a more engaging atmosphere and reduce staff burnout
- Promote an environment of continuous learning
- Provide greater coverage with less staff by relying on the right technology to get the job done
- Maintain a work/life balance while giving SOC engineers a feeling of positive control of their destinies
