- 1. 1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
- 2. 1980s: TCP/IP and the Public's Introduction to the Internet
- 3. 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 4. 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- 5. 2010s: A Decade of Digital Transformation
- 6. 2019–Present: The Response to Remote Work and Limitations of VPNs
- 7. VPN History FAQs
- 1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
- 1980s: TCP/IP and the Public's Introduction to the Internet
- 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- 2010s: A Decade of Digital Transformation
- 2019–Present: The Response to Remote Work and Limitations of VPNs
- VPN History FAQs
What Is the History of VPN?
- 1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
- 1980s: TCP/IP and the Public's Introduction to the Internet
- 1990s: The Rise of the Web and Emergence of Early VPN Technologies
- 2000s: VPNs Evolve Alongside Cybersecurity Challenges
- 2010s: A Decade of Digital Transformation
- 2019–Present: The Response to Remote Work and Limitations of VPNs
- VPN History FAQs
The history of the VPN is rooted in the evolution of secure online communication technologies. In the 1960s, ARPANET pioneered the concept of linking distant computers. The subsequent development of protocols like TCP/IP in the 1980s laid the groundwork for modern internet connectivity. From the 1990s onward, specific VPN technologies emerged to address growing concerns about online security and privacy.
1960s–1970s: The Dawn of ARPANET and the Need for Connectivity Across Different Networks
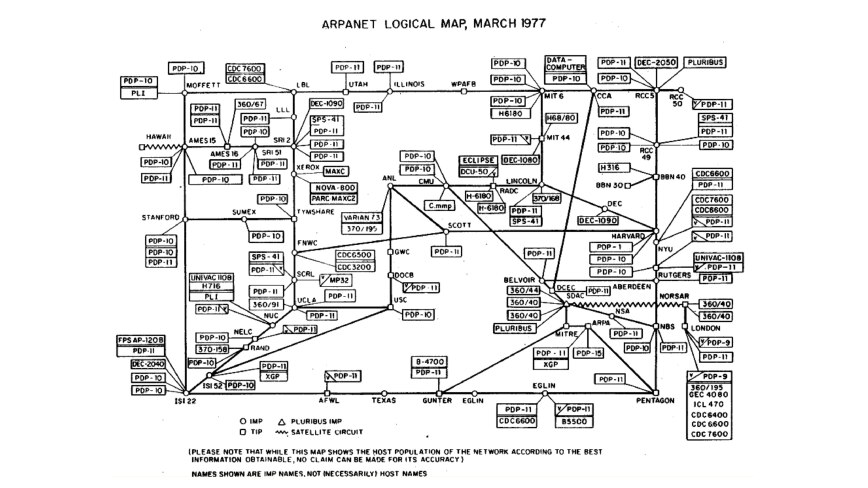
In the late 1960s, the Advanced Research Projects Agency (ARPA) developed a method to link distant computers. They introduced a system in 1969 that relied on packet switching, where data packets transferred between machines. This system, known as ARPANET, grew throughout the 1970s, connecting multiple educational and research institutions.
However, ARPANET had limitations. It operated on the network control protocol (NCP), limiting connections to computers within the same network. The challenge was to find a way to connect devices across varied networks.
1980s: TCP/IP and the Public's Introduction to the Internet
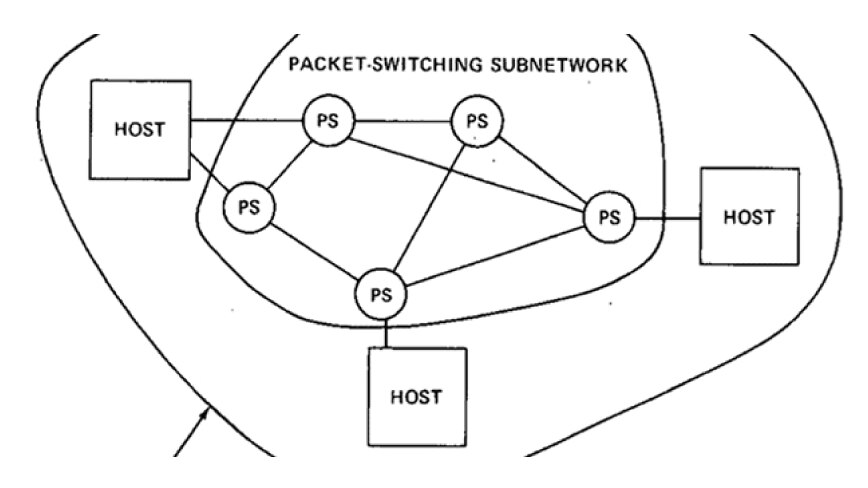
ARPANET's use grew notably within government and educational realms, prompting ARPA to find ways to link varied networks. By the 1980s, they officially adopted the Transmission Control Protocol (TCP), also known as Transmission Control Protocol/Internet Protocol (TCP/IP). The new approach transitioned from NCP to a system allowing diverse device connections, giving rise to what's now termed the internet.
The dominant internet protocols today, IPv4 and IPv6, stem from this TCP/IP protocol collection. An IP comprises unique digits identifying each device online. Accessing online resources demanded the right IP, but remembering numeric sequences wasn't convenient. So, in 1984, the Domain Name System (DNS) was born, mapping simple domain names to IP addresses.
After the establishment of IP and DNS, the internet welcomed the broader public. The inaugural online platform emerged in 1985, allowing users to enter chat rooms and engage in digital communities. Named America Online (AOL), this system relied on dial-up, where users dialed their internet service provider (ISP) to access AOL.
The expansion of online activities paved the way for commercial ISPs. In 1989, "The World," among the initial commercial ISPs, began offering internet connections to users via dial-up.
1990s: The Rise of the Web and Emergence of Early VPN Technologies
In the early 1990s, the introduction of HTTP enabled access to online resources through hyperlinks, leading to the birth of the World Wide Web (WWW).
As the digital realm began to spread beyond academic circles, the ability to communicate securely and privately online became a growing concern. This sparked the development of IP-layer encryption, which can be viewed as a forerunner to today's virtual private networks (VPNs).
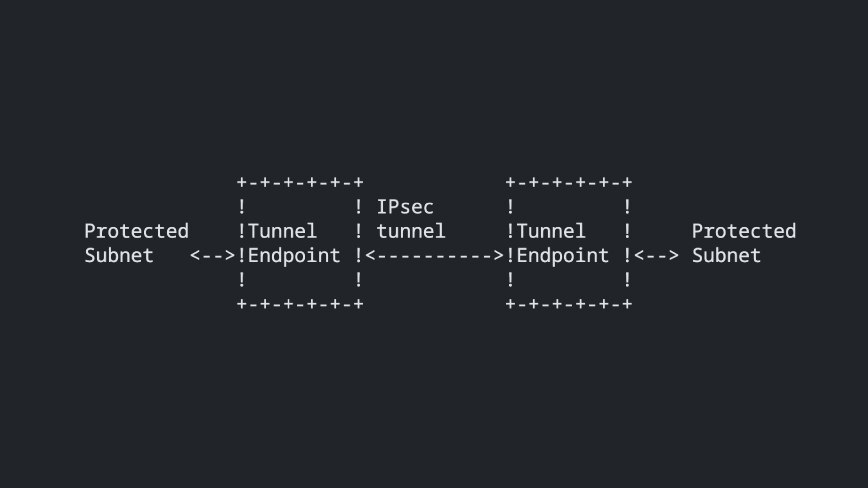
A few years later, AT&T Bell Laboratories showcased the Software IP Encryption Protocol (SwIPe), an effort that effectively demonstrated the potential of IP layer encryption. This innovation had a significant influence on the development of IPsec, an encryption protocol that remains in widespread use today.
IPsec, introduced around the mid-1990s, provided end-to-end security at the IP layer, authenticating and encrypting each IP packet in data traffic. Notably, IPsec was compatible with IPv4 and later incorporated as a core component of IPv6. This technology set the stage for modern VPN methodologies.
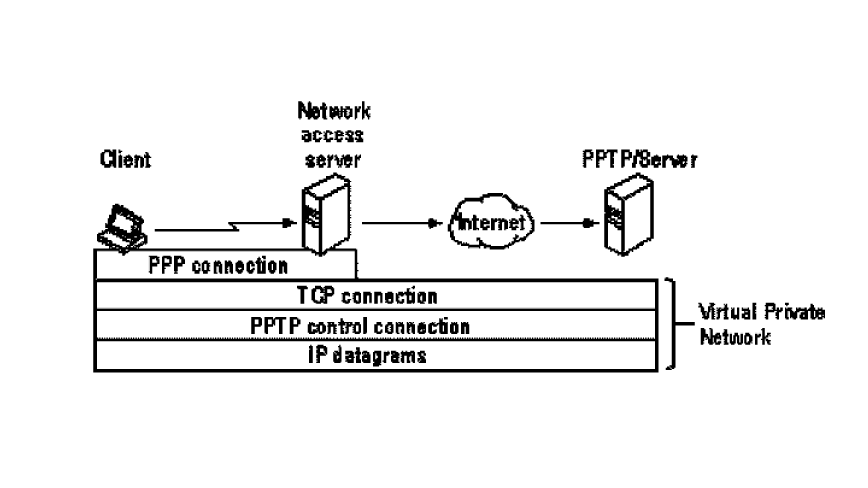
By the latter half of the decade, Microsoft introduced Point-to-Point Tunneling Protocol (PPTP), often credited to Microsoft employee and engineer Gurdeep Singh-Pall. PPTP marked a significant milestone in the evolution of VPN technology. This system encapsulated PPP packets, creating a virtual data tunnel to ensure more secure data transmission over the web.
Following closely, Cisco presented L2F, a protocol addressing the shortcomings of PPTP by accommodating multiple types of internet traffic and introducing enhanced encryption methods.
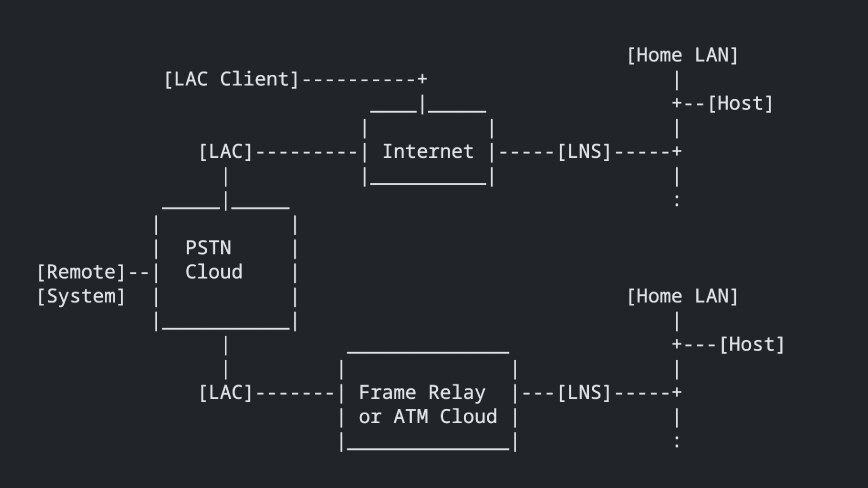
Eventually, a collaborative initiative between Microsoft and Cisco produced L2TP, which melded the strengths of both tunneling protocols, PPTP and L2F. This advanced protocol simplified VPN utilization and bolstered the security of data tunneling across IP networks.
Further reading:
2000s: VPNs Evolve Alongside Cybersecurity Challenges
The 2000s marked a significant shift in online security. As the internet became an integral part of daily life and work, the threats and challenges grew. VPNs emerged as a vital tool for businesses and individuals, ensuring online privacy and security in an increasingly interconnected world.
In the early 2000s, as the internet's adoption skyrocketed, businesses recognized the potential of an online presence and transitioned to the digital realm, creating websites, establishing e-commerce platforms, and integrating online payment systems.
Alongside these opportunities, the rise of cybercrimes became more pronounced. Vulnerabilities in the rapidly advancing internet technology became a target for malicious actors. The global nature of the internet presented challenges, as attackers could target victims worldwide. Social networking sites inadvertently created platforms for phishing and social engineering.
As businesses became more reliant on online operations, there was an urgent need to secure data. Initially, companies gravitated toward wide area networks (WAN) for security, but high costs led them to explore VPNs. Notably, during this period, James Yonan developed OpenVPN for personal use. This open-source protocol, along with the SSL VPN, became prominent solutions for businesses.
During the mid-2000s, individual users became more aware of online security. Public networks, particularly in cafes and airports, turned into hunting grounds for hackers. Consequently, the need for online privacy tools surged among individual internet users, too.
By 2005, recognizing the need for user-friendly security tools, the first commercial VPNs appeared, simplifying the previously complex setup processes. The decade concluded with VPNs evolving as essential tools, leading to an increase in third-party VPN service providers and innovative protocols like IKEv2/IPsec and SSTP.
Further reading:
2010s: A Decade of Digital Transformation
The 2010s marked significant internet growth. IT advancements led to a global online network affecting work and leisure. Cyberthreats rose in severity and number.
The internet of things enabled diverse devices to connect online. Smart assistants enhanced user experience. The gaming sector introduced online multiplayer games. Online retail growth shifted consumers to mobile shopping.
Streaming services like Netflix expanded, which introduced competition among platforms. New online professions emerged, necessitating reliable internet connections. ISPs faced demands for better speed and service.
As more activities moved online, the need for strong security solutions became evident. VPNs gained popularity due to the increasing online data vulnerabilities. VPN service providers responded by broadening their offerings and introducing features like no-logs policies, kill switches, and multihop connections.
VPN competition led to improved connection speeds and user-friendly designs. WireGuard emerged as a notable VPN protocol in the late 2010s, distinguished for its efficient encryption and adaptability to network changes.
Enterprises recognized the importance of secure networking. Solutions like SD-WAN and SASE rose to prominence, catering to requirements for secure and scalable business network connections.
Further reading:What Is WireGuard?
2019–Present: The Response to Remote Work and Limitations of VPNs
The 2020 COVID-19 outbreak intensified the need for secure online activities, emphasizing the importance of remote access VPNs. As organizations transitioned online, the demand for reliable VPNs grew. Remote access VPN providers expanded server capabilities, adopted multifactor authentication, and integrated malware protection.
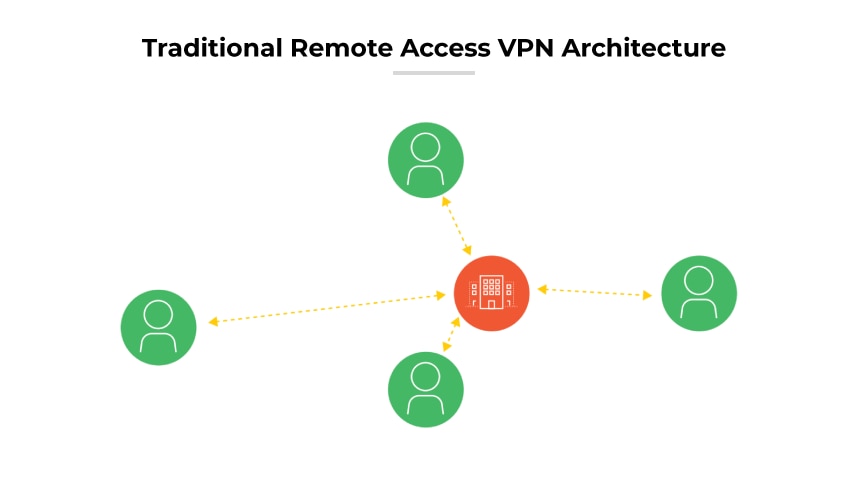
Today, remote work persists. But there’s a problem. Architecturally, remote access VPN is a hub-and-spoke architecture, with users sitting in spokes of various lengths depending on their distance from the hub (the internal data center). The distance reduces performance and introduces latency problems, but this remains the optimal architecture for data center applications because the goal is to reach the hub.
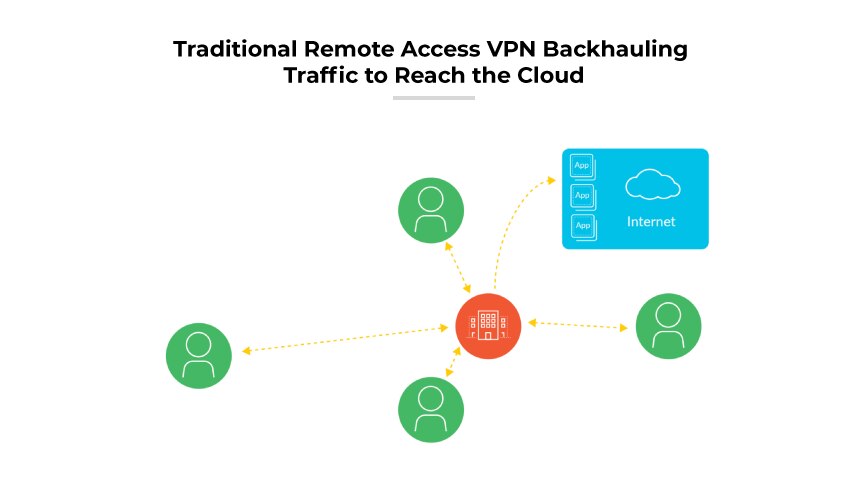
The model breaks down when there are cloud applications in the environment. Traffic in a remote access VPN always goes to the VPN gateway first, even if the application is hosted in the cloud. As a result, the traffic goes to the VPN gateway at headquarters, then egresses from the corporate perimeter firewall to the internet, with the application response going back to headquarters before it returns to the user.
Although this is reasonable from a security perspective, it doesn’t make sense for network optimization. To compensate for the networking difficulties with remote access VPN, organizations often make compromises that have negative security implications, including user-initiated tunnels, split-tunnel VPN, and web proxies.
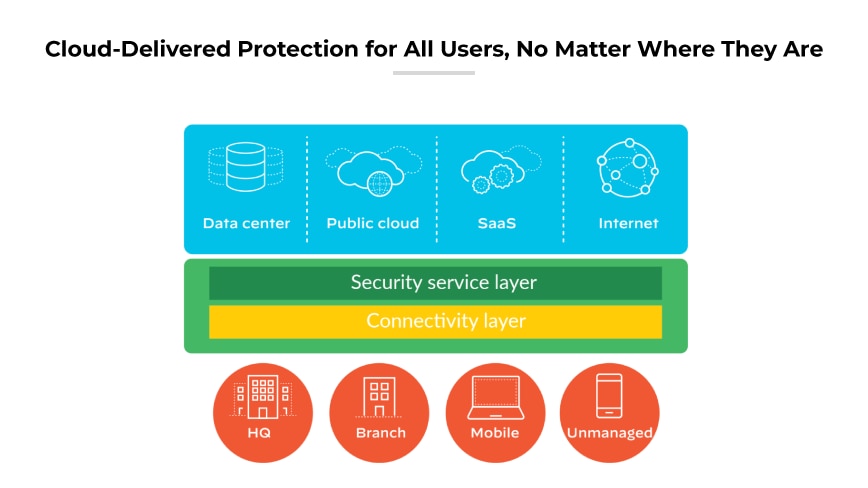
With the rapid growth of remote workforces and cloud-based applications, organizations are finding that remote access VPN is neither optimized for the cloud nor secure. An innovative approach is necessary to account for today’s application mix: A modern architecture for the mobile workforce.
Today’s mobile workforce needs access to the data center, the internet, and applications in public, private, and hybrid clouds. In other words, the proper architecture should optimize access to all applications, wherever they or the users are located.
Remote access VPN has been an enterprise network staple for years. However, as enterprises rapidly adopt more cloud applications, their security and networking needs are changing fundamentally. After a long history of the VPN’s evolution, so too must the solutions.
Further reading:
Sources
- https://www.computerhistory.org/collections/catalog/102646704
- https://www.darpa.mil/about-us/timeline/tcp-ip
- http://technet.microsoft.com/en-us/library/cc768084.aspx
- https://datatracker.ietf.org/doc/html/rfc2661
- https://datatracker.ietf.org/doc/html/rfc4306