What Are Firewall Rules? | Firewall Rules Explained
Firewall rules are specifications set by network administrators that instruct a firewall on how to process incoming and outgoing network traffic. They play an essential role in network security by dictating how firewalls should handle traffic based on parameters such as source or destination IP addresses, ports, and protocols.
Types of firewall rules include:
- Access rules
- Network address translation (NAT) rules
- Stateful packet filtering
- Application level gateways
- Circuit-level gateways
How Do Firewall Rules Work?

Firewall rules work as predetermined conditions that govern traffic flow through the network. When data packets arrive at the firewall, the firewall scrutinizes them against these rules to determine legitimacy.
Firewall rules are specific directives within the broader scope of firewall settings. Rule configuration allows the firewall to identify permissible sources, destinations, and ports, only allowing through traffic that complies with these set parameters. Firewall rules act on the principle of least privilege. This means they only grant access when necessary, which reduces the risk of unauthorized intrusion, as well as internal and external threats.
In enterprise environments, access control lists (ACLs) specify firewall rules, providing detailed lists of permissions that instruct the firewall on which traffic to allow or block. Each ACL contains numerous rules, each with conditions traffic must meet to either proceed or halt. These conditions typically include source and destination IP addresses, port numbers, and protocols used for the communication attempt. The firewall evaluates each packet against the ACLs in a sequential manner, processing rules from the top down. Once the firewall matches the packet to a rule, it executes the action associated with that rule—allow, deny, or reject.
Firewalls maintain a default policy to deny all traffic that does not explicitly match any rule. This fortifies the network against unforeseen vulnerabilities. Sophisticated firewalls may incorporate stateful inspection to monitor ongoing connections, ensuring incoming traffic is part of an established session initiated by an internal user.
Why Are Firewall Rules Important?
Firewall rules are a critical network security component. These rules act as a filter between a company’s internal private network and external sources, allowing administrators to control traffic flow. By defining a set of conditions for traffic evaluation, firewall rules play an instrumental role in defending against cyber threats, unauthorized access, and safeguarding sensitive data.
The significance of firewall rules extends beyond mere access control. They also enforce a company's security policies at the network level. Consistently updated and managed firewall rules ensure that firewalls only facilitate legitimate, secure traffic. Understanding firewall rules and their importance preserves the integrity of an organization’s data infrastructure.
Types of Firewall Rules

Access Control Rules
Access control rules are crucial in defining which traffic the firewall permits to enter or exit a network. They are based on criteria such as IP addresses, port numbers, and protocols to make real time decisions, enabling secure and controlled connectivity between different network zones.
Network Address Translation Rules
Network address translation (NAT) rules are essential for routing traffic between private and public IP addresses. They translate addresses and ports of transiting packets, helping to obscure the internal network structure.
Application-Level Gateways
Application-level gateways, or proxy firewalls, scrutinize traffic at the application layer. They apply security measures for specific applications. This allows for a more granular traffic inspection, ensuring the firewall allows only safe application traffic through.
Stateful Inspection Rules
Stateful inspection rules monitor the state of active connections and make decisions based on the context of traffic. This method tracks each connection traversing the firewall and ensures only packets matching a known active connection can pass.
Circuit-Level Gateways
Circuit-level gateways enforce security measures at the session layer of the OSI model. They monitor TCP handshakes across the firewall to ensure sessions initiate in a trusted manner, permitting or denying traffic without inspecting the packets deeply.
Examples of Firewall Rules
Firewall rule configuration specifies specific attributes to effectively manage and monitor data flow.
Consider an example where a firewall rule denies all traffic to a particular internal IP address from any source. This measure secures critical systems from external threats. Conversely, a rule could allow all outgoing traffic from the trusted internal network, facilitating necessary business operations while keeping stringent checks on incoming data packets
| Firewall Rule Example | ||||
|---|---|---|---|---|
| Source Address | Source Port | Destination Address | Destination Port | Action |
| 192.168.1.2 | 80 | 10.10.10.20 | 22 | Allow |
| 10.10.0.0/24 | Any | 192.168.0.0/24 | 443 | Deny |
| Any | Any | Any | Any | Deny |
This is a simplistic representation of firewall rules in an enterprise setting. It exhibits the granular control over network access, but also demonstrates how the configuration of rules aligns with security policies and business needs.
In an enterprise context, administrators must construct a series of such rules to establish a robust defense mechanism. These rulesets are often complex and meticulously arranged in a hierarchy, ensuring optimal network protection.
Firewall Rules Order
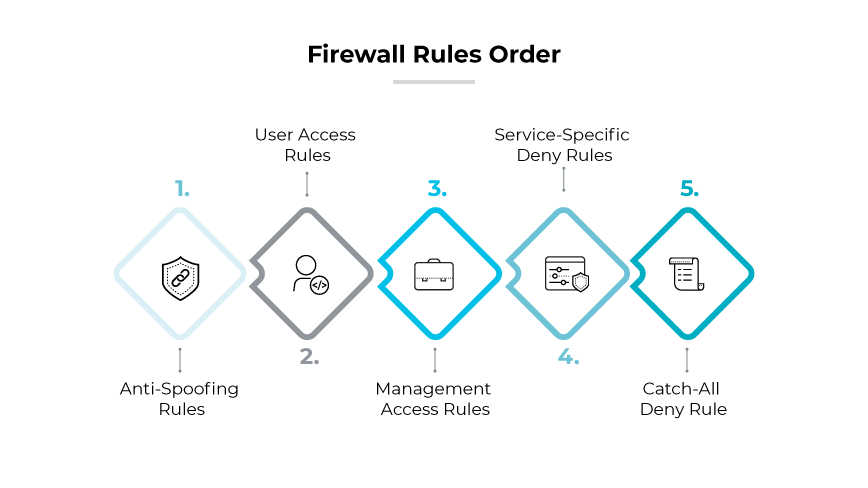
The ordering of firewall rules is important because firewalls process rules sequentially, typically from the top down. This ordered structure is imperative because once a rule matches a packet, the firewall does not evaluate subsequent rules. More specific rules must precede more general ones to ensure proper traffic filtering and avoid unintended blocking or allowing of traffic. Incorrect ordering can lead to security vulnerabilities, reduced network performance, or blocked legitimate traffic.
Firewall protocol best practices recommend creating and configuring firewall rules in the following order:1
- Anti-Spoofing Rules: Placed at the top to ensure traffic is arriving from a legitimate source and not from malicious actors impersonating trusted sources.
- User Access Rules: Dictates what standard users are permitted to do, typically enabling essential services like HTTP for web access.
- Management Access Rules: Defines what network management tools or addresses are allowed to interact with the firewall for monitoring and configuration purposes.
- Service-Specific Deny Rules: These rules block specific services that are known to be unnecessary or vulnerable, reducing noise and potential attack vectors.
- Catch-All Deny Rule: Positioned at the bottom, this rule ensures any traffic not explicitly allowed by previous rules is denied by default, enforcing a least privilege approach.
What Are Inbound and Outbound Firewall Rules?
In a firewall ruleset, inbound rules identify the types of traffic the firewall allows in the network.
Inbound traffic rules detail allowed connections, originating ports, and source addresses. When there are no inbound rules specified, the firewall does not allow inbound traffic. Inbound rules protect the network from unsanctioned access, harmful entities, and DoS attacks.
Outbound rules determine the nature of traffic exiting the network, specifying permissible destination addresses, ports, and protocols. Without explicit outbound rules, the firewall blocks all outbound traffic by default.
How to Manage Firewall Rules
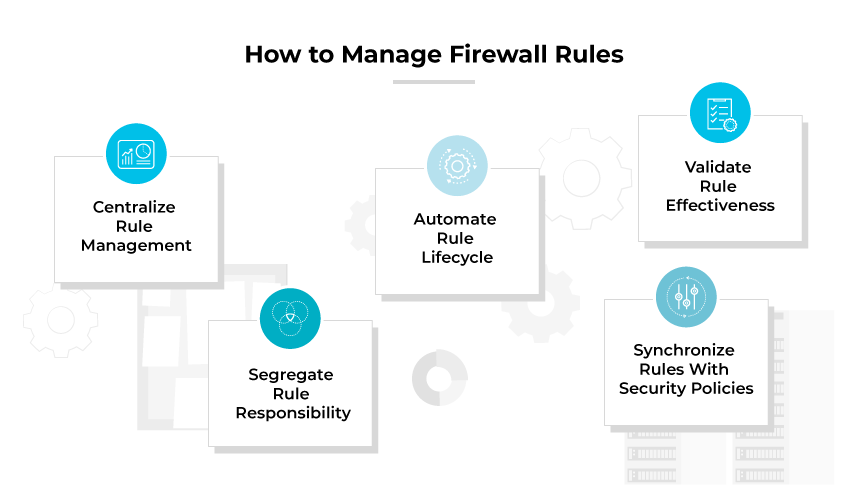
Managing firewall rules is crucial to maintaining network security and ensuring proper regulation of data flows in and out of a network. It is essential to strike a balance between accessibility, functionality, and security to ensure network protection without impeding business operations. These tasks are an ongoing process and require vigilance and attention to detail.
Centralize Rule Management
Centralizing the management of firewall rules is imperative for consistency and oversight. Using centralized management software, network administrators can oversee and modify rules across multiple firewalls, ensuring uniform application and synchronized changes.
Automate Rule Lifecycle
Automating the lifecycle of firewall rules enhances efficiency and reduces the margin of error. This involves setting up processes that automate the creation, review, and retirement of rules based on certain triggers or schedules. An automated rule lifecycle ensures rules are up-to-date and relevant to the current network environment.
Segregate Rule Responsibility
Differentiating responsibilities among team members can prevent unauthorized changes to firewall configurations. Segregating duties ensures only qualified personnel with the necessary knowledge and permissions can make changes to the firewall rules, which mitigates risks associated with unauthorized access or errors.
Synchronize Rules with Security Policies
It is important to align firewall rules with the organization’s overall security policies. This alignment ensures firewall rules reflect the security stance of the organization and that firewall configurations reflect policy changes promptly.
Validate Rule Effectiveness
Regularly validating the effectiveness of firewall rules is essential. This includes conducting tests to ensure rules are performing as intended and reviewing rules to confirm they are necessary, efficient, and do not inadvertently introduce security vulnerabilities.
Best Practices for Firewall Rules

Regular Evaluation of Firewall Rules
Firewall rules require consistent review to ensure they remain effective against evolving threats. This ongoing process includes the removal of obsolete or redundant rules, adjustment to counteract new vulnerabilities, and adherence to evolving compliance requirements. Effective evaluation practices contribute to both network security and adherence to data protection regulations.
Monitoring Traffic and Logs
Continuous monitoring of firewall logs is critical for identifying patterns of traffic and potential security incidents. Logs provide valuable insights into the nature of traffic, enabling network administrators to respond proactively to anomalies. This level of oversight is key to maintaining an understanding of network behavior and security posture.
Simplification Through Rule Categorization
Organizing firewall rules into categories based on function or characteristic simplifies management and reduces the potential for configuration errors. This categorization can also enhance the performance of the firewall by streamlining the rule evaluation process, improving network traffic throughput.
Enforcement of Least Privilege Principle
The principle of least privilege must apply rigorously within firewall rule configurations. Access permissions should be based solely on the minimum requirements necessary for a user or application to function. This strategy mitigates the risk of unauthorized access and potential internal threats.
Proactive Port Management
Blocking unnecessary or high risk ports is a fundamental aspect of firewall administration. Instituting a stringent policy on port access can significantly reduce the network’s exposure to attacks. A predefined list of restricted ports can serve as a reference for administrators to fortify the network's defenses.1
| Port Restrictions | ||
|---|---|---|
| Service | Port Type | Port Number |
| DNS Zone Transfers | TCP | 53 |
| TFTP Daemon | UDP | 69 |
| Link | TCP | 87 |
| SUN RPC | TCP & UDP | 111 |
| BSD UNIX | TCP | 512-514 |
| LPD | TCP | 515 |
| UUCPD | TCP | 540 |
| Open Windows | TCP & UPD | 2000 |
| NFS | TCP & UPD | 2049 |
| X Windows | TCP & UPD | 6000 - 6255 |
| Small services | TCP & UPD | 20 and below |
| FTP | TCP | 21 |
| SSH | TCP | 22 |
| Telnet | TCP | 23 |
| SMTP (except external web servers) | TCP | 25 |
| NTP | TCP & UDP | 37 |
| Finger | TCP | 79 |
| HTTP (except to external web servers) | TCP | 80 |
| POP | TCP | 109 & 110 |
| NNTP | TCP | 119 |
| NTP | TCP | 123 |
| NetBIOS in Windows NT | TCP & UDP | 135 |
| NetBIOS in Windows NT | UDP | 137 & 138 |
| NetBIOS | TCP | 139 |
| IMAP | TCP | 143 |
| SNMP | TCP | 161 & 162 |
| SNMP | UDP | 161 & 162 |
| BGP | TCP | 179 |
| LDAP | TCP & UDP | 389 |
| SSL (except to external web servers) | TCP | 443 |
| NetBIOS in Win2k | TCP & UDP | 445 |
| Syslog | UDP | 514 |
| SOCKS | TCP | 1080 |
| Cisco AUX port | TCP | 2001 |
| Cisco AUX port (stream) | TCP | 4001 |
| Lockd (Linux DoS Vulnerability) | TCP & UDP | 4045 |
| Cisco AUX port (binary) | TCP | 6001 |
| Common high order HTTP ports | TCP | 8000, 8080, 8888 |
1SANS Institute Firewall Checklist