-
- What created the need for NGFWs?
- How does an NGFW work?
- What are the limitations of traditional firewalls?
- What are the features of an NGFW?
- What are the benefits of an NGFW?
- What are the most common NGFW misconceptions?
- What are the differences between NGFWs and traditional firewalls?
- What to look for in an NGFW solution
- How to successfully deploy NGFWs in 11 steps
- How do NGFWs compare with other security technologies?
- NGFW FAQs
What Is a Next-Generation Firewall (NGFW)? A Complete Guide
14 min. read
Table of contents
A next-generation firewall (NGFW) is a network security device that identifies and controls applications, users, and content to enforce precise security policies.
It inspects traffic beyond ports and protocols to detect threats and prevent misuse of legitimate applications. It also integrates core firewall functions with intrusion prevention and threat detection capabilities to provide consistent, in-line protection.
What created the need for NGFWs?
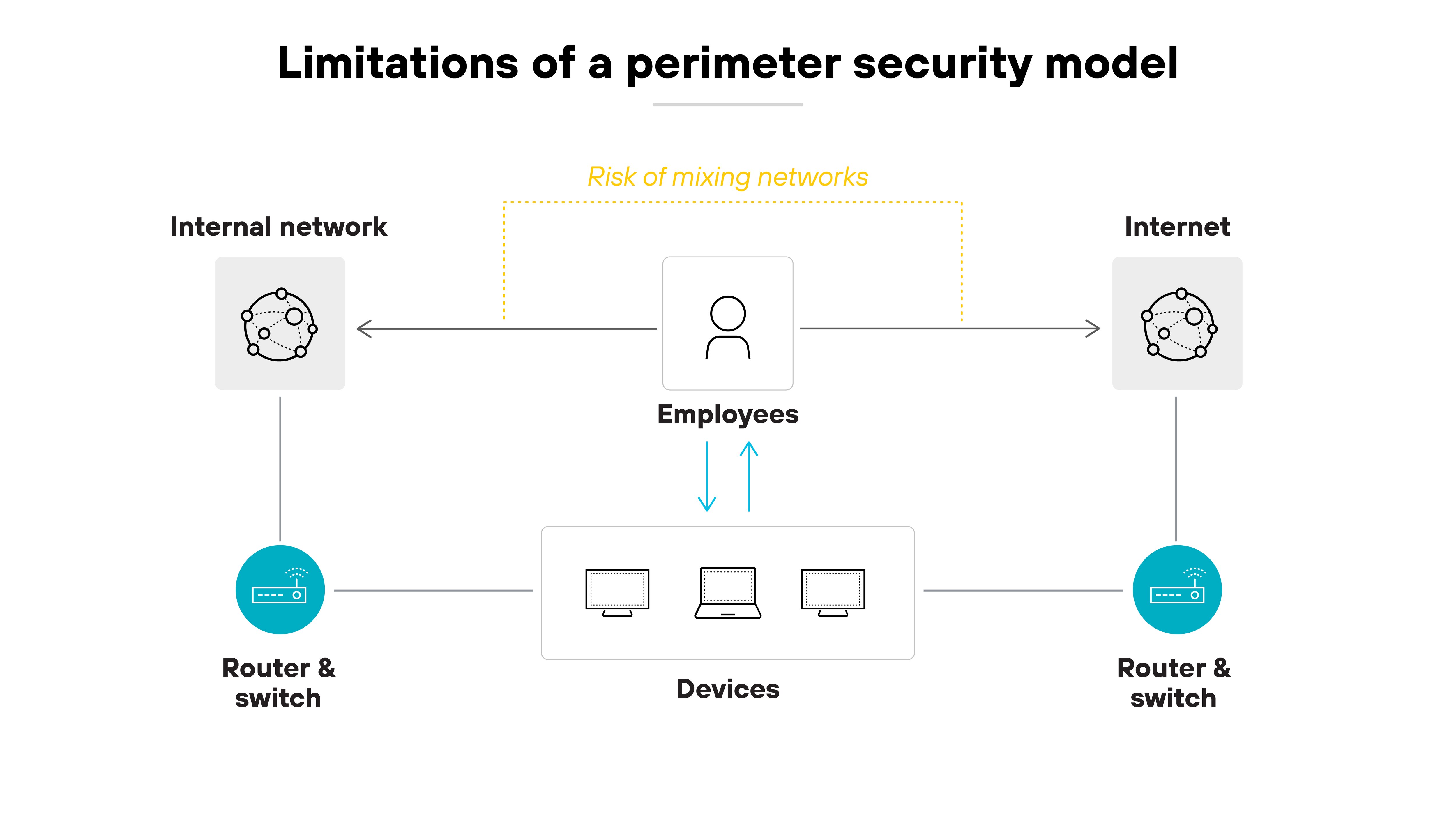
NGFWs emerged because perimeter security wasn't enough. Network security needed more context. More control. And a better way to handle complex, encrypted, and evasive traffic.
More specifically:
In the late 2000s, applications started behaving differently. Many used the same ports. Or tunneled through SSL. This made it harder for traditional firewalls to tell good from bad—or even know which app was running.
At the same time, threats got more evasive. Malware could hide in encrypted traffic. Attacks targeted specific apps, users, and data.
Traditional tools couldn’t keep up. They lacked application awareness. They couldn’t inspect encrypted content. And they couldn’t tie traffic back to users in meaningful ways.
That's what created the need for next-generation firewalls (NGFWs).
In 2008, Palo Alto Networks delivered the industry's first next-generation firewall–and it was a new era in network security technology.
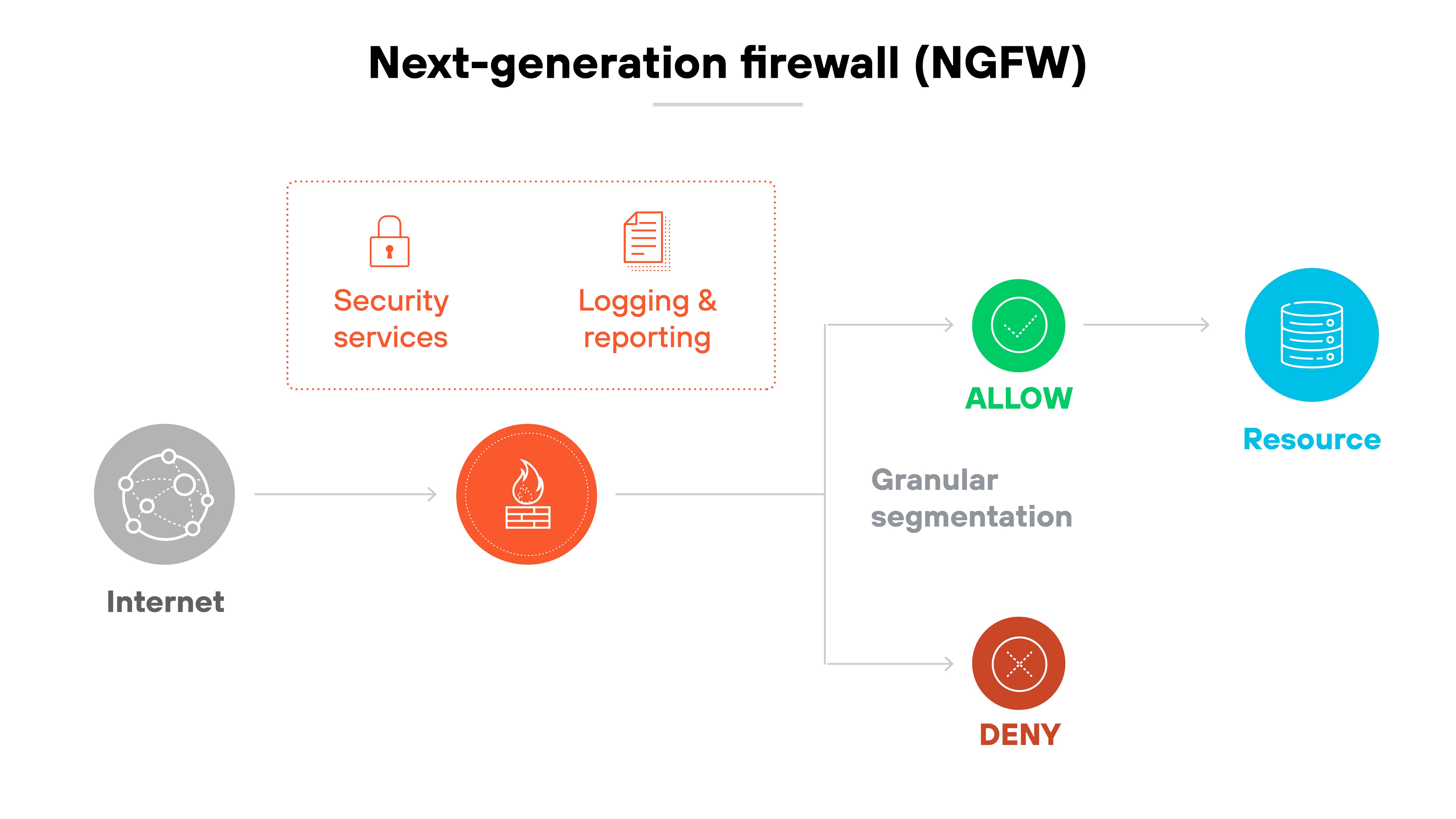
The NGFW was designed to provide deeper visibility and smarter enforcement. They combined traditional firewall capabilities with integrated intrusion prevention and full-layer inspection. They recognized traffic based on apps, not just ports. And they helped enforce policy based on who was using what—making them better suited to the risks of modern networks.
| Further reading: The History of Firewalls | Who Invented the Firewall?
How does an NGFW work?
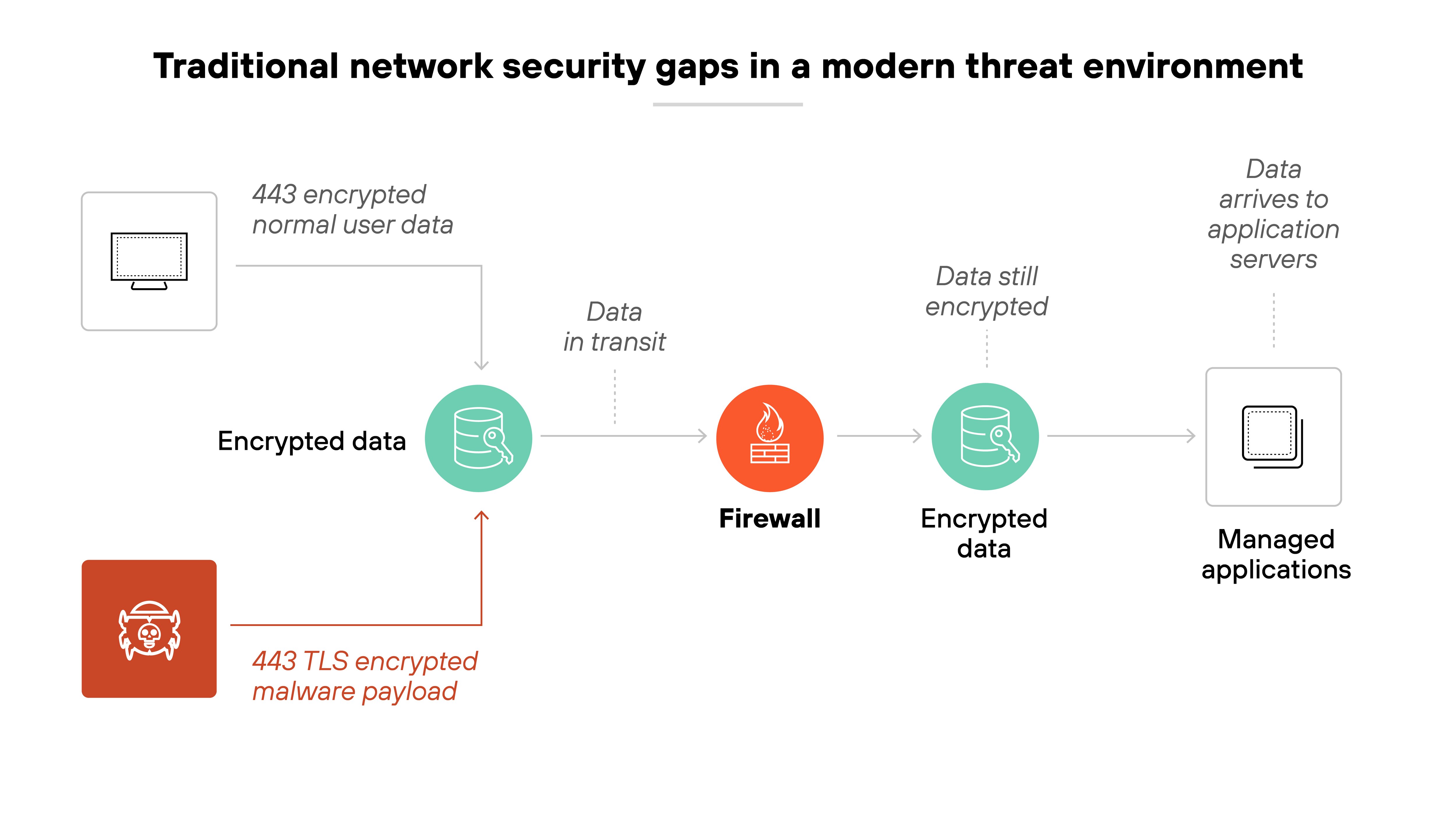
An NGFW analyzes network traffic beyond basic IP addresses and ports. It inspects the full packet to understand the application, user, and content involved in each transaction.
In other words:
It doesn’t just ask where the traffic came from. It looks at what the traffic is doing and who’s responsible for it.
NGFWs operate at higher layers of the OSI model, including the application layer. That’s where many threats now live—hidden inside common services like email, file sharing, or web traffic.
By inspecting traffic at Layer 7, an NGFW can recognize specific applications and detect evasive behavior. This allows it to enforce policies based on how applications are actually being used, not just where they appear to go.
Like this:
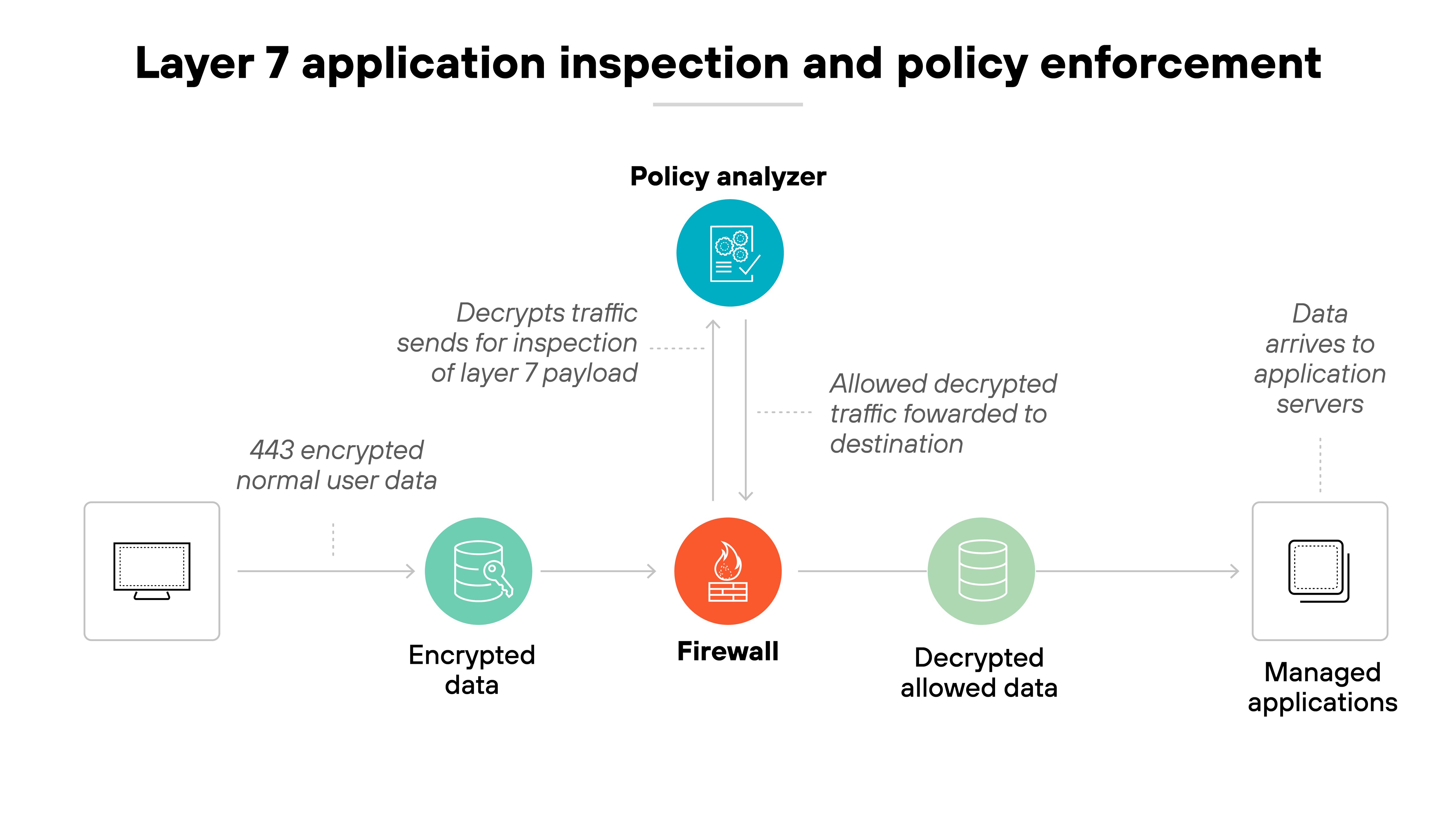
The deeper inspection also supports advanced threat prevention. Malicious traffic can be blocked in real time, even when it mimics normal activity.
| Further reading:
- Layer 3 vs Layer 7 Firewall: What Are the Differences?
- What Does a Firewall Do? | How Firewalls Work
- What Are Firewall Rules? | Firewall Rules Explained
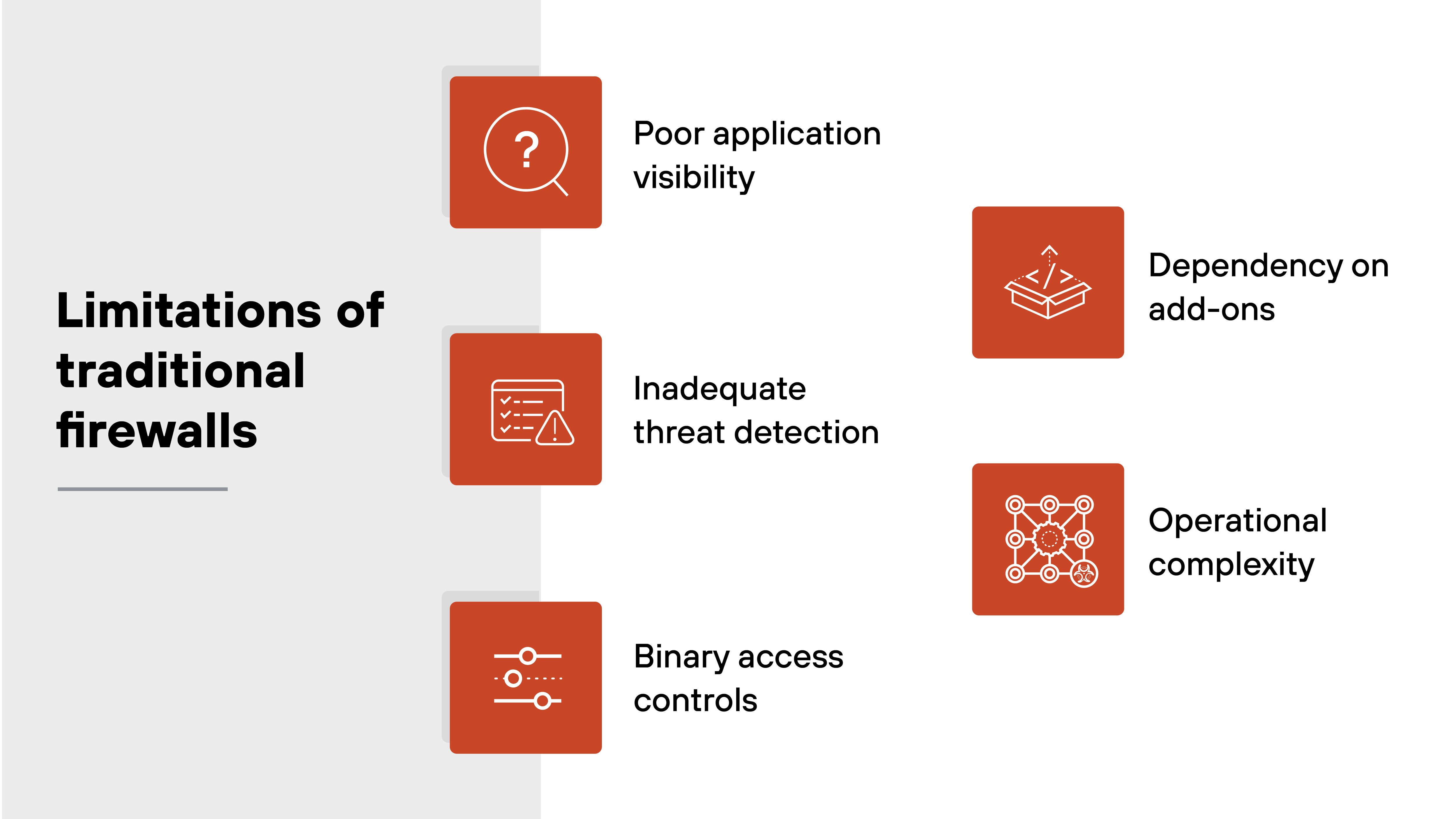
What are the limitations of traditional firewalls?
Traditional firewalls were built for a simpler time—when applications were predictable, threats were slower-moving, and networks had clear perimeters.
But that world doesn’t exist anymore.
As apps became cloud-based, threats more evasive, and users more distributed, the cracks in legacy firewall models started to show.
Let’s unpack the core limitations that prevent traditional firewalls from keeping up with today’s traffic, threats, and operational demands, including:
Poor application visibility
Inadequate threat detection
Binary access controls
Dependency on add-ons
Operational complexity
Poor application visibility
Traditional firewalls rely on ports and protocols to classify traffic. That worked when applications followed fixed port assignments.
Today’s applications don’t. Many use nonstandard ports, port hopping, tunneling, or encryption to get around basic traffic controls. This makes them hard to detect—and nearly impossible to control—with a legacy firewall.
Legacy firewalls assume that a given port equals a specific application. But modern applications don’t follow that rule.
Like this:
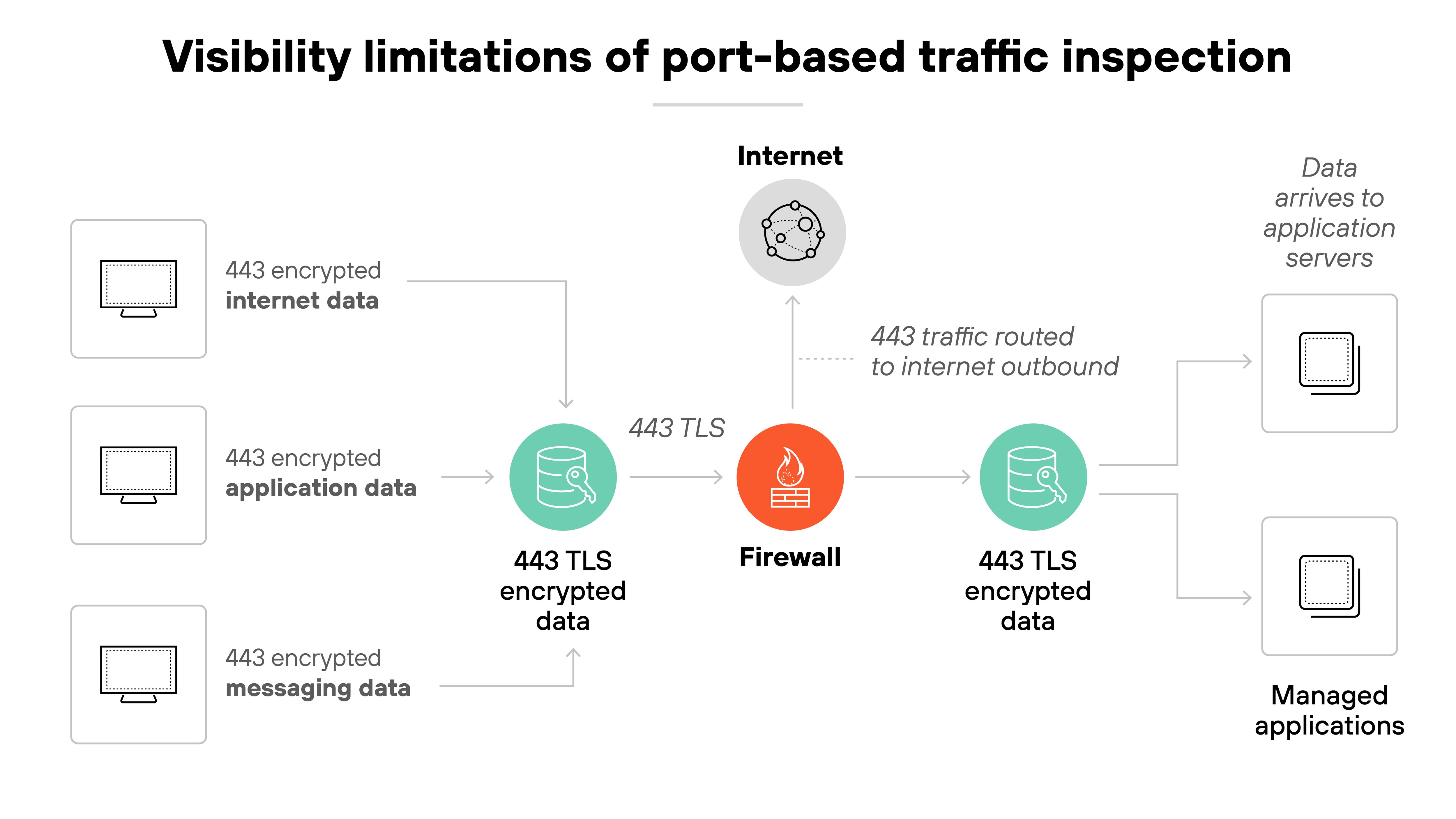
A messaging app might run over port 443, just like any web traffic. To a port-based firewall, it all looks the same. The result is a lack of visibility.
Which means: IT teams can’t see what’s actually being used, much less enforce meaningful controls.
Inadequate threat detection
Older firewalls focus on blocking known threats at the network layer. But most modern attacks happen at the application layer and evolve quickly.
Traditional firewalls don’t inspect enough of the traffic to catch those threats. And if they can’t decrypt and inspect encrypted traffic, they miss even more.
In other words: Traditional firewalls aren’t designed to analyze full sessions.
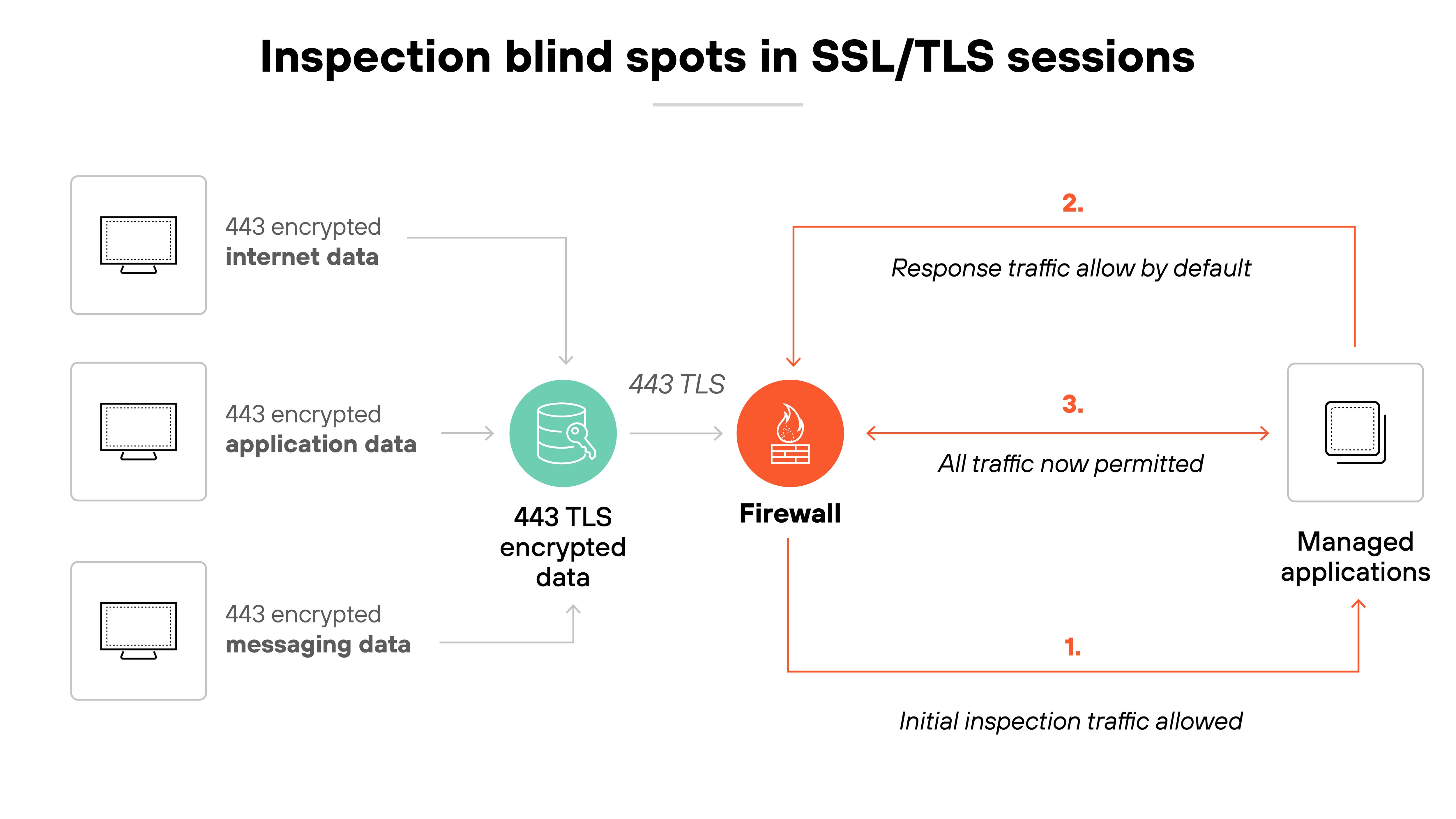
They often check only the initial packet to make a decision. That leaves them blind to payloads that carry malware or exploit code.
And since so much traffic is now encrypted, threats can hide inside SSL or TLS sessions. If the firewall can’t decrypt that traffic, it can’t stop what it can’t see.
Binary access controls
Legacy firewalls are limited to allow or block decisions. They can’t differentiate between safe and risky use of the same application.
That’s a problem when many tools have both legitimate and risky use cases.
For example: A cloud storage app might be fine for collaboration—but a risk for data exfiltration.
Here’s why that matters: Applications aren’t all good or all bad. The same app might be used to share internal files with coworkers—or to send sensitive data outside the company.
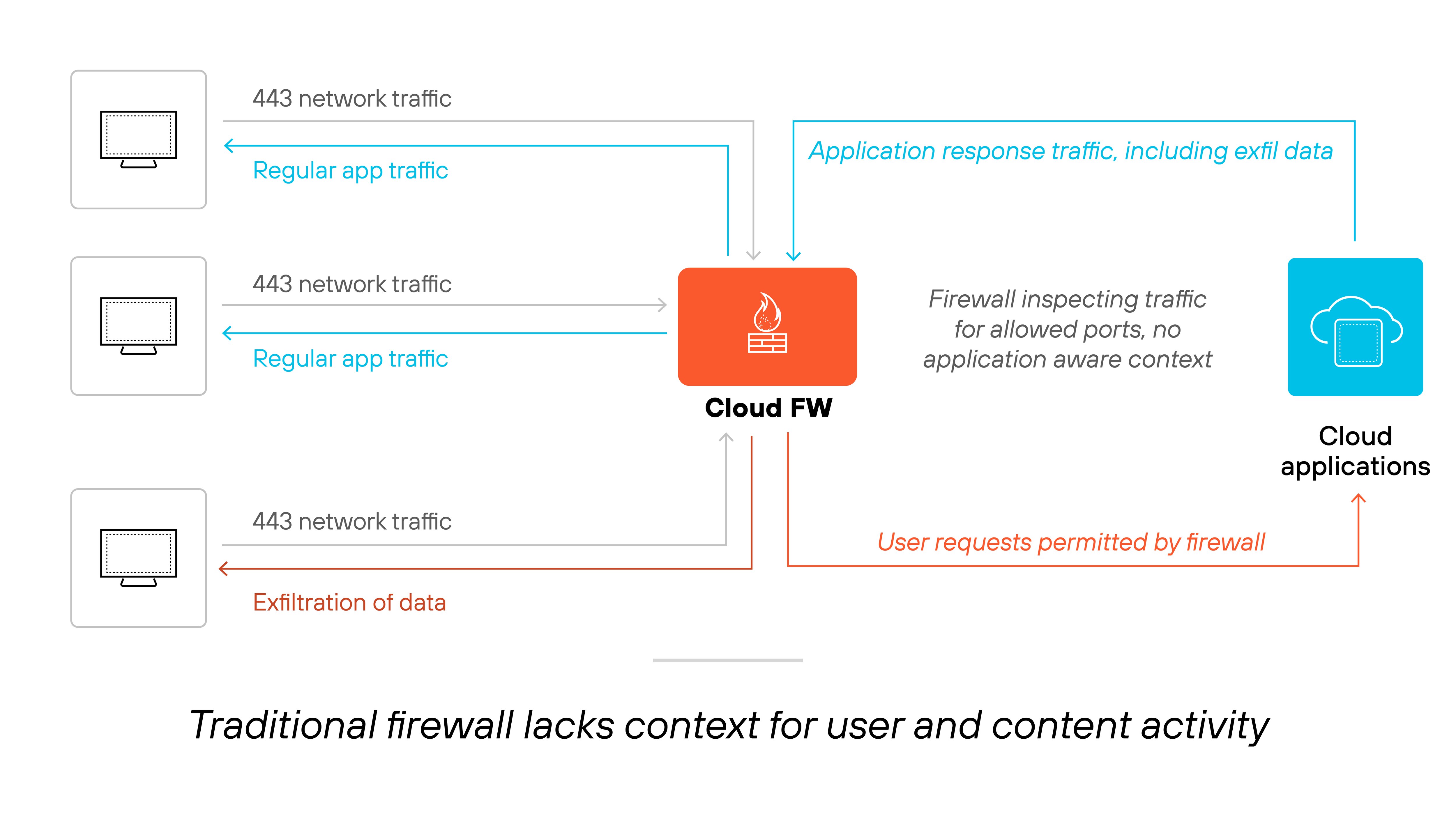
Traditional firewalls lack the context to tell the difference. Without user, content, or function-level awareness, the firewall has no way to enforce nuanced policies.
Dependency on add-ons
To keep up with modern threats, many organizations add separate tools—like intrusion prevention systems, URL filters, or antivirus appliances.
But stitching these together creates complexity. It spreads policy across consoles. And when tools don’t integrate well, it’s easier to miss gaps in coverage.
For example: A port-based firewall might allow traffic based on port 443. An external IPS might try to inspect that traffic. But if the firewall didn’t classify the app correctly—or if the IPS doesn’t see all the traffic—something gets through.
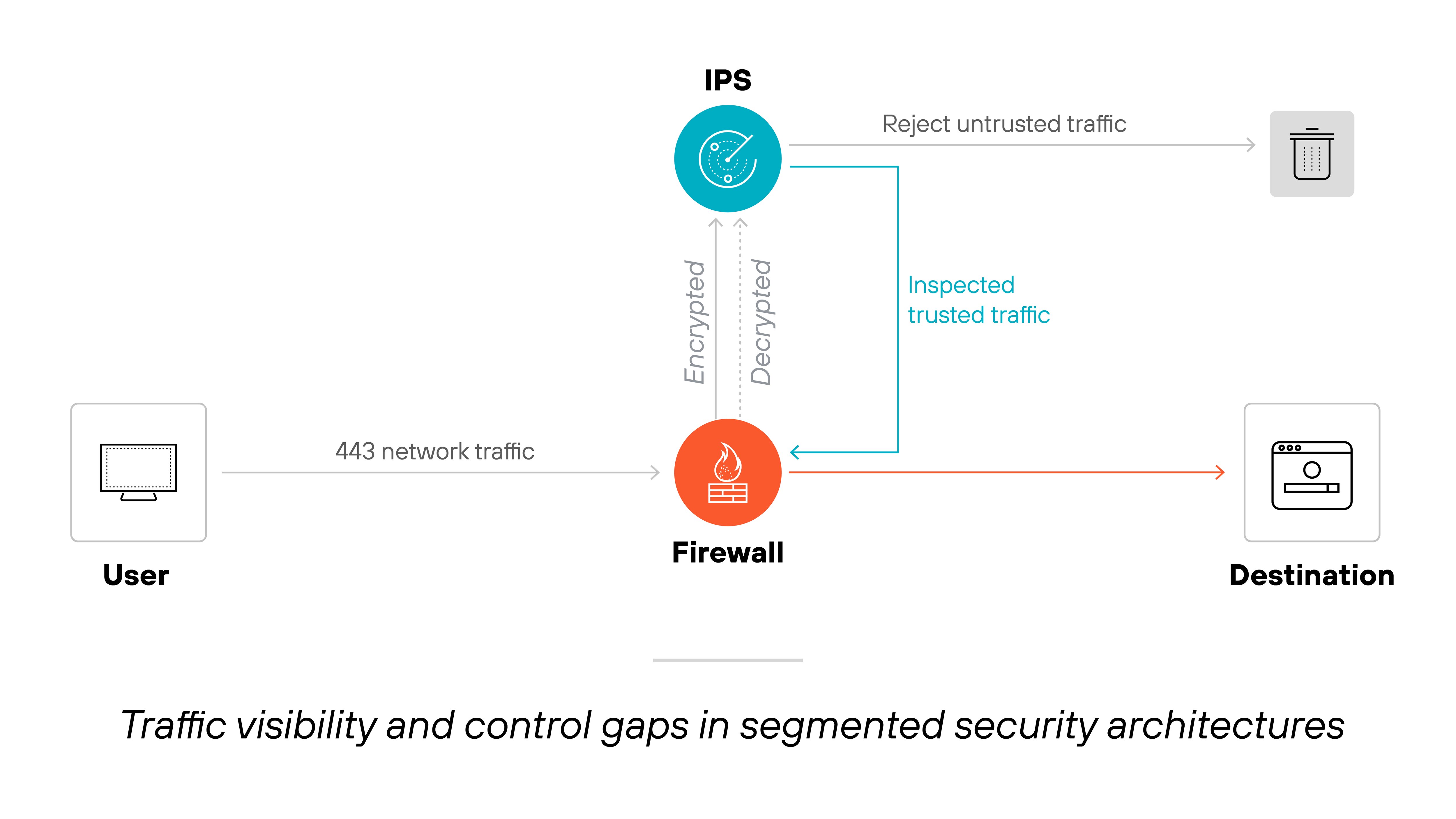
Managing policy across separate tools is hard to scale. And the lack of coordination leads to blind spots.
Operational complexity
Adding more devices and controls doesn’t always improve security.
In fact, it often introduces configuration errors, policy conflicts, and delays in response. Most legacy firewalls weren’t built to scale with today’s hybrid environments. Trying to bolt on features just increases management overhead.
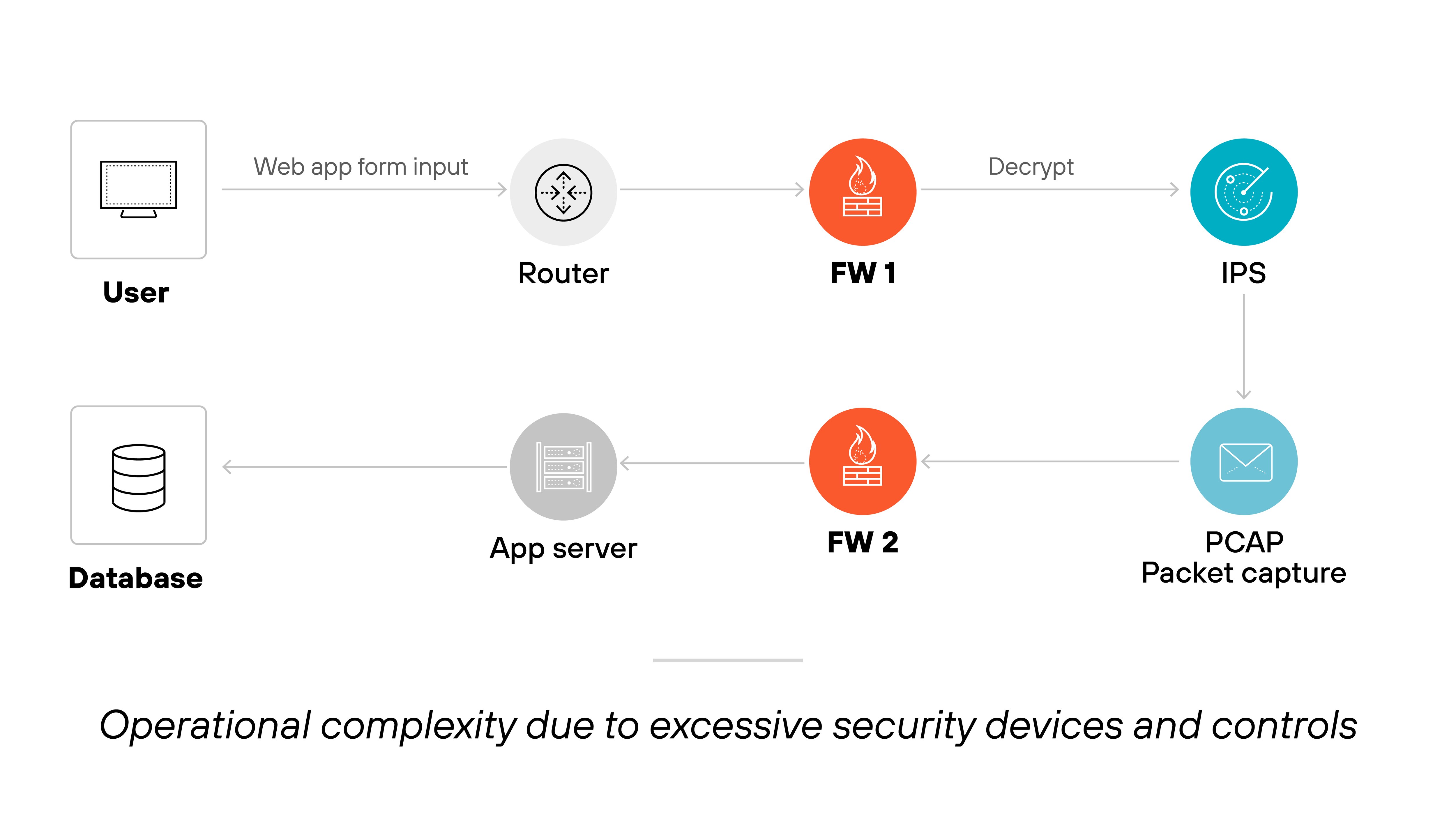
Why not just keep adding tools?
Because more tools mean more rules to manage. More consoles to check. More chances for something to break.
Firewalls built on outdated architectures weren’t designed for deep inspection, identity-based policies, or application-level controls. Patching them with new features only makes operations slower and riskier.
What are the features of an NGFW?
Core vs. modern NGFW features
| Core NGFW features | Modern NGFW features |
|---|---|
|
|
Next-generation firewalls combine traditional traffic filtering with advanced detection, control, and integration capabilities. That makes them fundamentally different from older firewall models.
They don't just block or allow traffic based on ports and IPs. Instead, they inspect traffic deeply—down to the user, app, content, and behavior—so policies can be applied with far more precision.
In other words:
NGFWs enable you to detect and control what's happening on the network. Even if it's encrypted. Even if it's evasive.
This section breaks NGFW features into two groups:
- Core features that define what made NGFWs a major step forward from traditional firewalls
- Modern features that expand their role with cloud integration, AI/ML, and Zero Trust capabilities
Let's start with the foundation.
Core NGFW features (up to 2020)
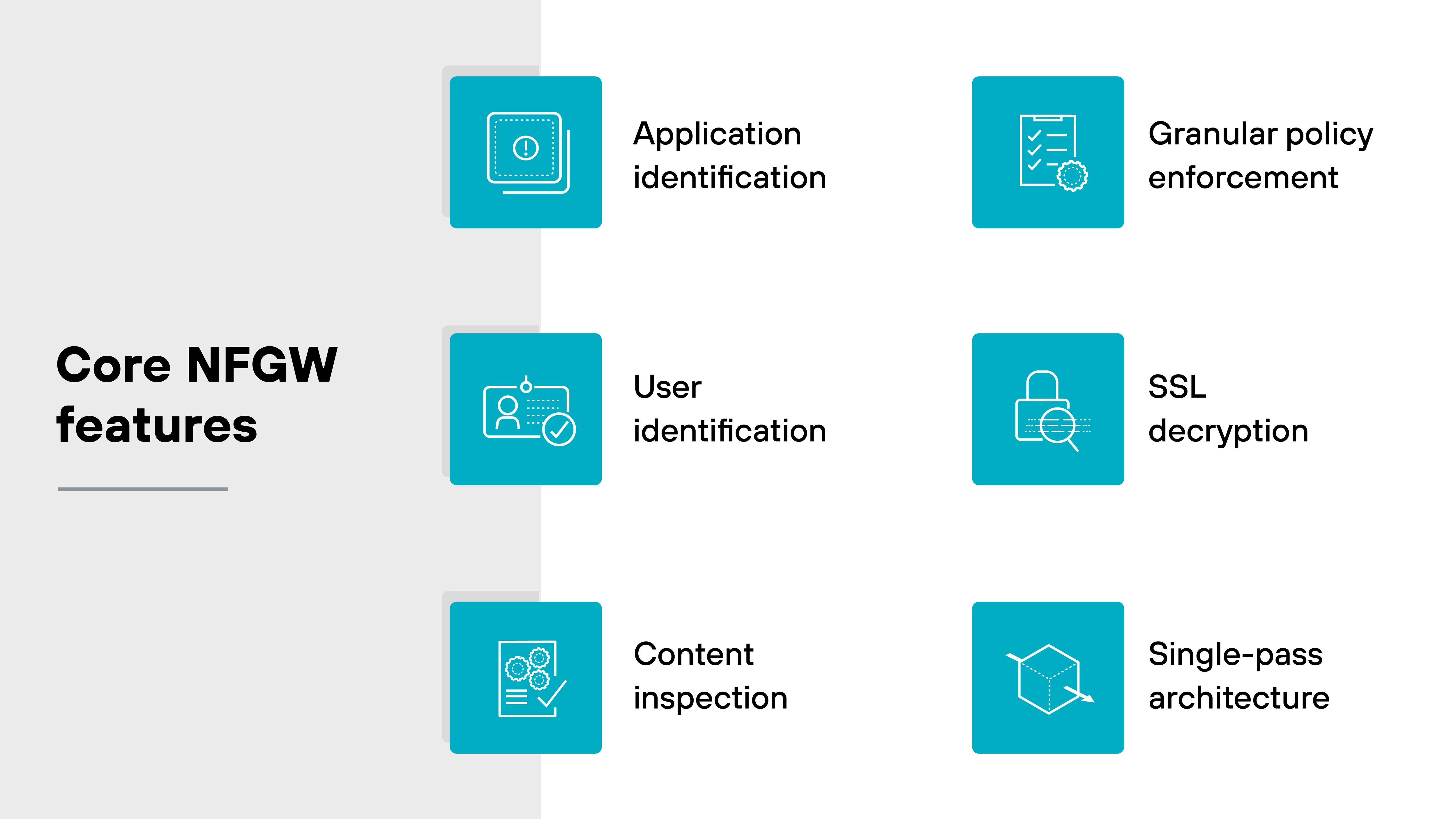
The original promise of the next-generation firewall was to close critical security gaps left by legacy firewalls.
Traditional models filtered traffic by IP address and port. That wasn’t enough once applications began evading controls and threats moved up the stack. NGFWs introduced deeper inspection and smarter enforcement—without sacrificing performance.
This section covers the core capabilities that defined early NGFWs. These features are still foundational today, enabling traffic classification, user awareness, content scanning, and policy precision.
Let’s break them down.
Application identification
Application identification allows NGFWs to classify traffic based on the actual application, not just the port or protocol. This means the firewall can detect and control evasive or encrypted applications that legacy systems would miss.
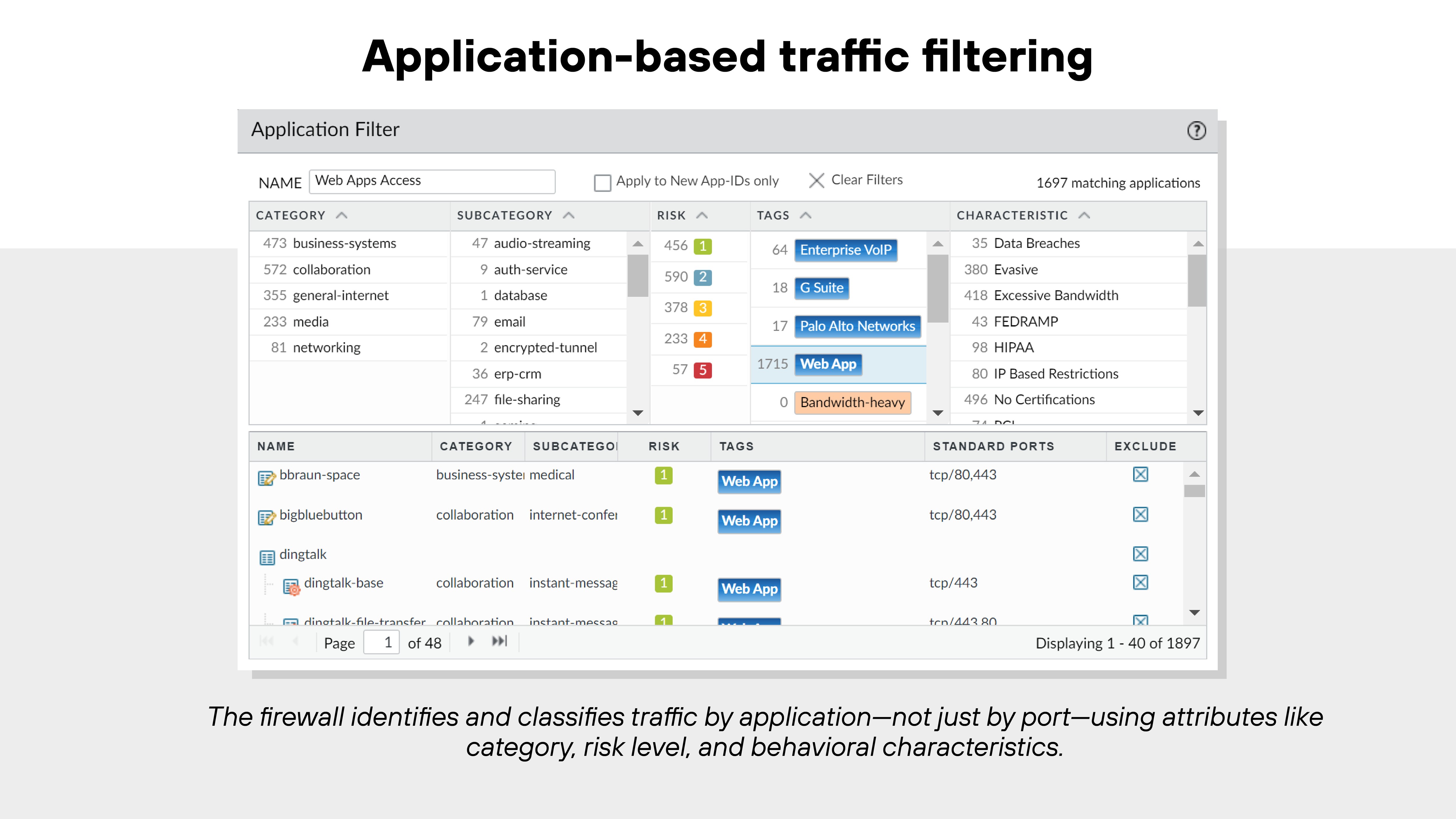
Techniques like protocol decoding, signature matching, and behavioral analysis work together to uncover the true identity of applications—even if they tunnel inside SSL or use nonstandard ports.
User identification
NGFWs map IP addresses to individual users. This lets administrators see who’s behind network activity and apply policies based on identity.
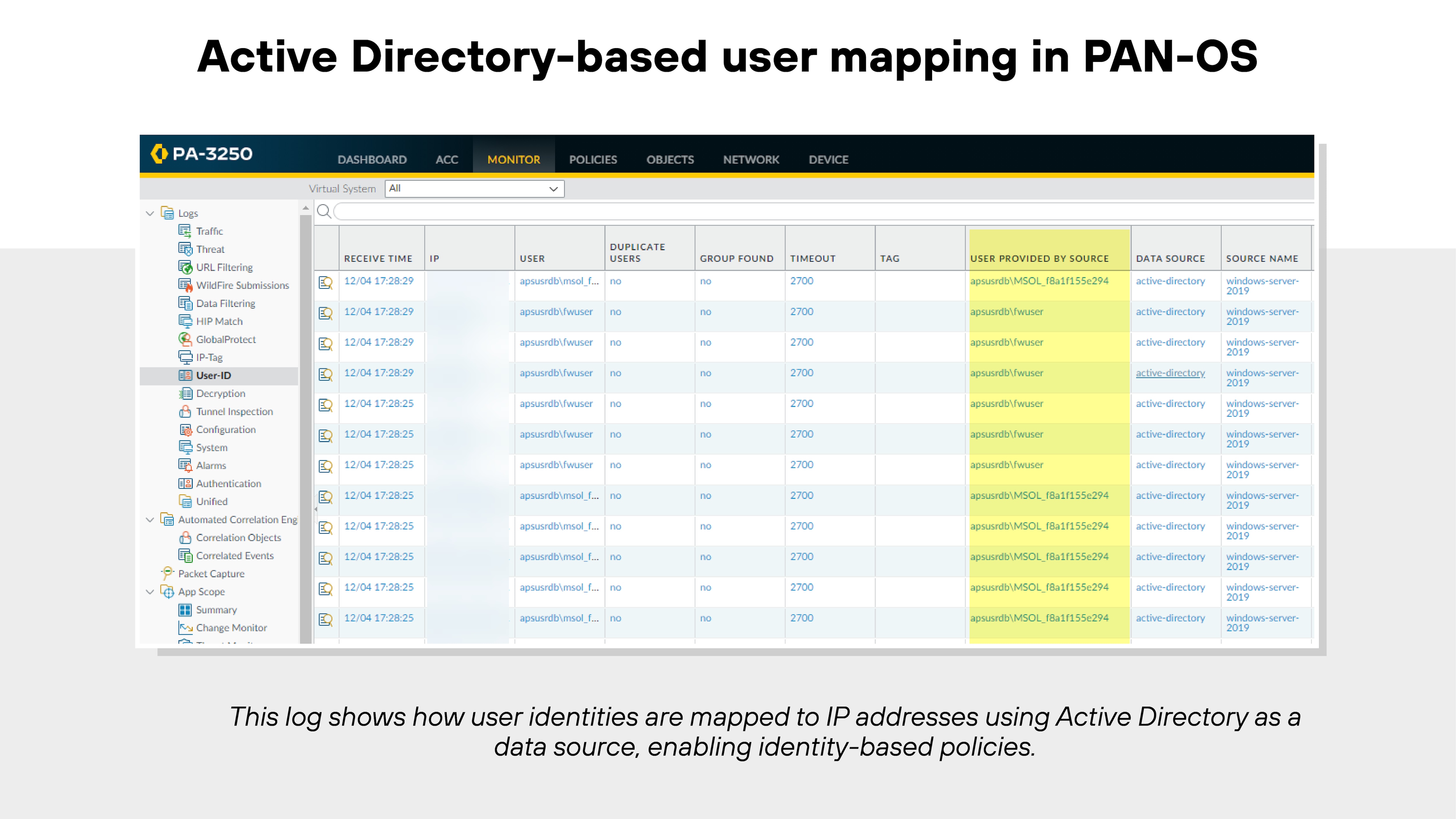
By integrating with directories like Active Directory, NGFWs keep user mappings updated in real time. That makes it possible to enforce role-based access and investigate security events by user rather than just IP.
Content inspection
Content inspection allows NGFWs to detect and block threats inside application traffic. That includes scanning for malware, exploit attempts, and sensitive data.
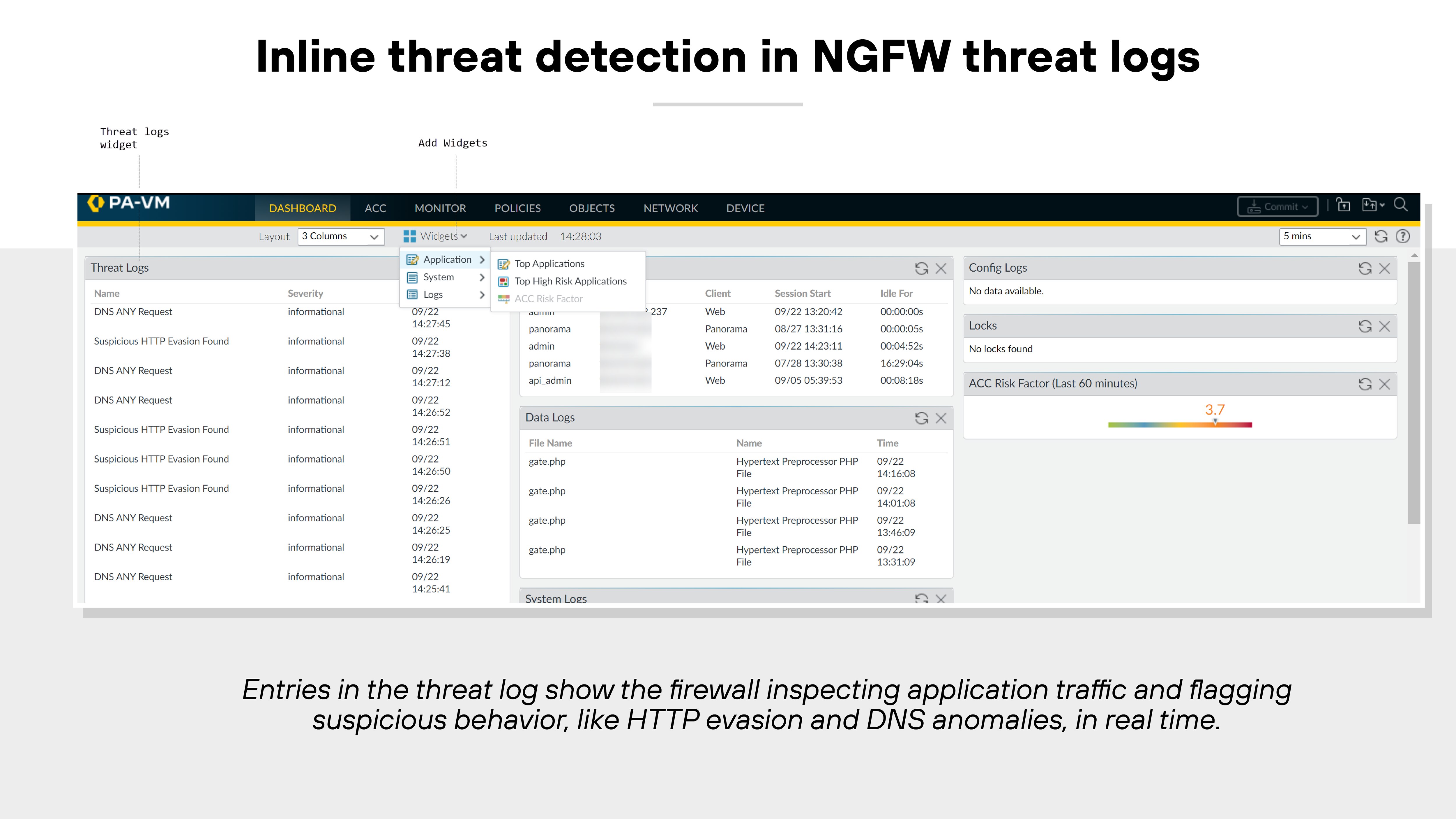
NGFWs often inspect files as they stream in, rather than waiting for full download. Some also use cloud-based services to analyze unknown threats and enforce URL and file filtering policies in line with internal risk controls.
Granular policy enforcement
NGFWs go beyond simple allow or block actions. Once traffic is identified by application, user, and content, administrators can apply fine-tuned controls.
Like this:
For example: An app might be allowed only for a specific user group or blocked during certain hours. Threat scanning and decryption can also be applied selectively, based on traffic type or destination.
SSL decryption
NGFWs can inspect encrypted traffic by performing SSL decryption. This reveals threats that would otherwise pass through unseen.
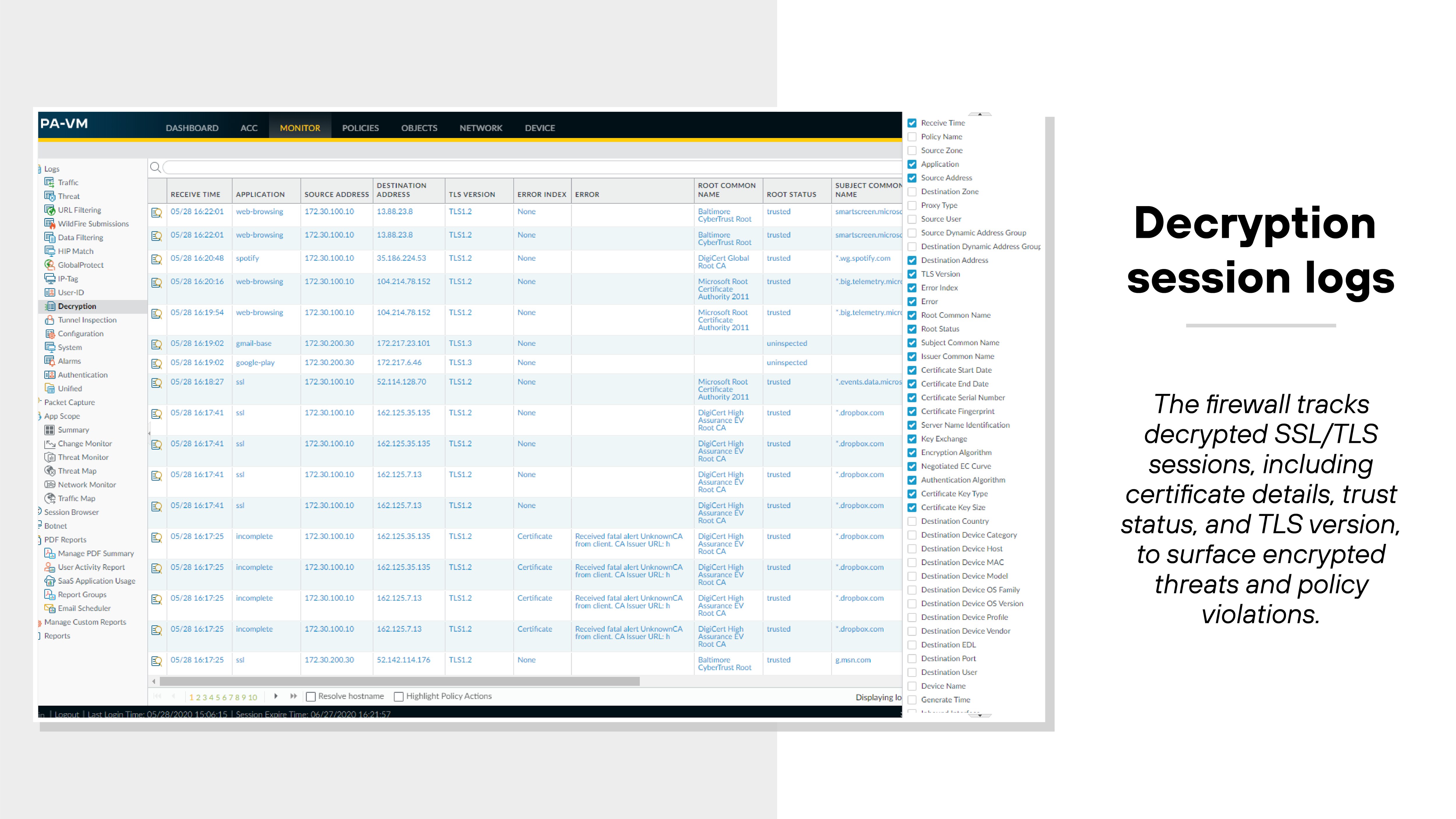
Effective NGFWs handle large volumes of encrypted sessions with minimal performance impact. Some even allow traffic decryption policies to exclude sensitive destinations for compliance reasons.
Single-pass architecture
Performance matters when applying deep inspection. NGFWs with single-pass architecture process each packet once, applying all relevant security functions in one flow.
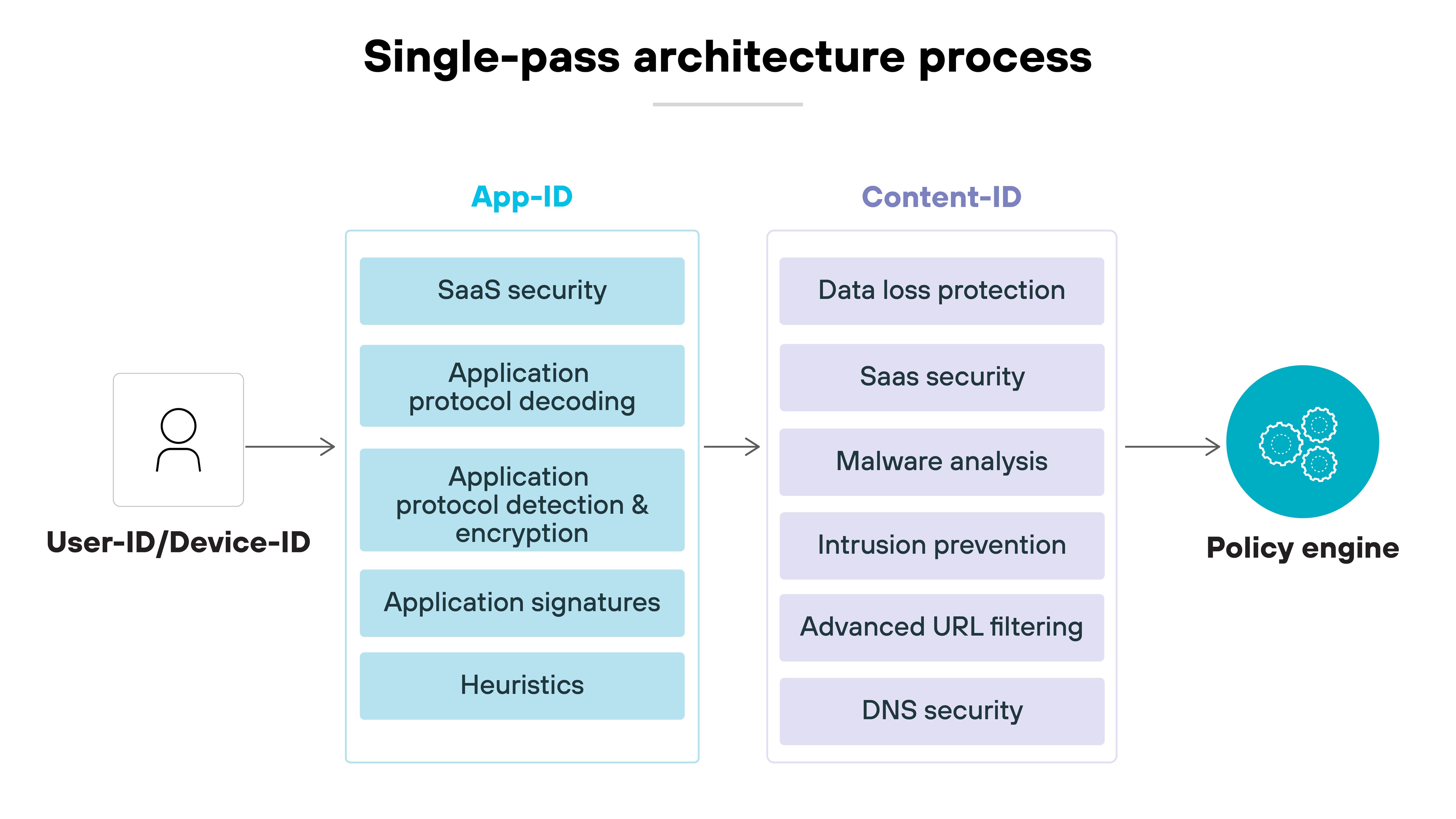
That’s more efficient than legacy firewalls, which may reprocess the same traffic multiple times through different engines. The result is consistent performance even under heavy load.
Modern NGFW features
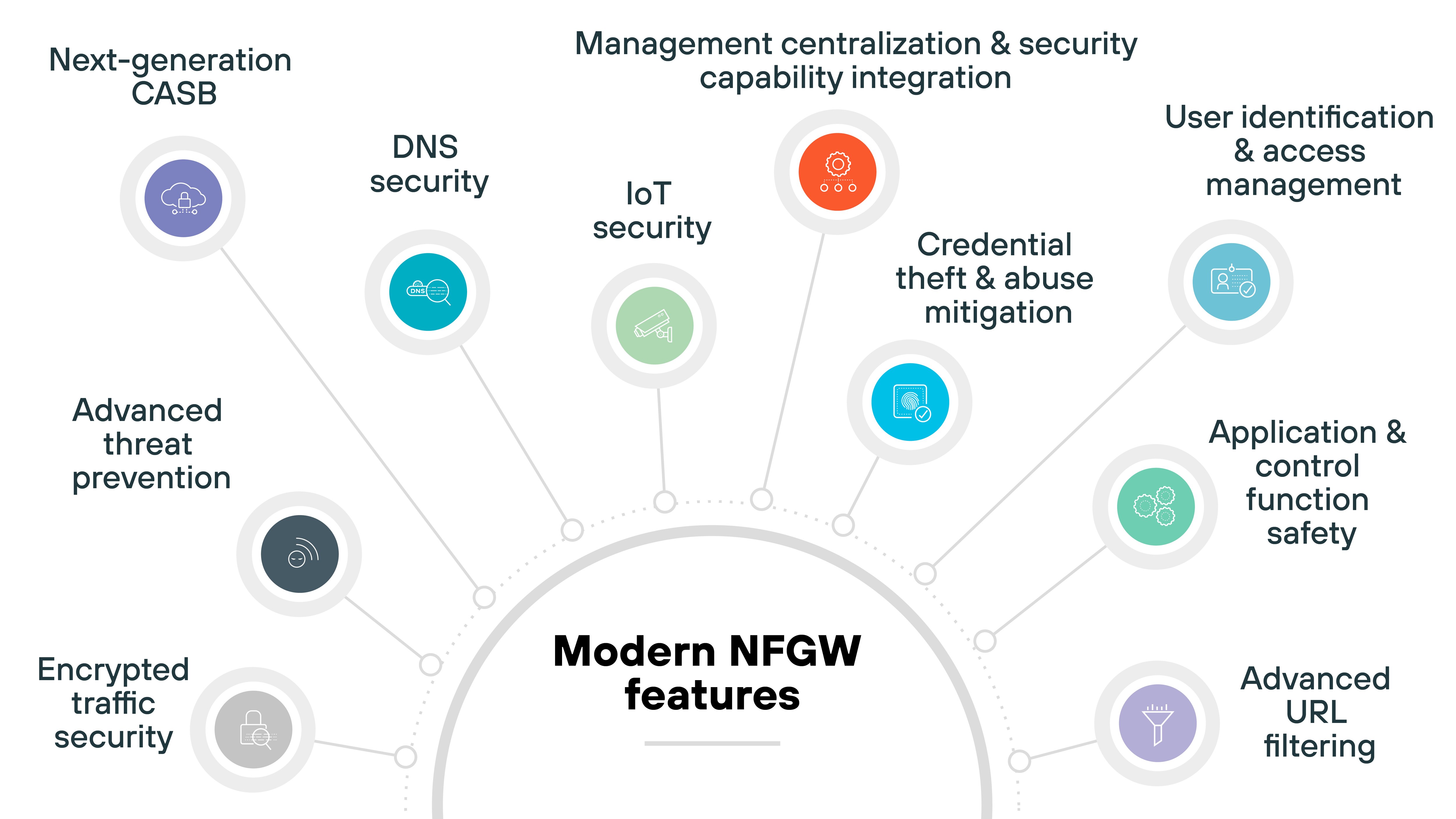
As threats evolved and enterprise networks became more complex, next-generation firewalls had to keep up.
The core NGFW capabilities introduced in the 2010s laid the foundation. But they weren’t enough on their own to handle modern challenges—like encrypted malware, SaaS sprawl, and IoT exposure.
Today’s NGFWs go further. They integrate advanced security services, expand visibility into cloud and device behavior, and apply machine learning to detect and stop attacks in real time. These additions reflect how firewall functionality has shifted from inspection alone to full-spectrum prevention and control.
Here’s what that looks like.
Advanced threat prevention
NGFWs use a multi-layered approach to block both known and unknown threats. That includes real-time traffic inspection, machine learning, and behavioral analysis to detect malware and exploit attempts as they happen.
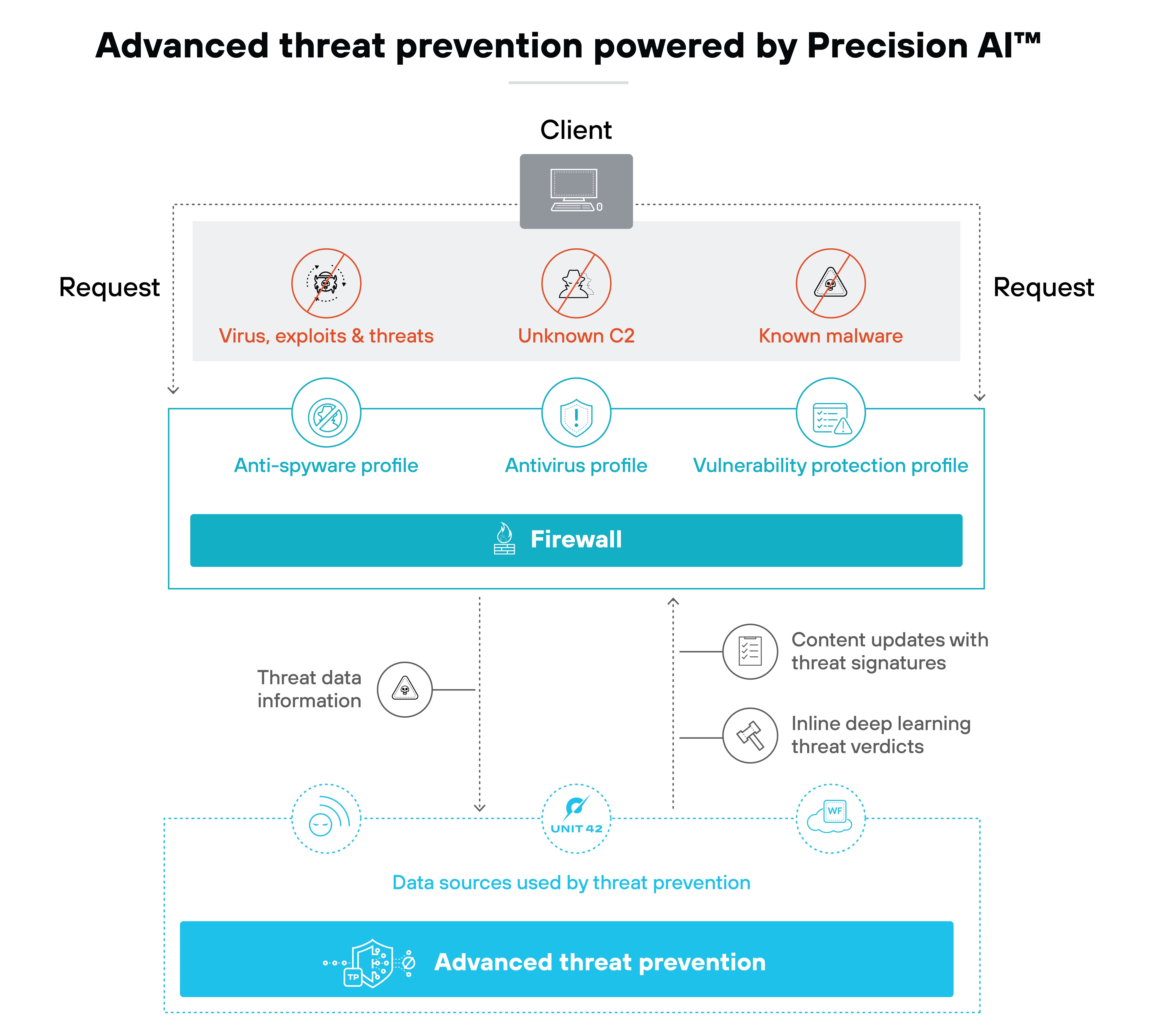
Unlike legacy intrusion prevention systems (IPS), modern NGFWs can prevent zero-day attacks inline. They also use shared threat intelligence and automatic signature updates to stay current with evolving threats—without requiring manual intervention.
Advanced URL filtering

Advanced URL filtering blocks access to malicious and risky websites. It uses real-time analysis and machine learning to inspect and classify URLs—even ones that haven’t been seen before.
This helps detect phishing attempts, malware distribution sites, and other web-based threats as users browse. It also supports granular web access policies based on user, group, or application, and helps maintain compliance with corporate browsing standards.
DNS security
DNS security protects the network by analyzing and controlling DNS queries. It prevents attacks like DNS tunneling, cache poisoning, and domain generation algorithm (DGA)-based evasion techniques.
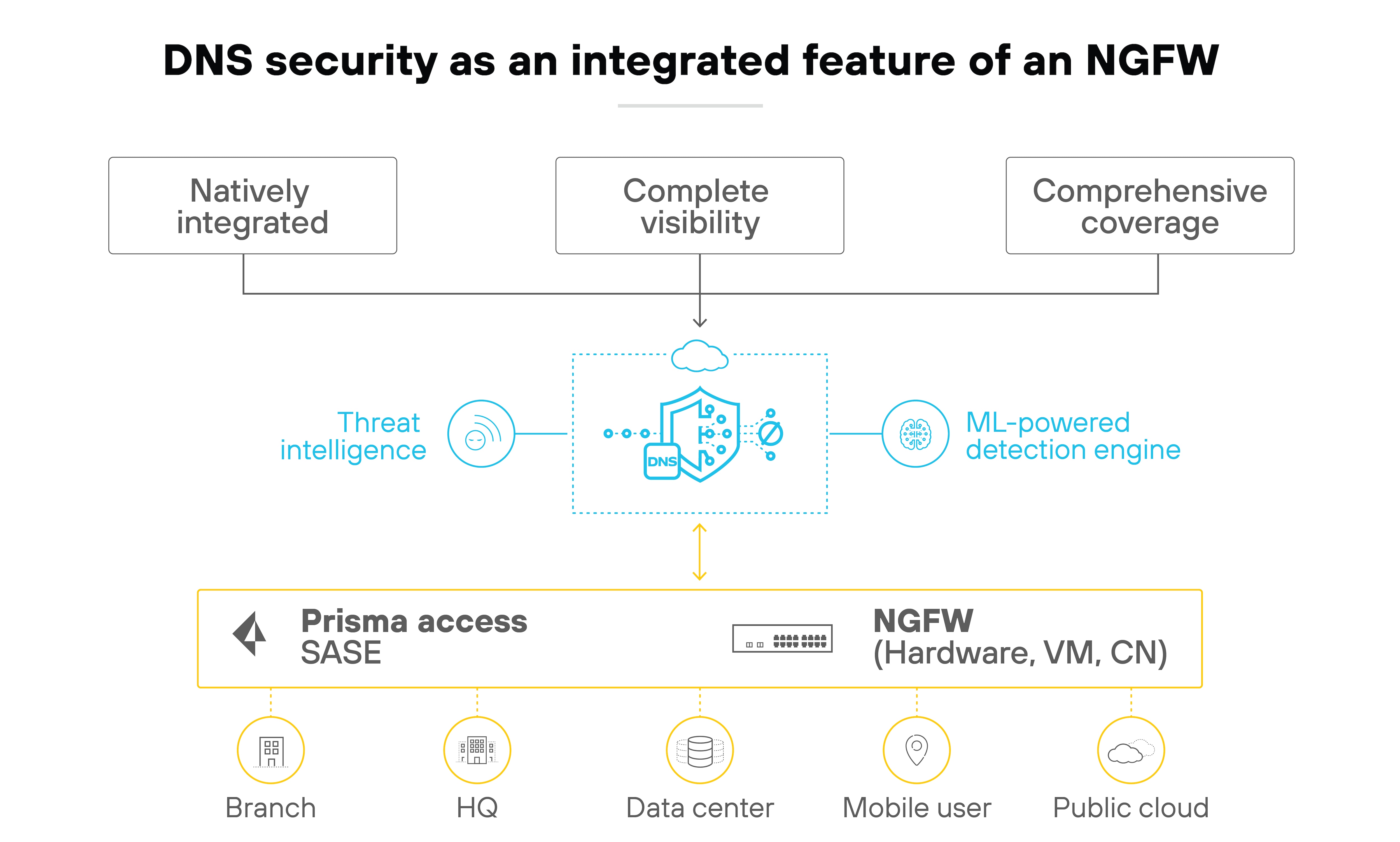
NGFWs with DNS security capabilities monitor DNS traffic for anomalies and known malicious domains. Some solutions use predictive analytics and machine learning to detect zero-day threats at the DNS layer.
Next-generation CASB
A next-generation cloud access security broker (CASB) built into an NGFW gives visibility and control over SaaS usage. It helps secure both sanctioned and unsanctioned cloud applications.
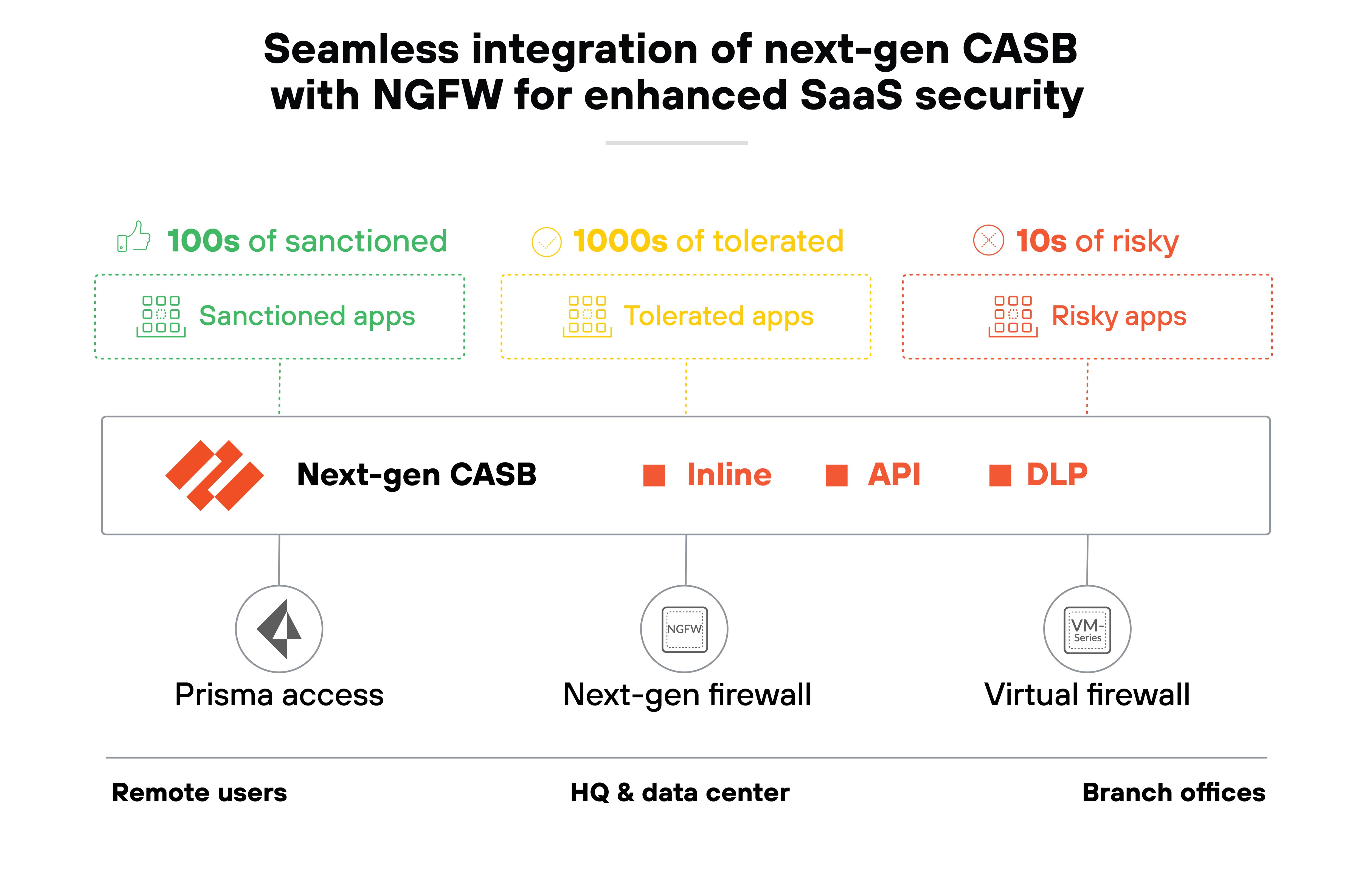
It also provides real-time posture assessments, data protection, and policy enforcement. This makes it easier to prevent data leakage, maintain compliance, and apply Zero Trust principles to cloud environments
IoT security
NGFWs can detect, identify, and secure unmanaged IoT devices on the network. Using machine learning and cloud-scale analytics, they recognize device types, assign profiles, and monitor behavior.
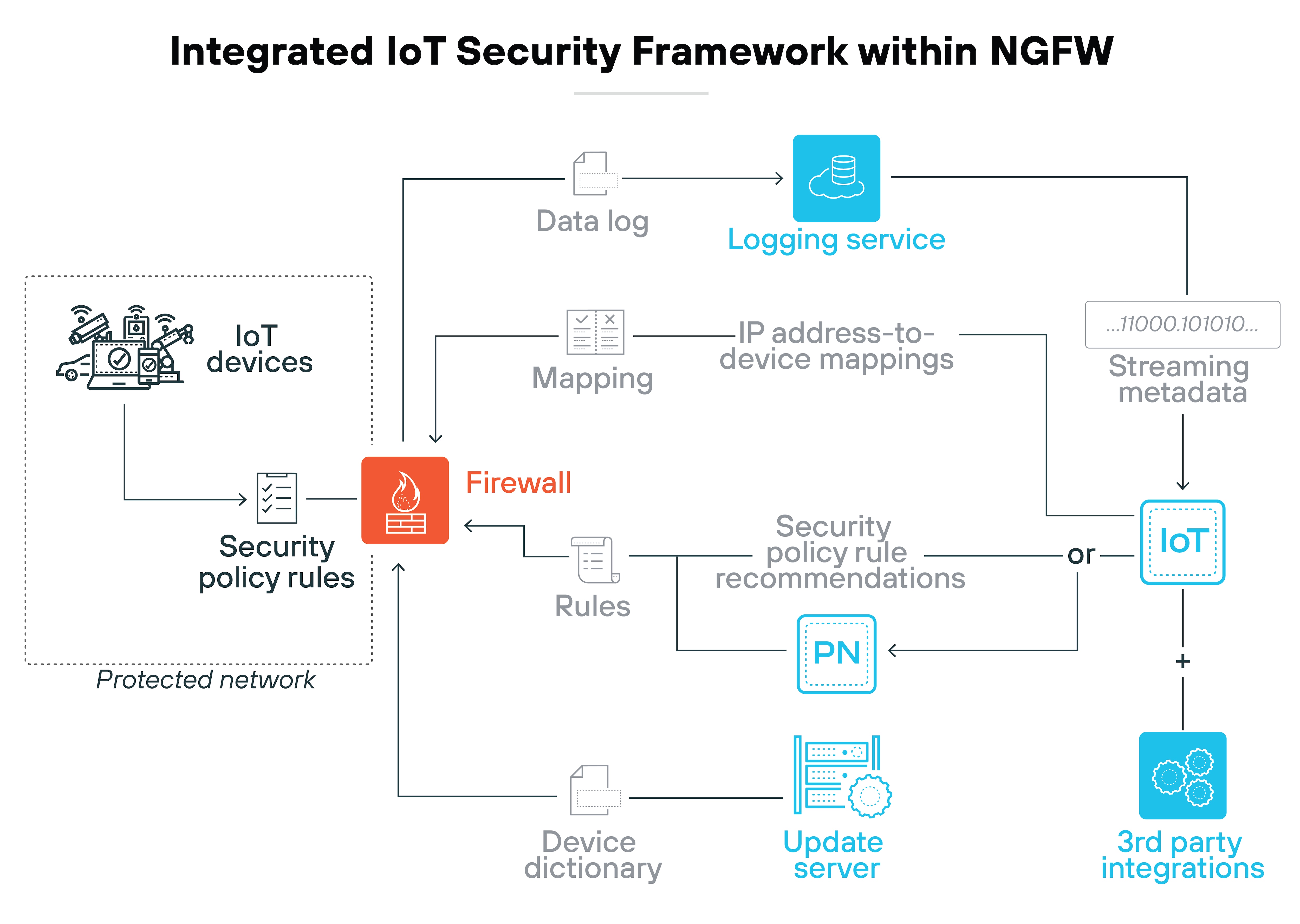
When a device deviates from its baseline, the firewall can automatically enforce a security policy. This helps reduce the risk posed by vulnerable or misconfigured devices without needing additional sensors.
User identification and access management
Modern NGFWs link traffic to specific users, not just IP addresses. They integrate with identity providers to map user identities across different devices and locations.
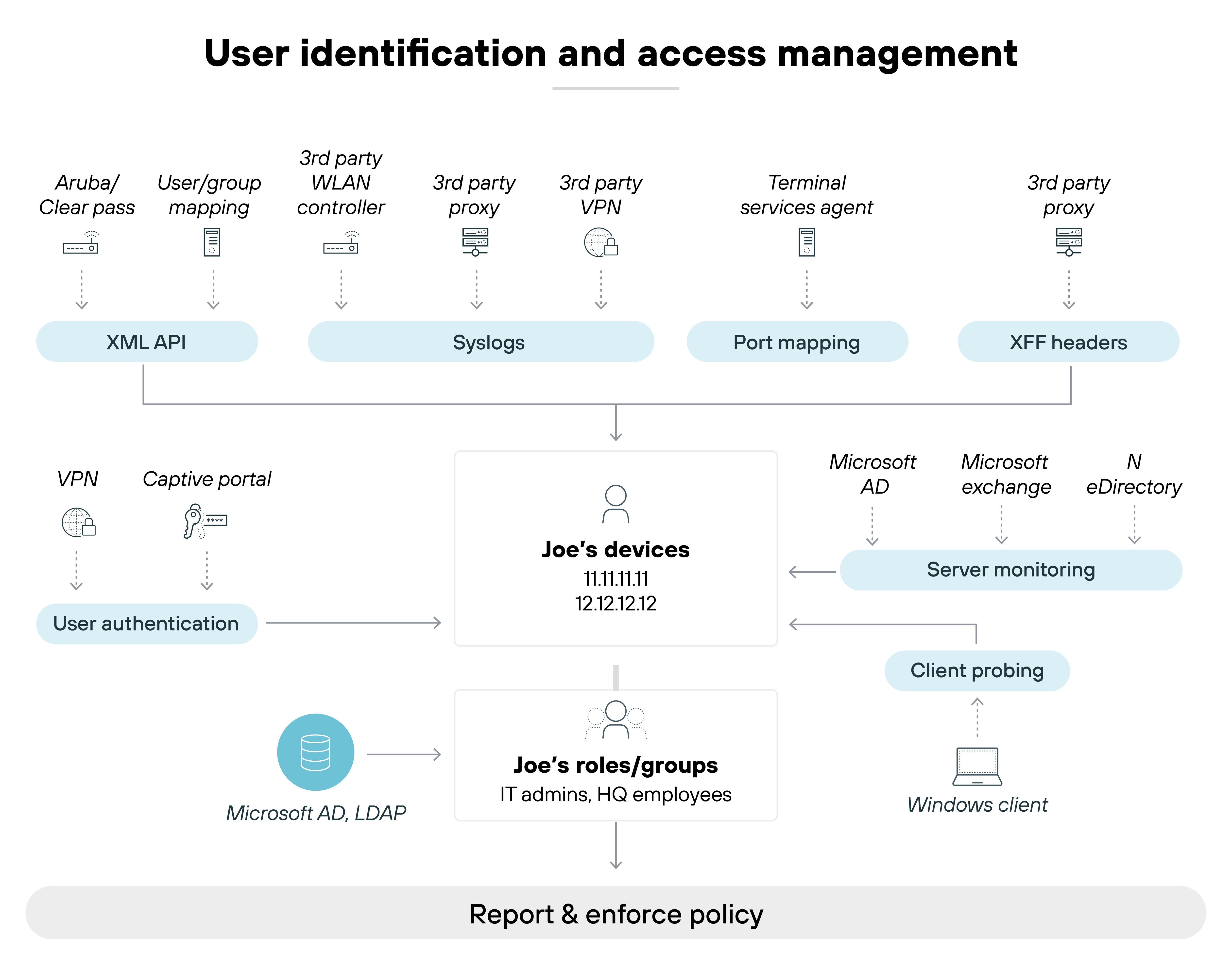
This enables user-based access policies. It also ensures consistent enforcement for remote users and supports Zero Trust principles by tying permissions to individual users rather than broad network segments.
Credential theft and abuse mitigation
NGFWs help prevent credential-based attacks by monitoring for suspicious behavior, enforcing multifactor authentication (MFA), and blocking known phishing sites.
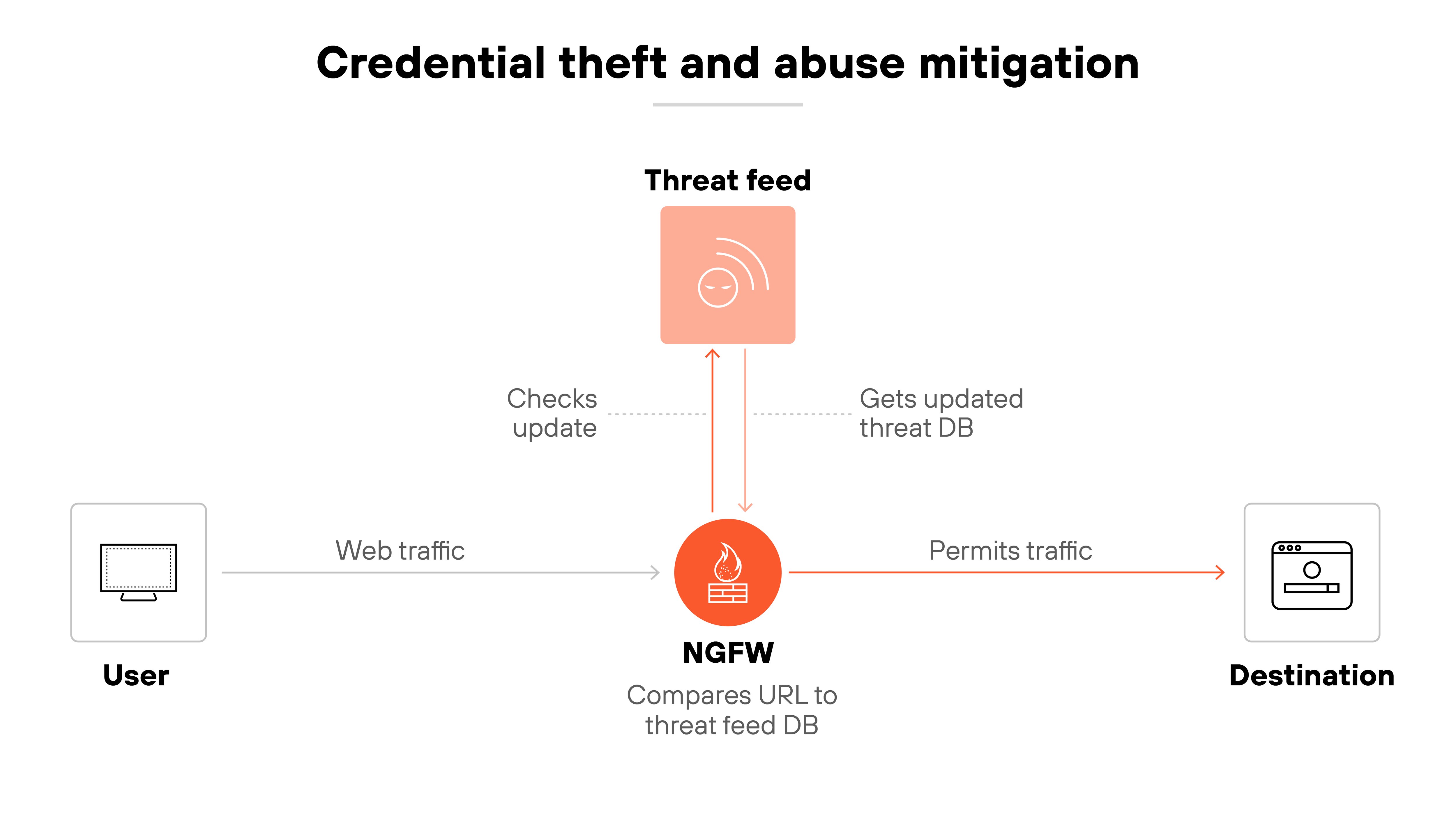
They also detect when users attempt to submit credentials to untrusted destinations. This stops attackers from using stolen credentials to move laterally or escalate privileges.
Application and control function safety
Application awareness is a foundational NGFW feature. It allows the firewall to identify traffic based on application behavior, not just ports and protocols.
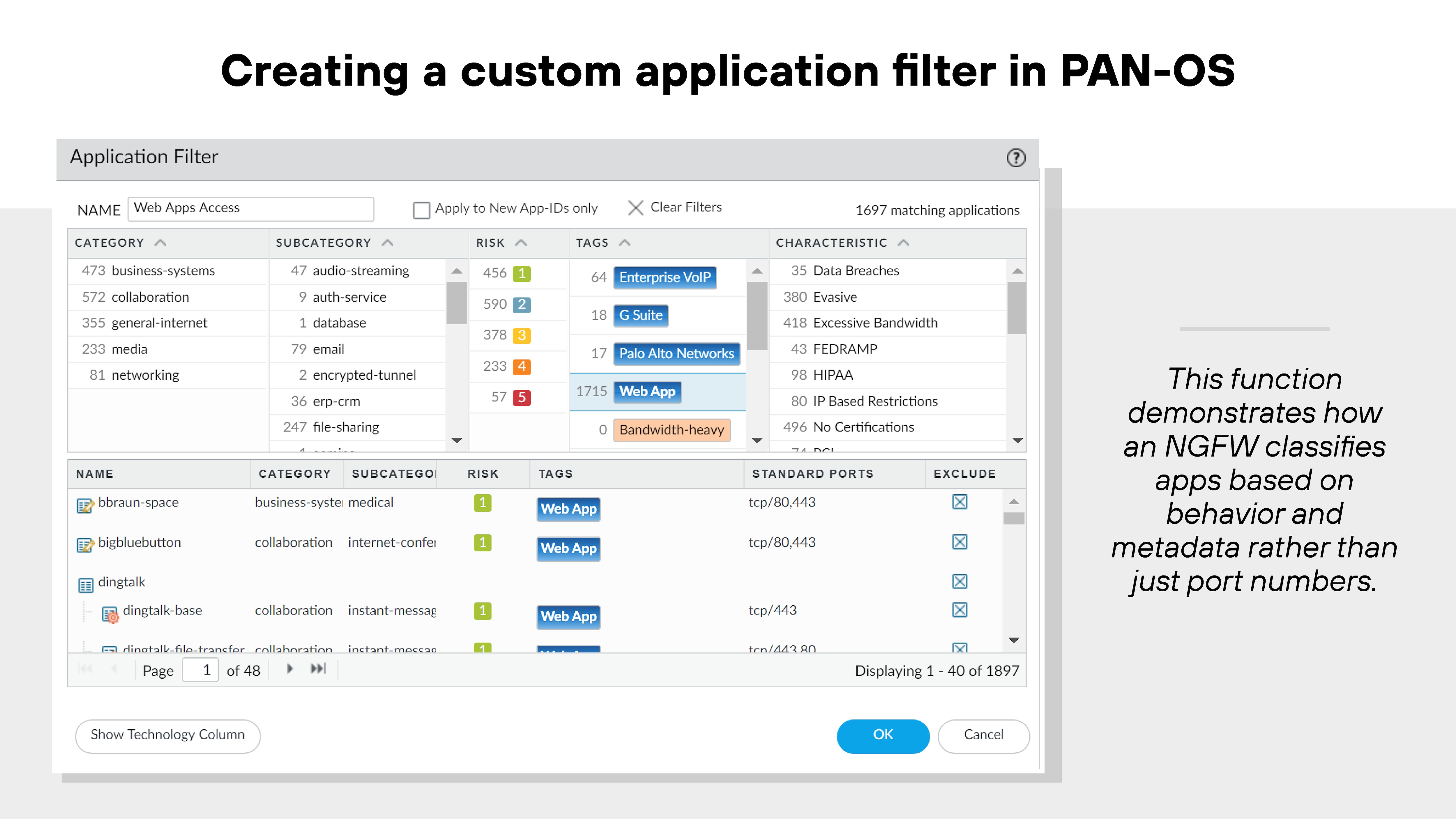
This helps distinguish between safe and risky application use. For example, a file-sharing app might be allowed for IT but blocked for everyone else. NGFWs can also control specific functions within apps, such as file upload or remote access.
Encrypted traffic security
Most internet traffic is encrypted. NGFWs need to inspect encrypted traffic without compromising performance or privacy.
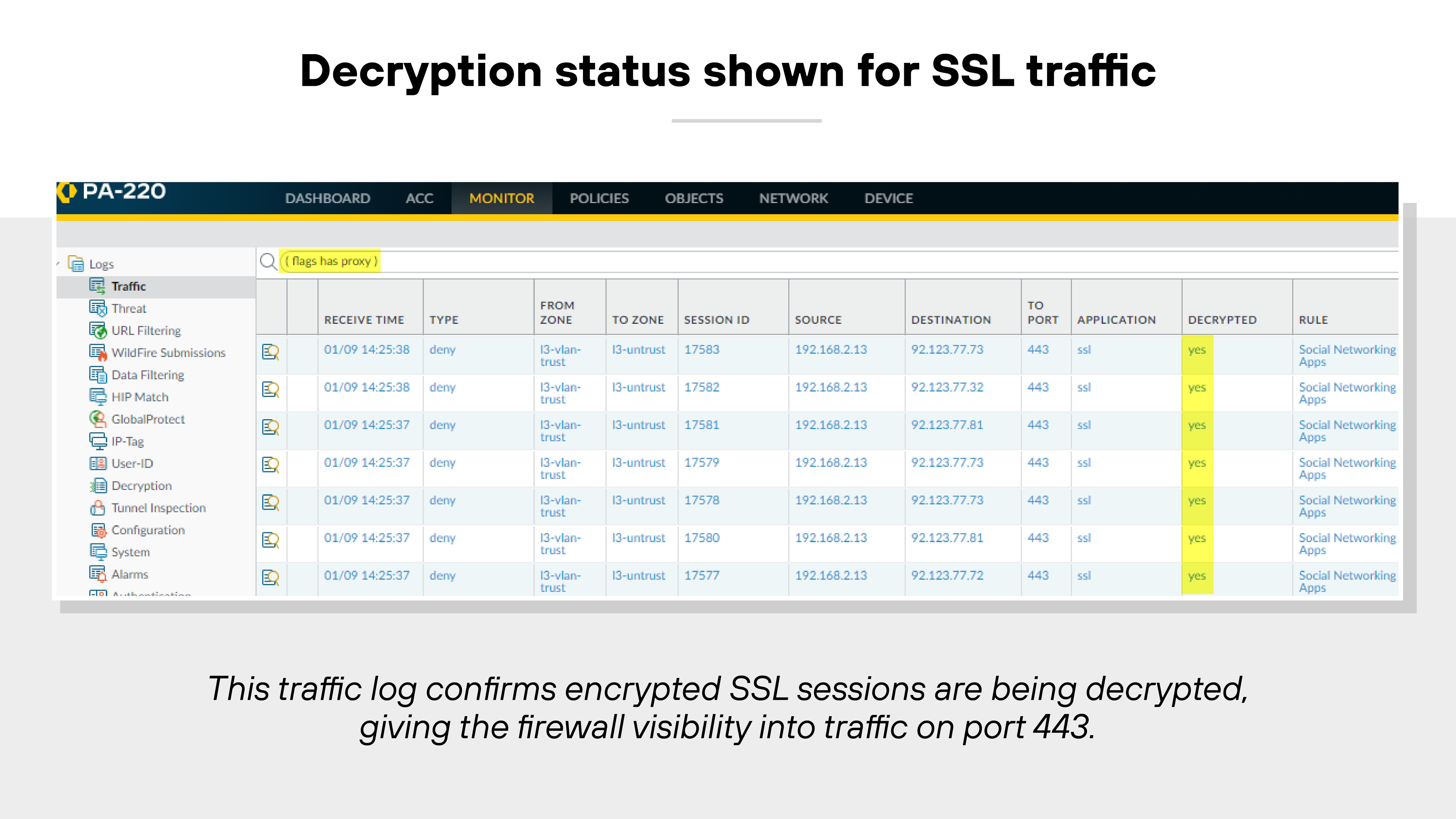
They offer policy-based decryption for SSL/TLS traffic, including TLS 1.3.
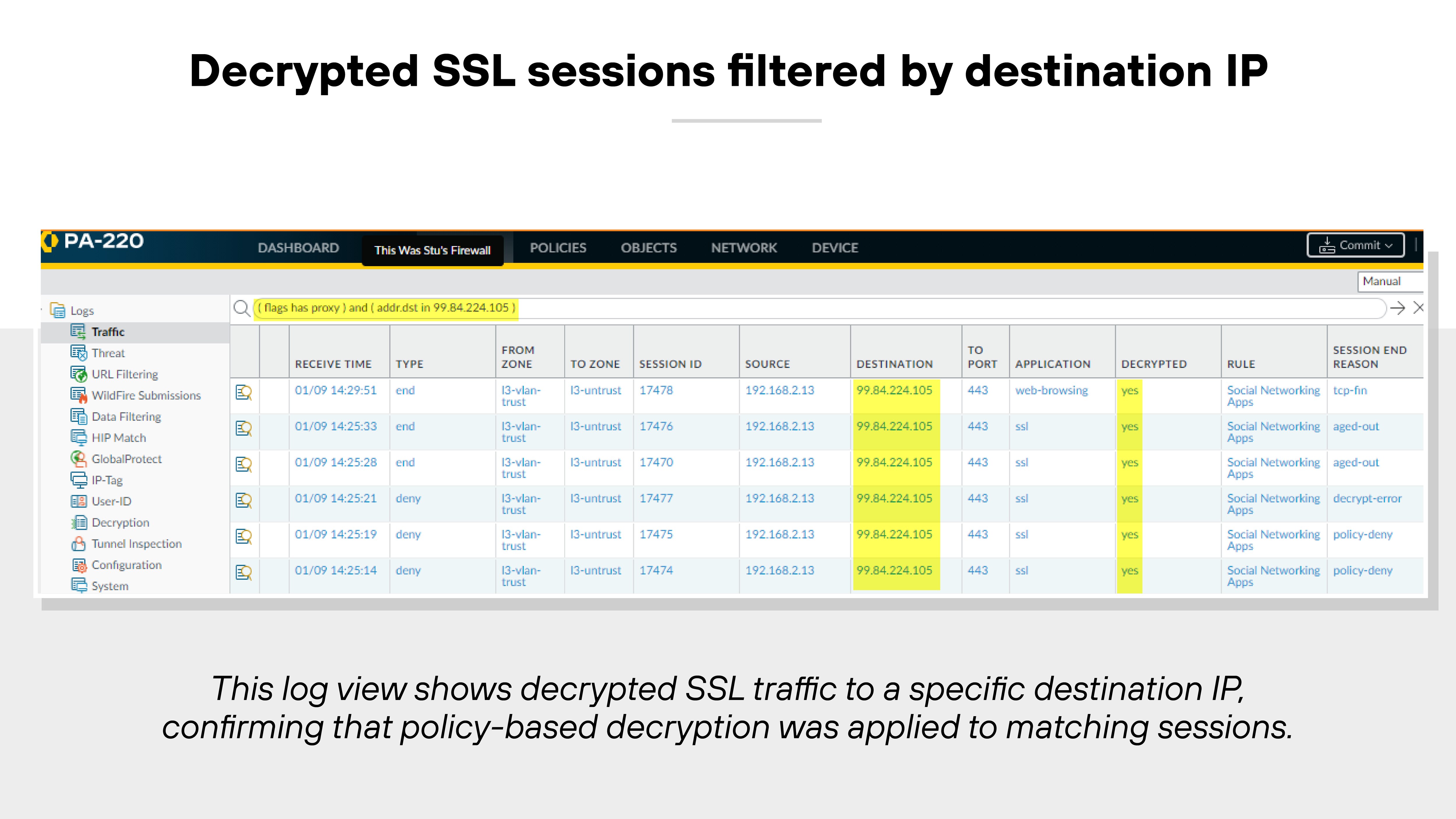
Admins can choose which traffic to decrypt and which to exempt based on sensitivity or regulatory requirements. Once decrypted, traffic can be inspected for threats, then re-encrypted for delivery.
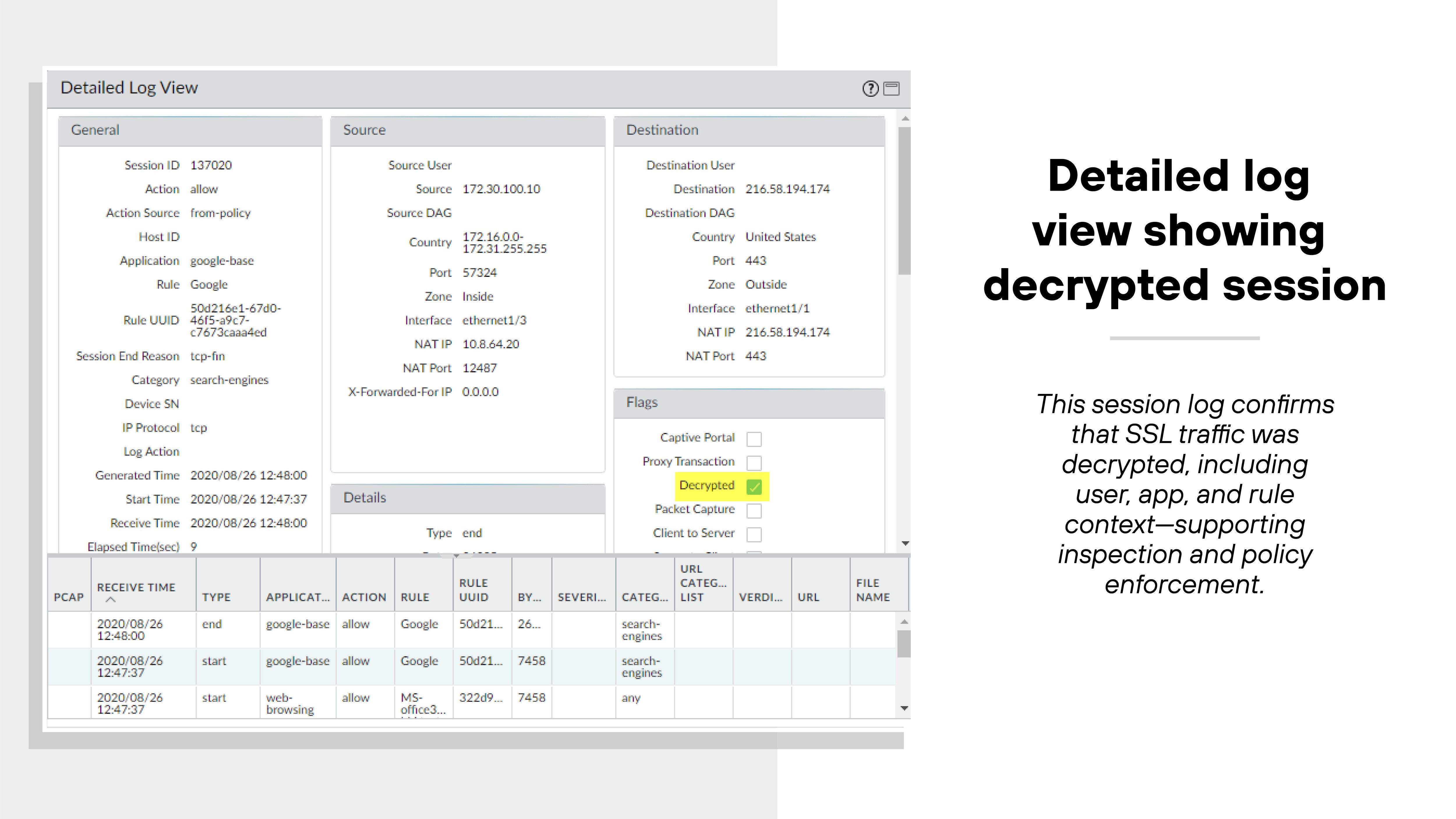
Management centralization and security capability integration
NGFWs support centralized management across all firewall deployments—on-premises, cloud, and branch. This helps ensure consistent policy enforcement and visibility across environments.
Integration is key. NGFWs combine traffic inspection, threat prevention, DNS filtering, CASB, and IoT visibility into one platform. This reduces the need for separate tools, simplifies administration, and lowers the risk of gaps between point products.
| Further reading:
- What Are the Top Firewall Features? | Traditional & NGFWs
- What Makes a Strong Firewall?
- What Is a Virtual Firewall?
- What Is a Container Firewall?
What are the benefits of an NGFW?
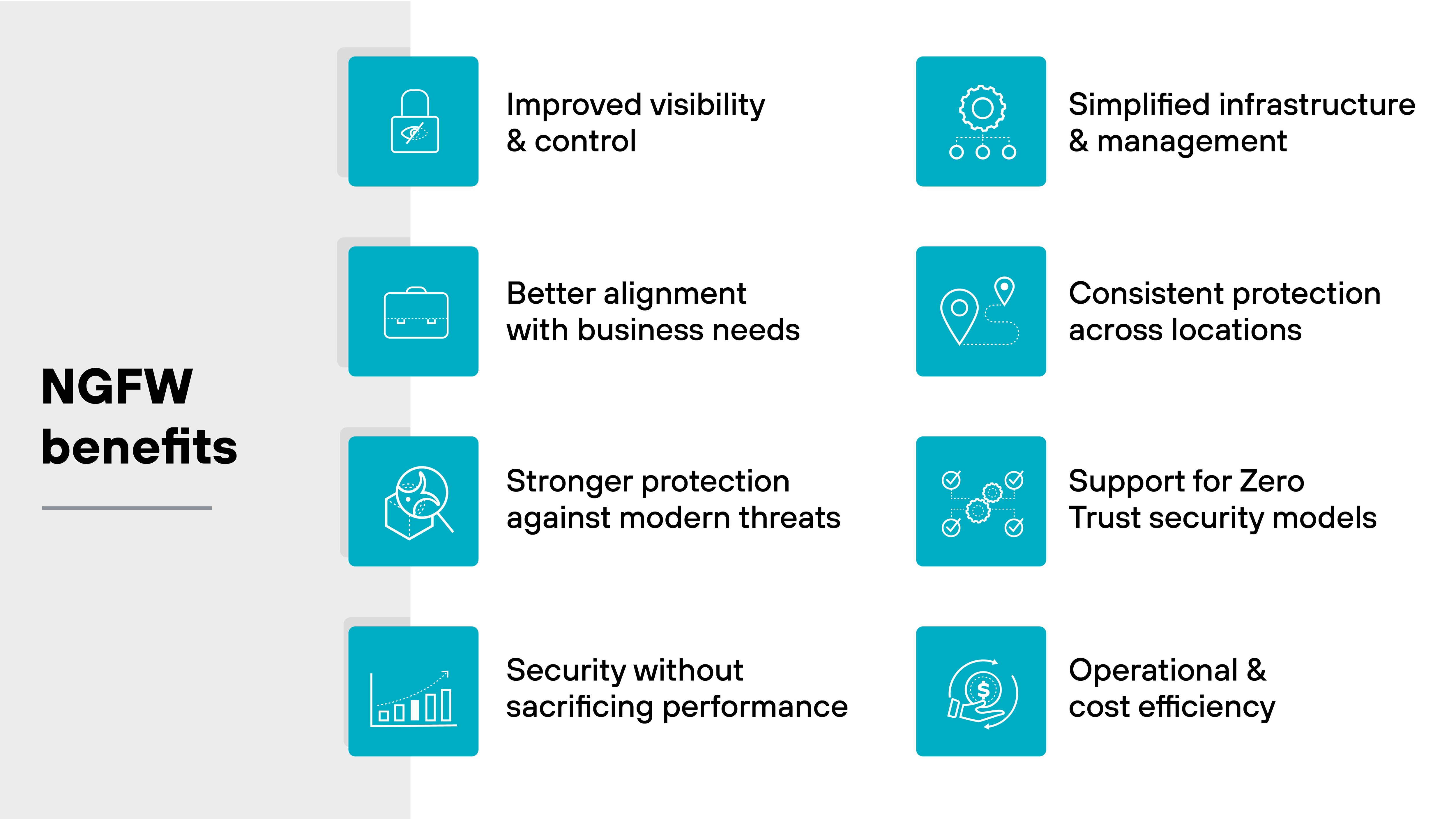
Next-generation firewalls do more than just protect the network perimeter. They unify traffic visibility, application control, and advanced threat prevention into one security platform.
Here's how that translates into real operational and security value.
Improved visibility and control
Traditional firewalls focus on IP addresses, ports, and protocols. NGFWs shift the focus to applications, users, and content.
Why does that matter?
It gives administrators more relevant insights. You can see exactly which applications are running, who's using them, and what kind of content is being transmitted. From there, you can apply policies based on business context—not just technical attributes.
This level of control helps reduce blind spots and makes it easier to enforce security standards without overblocking legitimate activity.
Better alignment with business needs
NGFWs help IT teams support business requirements without compromising security.
For example: Instead of blocking a cloud storage app outright, you can allow it only for specific users or limit risky actions like file sharing.
This lets the organization adopt tools it needs while maintaining control over how they're used.
In other words:
NGFWs make it easier for security teams to say "yes"—with guardrails.
Stronger protection against modern threats
Today's attacks often bypass traditional firewalls. They target applications directly. They hide inside encrypted traffic. And they use fast-changing techniques to avoid detection.
NGFWs are designed to deal with this.
They inspect traffic in real time, apply behavioral analysis, and pull threat intelligence from cloud-based sources. This helps detect and stop attacks that haven't been seen before—like zero-day exploits or targeted malware.
The result: Broader protection with faster response.
Security without sacrificing performance
Security tools can create latency if they're not designed to scale.
NGFWs address this with architecture that processes traffic efficiently. Instead of sending data through separate engines, they apply multiple inspection and control functions in a single pass.
That reduces processing time. And it keeps performance stable—even with high traffic volumes or heavy use of encrypted connections.
Simplified infrastructure and management
NGFWs consolidate multiple security functions into one platform.
For example: It's not uncommon to find URL filtering, IPS, DNS security, and CASB features all in the same device or service.
This reduces the number of tools you need to manage. It also cuts down on policy sprawl, configuration errors, and gaps between products.
Centralized management makes a big difference here. It helps teams maintain consistent policies across locations and deployment types—on-premises, remote, or cloud-based.
Consistent protection across locations
NGFWs apply the same policies to users no matter where they are. That includes employees working remotely, in branch offices, or on mobile devices.
Why this matters:
Without consistent policy enforcement, users outside the network perimeter can introduce security gaps. NGFWs close those gaps by extending full inspection and control to all traffic—regardless of location.
In other words:
You get the same level of protection for every user, even in distributed or hybrid environments.
Support for Zero Trust security models
NGFWs help enforce Zero Trust principles by verifying users, devices, and applications before granting access.
Here's how:
Instead of trusting internal traffic by default, NGFWs apply policy checks to everything. They integrate with identity systems to make decisions based on user role, group, and behavior—enabling more granular control.
That helps organizations reduce implicit trust, limit lateral movement, and strengthen segmentation.
Operational and cost efficiency
NGFWs reduce the need for multiple standalone tools. By consolidating security functions into one platform, they help lower both capital and operational costs.
Instead of running separate appliances for threat detection, URL filtering, and application control, you can centralize those capabilities. That means fewer systems to license, power, maintain, and manage.
It also reduces the administrative burden. With a single policy framework and management interface, security teams can save time and reduce complexity.
| Further reading: What Are the Benefits of a Firewall?
What are the most common NGFW misconceptions?
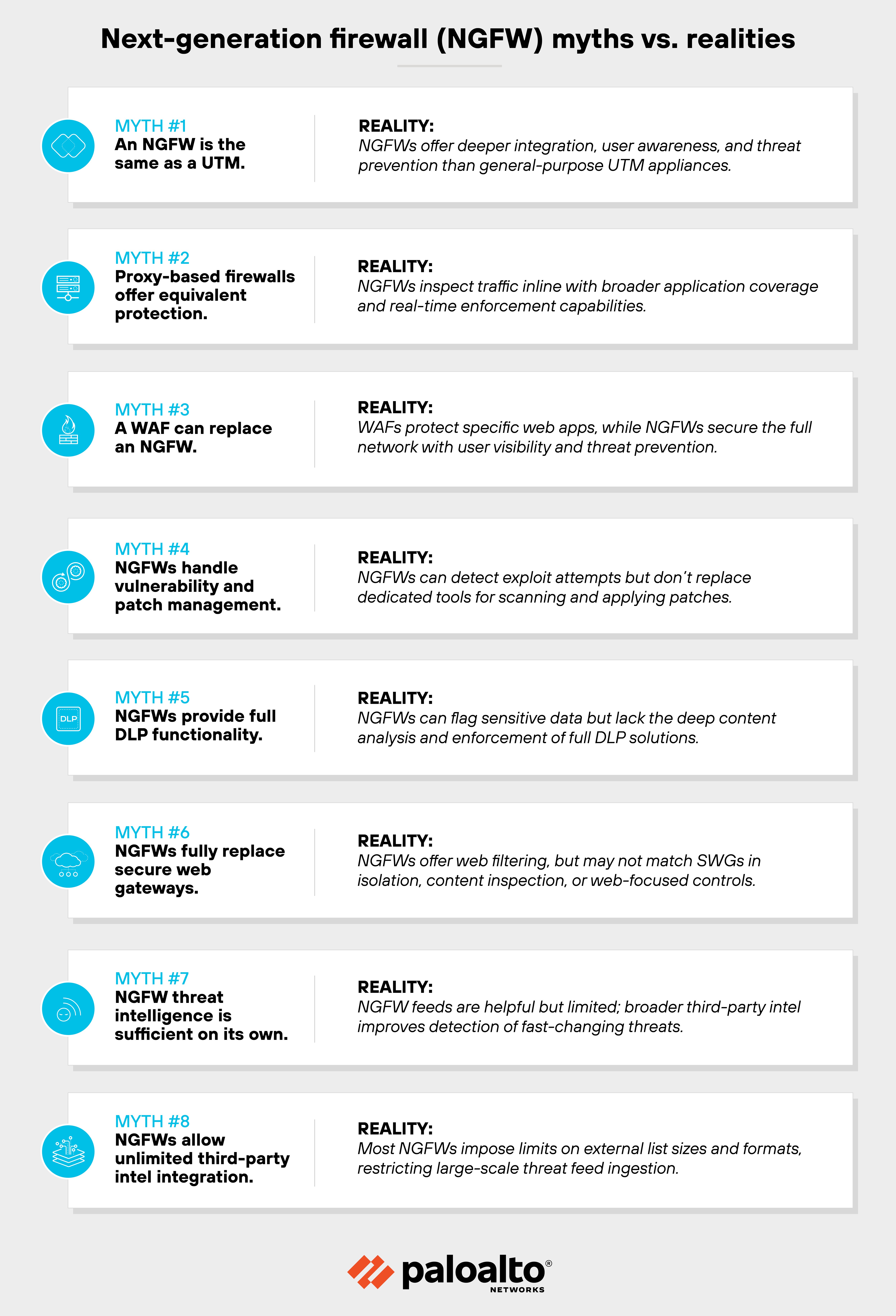
Misconception #1: An NGFW is the same as a UTM
Unified threat management (UTM) appliances bundle multiple security functions into a single device. These may include a basic firewall, antivirus, and intrusion prevention.
NGFWs, on the other hand, offer deeper integration and context sharing across security functions. They apply consistent policy enforcement across applications, users, and content. UTMs don't have the same visibility or control over app behavior or user identity.
They also lack the depth of inline threat prevention available in most NGFWs.
Misconception #2: Proxy-based firewalls offer equivalent protection
Proxy firewalls inspect traffic by terminating the session and creating a new one on behalf of the client. While this can obscure internal systems, it limits application coverage.
NGFWs inspect traffic in-line without terminating the session. They can analyze application behavior, enforce granular policies, and apply threat prevention in real time.
This gives them broader applicability and deeper control than proxy-based products.
Note:
Some environments still rely on proxy firewalls for specific use cases, like isolating web traffic, but they're typically used in tandem with NGFWs rather than as a replacement.
Misconception #3: A web application firewall (WAF) can replace an NGFW
WAFs focus on application-layer (Layer 7) traffic, particularly for HTTP-based applications. They look for vulnerabilities caused by poor coding practices or misconfigurations.
NGFWs operate across the full OSI stack. They provide network-layer visibility, user mapping, encrypted traffic inspection, and advanced threat prevention.
WAFs are useful for protecting individual applications. But they don't replace the broader protection NGFWs offer for the entire network.
Misconception #4: Vulnerability and patch management is a firewall function
Some assume NGFWs can detect and patch vulnerable systems. That's not accurate.
Vulnerability management tools scan hosts, check patch levels, and flag outdated software.
NGFWs can restrict traffic to vulnerable systems or detect exploit attempts, but they don't replace a dedicated patch management process.
Note:
NGFWs can complement vulnerability management by enforcing compensating controls, such as isolating unpatched systems or blocking known exploit traffic.
Misconception #5: NGFWs include full data loss prevention (DLP)
While NGFWs can detect sensitive data patterns in traffic, they don't provide full DLP capabilities.
Purpose-built DLP tools are designed to analyze content in depth, track data usage, and enforce complex data-handling policies.
NGFWs can block traffic matching specific patterns, but they don't offer the same level of contextual data analysis and policy enforcement.
Note:
While NGFWs may support regex-based or keyword matching for sensitive data, full DLP involves deeper inspection of file types, context, and user intent.
Misconception #6: NGFWs fully replace secure web gateways
Secure web gateways (SWGs) use URL categorization and filtering to enforce browsing policies. They may include sandboxing or malware detection, but are usually limited to web-based traffic.
Modern NGFWs often include integrated URL filtering. But not all provide the same level of content filtering, isolation, or dedicated web inspection features as a SWG.
That said, NGFWs offer more consistent policy enforcement across multiple types of traffic and protocols.
Misconception #7: Threat intelligence from an NGFW is enough on its own
Most NGFWs use proprietary threat intelligence feeds to detect and block threats. These feeds are useful—but may be limited to the vendor's view of the threat landscape.
Here's the issue:
Sophisticated attackers move fast and use evasion techniques that can bypass single-source detection.
Which means that broader threat intelligence—such as from government, open source, and commercial feeds—can provide more comprehensive protection.
NGFWs that don't support easy integration with third-party intelligence may fall short in identifying new or targeted threats.
Misconception #8: NGFWs support unrestricted threat intel integration
Some assume they can easily load large third-party IP or domain blocklists into an NGFW.
That's not always the case.
Many NGFWs have strict limits on list sizes and ingestion formats. They may allow basic external list integration, but lack the scale or flexibility needed for operational threat intelligence programs.
This makes it harder to use open source or commercial feeds at full fidelity.
Note:
Even when integration is supported, practical limits around processing power, ingestion frequency, and list size may impact real-time effectiveness.
| Further reading: Hardware Firewalls vs. Software Firewalls
What are the differences between NGFWs and traditional firewalls?
| Feature | Traditional firewalls | Next-generation firewalls (NGFWs) |
|---|---|---|
| Traffic control method | Based on IP addresses, ports, and protocols | Based on applications, users, content, and context |
| Application awareness | None or very limited (rely on ports) | Deep application visibility and control, regardless of port/protocol |
| User identification | IP-based; no user-level awareness | Integrates with identity services (e.g., LDAP/AD) to enforce user-based policies |
| Encrypted traffic inspection | Cannot decrypt or inspect SSL/TLS | Can decrypt, inspect, and re-encrypt SSL/TLS traffic |
| Threat prevention | Basic or bolted-on; often separate appliance | Integrated intrusion prevention, malware scanning, and behavior analysis |
| Granular control | Limited to allow or block based on static rules | Enables function-level control (e.g., file upload within app), time-based rules, and traffic shaping |
| Performance architecture | Multi-pass; higher latency when adding features | Single-pass; optimized performance even with full feature set enabled |
| Visibility into evasive threats | Blind to port hopping, tunneling, encryption | Designed to detect and block evasive threats using multiple techniques |
| Content inspection | Limited or bolt-on DPI (deep packet inspection) | Built-in URL filtering, data filtering, threat scanning, and cloud sandboxing |
| Integration with threat intelligence | Often limited to proprietary sources; poor 3rd-party integration | Uses vendor threat intel; supports limited external blocklists but often with scale/volume constraints |
| Architecture and management | Legacy infrastructure; often needs multiple products to cover gaps | Unified platform reduces complexity and appliance sprawl |
| Common use case | Network perimeter access control | Granular control and visibility across networks, users, and apps (including SaaS/cloud) |
Traditional firewalls were built for a different era of network traffic. They use static rules to filter traffic based on ports, protocols, and IP addresses.
That worked when applications mapped cleanly to well-known ports.
But today's applications rarely follow those rules.
Many use dynamic ports, encryption, and tunneling techniques that evade basic filtering. As a result, traditional firewalls can't reliably identify what's actually on the network.
Next-generation firewalls (NGFWs) are designed to address that gap.
Instead of assuming traffic type based on port numbers, NGFWs analyze the actual application behavior.
They use a combination of application signatures, protocol decoders, and heuristics to identify applications and their functions—regardless of port or encryption.
NGFWs also incorporate features like user identity, content inspection, and threat prevention into a unified policy model.
In other words: Traditional firewalls rely on limited indicators. NGFWs rely on direct application awareness and integrated control.
That shift allows them to enforce more precise security policies across modern, encrypted, and evasive traffic—something legacy firewalls weren't built to do.
| Further reading:
- What Is a Stateful Firewall? | Stateful Inspection Firewalls Explained
- What Is a Packet Filtering Firewall?
What to look for in an NGFW solution
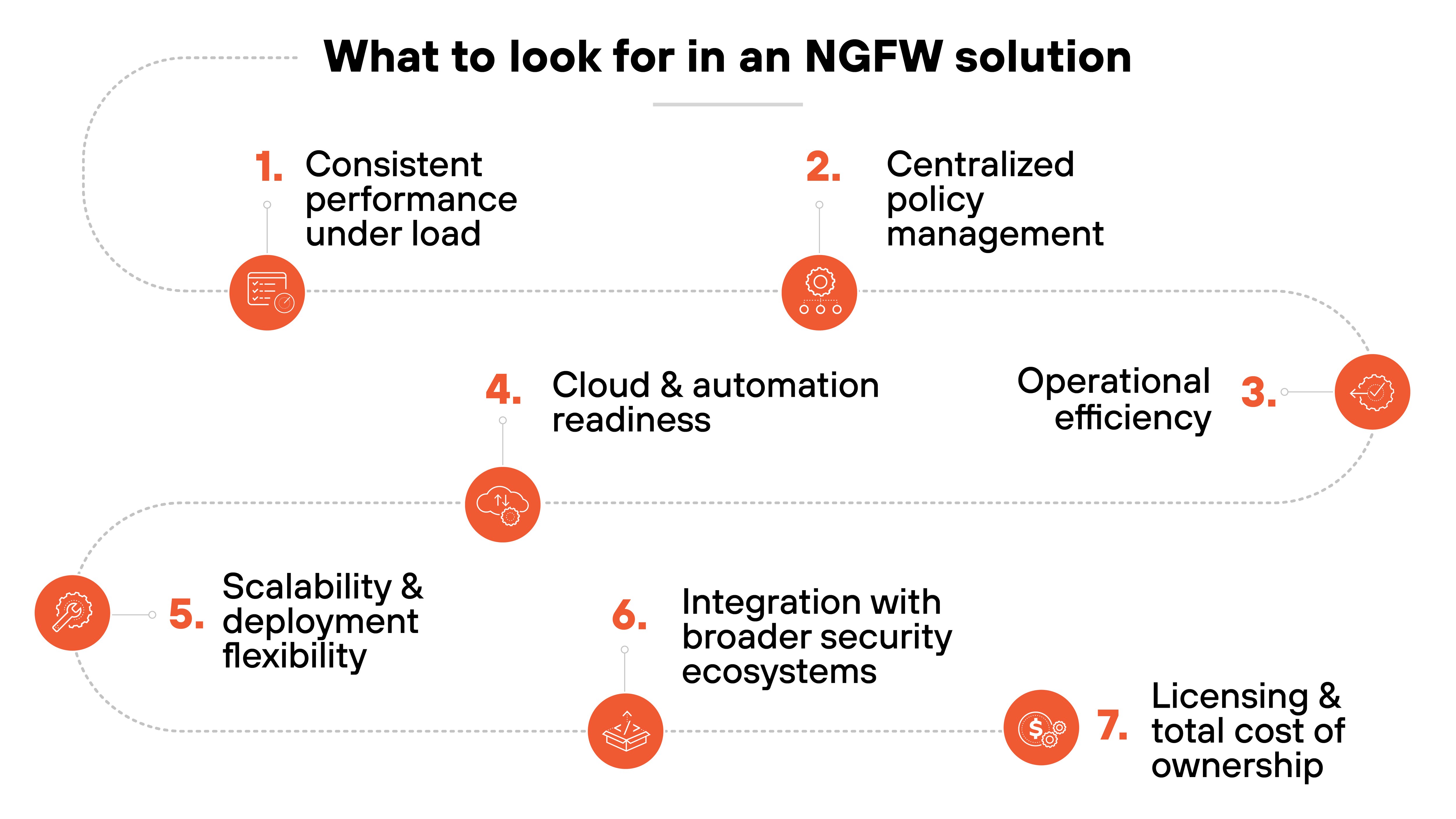
Choosing a next-generation firewall isn't just about checking off features.
Most NGFWs come with the same core capabilities. What matters more is how effectively they deliver those capabilities in your environment.
In other words:
It's not just what the firewall can do. It's how well it does it.
Here's what to look for.
Consistent performance under load
An NGFW should maintain low latency even when all security services are turned on.
Threat inspection, decryption, and logging can add overhead. The right solution handles this without degrading user experience or throughput.
This is especially important for real-time apps, branch environments, and encrypted traffic.
Tip:
Run test scenarios with full threat prevention, decryption, and logging enabled simultaneously. Some NGFWs advertise high throughput—but only under ideal conditions without real-world configurations.
Centralized policy management
You should be able to manage all firewall instances—on-premises and in the cloud—from one console. That includes creating policies, viewing logs, and pushing updates globally.
Look for intuitive policy workflows and tools that make large-scale management easier, not harder.
Tip:
Evaluate how the platform handles policy shadowing and overrides across distributed deployments. Look for systems that can flag or prevent conflicting rules before deployment.
Operational efficiency
Managing security shouldn't require jumping between tools.
The firewall should reduce administrative overhead by simplifying policy creation, automating tasks, and consolidating capabilities.
This helps teams stay focused on actual threats, not manual processes.
Cloud and automation readiness
An NGFW should work with modern infrastructure. That includes public clouds, private clouds, and automation tools like Terraform and Ansible.
Why? Because your environment will keep evolving. The firewall should keep up.
Tip:
Check for prebuilt integrations or modules for your specific infrastructure-as-code tools, not just "support." Native modules (e.g., Terraform providers) speed up rollout and reduce errors.
Scalability and deployment flexibility
You might need to deploy NGFWs in data centers, branch offices, or public clouds.
The solution should support a mix of physical, virtual, and cloud-native form factors—and scale as your needs grow.
This avoids re-architecture later on.
Integration with broader security ecosystems
NGFWs shouldn't operate in a vacuum. The solution should integrate with identity providers, endpoint protection, threat intelligence, SIEMs, and other security tools.
That way, data flows between systems. And you get a more complete view of risk.
Tip:
Ask whether the NGFW supports bi-directional integration—not just ingesting data from other tools, but also sharing enriched threat and traffic context back into your SIEM or SOAR.
Licensing and total cost of ownership
Different vendors package features in different ways. Some include advanced capabilities in the base license. Others charge separately.
Understand what's included. Make sure your pricing model aligns with your long-term needs—not just today's deployment.
Tip:
Request a breakout of what's included in each license tier—and what happens if features are turned off for cost. Some vendors tie essential functions like decryption or threat prevention to premium licenses, which can constrain use later.
How to successfully deploy NGFWs in 11 steps
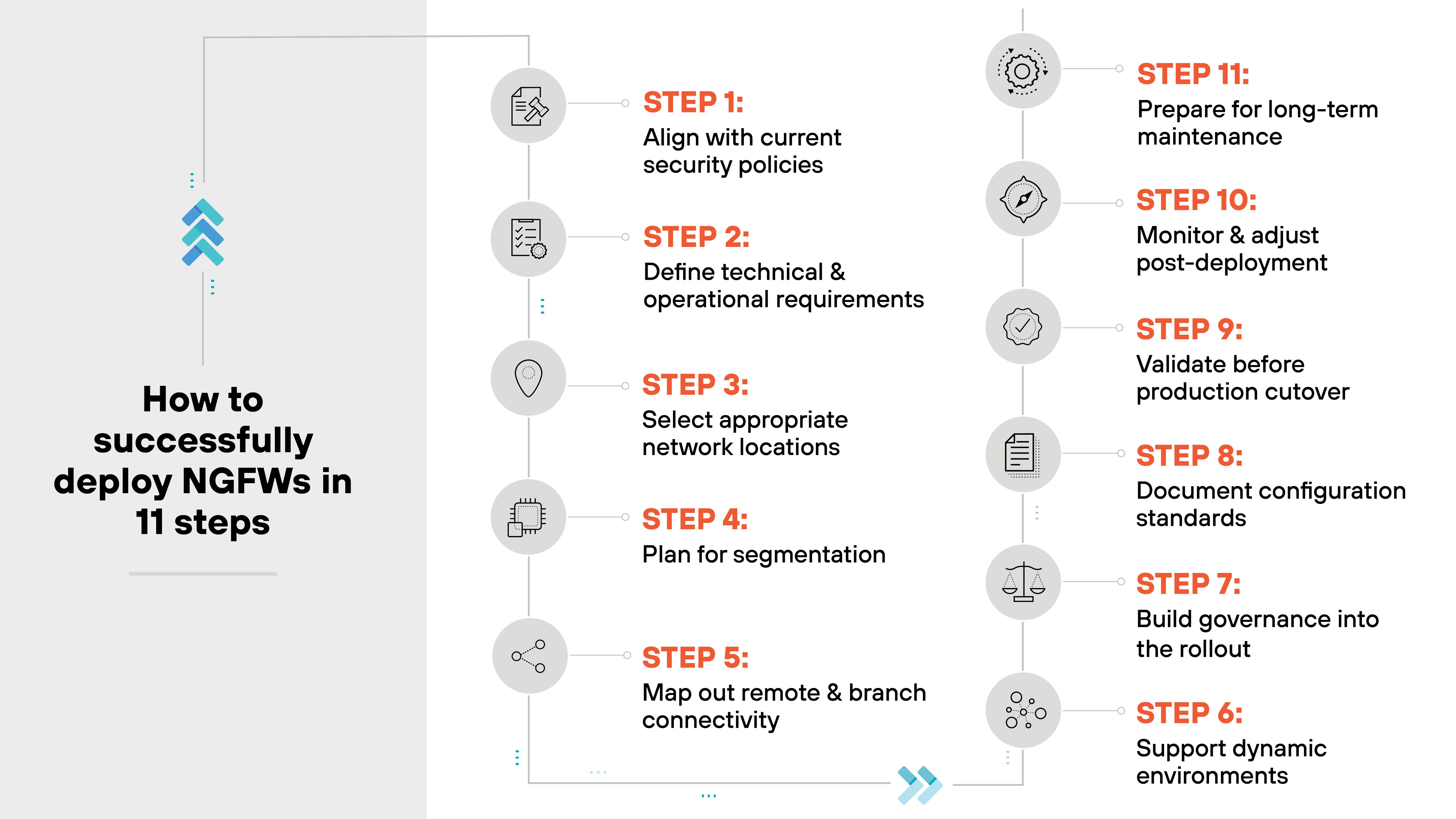
Deploying a next-generation firewall (NGFW) isn't just about getting the device online.
It involves planning, policy alignment, architectural decisions, and long-term operational readiness.
Step 1: Align with current security policies
Start with policy.
Your deployment should reflect what the organization already considers acceptable use and risk tolerance. If those policies are outdated or unclear, update them before touching the firewall.
Tip:
Include application-specific use cases in your policy alignment process—for example, what's considered acceptable use of cloud storage or remote access tools—so the NGFW can enforce policy beyond simple IP controls.
Step 2: Define technical and operational requirements
Document what your network needs from a functional and administrative standpoint. This includes network segmentation goals, remote access scenarios, and integration requirements across teams.
Step 3: Select appropriate network locations
Where you place NGFWs matters.
In some cases, you may need perimeter enforcement. In others, internal segmentation is the priority.
Choose locations that align with the type of traffic you need to inspect and the risks you need to manage.
Step 4: Plan for segmentation
Segment the network logically. This allows you to isolate sensitive systems, reduce lateral movement, and enforce policy boundaries.
Use zones that reflect business function, sensitivity, or trust level.
Tip:
Don't over-segment. Excessive zones can add complexity without meaningful isolation. Focus on high-risk systems, regulated data, or untrusted user groups.
Step 5: Map out remote and branch connectivity
If your organization supports remote users or branch offices, factor them into your design. The deployment should allow consistent enforcement regardless of user location.
Tip:
Make sure the deployment supports policy enforcement even when users connect via VPN or cloud-based access gateways. This is key for Zero Trust consistency.
Step 6: Support dynamic environments
Modern environments change often. That includes virtual machines, containers, and cloud workloads.
Make sure your deployment model can handle shifts without requiring frequent reconfiguration.
Step 7: Build governance into the rollout
Involve stakeholders across IT, HR, and compliance.
Make sure there is shared ownership of decisions that affect user access, acceptable use, and escalation paths.
Step 8: Document configuration standards
Don't rely on ad hoc decisions. Establish naming conventions, baseline rule sets, change control procedures, and logging practices before deployment begins.
Tip:
Include justification notes for any rule exceptions. This makes future audits or troubleshooting easier when teams change or incidents occur.
Step 9: Validate before production cutover
Test in a lab or staging environment using representative traffic.
Validate policy logic, administrative workflows, and interoperation with other tools. This reduces the risk of misconfiguration during rollout.
Step 10: Monitor and adjust post-deployment
Once in place, the firewall should be continuously monitored.
Track rule effectiveness, policy violations, and unexpected traffic behavior. Use this feedback to refine configurations over time.
Step 11: Prepare for long-term maintenance
Firewalls are not set-and-forget.
Assign ongoing responsibilities for updates, rule reviews, and audit readiness. And ensure your team has the access and training needed to manage the deployment long term.
| Further reading:
- What Is Firewall Configuration? | How to Configure a Firewall
- How to Troubleshoot a Firewall | Firewall Issues & Solutions
- What Is Firewall Management?
How do NGFWs compare with other security technologies?
Next-generation firewalls (NGFWs) don't exist in a vacuum. They complement, differ from, and sometimes overlap with other security technologies.
Here's how they compare.
NGFW vs. WAF
NGFWs and web application firewalls (WAFs) protect different layers of traffic.
NGFWs inspect network-layer traffic, often at layers 3, 4, and sometimes 7. WAFs focus on HTTP traffic at layer 7, specifically to protect web applications.
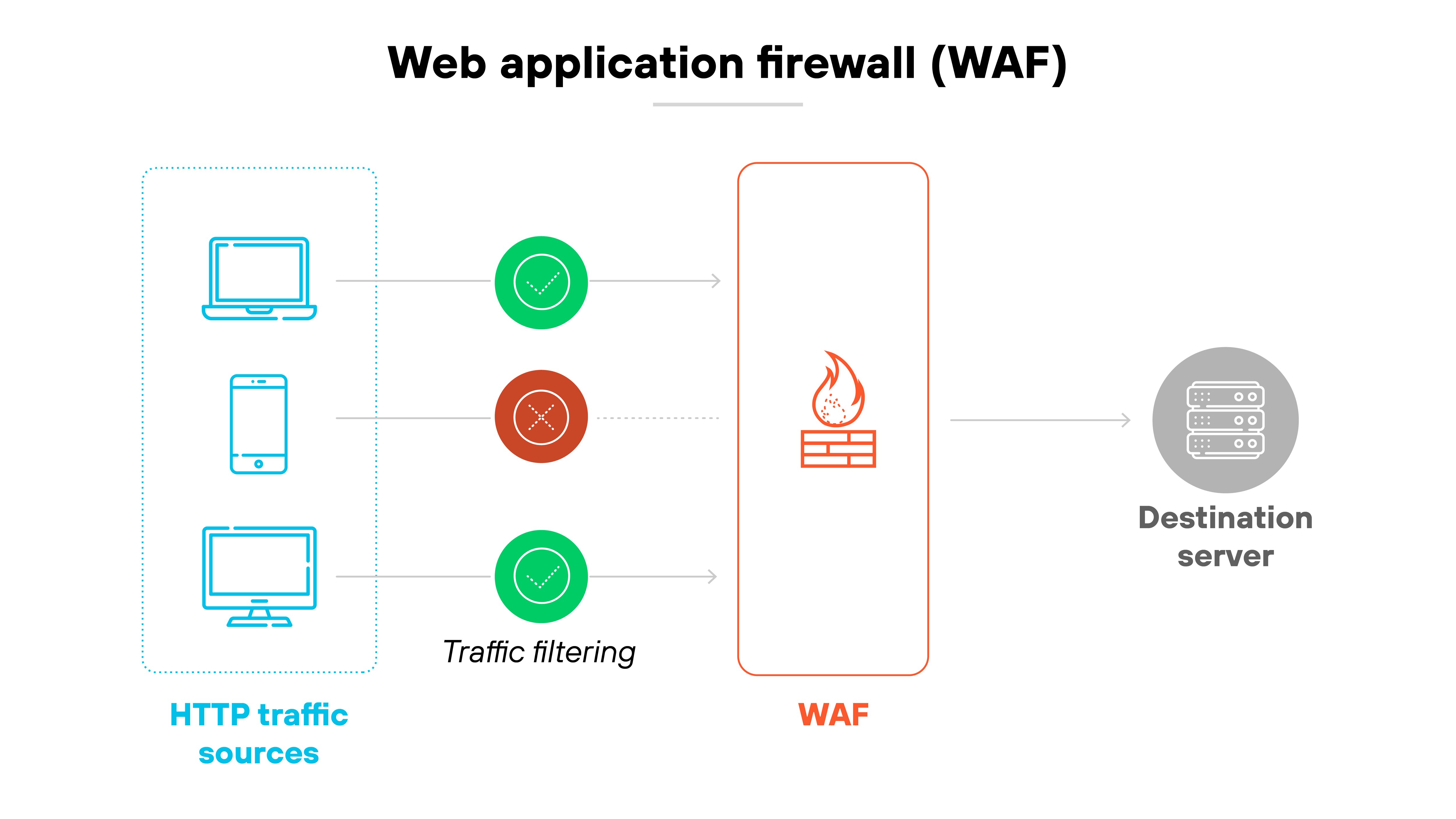
An NGFW might block malicious inbound traffic targeting the network. But it won’t stop an injection attack targeting a specific web form.
That’s a WAF’s job. NGFWs help control general access to apps. WAFs analyze how those apps behave under active use.
They also differ in who manages them. NGFWs are usually handled by network security teams. WAFs often require input from application developers. That’s because policy tuning depends on application logic, not just traffic patterns.
NGFW vs. UTM
At first glance, unified threat management (UTM) systems and next-generation firewalls (NGFWs) can seem similar—both combine multiple security functions into a single device. But the differences become clear with scale, flexibility, and depth of control.
UTMs consolidate basic features like firewalling, antivirus, URL filtering, and sometimes intrusion prevention. They’re typically designed for smaller environments and emphasize simplicity over customization. Their strength lies in offering broad protection through a general-purpose package.
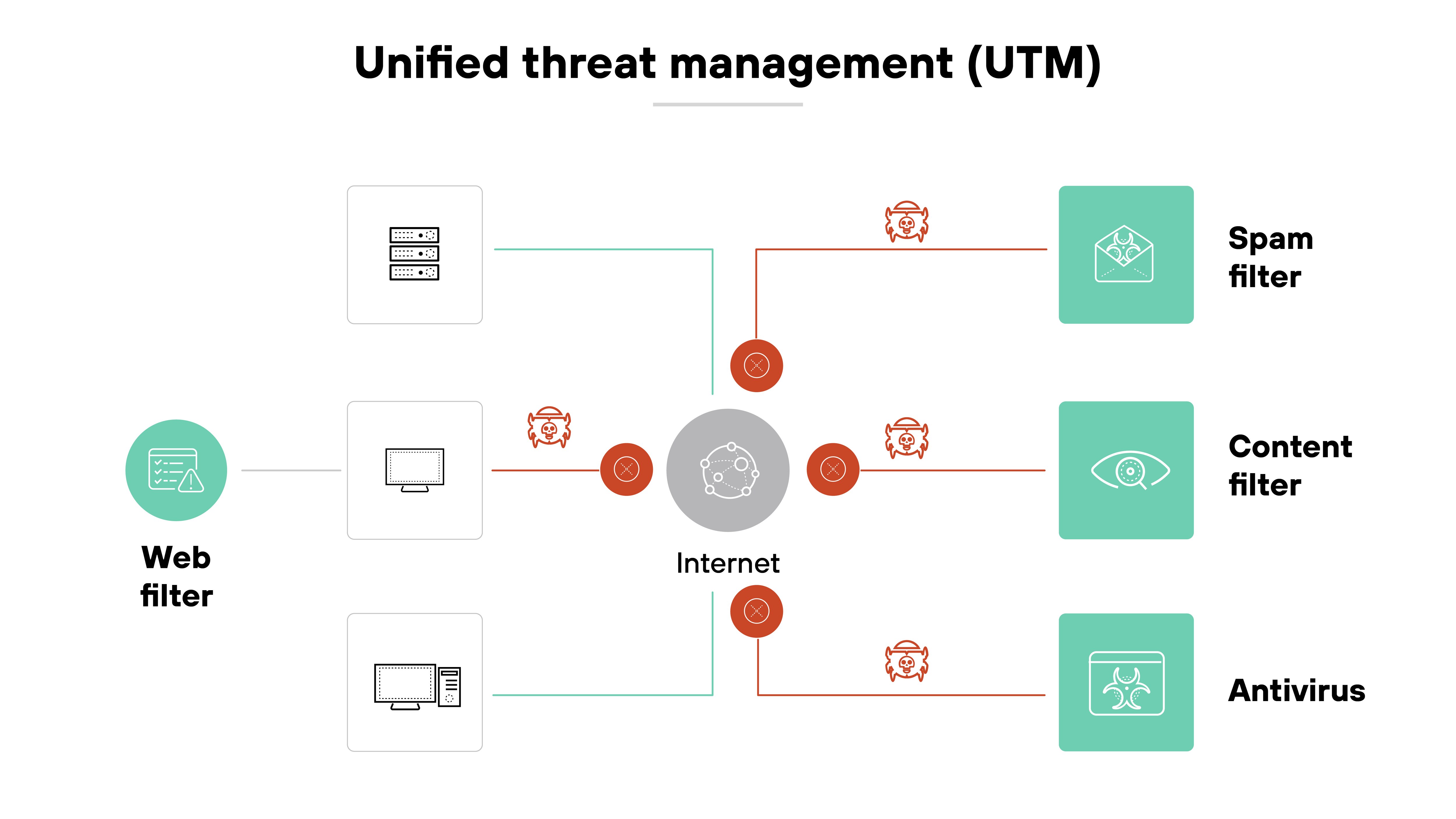
NGFWs, by contrast, are built for deeper inspection and more advanced security enforcement. They provide granular visibility into applications, users, and content—making them better suited for enterprise or high-volume networks.
Another key distinction is flexibility. While UTMs tend to be static, NGFWs can be tailored to specific use cases, offering more precise control and integration across complex environments.
NGFW vs. FWaaS
Firewall-as-a-service (FWaaS) is a deployment model. It refers to delivering firewall capabilities from the cloud.
NGFW is a set of capabilities. So you can have a FWaaS that uses NGFW features.
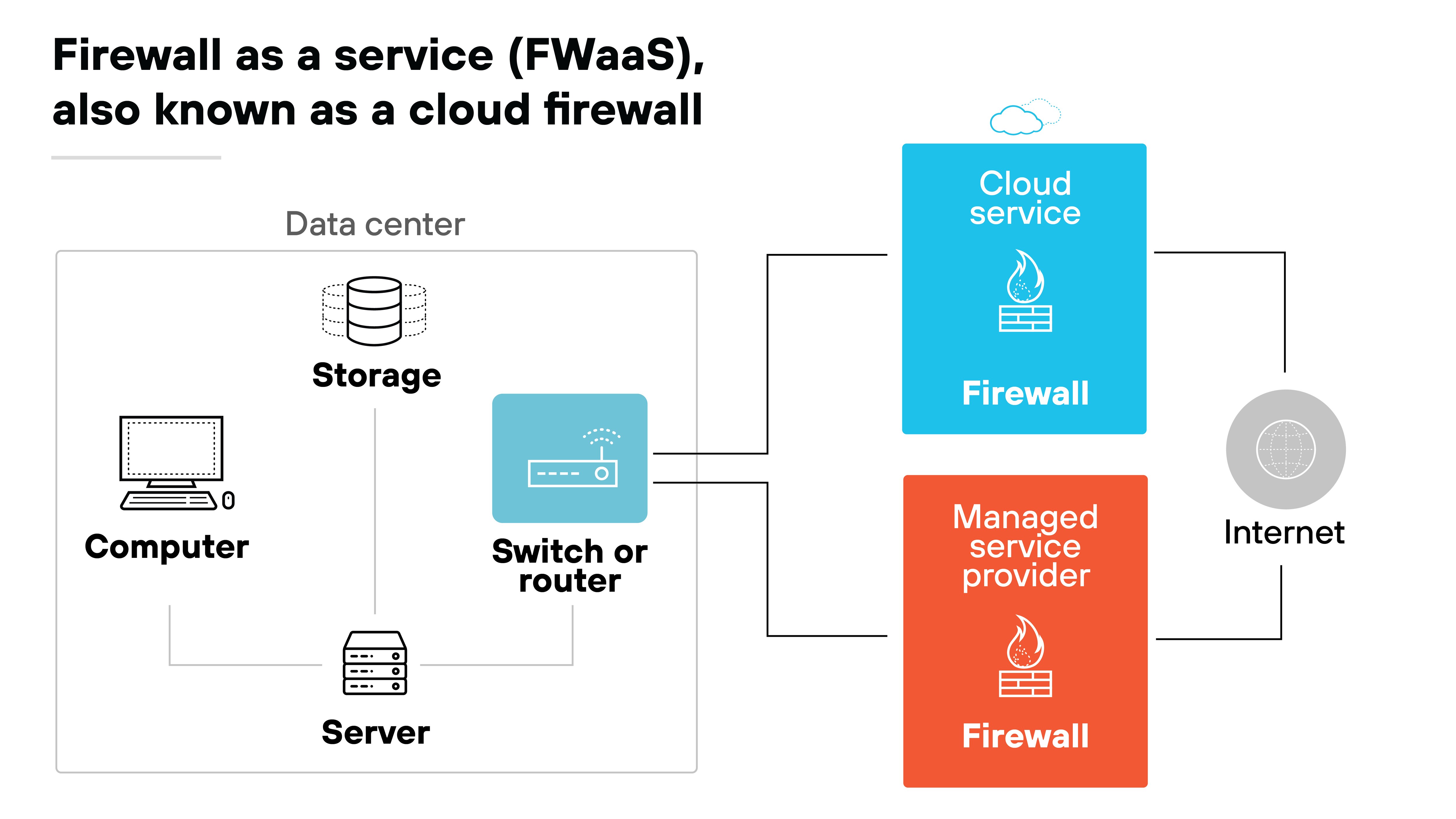
The key distinction is how they’re deployed and managed.
Traditional NGFWs are often physical or virtual appliances deployed on-premises.
FWaaS shifts the firewall to a cloud-based model, typically managed by a service provider.
This can be useful for organizations with a distributed workforce or heavy cloud adoption. But it doesn’t change the fundamentals of firewall inspection. Whether on-prem or cloud-hosted, a firewall still needs to enforce policy, inspect traffic, and log activity.
In other words:
FWaaS is a delivery method. NGFW is a capability set. The two are not mutually exclusive.
NGFW vs. network firewall
A network firewall filters traffic between a trusted internal network and an untrusted external one. It typically works by inspecting packets and applying rules to allow or deny traffic based on IP addresses, ports, and protocols.
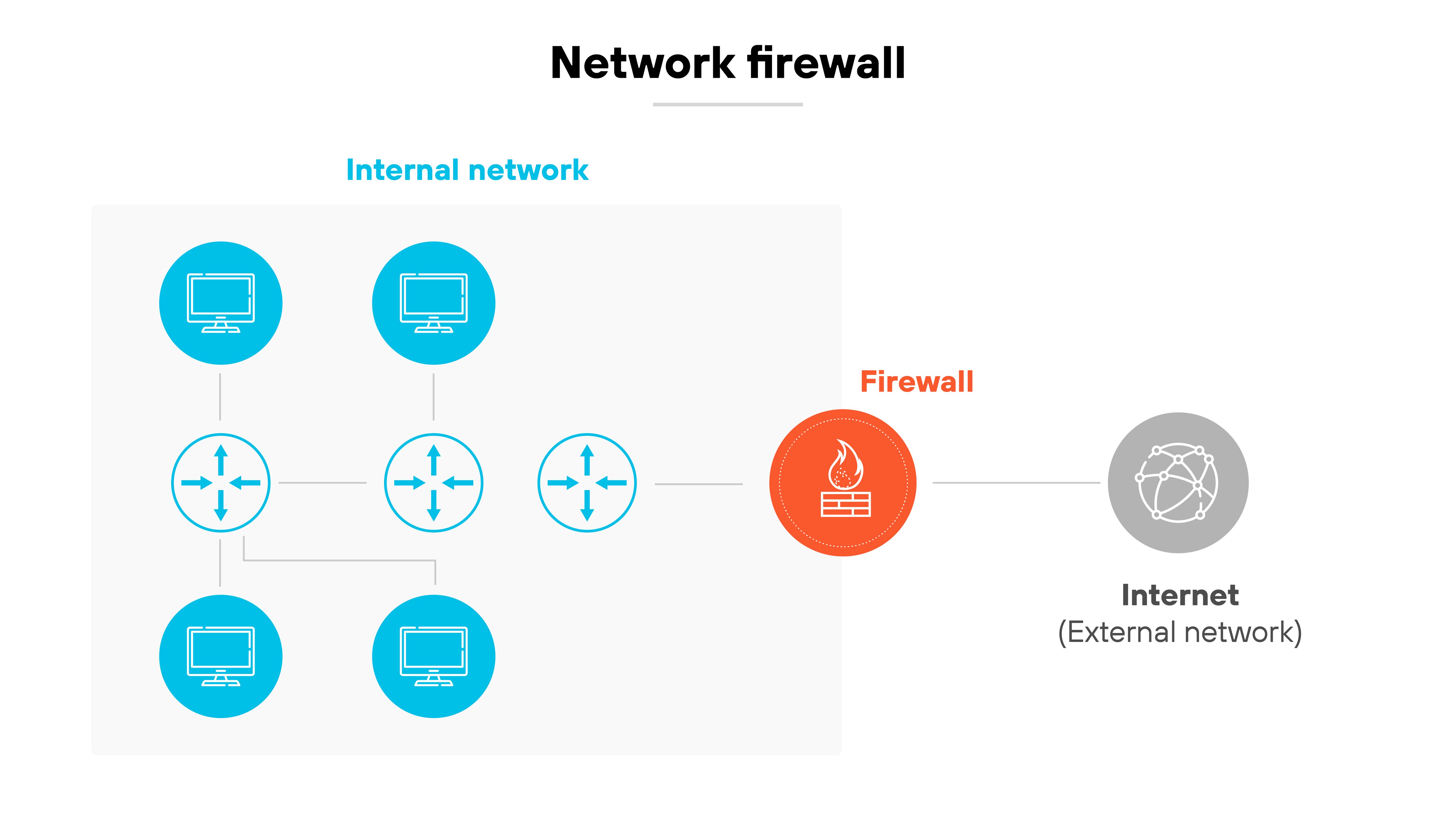
NGFWs build on this foundation. They include all the core capabilities of traditional firewalls—but go further. NGFWs analyze traffic at a deeper level and add features like application awareness, user identification, and integrated threat prevention.
Put simply:
Network firewalls control traffic at the perimeter. NGFWs add context and control based on who the user is, what application they're using, and whether the traffic poses a threat.
They're not separate categories. NGFWs are the next evolution of network firewalls.
| Further reading:
- What is the Difference Between Web Application Firewall (WAF) and Next-Generation Firewall (NGFW)?
- Firewall | Antivirus — What Is the Difference?
- IPS. vs. IDS vs. Firewall: What Are the Differences?
Learn the basics of NGFWs, featuring Next-Generation Firewalls for Dummies.
Download eBookNGFW FAQs
A next-generation firewall (NGFW) is a security device that inspects traffic by application, user, and content. It integrates traditional firewall functions with intrusion prevention and threat detection for deeper, context-aware enforcement.
NGFWs classify applications, identify users, inspect content, decrypt SSL traffic, block threats in real time, and enforce granular policies. Modern models also include DNS security, cloud control, IoT visibility, and integration with security ecosystems.
NGFWs inspect traffic across layers 3, 4, and 7 of the OSI model. They go beyond basic packet filtering by analyzing application-layer traffic for deeper visibility and control.
NGFWs use both. They rely on signature-based detection for known threats and behavioral analysis—including machine learning—to detect unknown or evasive attacks.
Yes. NGFWs include built-in intrusion prevention systems (IPS) that inspect traffic in real time and block malicious behavior—including zero-day attacks.
Single-pass architecture is key. It allows NGFWs to apply multiple security functions in one processing flow, maintaining performance even under heavy inspection loads.
SSL decryption. NGFWs decrypt, inspect, and re-encrypt SSL/TLS traffic to detect threats hidden in encrypted sessions.
Palo Alto Networks introduced the first NGFW and currently holds the leading market share in the NGFW space.
NGFWs provide deeper visibility, stronger threat prevention, and more granular control than traditional firewalls. They secure modern networks by inspecting encrypted traffic, identifying users, and detecting evasive threats.